- 21 May 2025
- 8 Minutes to read
-
Print
-
DarkLight
-
PDF
CAL Classifiers
- Updated on 21 May 2025
- 8 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
CAL™ provides anonymized, crowdsourced intelligence derived from global data for Indicators across all participating instances of ThreatConnect®, as well as in Polarity when using the ThreatConnect CAL integration with Polarity. CAL Classifiers are a set of labels applied by CAL to Indicators to represent predefined categorizations derived from CAL’s classification analytics and statistical models. They provide you with a standardized vocabulary for understanding key data points about an Indicator. CAL Classifiers are available for the following Indicator types: Address, ASN, CIDR, Email Address, File, Host, and URL.
Before You Start
User Roles
- To view CAL Classifiers for Indicators in your Organization, your user account can have any Organization role.
- To view CAL Classifiers for Indicators in a Community or Source, your user account can have any Community role except Banned for that Community or Source.
Prerequisites
- To view CAL enrichment information for Indicators in your ThreatConnect owners, enable CAL for your ThreatConnect instance and in your Organization:
- To enable CAL for your ThreatConnect instance, select the CALEnabled checkbox on the Settings tab of the System Settings screen (must be a System Administrator to perform this action).
- To enable CAL in your Organization, edit your Organization on the Organizations tab of the Account Settings screen and select the Enable CAL Data checkbox on the Permissions tab of the Organization Information window (must be a System Administrator, Operations Administrator, or Accounts Administrator to perform this action).
- Verify that your ThreatConnect instance can receive data from cal.threatconnect.com (if using an On Premises instance).
Viewing CAL Classifiers
An Indicator’s CAL Classifiers are displayed on the Indicator’s Details drawer (Figure 1), the Details card on the Overview tab of the Indicator’s Details screen (Figure 2), and the Indicator Analytics card on the Overview tab of the Indicator’s legacy Details screen (Figure 3).
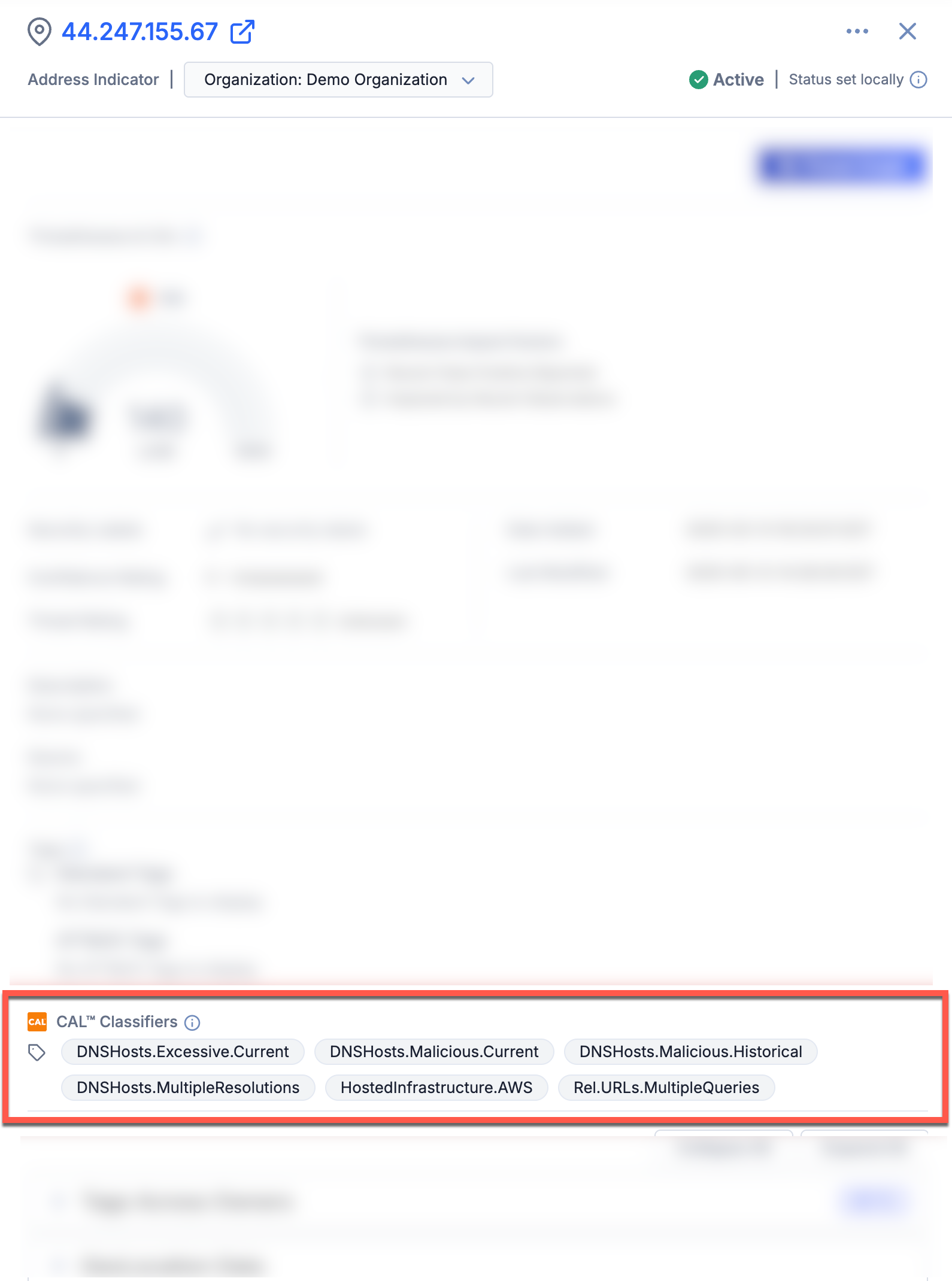
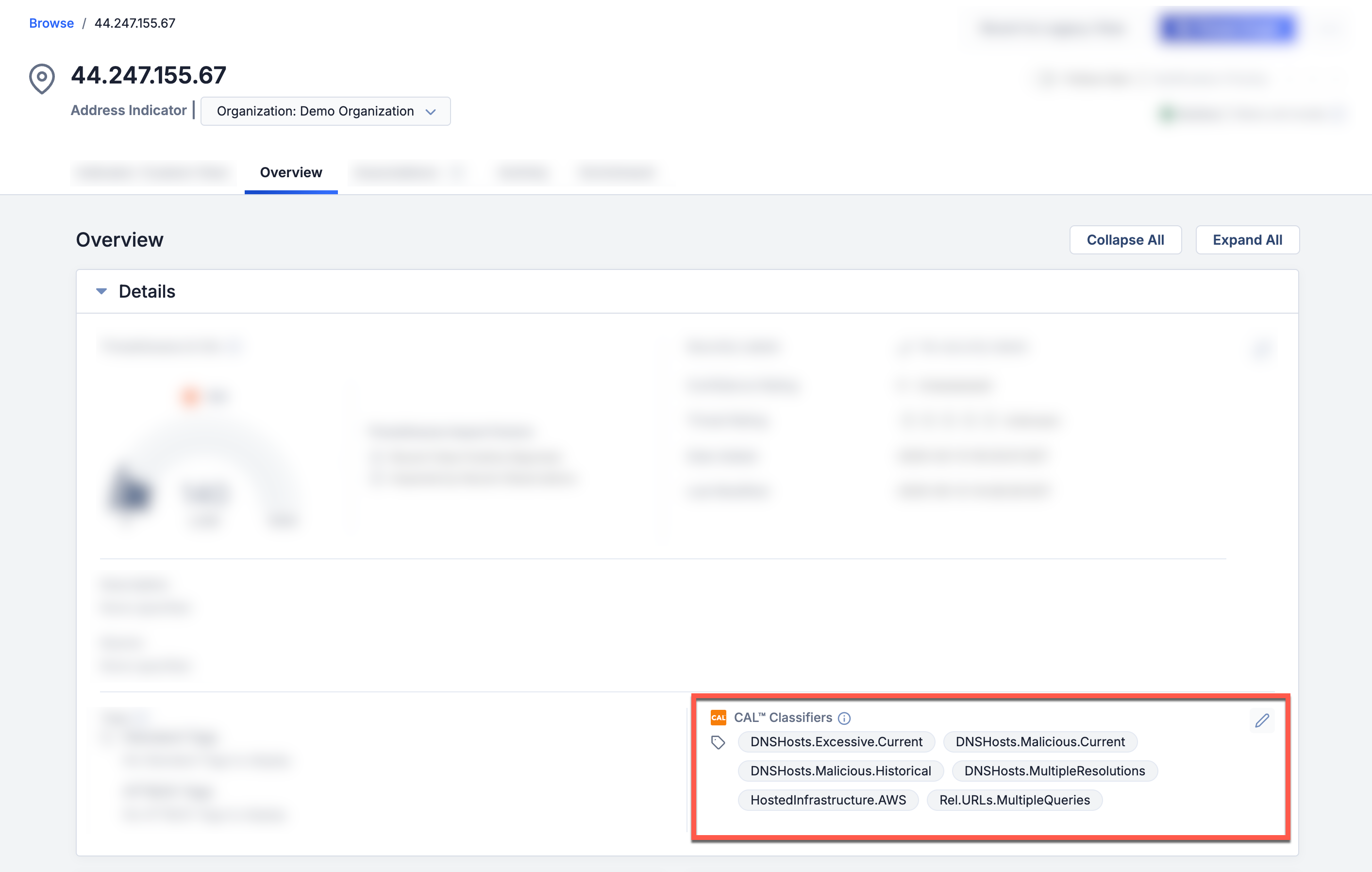
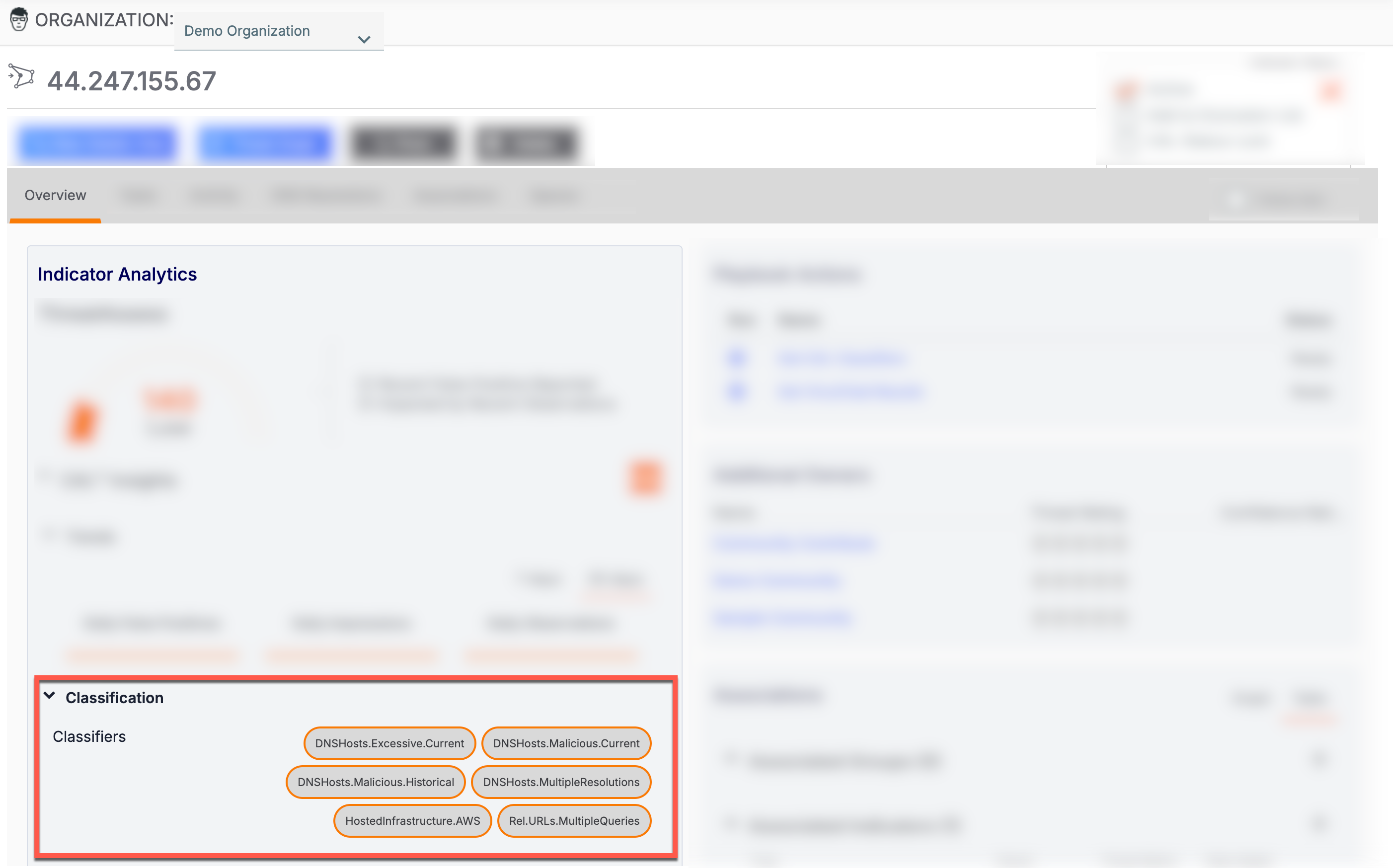
