- 02 Oct 2025
- 10 Minutes to read
-
Print
-
DarkLight
-
PDF
ATT&CK Tags
- Updated on 02 Oct 2025
- 10 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
An ATT&CK® Tag is a system-level Tag in ThreatConnect® that represents a technique or sub-technique in the MITRE ATT&CK® Enterprise Matrix. All ATT&CK Tags are formatted as: T<technique or sub-technique number> - <technique or sub-technique name>, as in T1499 - Endpoint Denial of Service and T1499.004 - Endpoint Denial of Service: Application or System Exploitation. ATT&CK Tags do not have an owner, and they cannot be deleted.
ATT&CK Tags are tied directly to the ThreatConnect ATT&CK Visualizer, as they must be applied to a Group in order to view the Group’s techniques and sub-techniques while using the ATT&CK Visualizer. In addition to Groups, you can apply ATT&CK Tags to Indicators, Intelligence Requirements (IRs), Victims, and Workflow Cases.
System Administrators can use pre-configured rules to convert standard Tags to ATT&CK Tags based on whether they exactly or approximately match a specific ATT&CK Tag. These rules ensure that all users on a ThreatConnect instance use ATT&CK Tags to identify the techniques and sub-techniques associated with a particular object.
Before You Start
User Roles
- To view ATT&CK Tags applied to Groups, Indicators, IRs, and Victims in an Organization, your user account can have any Organization role.
- To view ATT&CK Tags applied to Groups, Indicators, IRs, and Victims in a Community or Source, your user account can have any Community role except Banned for that Community or Source.
- To view ATT&CK Tags applied to Cases in an Organization, your user account can have any Organization role except App Developer.
- To view an ATT&CK Tag’s Details drawer and Details screen, your user account can have any Organization role.
- To apply ATT&CK Tags to Groups, Indicators, IRs, and Victims in an Organization, your user account must have an Organization role of Standard User, Sharing User, Organization Administrator, or App Developer.
- To apply ATT&CK Tags to Groups, Indicators, and Victims in a Community or Source, your user account must have a Community role of Contributor, Editor, or Director for that Community or Source.
- To apply ATT&CK Tags to Cases in an Organization, your user account must have an Organization role of Standard User, Sharing User, or Organization Administrator.
- To add ThreatConnect owners to ATT&CK Tag conversion rules, your user account must have a System role of Administrator.
Prerequisites
- To apply ATT&CK Tags to Cases, Workflow must be enabled for your Organization. To enable Workflow in your Organization, edit your Organization on the Organizations tab of the Account Settings screen and select the Enable Workflow checkbox on the Permissions tab of the Organization Information window (must be a System Administrator, Operations Administrator, or Accounts Administrator to perform this action).
Viewing ATT&CK Tags Applied to an Object
All areas of ThreatConnect that display an object’s Tags are divided into two subsections: Standard Tags and ATT&CK Tags. For example, Figure 1 shows the Tags section of the Details card on an object’s Details screen. In most areas of ThreatConnect, ATT&CK Tags can be identified by the & character before the Tag’s name.
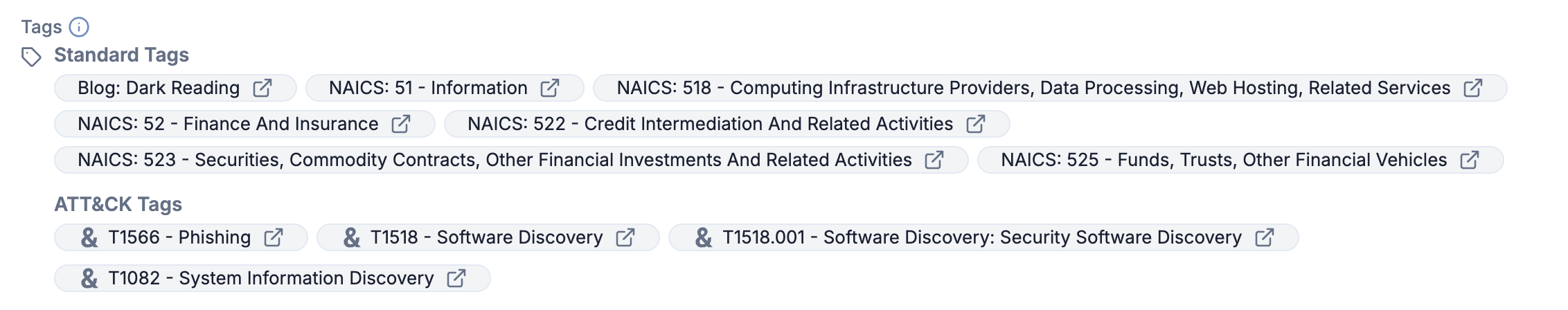
Identifying Objects That Have ATT&CK Tags
When searching by object type on the Search screen for Groups, Indicators, IRs, and Victims,or when viewing Groups, Indicators, IRs, and Victims on the Legacy Browse screen , you can run an advanced search with ThreatConnect Query Language (TQL) to filter objects based on the ATT&CK Tags applied to them.
