- 14 May 2025
- 21 Minutes to read
-
Print
-
DarkLight
-
PDF
The ThreatConnect Data Model
- Updated on 14 May 2025
- 21 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
ThreatConnect® models threat intelligence, internal investigation findings, and work done related to both primarily in seven categories:
- Indicator: An Indicator object represents an atomic piece of information that has some intelligence value.
- Group: A Group object represents a collection of related behavior and intelligence.
- Victim: A Victim object represents a specific organization or group that has been targeted or whose assets (e.g., accounts, infrastructure, equipment) have been exploited. Victim Assets are added to a Victim object to represent these assets.
- Intelligence Requirement: An Intelligence Requirement (IR) object models a collection of topics or a research question reflecting an organization’s cyberthreat-related priorities that guides a security or threat intelligence team’s research and analysis efforts.
- Workflow Case: The Workflow feature in ThreatConnect allows you to combine manual and automated operations to define consistent and standardized processes for your security teams, including digital risk investigations, malware analysis, phishing triage, alert triage, intel requirement development, escalation procedures, and breach standard operating procedures. The primary object in the Workflow feature in which work is done is a Case: a single instance of an investigation, query, or other procedure in your Organization.
- Artifact: An Artifact is a piece of data collected by a Workflow Case that might be useful to an analyst. Artifacts can be mapped to ThreatConnect Indicators if they are identical objects. For example, an investigation carried out in a Case might identify a particular URL that exists, or can be added, as a URL Indicator in ThreatConnect. All native ThreatConnect Indicator types have a corresponding Artifact type; however, not all Artifact types correspond to an Indicator type.
- Tag: A Tag is a metadata object that you can apply to Indicators, Groups, Victims, IRs, and Cases.
Associations represent relationships between data objects in ThreatConnect. You can use them to model and explore connections in your data to build a more nuanced and complete picture of the threats and threat actors in your environment. The Threat Graph feature allows you to model, create, and delete associations in a visual interface.
Understanding the ThreatConnect data model enables you to create and search for data in your owners, establish patterns across pieces of information, and orchestrate preventive and defensive strategies and operations. You can use the definitions provided in this article as a resource when importing, building, and modeling your own threat intelligence in ThreatConnect.
Before You Start
User Roles
- To view the Details screen for an Indicator, Group, Victim (including Victim Assets on the Assets tab), IR, or Tag in your Organization, your user account can have any Organization role.
- To view the Details screen for an Indicator, Group, Victim (including Victim Assets on the Assets tab), or Tag in a Community or Source, your user account can have any Community role except Banned for that Community or Source.
- To view a Workflow Case and Artifacts in the Case, your user account can have any Organization role except App Developer.
Prerequisites
- To access the Workflow functionality in your Organization, edit the Organization on the Organizations tab of the Account Settings screen and select the Enable Workflow checkbox on the Permissions tab of the Organization Information window (must be an Accounts Administrator, Operations Administrator, or System Administrator to perform this action).
Indicators
An Indicator represents an atomic piece of information that has some intelligence value within ThreatConnect’s Diamond Model. In ThreatConnect, Indicators are unique within an owner. For example, an Organization can have only one copy of the Host Indicator bad.com.
Indicators may be owned by Organizations, Communities, and Sources.
Indicator Types
ThreatConnect has 12 native Indicator types:
- Address: An Address Indicator represents a valid IP address, either IPv4
(e.g., 192.168.0.1) or IPv6. For IPv6, ThreatConnect supports standard (e.g., 1762:0:0:0:0:B03:1:AF18), “exploded” standard (e.g., 1762:0000:0000:0000:0000:0B03:0001:AF18), and compressed (e.g., 1762::B03:1:AF18) representations. Mixed notation (e.g., 1762:0:0:0:0:B03:127.32.67.15) is not supported. - ASN: An ASN (Autonomous System Number) Indicator represents a number that uniquely identifies each network on the Internet (e.g., ASN204288).
- CIDR: A CIDR (Classless Inter-Domain Routing) Indicator represents a block of network IP addresses (e.g., 10.10.1.16/32).
- Email Address: An Email Address Indicator represents a valid email address
(e.g., badguy@bad.com). - Email Subject: An Email Subject Indicator represents the subject line of an email.