CAL Classifiers Glossary
| CAL Classifier | Valid Indicator Types | Description |
|---|---|---|
| Active Host | Host | Host has a sufficient number of reported observations from ThreatConnect users within the allotted timeframe. |
| ASN.Invalid | ASN | ASN does not exist, according to the master list of ASN:CIDR mappings. |
| CloudHosted | URL | URL is hosted on a common cloud-hosting domain (e.g., amazonaws.com). |
| DNSHosts.Excessive.Current | Address | Address has an excessive number (3+) of hosts concurrently resolving to it. |
| DNSHosts.HistoricalResolutions | Address | Address has had hosts historically resolve to it, but currently no tracked hosts do. |
| DNSHosts.Malicious.Current | Address | Address has a sufficiently evil host that currently resolves to it. |
| DNSHosts.Malicious.Historical | Address | Address has had a sufficiently evil host resolve to it in the last 30 days, but not currently. |
| DNSHosts.MultipleResolutions | Address | Address has 2+ hosts currently resolving to it. |
| DNSRes.Excessive.Current | Host | Host currently resolves to an excessive number (5+) of concurrent IP addresses. |
| DNSRes.Excessive.Historical | Host | Host has resolved to an excessive number (5+) of concurrent IP addresses in the last 7 days, but does not currently resolve to an excessive number of concurrent IP addresses. |
| DNSRes.Malicious.Current | Host | Host resolves to an IP address that, as of the current day, is sufficiently evil. |
| DNSRes.Malicious.Historical | Host | Host resolved in the last 30 days to an IP address that, as of the current day, is sufficiently evil, but does not currently resolve to this IP address. |
| DNSRes.MultipleResolutions | Host | Host currently resolves to 2+ IP addresses. |
| DNSRes.NoResolution | Host | Host does not currently resolve to any IP address. |
| DNSRes.Parked | Host | Host resolves to a currently known-good IP address. |
| DNSRes.RecentlyUnparked | Host | Host resolved to a known-good IP address in the last 7 days, but no longer does. |
| Email.CommonDomain | EmailAddress | Email Address comes from a list of very common/popular email hosting services (e.g., @google.com). |
| Email.Disposable | EmailAddress | Email Address uses an email provider known to be disposable (e.g., badguy@mailinator.com). |
