- 10 Sep 2025
- 7 Minutes to read
-
Print
-
DarkLight
-
PDF
Search Results (Legacy)
- Updated on 10 Sep 2025
- 7 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
After you run a search from the Search drawer in ThreatConnect®, the legacy search engine returns a list of Indicators, Groups, Tags, Victims, Workflow Cases, and Artifacts that meet either of the following conditions:
- Exact match: The object’s summary was an exact match to the search query or, for Indicators only, a pattern for a ThreatConnect Indicator type.
- Potential match: A piece of the object’s metadata (i.e., an Attribute, a Case Note, a Task, or the contents of a document upload) matched the search query.
When viewing search results on the Search drawer, you may also identify, create, and explore new Indicators that do not yet exist in one of your ThreatConnect owners.
Before You Start
User Roles
- To view search results that are Indicators, Groups, Tags, or Victims in an Organization, your user account can have any Organization role.
- To view search results that are Indicators, Groups, Tags, or Victims in a Community or Source, your user account can have any Community role except Banned for that Community or Source.
- To view search results that are Cases or Artifacts in an Organization, your user account can have any Organization role except App Developer.
- To create Indicators in an Organization, your user account must have an Organization role of Standard User, Sharing User, Organization Administrator, or App Developer.
- To create Indicators in a Community or Source, your user account must have a Community role of Contributor, Editor, or Director for that Community or Source.
Prerequisites
- To search for potential matches in ThreatConnect when using the Search drawer, turn on and configure OpenSearch® and initialize the search index for your ThreatConnect instance via the System Settings screen (must be a System Administrator to perform this action).
Viewing Search Results
Exact Matches
Results that are an identical match to a term you entered into the search bar will be displayed in the Exact Matches section, which displays two types of results:
- Indicators, Groups, Tags, Victims, Workflow Cases, and Artifacts that exist in one of your ThreatConnect owners.
- Indicators that do not yet exist in one of your ThreatConnect owners, but match a pattern for a ThreatConnect Indicator type.
Viewing Exact Matches
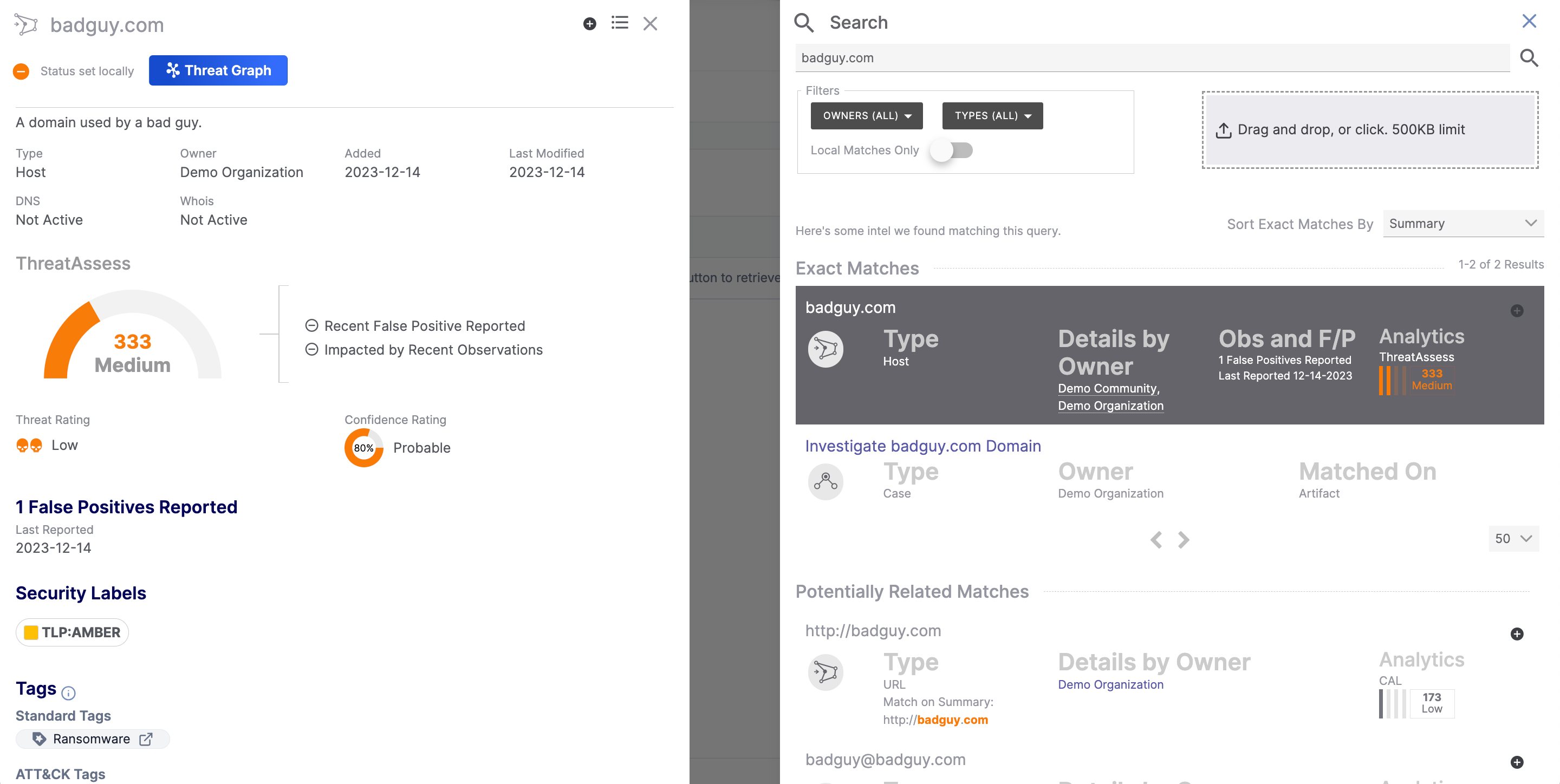
Figure 1 shows the results of a search for badguy.com.