- File: A File Indicator represents a unique file hash or series of hashes. ThreatConnect supports MD5, SHA-1, and SHA-256 file hash types.
- Hashtag: A Hashtag Indicator represents a hashtag term as used in social media.
- Host: A Host Indicator represents a valid hostname, also referred to as a domain (e.g., bad.com).
- Mutex: A Mutex Indicator is a synchronization primitive that can be used to identify malware files and relate malware families (e.g., \Sessions\1\BaseNamedObjects\Globa\CLR_PerfMon_WrapMutex).
- Registry Key: A Registry Key Indicator represents a node in a hierarchical database that contains data critical for the operation of Windows® and the applications and services that run on Windows (e.g., HKEY_CURRENT_USER\Software\MyApp).
- URL: A URL (Uniform Resource Locator) Indicator represents a valid URL, including protocol (e.g., http://www.bad.com/index.php?id=1). URLs are accepted according to RFC 3986, with a few exceptions: Underscore (_) is an allowed character for the third label (i.e., subdomains); the host section of the authority part must be lowercase; URL encoding is not verified (% is simply an accepted character in the path, query, and fragment); and user information must be removed from the authority part. Accepted schemes are http, https, ftp, and sftp. The host section of the authority part can be a hostname or an IPv4 address.
- User Agent: A User Agent Indicator is a characteristic identification string that a software agent uses when operating in a network protocol [e.g., Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.95 Safari/537.36].
Viewing Indicators
Follow these steps to view a table listing all Indicators in your ThreatConnect owners:
- Click Search
 on the top navigation bar.
on the top navigation bar. - Select the Indicators filter on the left sidebar of the Search screen.
Use the Search name/summary, Advanced Search, Indicator Type, and Filters options to filter the results set to specific Indicators or by Indicator type, owner, or other features. To view more information on a particular Indicator, click its entry in the Name/Summary column to navigate to its Details screen. The Overview tab of an Indicator’s Details screen contains cards displaying information about the Indicator, such as Security Labels and Attributes, as well as data specific to that Indicator type. For example, the Details screen for a File allows you to edit a file’s hashes and size, and the Details screen for an Address displays IP geolocation data. An Indicator’s Details screen also includes tabs providing information on the Indicator’s associations, user activity involving the Indicator, and enrichment services available for the Indicator’s type.
options to filter the results set to specific Indicators or by Indicator type, owner, or other features. To view more information on a particular Indicator, click its entry in the Name/Summary column to navigate to its Details screen. The Overview tab of an Indicator’s Details screen contains cards displaying information about the Indicator, such as Security Labels and Attributes, as well as data specific to that Indicator type. For example, the Details screen for a File allows you to edit a file’s hashes and size, and the Details screen for an Address displays IP geolocation data. An Indicator’s Details screen also includes tabs providing information on the Indicator’s associations, user activity involving the Indicator, and enrichment services available for the Indicator’s type.
Groups
A Group represents a collection of related behavior and intelligence. The term “Group” is derived from the Diamond Model of Intrusion Analysis’s concept of an “Activity Group.” It refers to a grouping, or cluster, of related activity. In ThreatConnect, a Group’s associated Indicators, IRs, Victim Assets, Cases, Artifacts, Tags, and other Groups all are considered to be part of the same cluster of activity.
Because different owners on a ThreatConnect instance may have different, unique information about a Group, Groups do not have to be unique across owners, or even within a particular owner. For example, an instance of ThreatConnect can contain multiple copies of the Intrusion Set Group APT 41 across different Organizations, Communities, and Sources or even within the same Organization, Community, or Source. This arrangement enables each owner to maintain the integrity of, and control access to, each version of a Group.
Groups may be owned by Organizations, Communities, and Sources.
Group Types
ThreatConnect has 17 Group types:
- Adversary: The Adversary Group represents an attributed malicious organization or individual identity or persona. An Adversary can be tracked by its assets (e.g., websites, email addresses, hacker monikers, social media handles, etc.) to allow for monitoring of activity. The Adversary Group is commonly used to capture the handles and aliases of threat actor personas in online forums. Examples of Adversaries include persona handles seen in dark web forums; an organization attributed to an Intrusion Set (see “Intrusion Set” later in this list), such as the Russian Foreign Intelligence Service (SVR); and individual identities attributed to malicious activity, such as Yu Pingan, who was arrested by U.S. law enforcement for developing malware used in Turbine Panda activity.
