- 18 Sep 2024
- 19 Minutes to read
-
Print
-
DarkLight
-
PDF
The Details Drawer
- Updated on 18 Sep 2024
- 19 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The Details drawer for an Indicator, Group, Tag, Track, Victim, or Victim Asset in ThreatConnect® provides a detailed overview of the threat intelligence data object you are investigating, including its metadata and associations. From this drawer, you can gather context about the object and take additional action, such as opening the Details screen to further analyze the object or pivoting from the object to an associated entity.
Before You Start
User Roles
- To view the Details drawer for a threat intelligence data object in an Organization, your user account can have any Organization role.
- To view the Details drawer for a threat intelligence data object in a Community or Source, your user account can have any Community role except Banned for that Community or Source.
- To delete an Indicator in an Organization via the Details drawer, your user account must have an Organization role of Standard User, Sharing User, Organization Administrator, or App Developer.
- To delete an Indicator in a Community or Source via the Details drawer, your user account must have a Community role of Editor or Director for that Community or Source.
Prerequisites
- To view information retrieved from CAL™ for Indicators, turn on CAL for your Organization and ThreatConnect instance (must be a System Administrator to perform this action).
- To have access to the Tags Across Owners card and Unified View option on the Details drawer for Indicators, turn on the multiSourceViewEnabled system setting (must be a System Administrator to perform this action).
Accessing the Details Drawer for Threat Intelligence Data
Currently, you can access the Details drawer for threat intelligence data objects in the following areas of ThreatConnect:
- the Browse screen
- the Search drawer
- the Search screen
- Threat Graph
- the Artifacts, Associations, and Potential Associations cards in Workflow Cases
- the Keyword Tracking & Results card on the Details screen for Intelligence Requirements (IRs)
Details Drawer Layout
A threat intelligence data object’s Details drawer consists of several sections with relevant information about the object. Depending on the type of object whose Details drawer you are viewing, the layout of the drawer and the data the drawer shows will vary.
Indicators
Figure 1 shows the Details drawer for a File Indicator. The Details drawer for all other Indicator types has a similar layout.
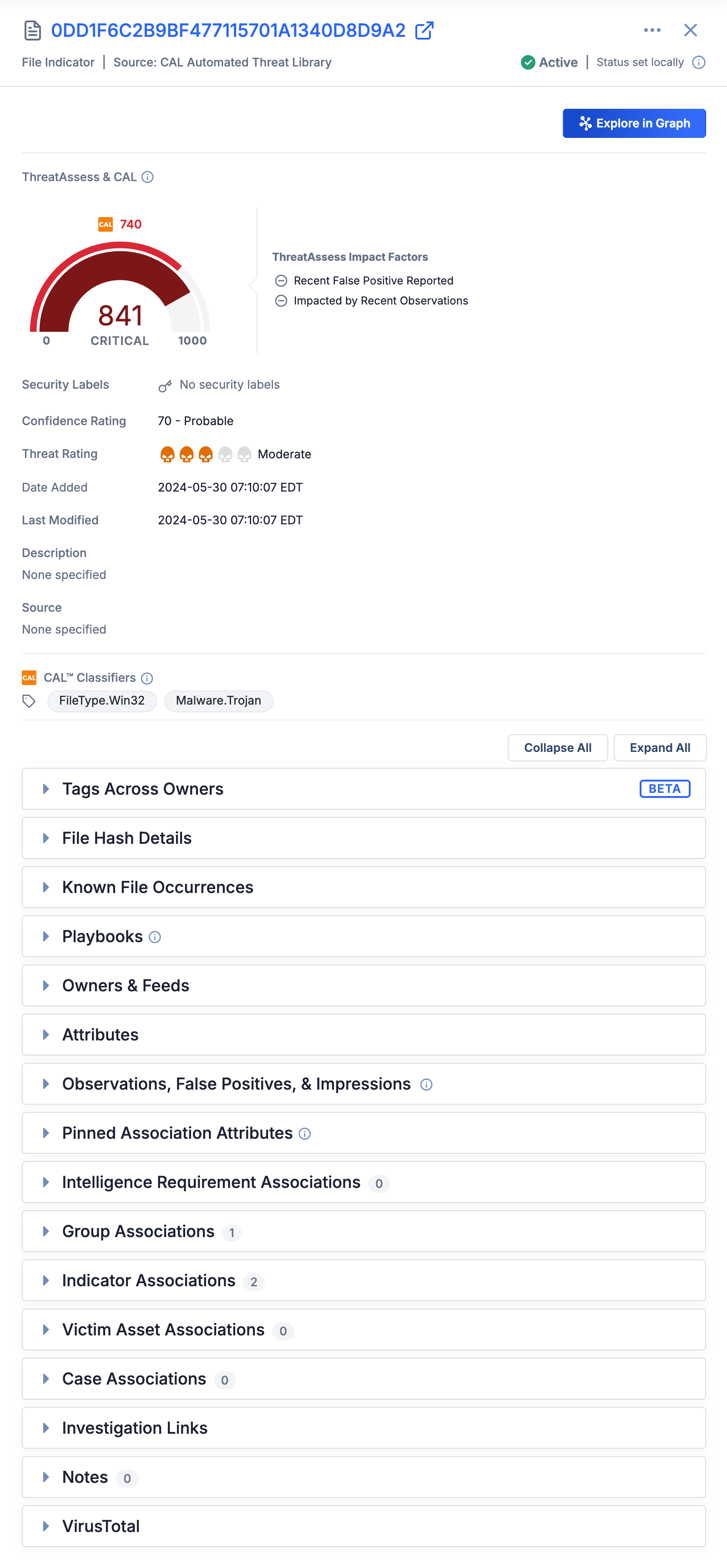
The Details drawer for Indicators consists of three primary sections:
- Header: The header of an Indicator’s Details drawer displays the Indicator’s summary, type, and owner, as well as the Indicator’s status and whether it was set locally (i.e., by a user with permission to change an Indicator’s status on your ThreatConnect instance) or by CAL. The header also includes a ⋯ menu , as well as an Explore in Graph button that lets you view the Indicator in Threat Graph.NoteIf viewing the Details drawer for an Indicator that exists in multiple owners, the drawer’s header will include an Owners dropdown that you can use to switch between the Indicator’s Details drawer in each of its owners. If the multiSourceViewEnabled system setting is turned on for your ThreatConnect instance, this dropdown will include a Unified View option that lets you view information about the Indicator from all of its owners to which you have access.NoteIf CAL Status Lock is turned on for an Indicator, a message stating “CAL Status Lock Enabled” will be displayed in the header of the Indicator’s Details drawer, to the left of the Indicator’s status. Similarly, if an Indicator is on an Indicator Exclusion List, a message stating “⊘ On Exclusion List” will be displayed in the header of the Indicator’s Details drawer, to the left of the Indicator’s status.
- Details: The top portion of an Indicator’s Details drawer displays the following details about the Indicator:
- ThreatAssess & CAL: The Indicator’s ThreatAssess score, CAL score, and ThreatAssess and CAL impact factors.
- Security Labels: The Security Labels applied to the Indicator.
- Confidence Rating: The Indicator’s Confidence Rating.
- Threat Rating: The Indicator’s Threat Rating.
- Date Added: The date and time when the Indicator was created in the owner listed in the Details drawer header.
- Last Modified: The date and time when the Indicator was last modified in the owner listed in the Details drawer header.
- Description: The Indicator's default Description Attribute.
- Source: The Indicator's default Source Attribute.
- Tags: The Tags applied to the Indicator in the owner listed in the Details drawer header. This section is available only if the multiSourceViewEnabled system setting is turned off. Otherwise, the Tags applied to the Indicator will be displayed on the Tags Across Owners card in the bottom portion of the Details drawer, and they will be the Tags applied to the Indicator across all of the Indicator’s owners to which you have access.
- CAL™ Classifiers: The CAL Classifiers applied to the Indicator.
- Cards: The bottom portion of an Indicator’s Details drawer contains cards with relevant information for the Indicator. The cards available in this section depend on the type of Indicator whose Details drawer you are viewing. Click on an individual card to expand and collapse it, or use the Collapse All and Expand All buttons to collapse and expand all cards, respectively.
Table 1 provides a description of each card that may be displayed in the bottom portion of an Indicator’s Details drawer and the Indicator type(s) for which each card is available.