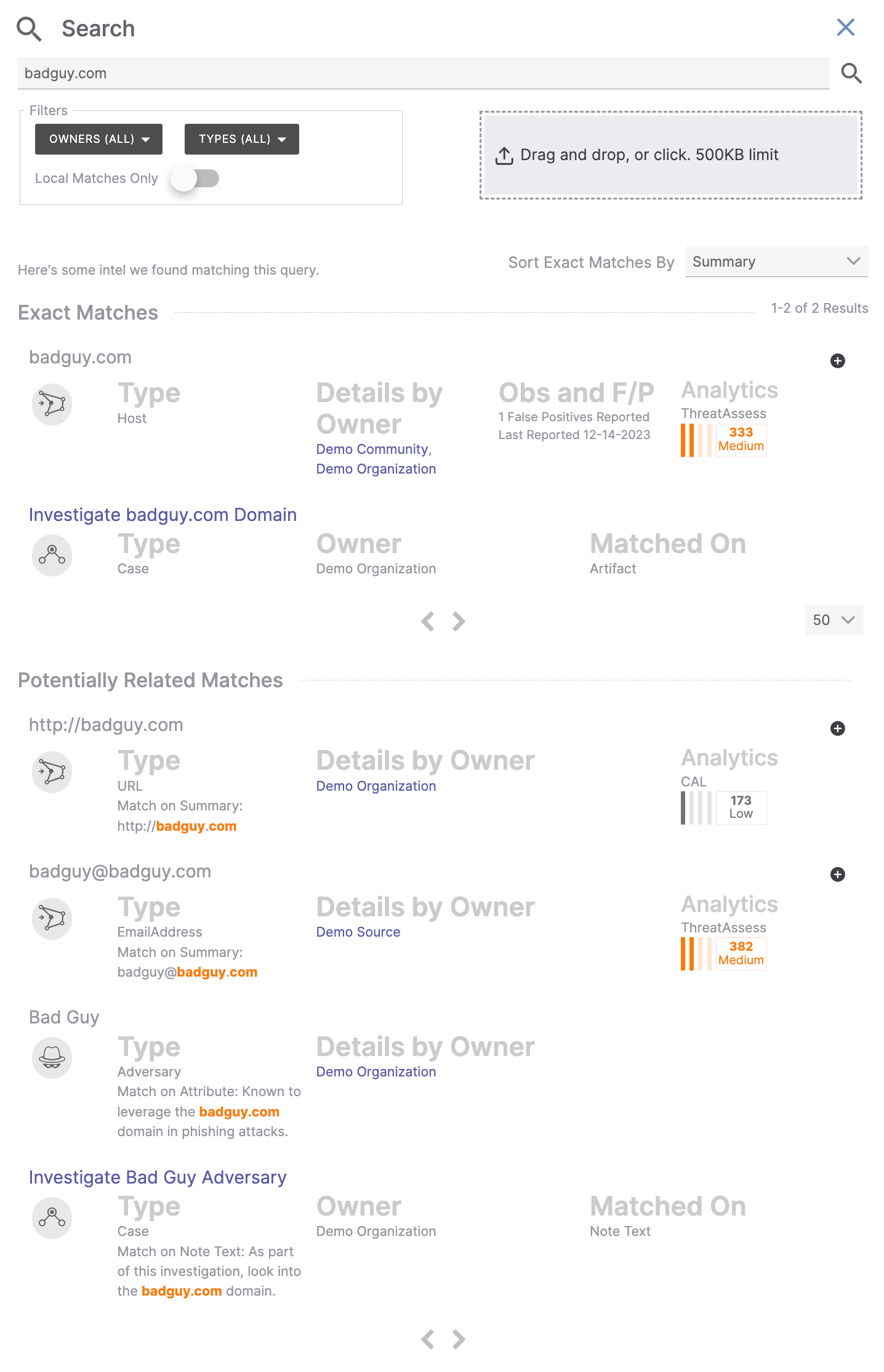
This search resulted in two exact matches: one to an Artifact in a Case that exists in the user’s Organization and another to a Host Indicator that exists in the user’s Organization and one of their Communities. For Indicators, information on observations/false positives and analytical information from ThreatAssess or CAL™ (if ThreatAssess data do not exist for the Indicator) are also provided if available.