| Executable.Android | File | File hash is known to represent an Android™ executable. |
| Executable.iOS | File | File hash is known to represent an iOS™ executable. |
| Executable.Legacy | File | File hash is known to represent a legacy (pre-2000) executable. |
| Executable.Modern | File | File hash is known to represent a modern-architecture (later than the year 2000) executable. |
| ExternalUsage.<platform>.Historical | Address, ASN, Email Address, Host, URL | Indicator has documented historical usage attributed from the ThreatConnect Intelligence Source. |
| FileType.<platform>.<subplatform> | File | The File’s reputed type, platform, and subplatform. |
| Host.DGA.Suspected | Host | Host may have been generated by a domain generation algorithm (DGA), a tactic frequently employed by malicious actors to create multiple domains to leverage during cyber attacks. This label can be applied via machine learning or through association with a source providing DGA indicators. |
| Host.DynamicDNS | Host, URL | Indicator (or its domain) includes a known dynamic DNS provider (e.g., no-ip.com). |
| Host.ExcessiveLength | Host | Host has at least 50 characters. |
| Host.LoginFraud | Host | Host includes text similar to common websites (e.g., paypal), along with keywords of interest (e.g., auth, login, secure). |
| Host.RecentlyRegistered.30D | Host | Host was registered within the last 30 days. |
| Host.RecentlyRegistered.7D | Host | Host was registered within the last 7 days. |
| Host.Spoofing | URL | URL contains strings indicative of a spoof attempt (e.g., .com-). |
| Host.Unicode | Host, URL | Indicator contains Unicode characters in the domain name, signified by xn--. |
| Host.WHOIS.Expired | Host | Host’s most recent WHOIS registration has expired. |
| Host.WHOIS.LongRegistration | Host | Host’s most recent WHOIS registration was for at least 5 years. |
| Host.WHOIS.ShortRegistration | Host | Host’s most recent WHOIS registration was for less than 6 months. |
| HostedInfrastructure.AWS | Address, Host, URL | Host or URL is related to, or Address belongs to, a known Amazon Web Services® (AWS) CIDR block. |
| HostedInfrastructure.Cloudflare | Address, Host, URL | Host or URL is related to, or Address belongs to, a known Cloudflare® CIDR block. |