- Attack Pattern: The Attack Pattern Group represents a type of tactics, techniques, and procedures (TTP) that describes ways in which adversaries attempt to compromise targets. Historically, this Group type was used to capture MITRE ATT&CK® techniques in ThreatConnect.ImportantThe Attack Pattern Group is a legacy Group type in ThreatConnect. Its original utility has been updated and replaced by the ATT&CK Tag. We recommend that you leverage ATT&CK Tags when modeling Enterprise ATT&CK techniques and sub-techniques.
- Campaign: The Campaign Group represents a collection of related Incidents. (See “Incident” later in this list.)
- Course of Action: The Course of Action Group represents a recommendation from a producer of intelligence to a consumer on the actions that they might take in response to that intelligence.
- Document: The Document Group represents a file of interest, such as a PDF report that contains valuable intelligence or a malware sample. The contents of file attachments for Document Groups are indexed in ThreatConnect for searches (e.g., on the Search screen, when generating or updating IR results).NoteDocument attachments that have been added to the Malware Vault are not indexed for searches.
- Email: The Email Group represents an occurrence of a specific suspicious email, such as a phishing attempt.
- Event: The Event Group represents an observable occurrence of notable activity in an information system or network that may indicate a security incident. For example, an Event might be created from a SIEM alert that needs to be triaged and investigated.
- Incident: The Incident Group represents a snapshot of a particular intrusion, breach, or other event of interest.
- Intrusion Set: The Intrusion Set Group represents a set of adversarial behaviors and resources with common properties that is believed to be orchestrated by one or more Adversaries, such as a person, criminal organization, company, government, government agency, hacktivist, etc. An Intrusion Set may capture multiple Campaigns or other activities that are all tied together by shared Attributes indicating a common known or unknown Adversary or set of Adversaries. New activity can be attributed to an Intrusion Set even if the Adversaries behind the attack are not known. In practice, while it is relatively rare to observe, Adversaries can move from supporting one Intrusion Set to supporting another, or they may support multiple Intrusion Sets. Examples of Intrusion Sets include Turbine Panda (as named by CrowdsStrike®) and APT 29 (as named by Mandiant® and Google®).
- Malware: The Malware represents a malware family.
- Report: The Report Group is a generic object that can hold a collection of threat intelligence focused on one or more topics, such as a description of a threat actor, malware, or attack technique, including context and related details. It can be used to group related pieces of threat intelligence together so that they can be published as a comprehensive cyberthreat story. Reports can be used to memorialize and distribute a wide variety of threat reports, such as reports on malware families, risk reports on specific infrastructure, and even writeups on physical security. Certain file types uploaded to a Report are viewable directly on the Report File card on the Overview tab of that Report’s Details screen. The Report Group is designed to be a neutral object that is suitable for a variety of topics. This design is in contrast to that of other Groups such as Adversary and Incident, which have more specific definitions.ImportantThe Report Group object is a separate entity from the reports that you can create via the ThreatConnect reporting feature.
- Signature: The Signature Group represents an actual Signature that can be used for detection or prevention in a supported format. The following formats are currently supported: Bro, ClamAV®, CybOX™, Iris® Search Hash, Microsoft® Kusto Query Language [KQL], OpenIOC, Regex, Splunk® Search Processing Language (SPL), Sigma, Snort®, STIX™ Pattern, Suricata, ThreatConnect Query Language (TQL) Query, and YARA.NoteSystem Administrators may create custom Signature types.
- Tactic: The Tactic Group represents an action or strategy carefully planned to achieve a specific end. This Group type is typically used to capture MITRE ATT&CK tactics in ThreatConnect.
- Task: The Task Group represents an assignment given to a ThreatConnect user.ImportantThe Task Group is a legacy Group type. Its original utility has been replaced by the Workflow Task. We recommend using Workflow Tasks within Cases for managing work for your team in ThreatConnect.
- Threat: The Threat Group represents a group of related activity, whether attribution is known or not. This relation can be based on technology (e.g., Shellshock) or pertain to a grouping of activity that is presumed to be by the same selection of actors (e.g., Bitterbug).ImportantThe Threat Group is a legacy Group type in ThreatConnect. Its original utility has been replaced by the Intrusion Set, Malware, and Tool Groups. We recommend using these Groups as appropriate to maintain best practices and to simplify sharing of information within and outside of ThreatConnect.