| Name | Description | Applicable Indicator Type(s) |
|---|---|---|
| Attributes | The Attributes added to the Indicator. | All |
| Case Associations | The Cases associated to the Indicator. | All |
| DNS Resolution | The DNS resolution history for the Indicator (domain resolutions for Address Indicators; IP address resolutions for Host Indicators), as well as location and count information for computers that attempted to access suspicious domains captured by Quad9® infrastructure within the last 90 days. | Address; Host |
| DomainTools | The enrichment data retrieved from DomainTools® for the Host Indicator. Click Retrieve Data on the DomainTools card to retrieve the latest enrichment data from DomainTools for the Indicator. | Host |
| Farsight Passive DNS | The enrichment data retrieved from Farsight Security® for the Address or Host Indicator. Click Retrieve Data on the Farsight Passive DNS card to retrieve the latest enrichment data from Farsight Security for the Indicator. | Address; Host |
| File Hash Details | The File Indicator’s MD5, SHA1, and SHA256 file hashes and file size, as well as analytics about a file sample’s various hashes derived from CAL. | File |
| GeoLocation Data | The IP address geographic information within ThreatConnect and CAL for the Address Indicator. | Address |
| Group Associations | The Groups associated to the Indicator. | All |
| Indicator Associations | The Indicators associated to the Indicator. | All |
| Intelligence Requirement Associations | The IRs associated to the Indicator. | All |
| Investigation Links | Links to search results of various third-party lookups and other information services. Each link is a shortcut to query results for the Indicator, which will open in a new browser tab. | All |
| Known File Occurrences | The Known File Occurrences added to the File Indicator. | File |
| Notes | The posts added to the Indicator. | All |
| Observations, False Positives, & Impressions | The number of observations and false positive reports for the Indicator in your ThreatConnect instance, as well as the number of observations, false positive reports, and impressions derived from CAL for the Indicator. Select Report False Positive on the Observations, False Positives, & Impressions card to report the Indicator as a false positive. | All |
| Owners & Feeds | The owners in which the Indicator exists, the Threat Rating and Confidence Rating assigned to the Indicator by those owners, and the feeds that have reported the Indicator. | All |
| Pinned Association Attributes | The association Attributes added to Groups associated to the Indicator. | All |
| Playbooks | The active Playbooks with a UserAction Trigger configured for the Indicator’s type. Click Run playbook | All |