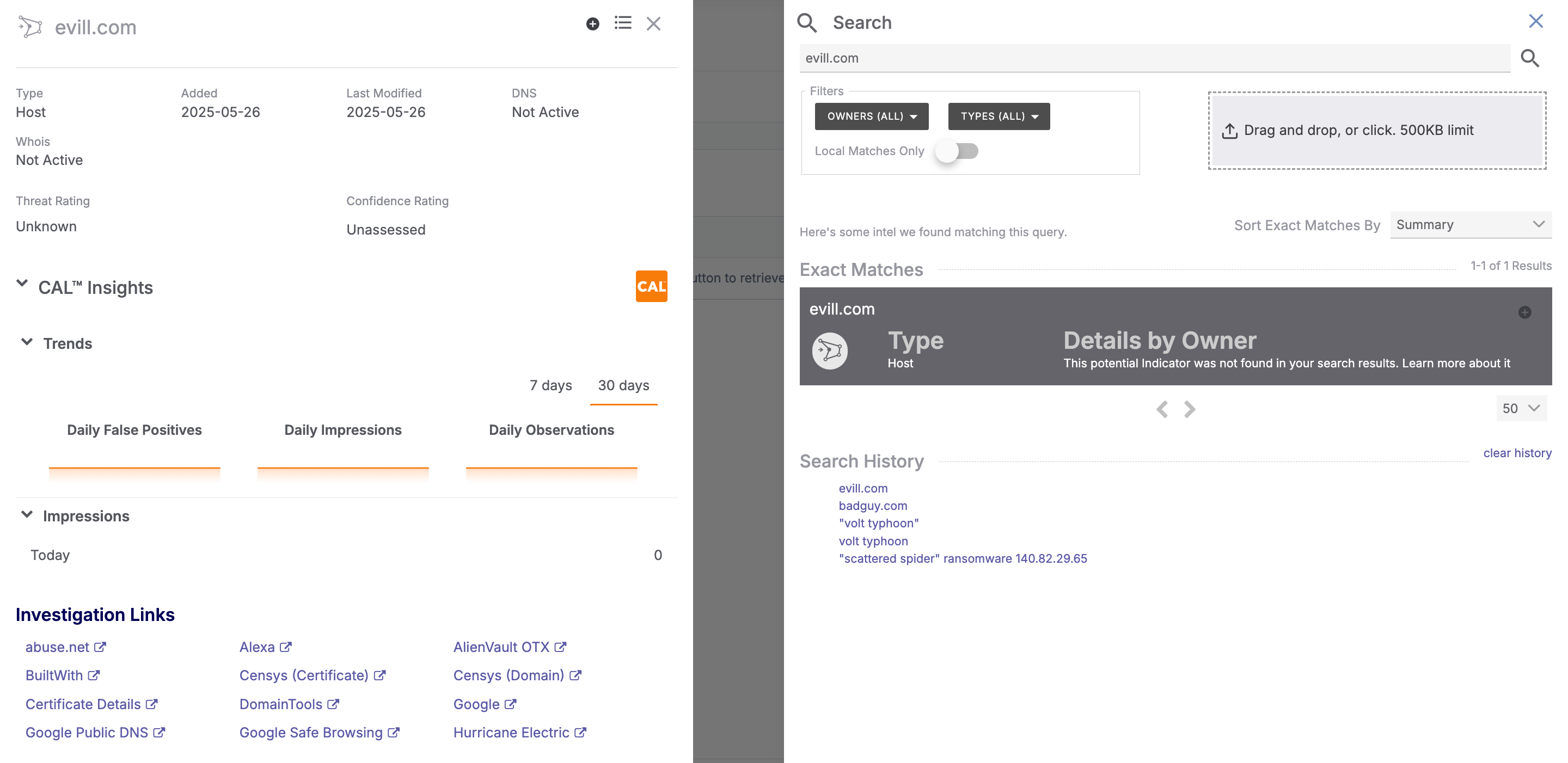
Figure 2 shows the results of a search for evill.com.
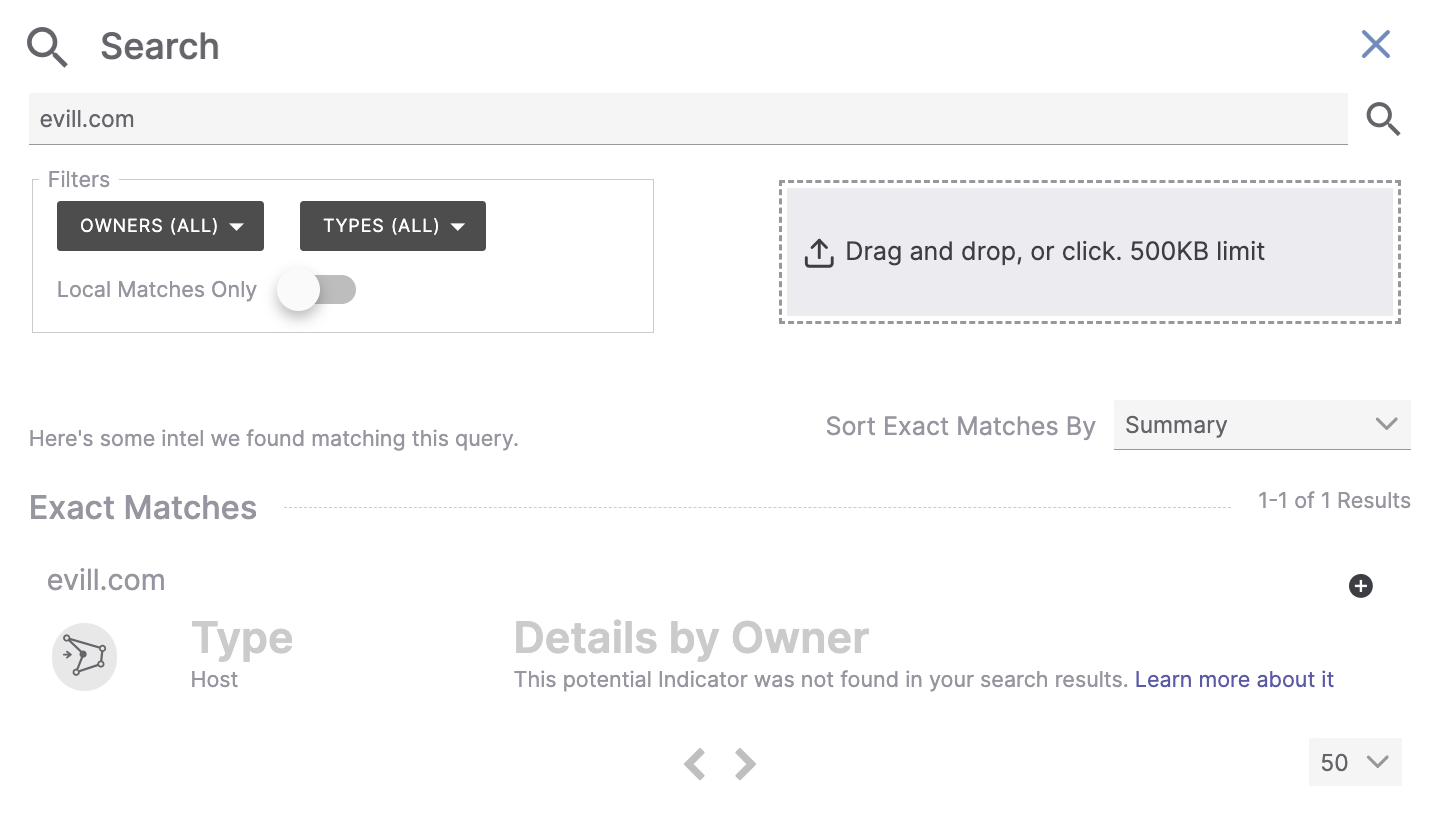
This search resulted in an exact match as well, but of the second type. The search term does not exist in any of the user’s owners, but it did meet the pattern criteria for a Host Indicator.
Figure 3 shows the results of a search for royal ransomware group.
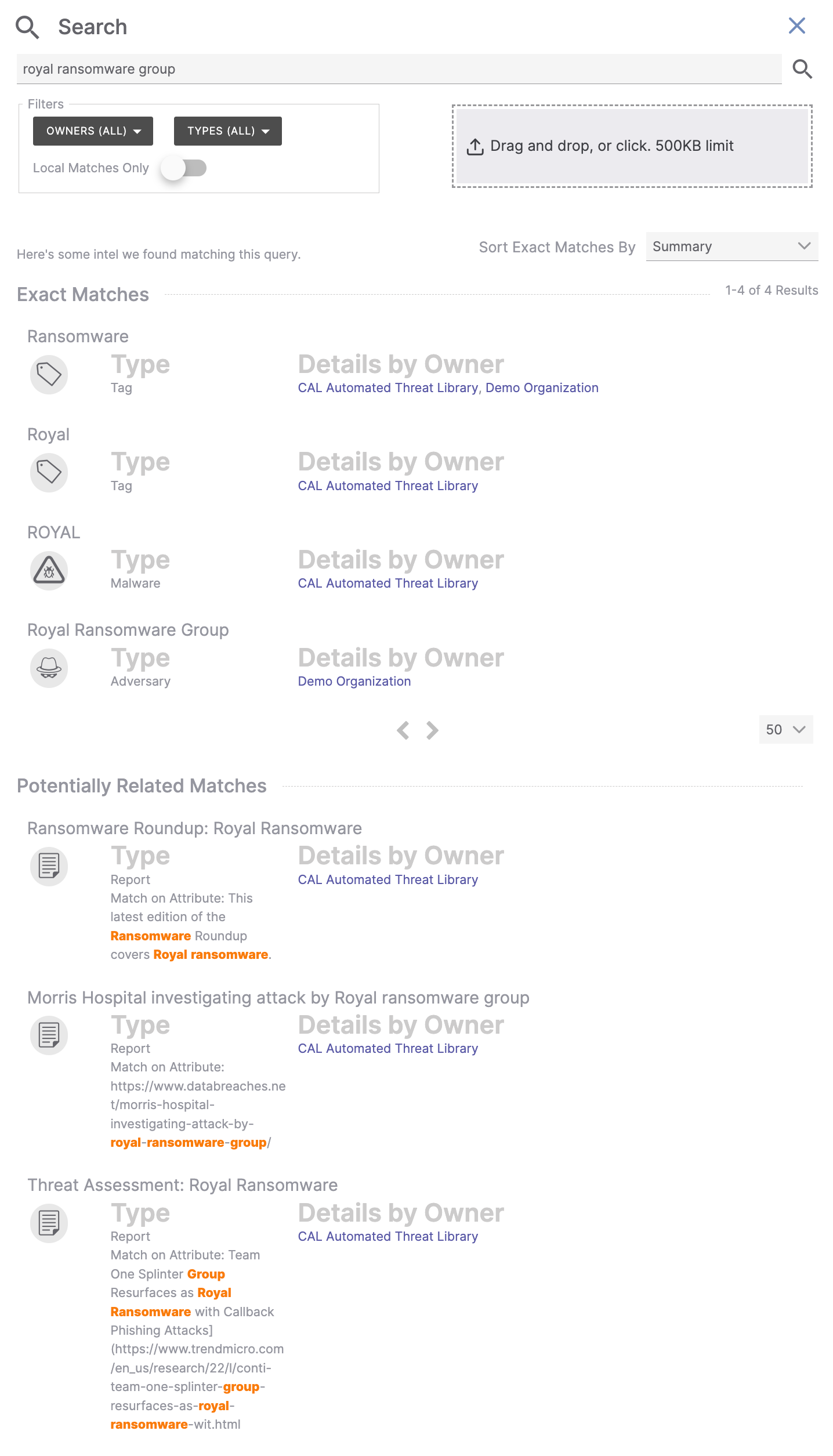
This search resulted in four exact matches, each of which is an exact match to part or all of the search phrase: one for a Tag named Ransomware, one for a Tag named Royal, one for a Malware Group named ROYAL, and one for an Adversary Group named Royal Ransomware Group. All exact matches that are Groups, Tags, Victims, Cases, or Artifacts will be of the first type, which means that all exactly matched objects exist in one of the user's owners.