| HostedInfrastructure.Facebook | Address, Host, URL | Host or URL is related to, or Address belongs to, a known Facebook™ CIDR block. |
| HostedInfrastructure.Google | Address, Host, URL | Host or URL is related to, or Address belongs to, a known Google® CIDR block. |
| HostedInfrastructure.MaxCDN | Address, Host, URL | Host or URL is related to, or Address belongs to, a known MaxCDN (legacy service owned by Akamai®) CIDR block. |
| HostedInfrastructure.Microsoft | Address, Host, URL | Host or URL is related to, or Address belongs to, a known Microsoft® CIDR block. |
| HostedInfrastructure.Twitter | Address, Host, URL | Host or URL is related to, or Address belongs to, a known X™ (formerly Twitter®) CIDR block. |
| IntrusionPhase.<value>.Current | Address, Email Address, File, Host, URL | Indicator has a documented Intrusion Phase (e.g., C2) Attribute from the ThreatConnect Intelligence Source within allotted timeframe (by Indicator type). |
| IntrusionPhase.<value>.Historical | Address, Email Address, File, Host, URL | Indicator has a documented Intrusion Phase (e.g., C2) Attribute from the ThreatConnect Intelligence Source outside allotted timeframe (by Indicator type). |
| LikelyPythonScript | Host | Host appears to be a mislabeled Python® file rather than a legitimate Host. |
| Malware.<type> | File | File has reputation with a specific type of malware. |
| MultipleSuspiciousURLs | Host | Host has 2 or more suspicious URLs associated with it. |
| Observations.High | Address, Email Address, File, Host, URL | Indicator has a high number of observations for its type. |
| Observations.Low | Address, Email, File, Host, URL | Indicator has a low number of observations for its type. |
| Observations.Med | Address, Email Address, File, Host, URL | Indicator has a moderate number of observations for its type. |
| PrivateNetwork | Address | Address belongs to a netblock known as a private address space (e.g., 192.168.0.0/16). |
| ProxyRegistration | Email Address | Email Address uses an email provider that provides proxy registration (e.g., badguy@domainsbyproxy.com). |
| Quad9.Geo.Recent.<country name> | Host | Quad9® Host with a country label has been last seen by CAL within last 7 days. |
| Quad9.Geo.Historical.<country name> | Host | Quad9 Host with a country label was last seen by CAL prior to the last 7 days. |