| RiskIQ | The enrichment data retrieved from RiskIQ® for the Host Indicator. Click Retrieve Data on the RiskIQ card to retrieve the latest enrichment data from RiskIQ for the Indicator. | Host |
| Shodan | The enrichment data retrieved from Shodan® for the Address Indicator. Click Retrieve Data on the Shodan card to retrieve the latest enrichment data from Shodan for the Indicator. | Address |
| Tags Across Owners | The Tags applied to the Indicator across all of the Indicator’s owners to which you have access. This card is available only if your System Administrator turned on the multiSourceViewEnabled system setting. Otherwise, the Tags applied to the Indicator will be displayed in the top portion of the drawer, and they will be the Tags applied to the Indicator only in the owner listed in the Details drawer header. Important As of ThreatConnect 7.6, the Tags Across Owners card is a beta feature. | All |
| URLScan | The enrichment data retrieved from urlscan.io for the URL Indicator. Click Retrieve Data on the URLScan card to retrieve the latest enrichment data from urlscan.io for the Indicator. | URL |
| Victim Asset Associations | The Victim Assets associated to the Indicator. | All |
| VirusTotal | The enrichment data retrieved from VirusTotal™ for the Address, File, Host, or URL Indicator. Click Retrieve Data on the VirusTotal card to retrieve the latest enrichment data from VirusTotal for the Indicator. | Address; File; Host; URL |
| Whois | The WHOIS data for the Host Indicator. | Host |
Unified View
If an Indicator exists in multiple owners and the multiSourceViewEnabled system setting is turned on for your ThreatConnect instance, you can select Unified View in the Owners dropdown in the header of the Indicator’s Details drawer to view information about the Indicator from all of its owners to which you have access (Figure 2).
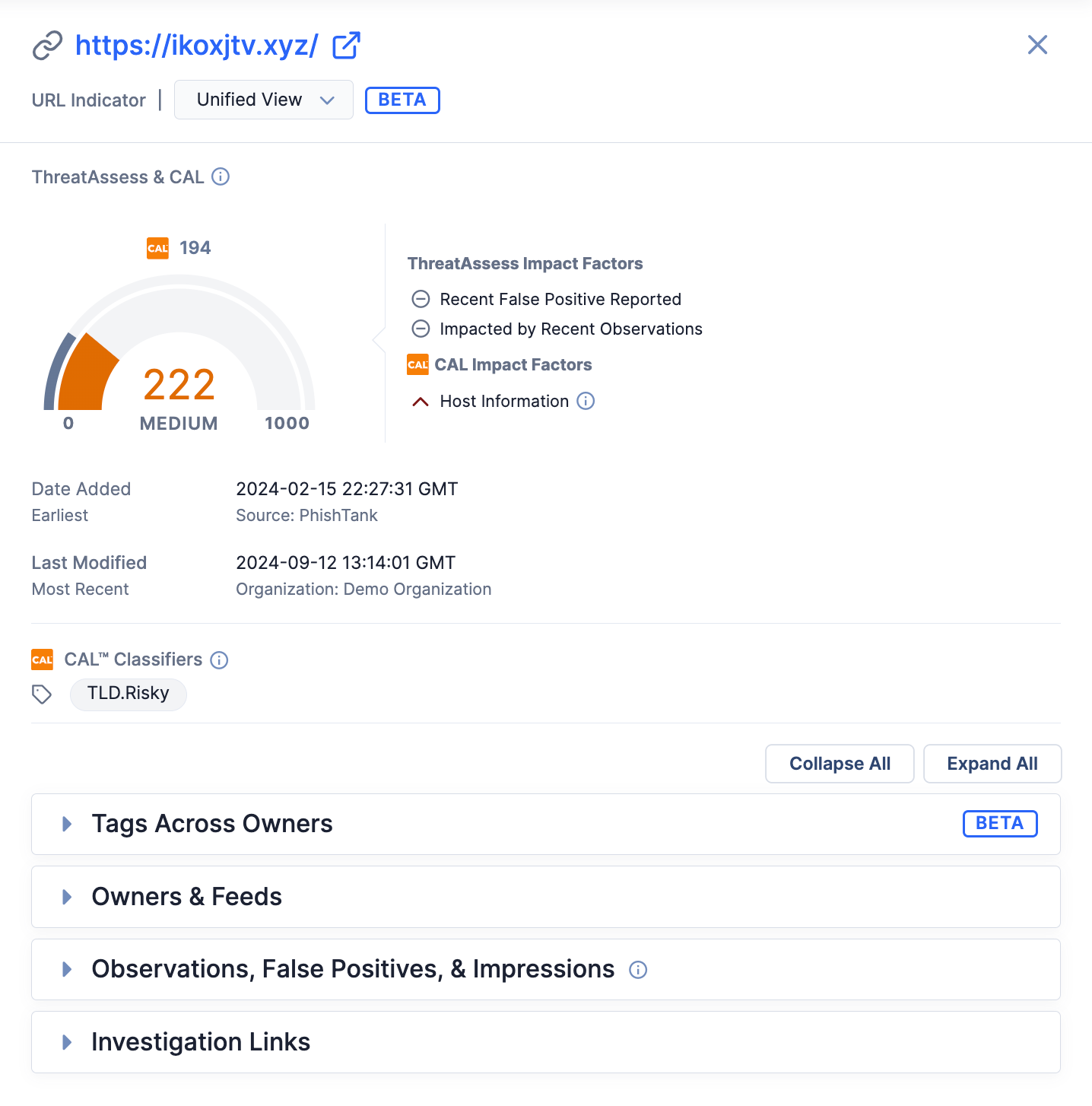
When Unified View is selected in the Owners dropdown, the Details drawer will display the following information:
- The Indicator’s ThreatAssess score, CAL score, and ThreatAssess and CAL impact factors
- The Indicator’s earliest creation date (i.e., the date and time when the Indicator was first added to any of its owners)
- The Indicator’s most recent “last modified” date (i.e., the date and time when the Indicator was last modified in any of its owners)
- The CAL Classifiers applied to the Indicator
- The Tags Across Owners; Owners & Feeds; Observations, False Positives, & Impressions; and Investigation Links cards
Groups
Adversary, Attack Pattern, Campaign, Course of Action, Document, Event, Incident, Intrusion Set, Malware, Report, Tactic, Threat, Tool, and Vulnerability
Figure 3 shows the Details drawer for a Report Group. The Details drawer for Adversary, Attack Pattern, Campaign, Course of Action, Document, Event, Incident, Intrusion Set, Malware, Tactic, Threat, Tool, and Vulnerability Groups has a similar layout.