Figure 4 show the results for a search of the exact phrase "royal ransomware group".
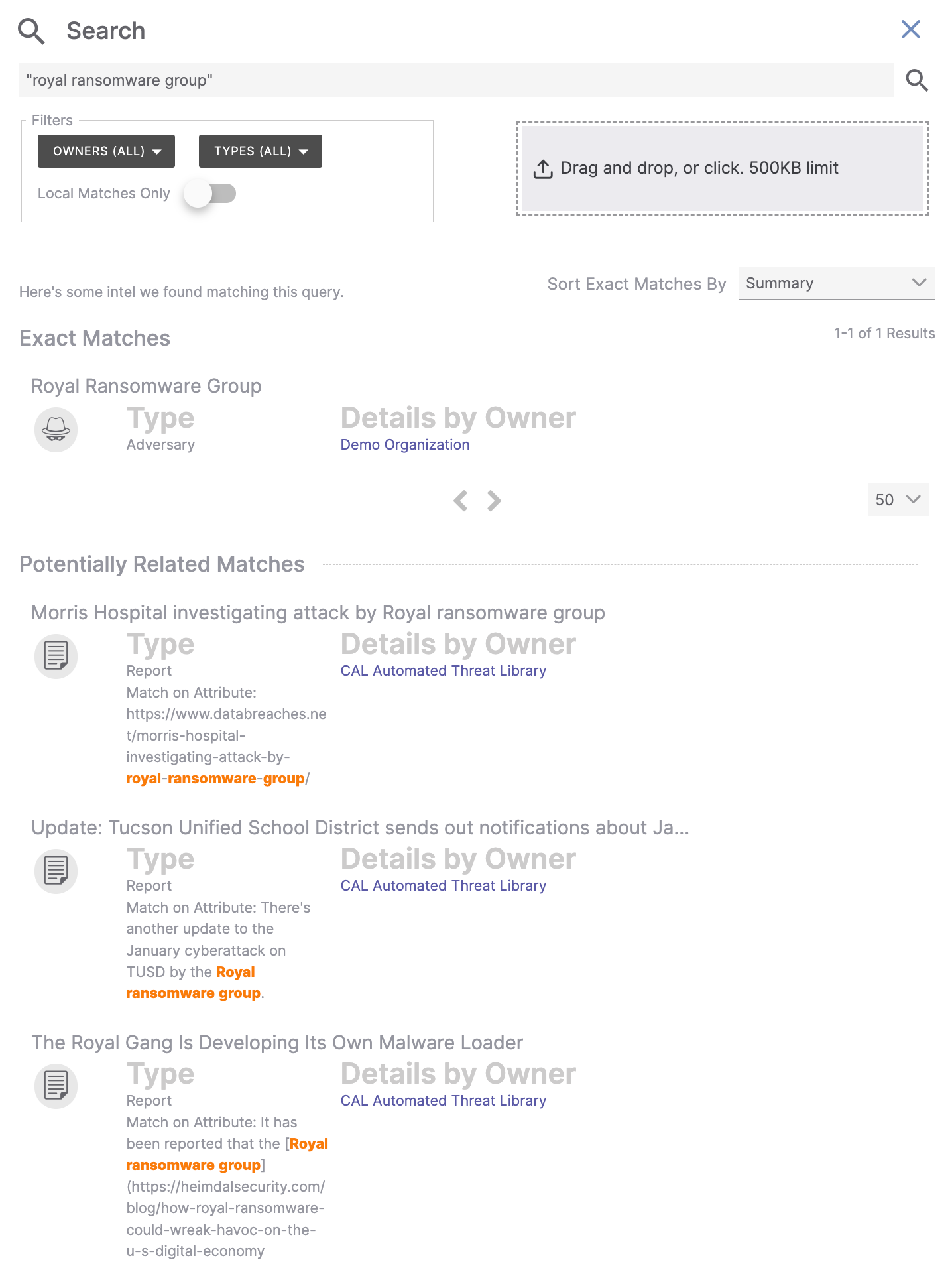
This search resulted in a single match for an Adversary Group named Royal Ransomware Group in the user’s Organization.
Sorting Exact Matches
Use the Sort Exact Matches By dropdown at the top right of the search results to sort exact matches by summary (i.e., the name of the object), type (e.g., Host, Tag), or analytics (i.e., in ascending or descending order by ThreatAssess score).
Potentially Related Matches
The Potentially Related Matches section shows objects in your owners that may be related to the search term. When looking for potential matches, the search mechanism searches all data, including object summaries and descriptions, Attributes and Case Attributes, Notes, Tasks, and the contents of document uploads.