- Tool: The Tool Group represents legitimate software that can be used by threat actors to perform attacks.
- Vulnerability: The Vulnerability Group represents a mistake in software that can be directly used by a hacker to gain access to a system or network.
Viewing Groups
Follow these steps to view a table listing all Groups in your ThreatConnect owners:
- Click Search
 on the top navigation bar.
on the top navigation bar. - Select the Groups filter on the left sidebar of the Search screen.
Use the Search name/summary, Advanced Search, Group Type, and Filters options to filter the results set to specific Groups or by Group type, owner, or other features. To view more information on a particular Group, click its entry in the Name/Summary column to navigate to its Details screen. The Overview tab of a Group’s Details screen contains cards displaying information about the Group, such as Security Labels and Attributes. A Group’s Details screen also includes tabs providing information on the Group’s associations and user activity involving the Group and allowing you to copy the Group to another owner.
options to filter the results set to specific Groups or by Group type, owner, or other features. To view more information on a particular Group, click its entry in the Name/Summary column to navigate to its Details screen. The Overview tab of a Group’s Details screen contains cards displaying information about the Group, such as Security Labels and Attributes. A Group’s Details screen also includes tabs providing information on the Group’s associations and user activity involving the Group and allowing you to copy the Group to another owner.
Victims
A Victim represents a specific organization or group that has been targeted or whose assets (e.g., accounts, infrastructure, equipment) have been exploited.
Victims may be owned by Organizations, Communities, and Sources.
Viewing Victims
Follow these steps to view a table listing all Victims in your ThreatConnect owners:
- Click Search
 on the top navigation bar.
on the top navigation bar. - Select the Victims filter on the left sidebar of the Search screen.
Use the Search name/summary, Advanced Search, and Filters options to filter the results set to specific Victims or by owner or other features. To view more information on a particular Victim, click its entry in the Name/Summary column to navigate to its Details screen. The Overview tab of a Victim’s Details screen contains cards displaying information about the Victim, such as Security Labels and Attributes. A Victim’s Details screen also includes tabs providing information on the Victim’s associations and user activity involving the Victim.
options to filter the results set to specific Victims or by owner or other features. To view more information on a particular Victim, click its entry in the Name/Summary column to navigate to its Details screen. The Overview tab of a Victim’s Details screen contains cards displaying information about the Victim, such as Security Labels and Attributes. A Victim’s Details screen also includes tabs providing information on the Victim’s associations and user activity involving the Victim.
Victim Assets
Victim Assets are added to a Victim to represent exploited assets. The following types of Victim Assets are available in ThreatConnect:
- Email address
- Social network account
- Network account
- Website
- Phone number
Victim Assets do not have an owner themselves, but the Victims to which they are added may be owned by Organizations, Communities, and Sources.
Viewing Victim Assets
Follow these steps to view a table listing all Victim Assets in your ThreatConnect owners:
- Click Search
 on the top navigation bar.
on the top navigation bar. - Select the Victim Assets filter on the left sidebar of the Search screen.
Use the Search name/summary, Advanced Search, Assets Type, and Filters options to filter the results set to specific Victim Assets or by owner, Asset type, or other features. To view more information on a particular Victim Asset, click in its row to view its Details drawer. The Details screen is not available for Victim Assets. However, you can view more information on a Victim Assets on the Assets tab of the Details screen for the Victim to which the Victim Asset belongs.
options to filter the results set to specific Victim Assets or by owner, Asset type, or other features. To view more information on a particular Victim Asset, click in its row to view its Details drawer. The Details screen is not available for Victim Assets. However, you can view more information on a Victim Assets on the Assets tab of the Details screen for the Victim to which the Victim Asset belongs.
Intelligence Requirements
An Intelligence Requirement (IR) represents a collection of topics or a research question reflecting an organization’s cyber threat–related priorities that guides a security or threat intelligence team’s research and analysis efforts.
IRs may be owned only by Organizations.
Intelligence Requirement Subtypes
IRs in ThreatConnect are classified in five subtypes:
- Intelligence Requirement (IR): This subtype represents threats of overall concern to an organization (e.g., cyber threats, fraud, geopolitical/physical threats).