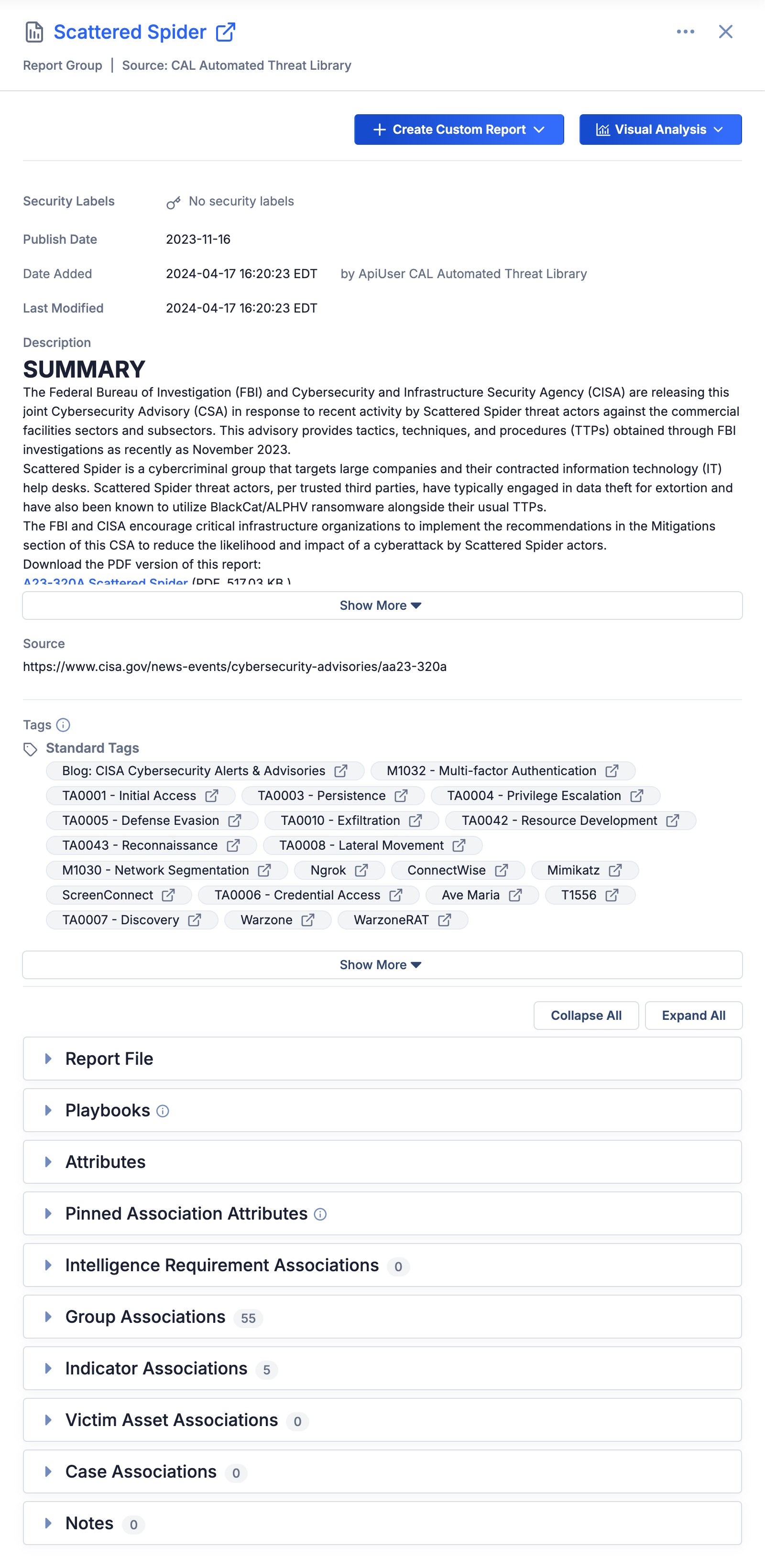
The Details drawer for Adversary, Attack Pattern, Campaign, Course of Action, Document, Event, Incident, Intrusion Set, Malware, Report, Tactic, Threat, Tool, and Vulnerability Groups consists of three primary sections:
- Header: The header of a Group’s Details drawer displays the Group’s summary, type, and owner. It also includes a ⋯ menu, a + Create Custom Report button that lets you create a report for the Group from scratch or from a Group report template, and a Visual Analysis button that lets you view and analyze the Group in Threat Graph or the ATT&CK® Visualizer.NoteIf viewing the Details drawer for an Adversary, Attack Pattern, Campaign, Course of Action, Document, Event, Incident, Intrusion Set, Malware, Report, Tactic, Threat, Tool, or Vulnerability Group in Threat Graph and the Group exists in multiple owners, the drawer’s header will include an Owners dropdown that you can use to switch between the Group’s Details drawer in each of its owners. However, if there are multiple copies of the Group in a single owner (that is, there is more than one Group with the same name and type in an owner), you cannot choose which copy of the Group the Details drawer will open for in Threat Graph. Also, you cannot toggle between the Details drawer for each copy of the Group in a single owner in Threat Graph.
- Details: The top portion of a Group’s Details drawer displays the following details about the Group:
- Security Labels: The Security Labels applied to the Group.
- First Seen: The date when the Campaign was first seen (Campaign Groups only).
- Event Date: The date when the Event or Incident took place (Event and Incident Groups only).
- Event Type: The Event’s type (Event Groups only).
- Status: The status of the Event or Incident (Event and Incident Groups only).
- Publish Date: The date when the Report was published (Report Groups only).
- Date Added: The date and time when the Group was created in the owner listed in the Details drawer header.
- Last Modified: The date and time when the Group was last modified in the owner listed in the Details drawer header.
- Description: The Group's default Description Attribute.
- Source: The Group's default Source Attribute.
- Tags: The Tags applied to the Group in the owner listed in the Details drawer header.
- Cards: The bottom portion of a Group’s Details drawer contains cards with relevant information for the Group. The cards available in this section depend on the type of Group whose Details drawer you are viewing. Click on an individual card to expand and collapse it, or use the Collapse All and Expand All buttons to collapse and expand all cards, respectively.