| Quad9.HighVolume.30D | Host | Host has seen significant DNS lookups through Quad9 in the last 30 days. |
| Quad9.HighVolume.7D | Host | Host has seen significant DNS lookups through Quad9 in the last 7 days. |
| Quad9.RecentLookups.30D | Host | Host has been actively resolved through Quad9 DNS in the last 30 days. |
| Quad9.RecentLookups.7D | Host | Host has been actively resolved through Quad9 DNS in the last 7 days. |
| Rank.CiscoUmbrella.Top1M | Host | Host is in Cisco Umbrella™’s Top 1 Million domain list, in the 100,001–1,000,000 spot. |
| Rank.CiscoUmbrella.Top100K | Host | Host is in Cisco Umbrella’s Top 1 Million domain list, in the 10,001–100,000 spot. |
| Rank.CiscoUmbrella.Top10K | Host | Host is in Cisco Umbrella’s Top 1 Million domain list, in the 1,001–10,000 spot. |
| Rank.CiscoUmbrella.Top1K | Host | Host is in Cisco Umbrella’s Top 1 Million domain list, in the 101–1,000 spot. |
| Rank.CiscoUmbrella.Top100 | Host | Host is in Cisco Umbrella’s Top 1 Million domain list, in the 1–100 spot. |
| Rank.Majestic.Top1M | Host | Host is in Majestic’s Top 1 Million domain list, in the 100,001–1,000,000 spot. |
| Rank.Majestic.Top100K | Host | Host is in Majestic’s Top 1 Million domain list, in the 10,001–100,000 spot. |
| Rank.Majestic.Top10K | Host | Host is in Majestic’s Top 1 Million domain list, in the 1,001–10,000 spot. |
| Rank.Majestic.Top1K | Host | Host is in Majestic’s Top 1 Million domain list, in the 101–1,000 spot. |
| Rank.Majestic.Top100 | Host | Host is in Majestic’s Top 1 Million domain list, in the 1–100 spot. |
| Rank.Tranco.Top1M | Host | Host is in Tranco’s Top 1 Million domain list, in the 100,001–1,000,000 spot. |
| Rank.Tranco.Top100K | Host | Host is in Tranco’s Top 1 Million domain list, in the 10,001–100,000 spot. |
| Rank.Tranco.Top10K | Host | Host is in Tranco’s Top 1 Million domain list, in the 1,001–10,000 spot. |
| Rank.Tranco.Top1K | Host | Host is in Tranco’s Top 1 Million domain list, in the 101–1,000 spot. |
| Rank.Tranco.Top100 | Host | Host is in Tranco’s Top 1 Million domain list, in the 1–100 spot. |
| Rel.Addresses.Malicious | CIDR, ASN | ASN address provider or CIDR range has a high number of malicious IP addresses. |
| Rel.EmailAddresses.Suspicious | Host | Host has a sufficient number of related email addresses that are sufficiently evil. |