- Priority Intelligence Requirement (PIR): This subtype represents threat actor motives; TTPs; targets; impacts; or attributions in association with IRs.
- Specific Intelligence Requirement (SIR): This subtype represents facts associated with threat activity, such as indicators of compromise (IOCs).
- Request for Information (RFI): This subtype represents one-off requests for information related to topics of interest to particular stakeholders.
- Research Requirement (RR): This subtype represents a topic or area of investigation that is of interest to an individual or group and does not merit a full intelligence requirement, but does require tracking of relevant information
Viewing Intelligence Requirements
Follow these steps to view a table listing all IRs in your Organization:
- Click Search
 on the top navigation bar.
on the top navigation bar. - Select the Intelligence Requirements filter on the left sidebar of the Search screen.
Use the Search requirement or ID…, Advanced Search, and Filters options to filter the results set to specific IRs or by subtype, category, or other features. To view more information on a particular IR, click its entry in the Requirement column to navigate to its Details screen. The Overview tab of an IR’s Details screen contains cards displaying information about the IR, including its subtype, category, keyword query, and results returned from its keyword query. An IR’s Details screen also includes a tab that provides information on the IR’s associations.
options to filter the results set to specific IRs or by subtype, category, or other features. To view more information on a particular IR, click its entry in the Requirement column to navigate to its Details screen. The Overview tab of an IR’s Details screen contains cards displaying information about the IR, including its subtype, category, keyword query, and results returned from its keyword query. An IR’s Details screen also includes a tab that provides information on the IR’s associations.
Workflow Cases
The Workflow feature in ThreatConnect supports case management, enabling you to define and operationalize consistent, standardized processes for investigating, tracking, and taking action on information security threats and incidents. The primary object in the Workflow feature in which work is done is a Case: a single instance of an investigation, query, or other procedure in your Organization.
Workflow Cases may be owned only by Organizations.
Viewing Cases
Hover over Workflow on the top navigation bar and select Cases, or just click Workflow, to view all Cases in your Organization. Use the filter and search options to filter the results set to specific cases or by severity, resolution, assignee, or other features. To view more information on a particular Case, click the Case’s card (in grid view) or entry in the table (in table view). The screen for the Case displays sections and cards with information about the Case, including the Phases and Tasks that determine the actions to be taken during the Case’s procedure, information on the Case’s associations, the Case’s Artifacts, and a timeline showing all events and changes that have taken place in the Case.
Artifacts
An Artifact is a piece of data representing information in a Workflow Case that may be useful to an analyst. Artifacts can be mapped to ThreatConnect Indicators if they are identical objects. For example, the Artifact bad.com maps to the Host Indicator type in ThreatConnect. These mappings can help you connect information gathered during a Case with Indicators in your ThreatConnect owners.
Artifacts do not have an owner themselves, but the Cases to which they belong may be owned only by Organizations.
Viewing Artifacts
Expand the Artifacts card when viewing a Workflow Case in your Organization to view a table listing all Artifacts in that Case. Use the filter and search options at the top of the card to filter the results set to specific Artifacts or by type, status, or other features. To view more information on a particular Artifact, such as CAL score and associated objects, expand its entry in the table.
Tags
A Tag is a metadata object that you can apply to Indicators, Groups, Victims, IRs, and Cases. A Tag provides a quick and easy way to view categorical information about an object, as well as creates a path from one object to another via its association with each object. Tags in ThreatConnect come in two “flavors”: standard Tags and ATT&CK Tags.
Standard Tags may be owned by Organizations, Communities, and Sources. ATT&CK Tags do not have an owner.
Viewing Tags
Follow these steps to view a table listing all Tags in your ThreatConnect owners, as well as all ATT&CK Tags:
- Click Search
 on the top navigation bar.
on the top navigation bar. - Select the Tags filter on the left sidebar of the Search screen.
Use the Search name/summary or ID…, Advanced Search, Tag Type, and Filters options to filter the results set to specific Tags or by Tag type, owner, or other features. To view more information on a particular Tag, click its entry in the Name/Summary column to navigate to its Details screen. The Overview tab of a Tag’s Details screen contains cards displaying information about the Tag, such as synonymous Tags. A Tag’s Details screen also includes tabs providing information on the Tag’s associations and user activity involving the Tag.
options to filter the results set to specific Tags or by Tag type, owner, or other features. To view more information on a particular Tag, click its entry in the Name/Summary column to navigate to its Details screen. The Overview tab of a Tag’s Details screen contains cards displaying information about the Tag, such as synonymous Tags. A Tag’s Details screen also includes tabs providing information on the Tag’s associations and user activity involving the Tag.