Reviewing the examples in the “Exact Matches” section, the following potentially related matches were found for each search:
- Figure 1 includes a Potentially Related Matches section with two Indicators whose summary includes the search term (badguy.com), one Group with an Attribute that mentions the search term, and one Case with a Note that mentions the search term.
- Figure 2 does not include a Potentially Related Matches section, because no objects that may be related to the search term (evill.com) were found.
- Figure 3 includes a Potentially Related Matches section with three Report Groups, each of which has an Attribute that mentions part or all of the search term (royal ransomware group). For instance, one Group has an Attribute that mentions “ransomware” and “Royal ransomware,” while another Group has an Attribute that mentions “royal-ransomware-group.”
- Figure 4 includes a Potentially Related Matches section with three Report Groups, each of which has an Attribute that mentions the complete search phrase (royal ransomware group).
Viewing Search Result Details
You can explore objects listed in the search results further by clicking on the link(s) in the Details by Owner section or, for Cases, the name of the object. For objects that exist in one of your owners, the Details by Owner section will list all of the object's owners, with each owner's name being a link to the object's Details drawer.
For example, in Figure 1, clicking the Demo Organization link for the badguy.com object in the Exact Matches section will display the Details drawer for the badguy.com Host Indicator that exists in the Demo Organization owner (Figure 5).
- To view the Details screen for the object, click View full details
 at the upper-right corner of the Details drawer.
at the upper-right corner of the Details drawer. - If viewing the Details drawer for an Indicator that does not exist in at least one of your owners, an Add
 icon will be displayed at the upper-right corner of the Details drawer. Click this icon to add the Indicator to one of your owners in which it does not exist. After adding the Indicator to an owner, the Details drawer will change to show the Indicator in the new owner, and the new owner will be listed in the Details by Owner section on the Search drawer.
icon will be displayed at the upper-right corner of the Details drawer. Click this icon to add the Indicator to one of your owners in which it does not exist. After adding the Indicator to an owner, the Details drawer will change to show the Indicator in the new owner, and the new owner will be listed in the Details by Owner section on the Search drawer.
For Indicators that do not exist in one of your owners, the Details by Owner section of a results entry will provide a Learn more about it link that, when clicked, opens a Details drawer for the Indicator on the left-hand side of the screen (Figure 6).
This drawer can be used to view information that CAL has on the Indicator, if any, or to follow the investigation links to further explore the Indicator. To add this Indicator to one of your owners, click Add![]() at the upper-right corner of the Details drawer, or to the right of its results entry in the Search drawer, and select the desired owner.
at the upper-right corner of the Details drawer, or to the right of its results entry in the Search drawer, and select the desired owner.
You can also view a modified Details screen for the Indicator by clicking View full details at the upper-right corner of the Details drawer (Figure 7).
at the upper-right corner of the Details drawer (Figure 7).
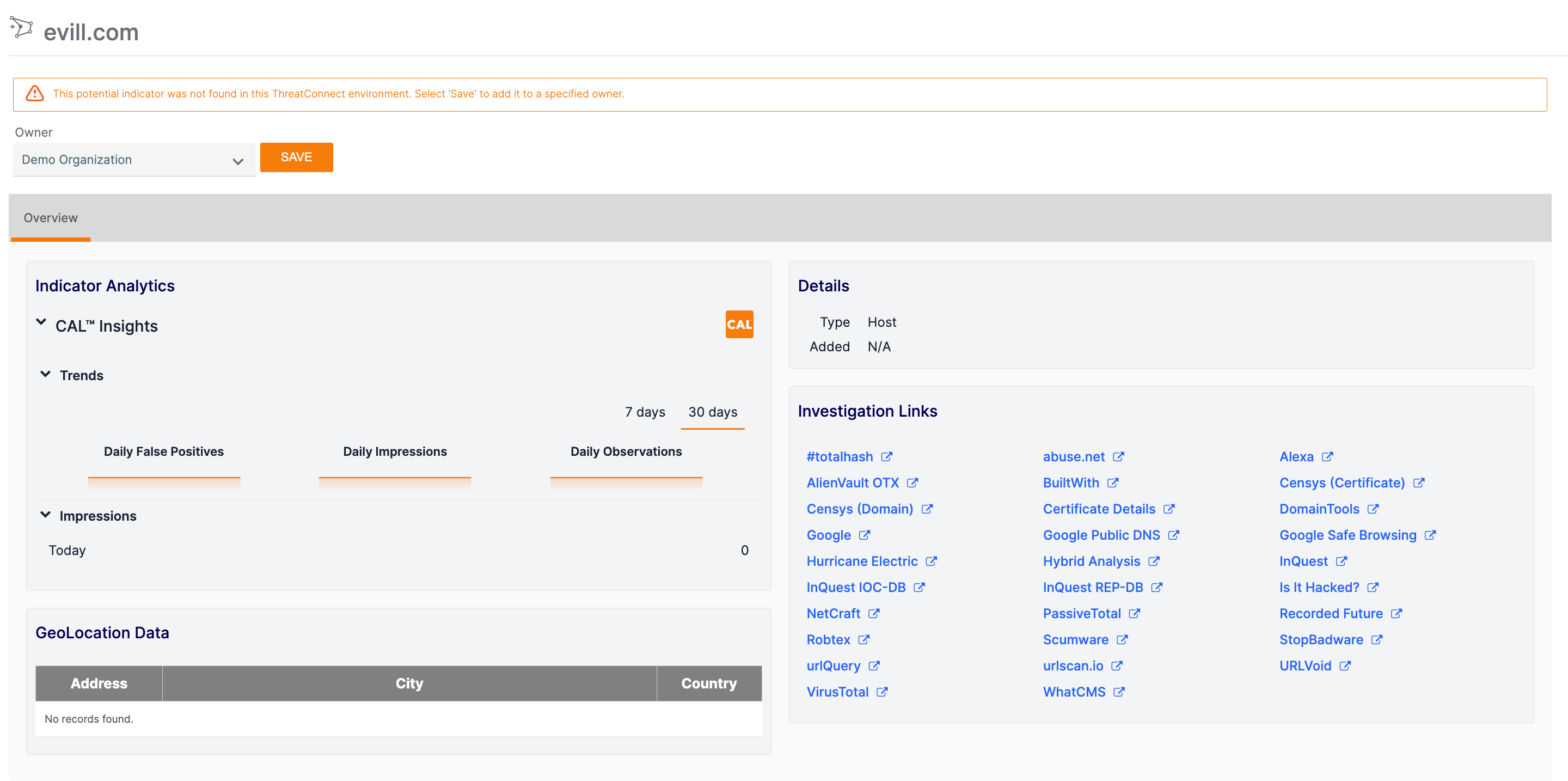
Use the Indicator Analytics section to view any information CAL has on the Indicator, or follow the links in the Investigation Links section to explore the Indicator further. To add the Indicator to one of your owners, select the desired owner from the Owner dropdown at the top left of the screen and then click the SAVE button.