| Rel.Host.KnownGood | URL | URL is related to a known-good host. |
| Rel.Host.Suspicious | Email Address | Email Address has an email provider host that is known to be sufficiently evil. |
| Rel.Hosts.Malicious | CIDR | A high number of malicious hosts currently resolve within this CIDR range. |
| Rel.NSClients.Malicious | Host | Host is currently being used as a nameserver by a high proportion of malicious hosts. |
| Rel.NSClients.Suspicious | Host | Host is currently being used as a nameserver by a substantial number of suspicious hosts. |
| Rel.Subdomains.Suspicious | Host | Host has a sufficient number of subdomains that are sufficiently evil. |
| Rel.URL.Suspicious | Host | Host is associated with at least one suspicious URL. |
| Rel.URLs.Malicious | CIDR | A high number of malicious URLs currently resolve within this CIDR range. |
| Rel.URLs.MultipleQueries | Address | Address has recently been observed hosting a large number of URLs that have multiple queries. |
| Status.Safelist | Address, ASN, Email Address, Host, URL | Indicator is on the CAL Safelist, a manually curated list maintained for the ThreatConnect community. |
| Status.Sinkholed | Host | Host is currently believed to be sinkholed, based on its nameserver. |
| Subdomains.HighCount | Host | Host has at least 4 subdomains (regex implementation with known flaw—e.g., .co.uk). |
| Suspicious.ExcessiveSubdomains | Host | Host has at least 4 subdomains [excluding multilevel top-level domains (TLDs) such as .co.uk]. |
| TLD.AlternativeDNS | Host | Host has a TLD from a list of alternative DNS providers. |
| TLD.DarkWeb | Host, URL | Indicator (or its domain) ends in .onion. |
| TLD.Invalid | Host | Host does not have a valid TLD from the public suffix list. |
| TLD.Risky | Host, URL | Indicator uses a TLD that is considered risky (e.g., bad.ru). |
| TLD.Uncommon | Host | Host does not contain the “common” TLD flags, such as .com, .net, etc. |
| TorExitNode | Address | Address comes from the Tor Exit Nodes feed. |
| Trending.Impressions | Address, Email Address, File, Host, URL, ASN, CIDR | Indicator has a sufficient number of impressions in the last day or week. |
| Trending.Observations | Address, Email Address, File, Host, URL, ASN, CIDR | Indicator has a sufficient number of observations in the last week. |