You can view Tags applied to Indicators, Groups, Victims, and IRs on those objects’ Details screen. You can view Tags applied to a Case on its Case Details card.
Associations
An association is a connection between two data objects. Associations allow you to model, discover, and create correlations and relationships between data objects in the ThreatConnect data model. You can explore and create associations visually in Threat Graph, in list format on the Associations tab of the Details screen, on the Associations card and Associations tab of the legacy Details screen, and on a Case’s Associations card.
Data objects can be associated with each other in the following ways in ThreatConnect:
- Indicators can be associated with Groups, Victim Assets, IRs, Cases, Artifacts, and other Indicators.NoteIndicators are associated with Victim Assets indirectly, through a mutual association to a Group.
- Groups can be associated with Indicators, Victim Assets, IRs, Cases, Artifacts, and other Groups.
- Victim Assets can be associated with Indicators, Groups, and IRs.NoteVictim Assets are associated with Indicators indirectly, through a mutual association to a Group.
- IRs can be associated with Indicators, Groups, Victim Assets, Cases, and Artifacts.
- Cases can be associated with Indicators, Groups, IRs, and other Cases.NoteArtifacts are parts of a Case. This relationship is not treated as an association in ThreatConnect.
- Artifacts can be associated with Indicators, Groups, and IRs.NoteArtifacts are parts of a Case. This relationship is not treated as an association in ThreatConnect.
- Tags can be applied to Indicators, Groups, Victims, IRs, and Cases. This relationship is not an actual association in ThreatConnect, but it can be modeled as one in Threat Graph.
ThreatConnect Data Model Example
Figure 1 shows an example of the ThreatConnect data model, illustrating a set of Groups (Adversary, Campaign, Incident, Intrusion Set, and Signature) and Indicators (Address, Email Address, File, and Host) connected to each other in various ways by associations.
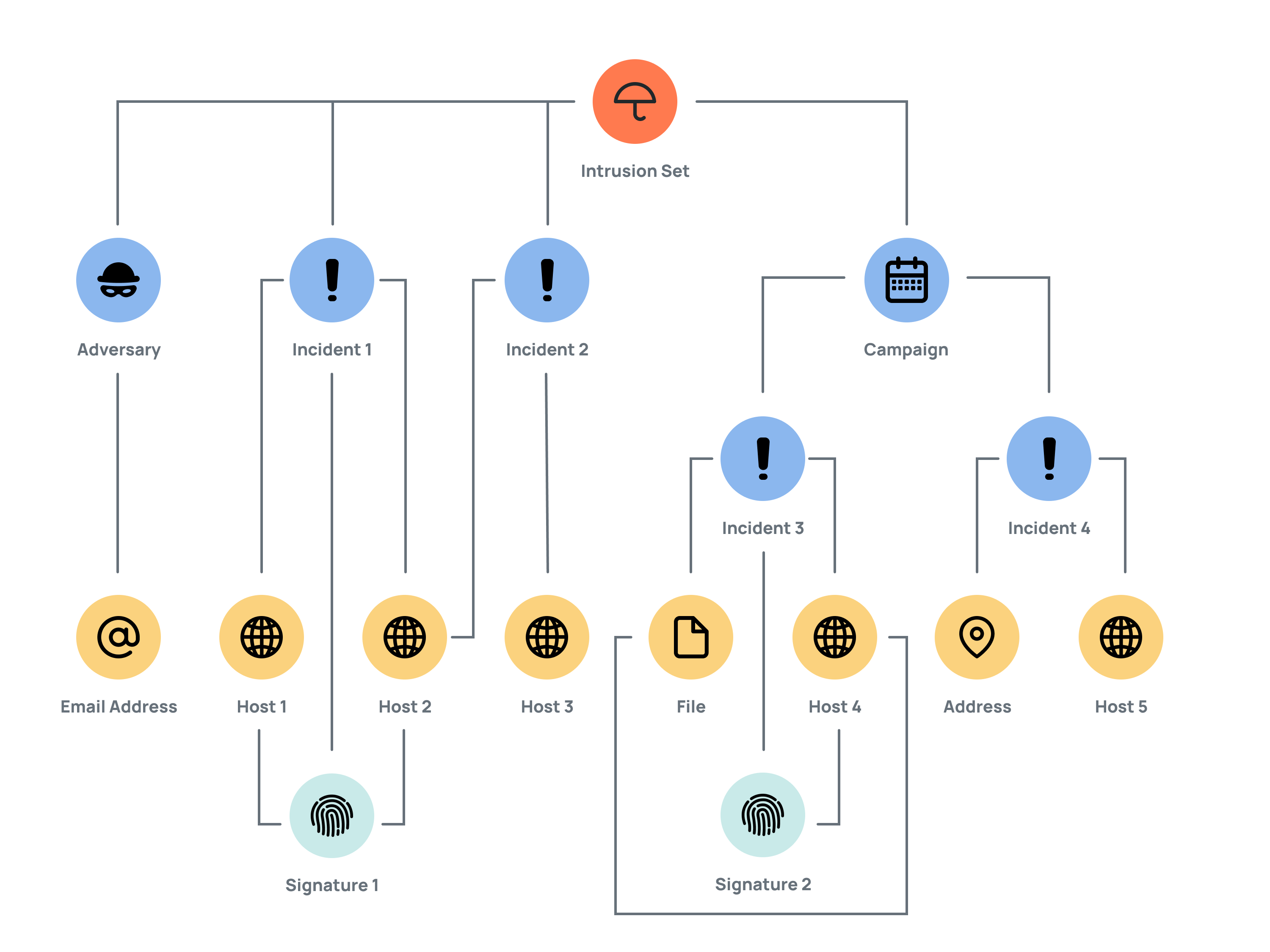
In this example, an Intrusion Set Group identified as an overseas hacking unit is associated with the following Group objects, each of which has a connection to at least one Indicator object:
- Adversary: This Group object is a malicious actor. It has ties to an Email Address Indicator listed as the Start of Authority (SOA) record for domains used by the Intrusion Set.