Multi-Item Search Results
To search for multiple items in a single search, enter the items one after another, with a space in between each item. For example, Figure 8 shows the results of a search for the following terms: badguy.com "bad guy" ransomware.
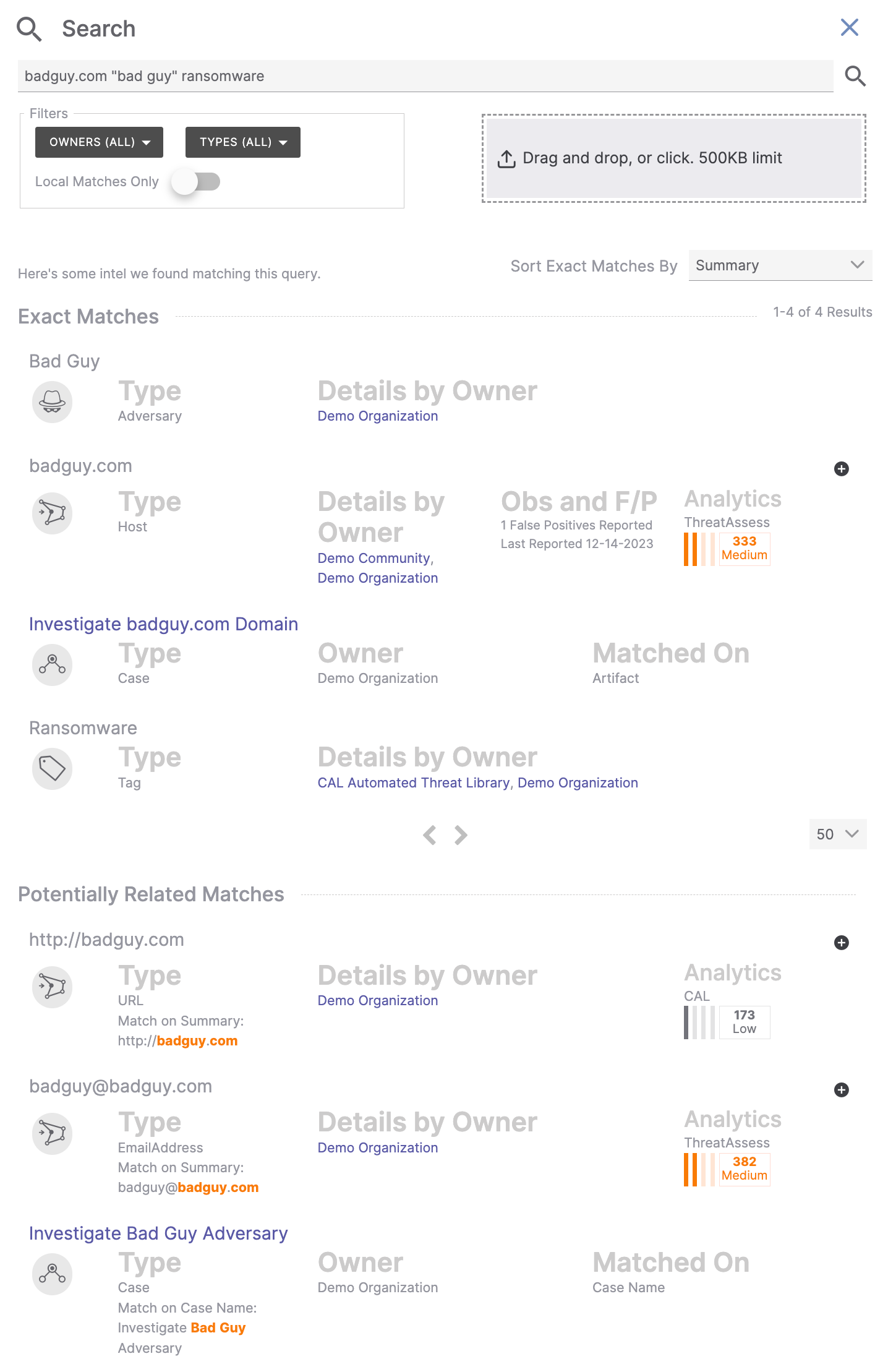
The search bar also supports line breaks (Shift + Enter). When you enter search terms with line breaks, only exact matches to Indicators, Cases, and Artifacts will be shown in the Exact Matches section. Exact matches to Groups, Tags, and Victims in your owners will be shown in the Potentially Related Matches section.