Table 2 provides a description of each card that may be displayed in the bottom portion of a Group’s Details drawer and the Group type(s) for which each card is available.
| Name | Description | Applicable Group Type(s) |
|---|---|---|
| Attributes | The Attributes added to the Group. | All |
| Case Associations | The Cases associated to the Group. | All |
| Document File | The name, type, and size of the file uploaded to the Document Group and the status of the file upload. To preview or download the file, click the thumbnail preview or Download, respectively, on the Document File card. | Document |
| Group Associations | The Groups associated to the Group. | All |
| Indicator Associations | The Indicators associated to the Group. | All |
| Intelligence Requirement Associations | The IRs associated to the Group. | All |
| Notes | The posts added to the Group. | All |
| Pinned Association Attributes | The association Attributes added to Groups associated to the Group. | All |
| Playbooks | The active Playbooks with a UserAction Trigger configured for the Group’s type. Click Run playbook | All |
| Report File | The name, type, and size of the file uploaded to the Report Group and the status of the file upload. To preview or download the file, click the thumbnail preview or Download, respectively, on the Report File card. | Report |
| Victim Asset Associations | The Victim Assets associated to the Group. | All |
Email, Signature, and Task
Figure 4 shows the Details drawer for a Signature Group. The Details drawer for Email and Task Groups has a similar layout.
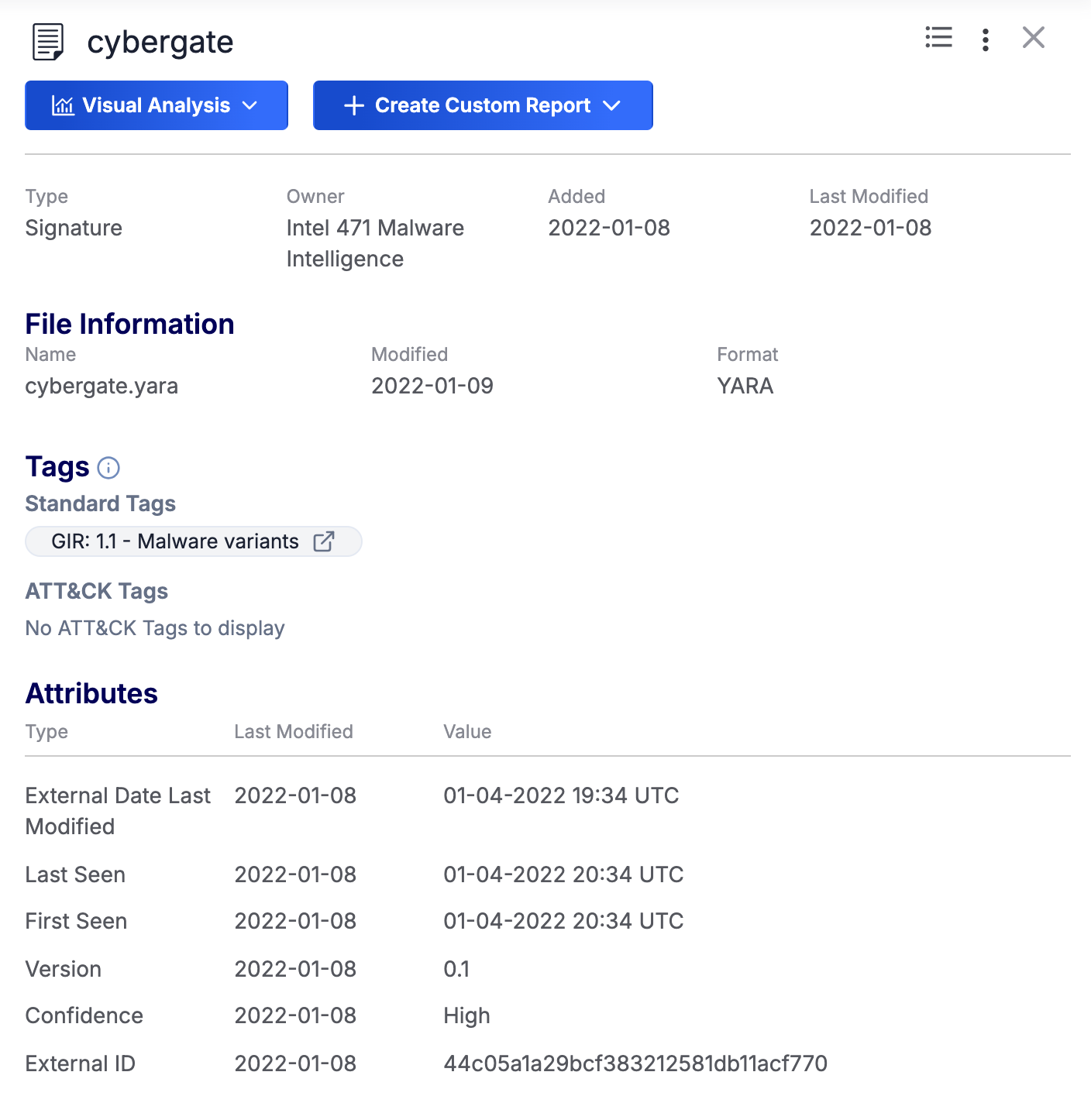
Table 3 provides a description of each section and element that may be displayed on the Details drawer for Email, Signature, and Task Group and the Group type(s) for which each section is available.