| URLShortener | URL | URL uses a domain associated with URL shortening services. |
| Usage.<value>.Current | Address, Host, URL | Indicator has a documented Usage (e.g., VulnerabilityScan) Attribute from the ThreatConnect Intelligence Source within allotted timeframe (by Indicator type). |
| Usage.<value>.Historical | Address, Host, URL | Indicator has a documented Usage (e.g., VulnerabilityScan) Attribute from the ThreatConnect Intelligence Source outside allotted timeframe (by Indicator type). |
| Usage.CDN | Address | Address has been reported by an external feed as serving content delivery network (CDN) functions. |
| Usage.DedicatedServer.Suspected | Address, Host, URL | Based on ThreatConnect’s observations, Address is known to host only one domain, or Host or URL is known to have only one IP address. |
| Usage.DNS | Address | Address has been reported by an external feed as serving DNS functions. |
| Usage.Nameserver.Boutique | Host | Host is currently being observed as a nameserver by only a small number of host clients. |
| Usage.Nameserver.Common | Host | Host is currently being used as a nameserver by a high number of other hosts and is likely to be benign. |
| Usage.Nameserver.Current | Host | Host is currently being used as a nameserver by other hosts. |
| Usage.Nameserver.SelfRef | Host | Host is currently using itself as a nameserver. |
| Usage.Sinkhole | Host | Host is suspected to be operating as a sinkhole by its owner. |
| WebExtension.Executable | URL | URL ends in a suffix implying an executable file. |
ThreatConnect® is a registered trademark, and CAL™ is a trademark, of ThreatConnect, Inc.
Akamai® is a registered trademark of Akamai Technologies, Inc.
Amazon Web Services® is a registered trademark of Amazon Web Services, Inc.
Cisco Umbrella™ and iOS™ are trademarks of Cisco Systems, Inc.
Cloudflare® is a registered trademark of Cloudflare, Inc.
Google® is a registered trademark, and Android™ is a trademark, of Google LLC.
Facebook™ is a trademark of Meta Platforms, Inc.
Microsoft® is a registered trademark of Microsoft Corporation.
Python® is a registered trademark of Python Software Foundation.
Quad9® is a registered trademark of Quad9 Foundation.
Twitter® is a registered trademark of Twitter, Inc.
X™ is a trademark of X Corp.
20094-01 v.04.A