- Incident 1: Open-source reporting in a cybersecurity-industry blog provided details about some of the Intrusion Set’s activity, represented by Incident 1. In particular, the report identified a domain, Host 1, and the Internet provider that hosts it, Host 2, both of which have been used by the Intrusion Set’s infrastructure and are associated with Incident 1. Snort Signature 1, used to detect network indicators, is associated with Host 1 and Host 2 through their rules, as well as to Incident 1.
- Incident 2: The cybersecurity-industry blog also identified a new series of phishing attacks from the Intrusion Set targeting foreign journalists, politicians, and activists. These attacks, represented by Incident 2, are focused on stealing email-account details of the victims and finding information about their contacts and networks. Host 2 and Host 3, identified as having been used by the Intrusion Set’s infrastructure, are associated with Incident 2.
- Campaign: This effort targets foreign organizations involved in the technology, government, and energy sectors. It is directly tied to the Intrusion Set. Through Incident 3, ThreatConnect identified a malicious File that is likely the Campaign's malware, which, when executed, connects to Host 4. Snort Signature 2, which is used to detect network Indicators, is associated with Incident 3 and, through its Snort rules, to Host 4. In Incident 4, over 50 samples of the tools used by the Campaign were collected. These tools included Internet Relay Chat (IRC) bots, an open-source Python® remote-access tool, malicious macros, and others. In particular, Incident 4 collected an Address the Campaign uses as its command-and-control IP address and a Host (Host 5) as its command-and-control domain.
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
ClamAV® and Snort® are registered trademarks of Cisco Systems, Inc.
CrowdStrike® is a registered trademark of CrowdStrike, Inc.
Google® is a registered trademark of Google LLC.
MITRE ATT&CK® and ATT&CK® are registered trademarks, and CybOX™ and STIX™ are trademarks, of The MITRE Corporation.
Iris® is a registered trademark of DomainTools, LLC.
Microsoft® and Windows® are registered trademarks of Microsoft Corporation.
Python® is a registered trademark of Python Software Foundation.
Splunk® is a registered trademark of Splunk, Inc.
20027-01 v.17.A