| Name | Description | Applicable Group Type(s) |
|---|---|---|
| Added | The date when the Group was created. | All |
| Assignees | The users assigned to the Task. | Task |
| Associated Indicators | The Indicators associated to the Group. If there are more than 10 associated Indicators, a link labeled all associated indicators... will be displayed at the bottom of this section. Click it to display the Associations tab of the Group’s Details screen and view all associated Indicators. | All |
| Associated Intel | The Groups associated to the Group. | All |
| Associated Victim Assets | The Victim Assets associated to the Group. | All |
| Attributes | The Attributes added to the Group. | All |
| + Create Custom Report | Click + Create Custom Report create a report for the Group from scratch or from a Group report template. | All |
| Description | If a default Description Attribute has been added to the Group, it will be displayed above the Type, Owner, Added, and Last Modified sections. | All |
| Due Date | The date when the Task is due. | Task |
| Email Information | This section displays the following information for the Email Group: the Threat Score of the Email, the sender’s email address, the date when the Email was sent, and the Email’s subject. | |
| File Information | The name and format of the signature file corresponding to the Signature Group and the date when the file was last modified. | Signature |
| Last Modified | The date when the Group was last modified. | All |
| Owner | The Organization, Community, or Source to which the Group belongs. | All |
| Security Labels | The Security Labels applied to the Group. | All |
| Status | The status of the Task. | Task |
| Tags | The Tags applied to the Group. | All |
| Type | The Group’s type. | All |
| Visual Analysis | Click Visual Analysis to display the following options:
| All |
Tags
Table 4 provides a description of each section and element that may be displayed on the Details drawer for a Tag, which has a layout similar to the one shown in Figure 4.
| Name | Description |
|---|---|
| Associated Indicators | The Indicators to which the Tag is applied. If there are more than 10 Indicators, a link labeled all associated indicators... will be displayed at the bottom of this section. Click it to display the Tag’s legacy Details screen and view all Indicators to which it is applied on the Associations card . |
| Associated Intel | The Groups to which the Tag is applied. |
| Associated Victims | The Victims to which the Tag is applied. |
| Explore in Graph | Click Explore in Graph to view the Tag in Threat Graph. |
| Last Used | The date when the Tag was last used. For Tags that have not been used since the Last Used date was introduced in ThreatConnect, this section will display a value of Unknown. |
| Owner | The Organization, Community, or Source to which the Tag belongs. |
| Summary | The Tag’s summary. |
| Synonymous Tags | This section is displayed only for main Tags defined in Tag normalization rules (i.e., Tags with the |
| Type | This section will always display a value of “Tag.” |
Tracks
Table 5 provides a description of each section that may be displayed on the Details drawer for a Track, which has a layout similar to the one shown in Figure 4.
| Name | Description |
|---|---|
| Active | This section specifies whether the Track is active. |
| Added | The date when the Track was created. |
| Description | If a description has been added to the Track, it will be displayed above the Type, Owner, Added, and Active sections. |
| Owner | The Organization, Community, or Source to which the Track belongs. |
| Results | The number of results for the Track. |
| Type | This section will always display a value of “Track.” |
Victims
Table 6 provides a description of each section that may be displayed on the Details drawer for a Victim, which has a layout similar to the one shown in Figure 4.
| Name | Description |
|---|---|
| Assets | The Victim Assets added to the Victim. Victim Asset(s) are also displayed in the Associated Victim Assets section. |
| Associated Indicators | The Indicators associated to one or more of the Victim’s Assets. If there are more than 10 associated Indicators, a link labeled all associated indicators... will be displayed at the bottom of this section. Click it to display the Victim’s legacy Details screen and view all associated Indicators on the Associations card . |
| Associated Intel | The Groups associated to one or more of the Victim’s Assets. |
| Associated Victim Assets | The Victim Assets added to the Victim. Victim Asset(s) are also displayed in the Assets section. |
| Attributes | The Attributes added to the Victim. |
| Description | If a default Description Attribute has been added to the Victim, it will be displayed above the Type, Owner, Victim Organization, and Sub-Organization sections. |
| Nationality | The Victim’s nationality. |
| Owner | The Organization, Community, or Source to which the Victim belongs. |
| Security Labels | The Security Labels applied to the Victim. |
| Sub-Organization | The Victim’s sub-organization. |
| Tags | The Tags applied to the Victim. |
| Type | This section will always display a value of “Victim.” |
| Victim Organization | The Victim’s organization. |
| Work Location | The Victim’s work location. |
Victim Assets
Table 7 provides a description of each section that may be displayed on the Details drawer for a Victim Asset, which has a layout similar to the one shown in Figure 4.