For example, Figure 9 shows the results of a search for four separate terms: badguy.com, "bad guy", ransomware, and dfdfdf.
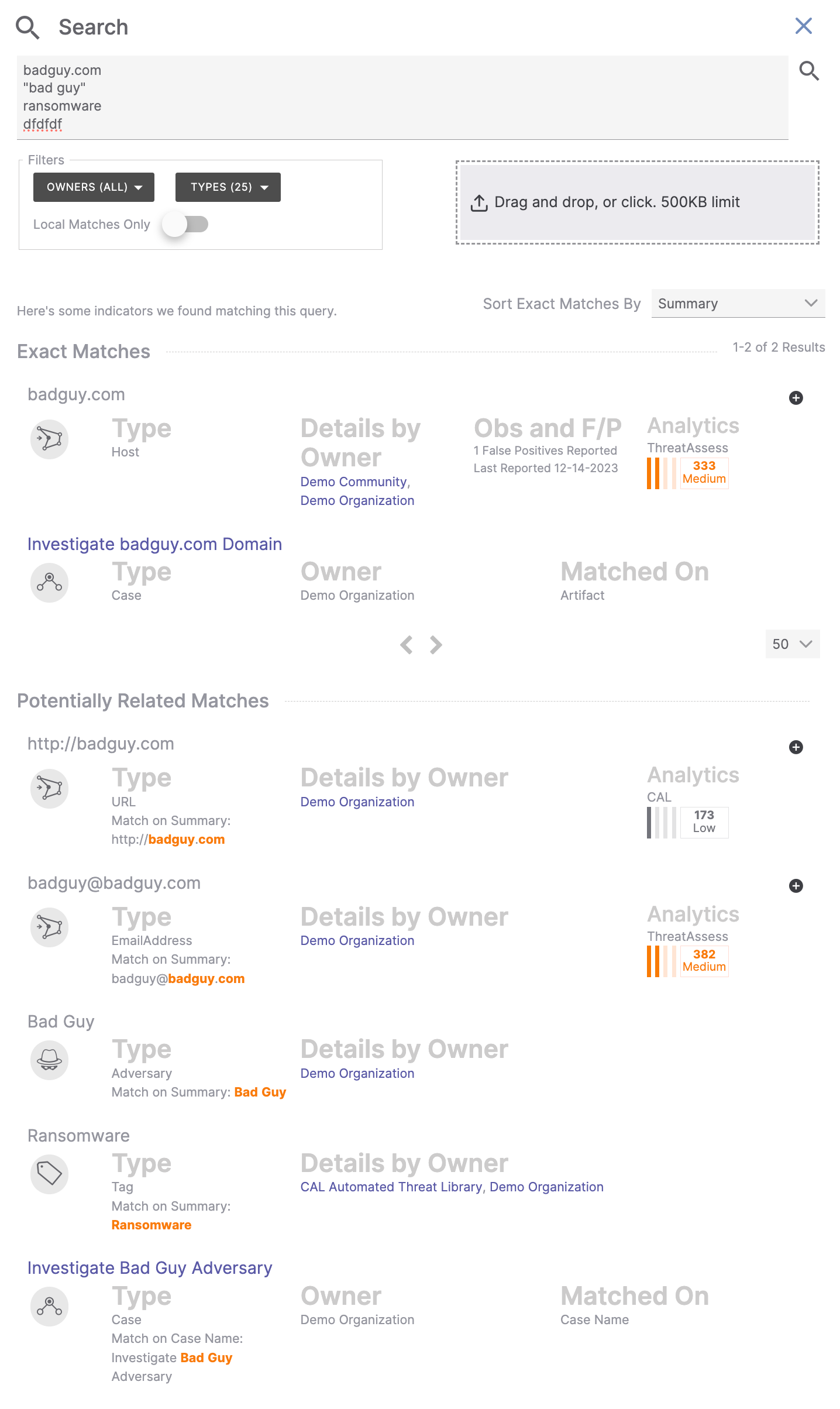
The following matches were found for each search term:
- badguy.com: Four matches were found for this search term, two of which are exact matches to an Artifact in a Case that exists in the user’s Organization and a Host Indicator that exists in the user’s Organization and one of their Communities. Because these matches are an Indicator and Artifact, they are listed in the Exact Matches section.
- bad guy: Two matches were found for this search term, one of which is an exact match to an Adversary Group named Bad Guy that exists in the user’s Organization. However, since this object is not an Indicator, Case, or Artifact, it is listed in the Potentially Related Matches section.
- ransomware: One exact match was found for this search term: a Tag named Ransomware that exists in the user’s Organization and one of their Sources. However, since this object is not an Indicator, Case, or Artifact, it is listed in the Potentially Related Matches section.
- dfdfdf: No matching items were found for this search term.
ThreatConnect® is a registered trademark, and CAL™ is a trademark, of ThreatConnect, Inc.
OpenSearch® is a registered trademark of Amazon Web Services.
20075-04 v.08.B