| Name | Description |
|---|---|
| Asset | For Email Address, Network Account, and Social Network Victim Assets, this section will display the corresponding account type, if one has been provided; for Phone and Website Victim Assets, this section will always display a value of “None,” as you cannot specify an account type for these Victim Asset types. |
| Associated Indicators | The Indicators associated to the Victim Asset. If there are more than 10 associated Indicators, a link labeled all associated indicators... will be displayed at the bottom of this section. Click it to display the legacy Details screen for the Victim to which the Victim Asset belongs and view all associated Indicators on the Associations card . |
| Associated Intel | The Groups associated to the Victim Asset. |
| Type | This Victim Asset’s type. |
| Victim | The Victim to which the Victim Asset belongs. |
Details Drawer Options Menu
The Details drawer options menu, available for Indicators, Groups, and Tags only, lets you perform additional actions while investigating objects of these types.
Indicators
If you are viewing the Details drawer for an Indicator, click the ⋯ menu in the drawer’s header to display the following options:
- Pivot: Select Pivot to pivot from the Indicator and view its associated objects on the Browse screen.
- Follow: If you are not following the Indicator, the ⋯ menu will display the Follow option. Select Follow to follow the Indicator. By default, the notification priority level for the followed Indicator will be set to Medium.
- Unfollow: If you are already following the Indicator, the ⋯ menu will display the Unfollow option. Select Unfollow to unfollow the Indicator.
- Delete: If your user account has permissions to delete Indicators in the Indicator’s owner, the ⋯ menu will display the Delete option. Select Delete to delete the Indicator.
Groups
If you are viewing the Details drawer for an Adversary, Attack Pattern, Campaign, Course of Action, Document, Event, Incident, Intrusion Set, Malware, Report, Tactic, Threat, Tool, or Vulnerability Group (Figure 3), click the ⋯ menu in the drawer’s header to display the following options:
- Pivot: Select Pivot to pivot from the Group and view its associated objects on the Browse screen.
- Follow: If you are not following the Group, the ⋯ menu will display the Follow option. Select Follow to follow the Group. By default, the notification priority level for the followed Group will be set to Medium.
- Unfollow: If you are already following the Group, the ⋯ menu will display the Unfollow option. Select Unfollow to unfollow the Group.
- Delete: If your user account has permissions to delete Groups in the Group’s owner, the ⋯ menu will display the Delete option. Select Delete to delete the Group.
If you are viewing the Details drawer for an Email, Signature, or Task Group (Figure 4) , click the ⋮ menu in the drawer’s header to display the following options:
- Download: If the Details drawer is for a Signature Group with a file attachment, the Download option will be available. Select Download to download the Signature Group’s file attachment.
- Pivot: Select Pivot to pivot from the Group and view its associated objects on the Browse screen.
Tags
If you are viewing the Details drawer for a Tag, click the ⋮ menu in the drawer’s header to display the following option:
- Pivot: Select Pivot to pivot from the Tag and view its associated objects on the Browse screen.
Accessing the Details Screen From the Details Drawer
If you are viewing the Details drawer for an Email, Signature, or Task Group; Tag; Track; Victim; or Victim Asset, click View full details at the upper-right corner of the drawer to open the object’s legacy Details screen. If you are viewing the Details drawer for an Indicator or an Adversary, Attack Pattern, Campaign, Course of Action, Document, Event, Incident, Intrusion Set, Malware, Report, Tactic, Threat, Tool, or Vulnerability Group, click the object’s summary in the drawer’s header to open the object’s Details screen.
at the upper-right corner of the drawer to open the object’s legacy Details screen. If you are viewing the Details drawer for an Indicator or an Adversary, Attack Pattern, Campaign, Course of Action, Document, Event, Incident, Intrusion Set, Malware, Report, Tactic, Threat, Tool, or Vulnerability Group, click the object’s summary in the drawer’s header to open the object’s Details screen.
ThreatConnect® is a registered trademark, and CAL™ is a trademark, of ThreatConnect, Inc.
DomainTools® and Farsight Security® are registered trademarks of DomainTools, LLC.
VirusTotal™ is a trademark of Google, Inc.
RiskIQ® is a registered trademark of Microsoft Corporation.
Quad9® is a registered trademark of Quad9 Foundation.
Shodan® is a registered trademark of Shodan.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.
20051-03 v.18.A