The query in the following example searches for objects with an ATT&CK Tag representing one of the specified technique IDs applied to them:
hasTag(techniqueId is not null and techniqueId startswith ("T1486","T1490","T1027","T1047","T1036","T1059","T1562","T1112","T1204","T1055"))For more information on using ATT&CK Tag–related TQL queries, see the “Query for ATT&CK Tags” section of Constructing Query Expressions.
Viewing ATT&CK Tag Details
On the Search: Tags screen and the Legacy Browse screen, you can view all ATT&CK Tags and access an ATT&CK Tag’s Details drawer and Details screen.
Viewing ATT&CK Tags in Search: Tags
Follow these steps to view only ATT&CK Tags on the Search: Tags screen and access an ATT&CK Tag’s Details drawer and Details screen:
- From the Search & Create dropdown on the top navigation bar, select Tags.
- From the Tag type dropdown at the upper right of the Search: Tags screen, select ATT&CK Tag to display only ATT&CK Tags in the results table.
- To open an ATT&CK Tag’s Details drawer, click the ATT&CK Tag’s row or select View Details from the ATT&CK Tag’s ⋯ menu.
- To open an ATT&CK Tag’s Details screen, click the ATT&CK Tag’s name/summary.
Viewing ATT&CK Tags in Legacy Browse
Follow these steps to view only ATT&CK Tags on the Legacy Browse screen and access an ATT&CK Tag’s Details drawer and Details screen:
- From the Search & Create dropdown on the top navigation bar, select Legacy Browse.
- Select the Tags filter on the left side of the screen.
- Turn on the Advanced Search toggle at the upper left of the screen.
- Enter the following TQL query into the search bar:
techniqueId is not null - Click Search
 or press Enter to run the query and display only ATT&CK Tags in the results table.
or press Enter to run the query and display only ATT&CK Tags in the results table. - To open an ATT&CK Tag’s Details drawer, click the ATT&CK Tag’s row.
- To open an ATT&CK Tag’s Details screen, hover over the ATT&CK Tag’s row and click one of the following icons next to the ATT&CK Tag’s name/summary:
- View full details
 : Open the Details screen in the current browser tab.
: Open the Details screen in the current browser tab. - View full details in new tab
 : Open the Details screen in a new browser tab.
: Open the Details screen in a new browser tab.
- View full details
Applying ATT&CK Tags to an Object
Follow these steps to apply ATT&CK Tags to Groups, Indicators, IRs, Victims, or Cases:
- Edit the Tags applied to a Group, Indicator, IR, Victim, or Case.
- Begin entering text into the Tags text box. If there are ATT&CK Tags that match part or all of the entered text, the menu below the Tags text box will display the Tags under the ATT&CK Tags heading (Figure 2).
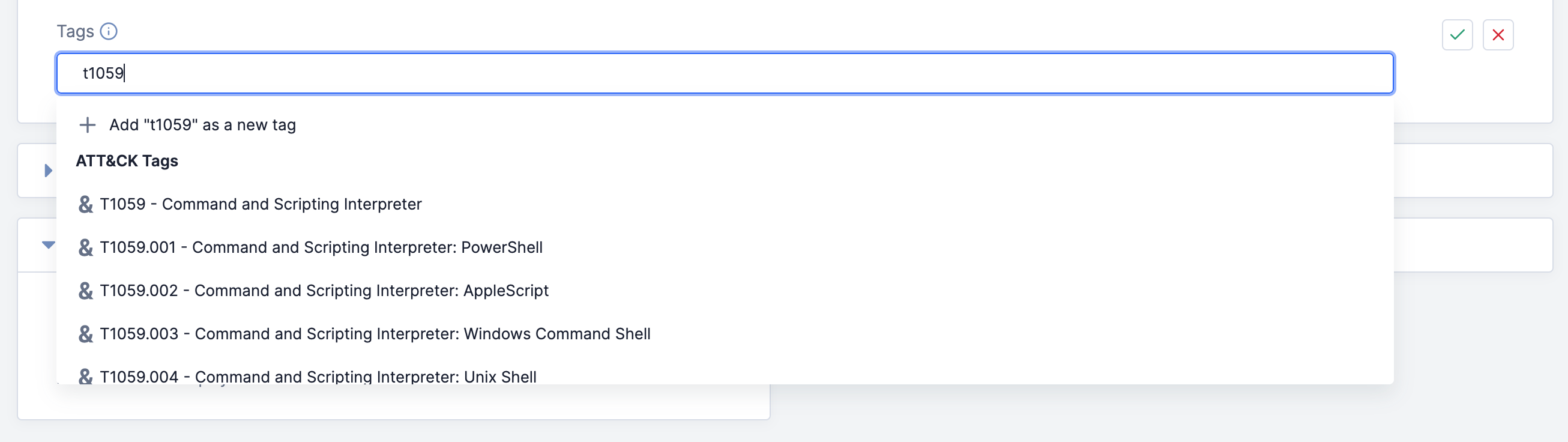 ImportantIf there are standard Tags whose names match part or all of the entered text, they will be listed under the Standard Tags heading in the menu, which comes before the ATT&CK Tags heading. Scroll down to view the list of ATT&CK Tags under the ATT&CK Tags heading.
ImportantIf there are standard Tags whose names match part or all of the entered text, they will be listed under the Standard Tags heading in the menu, which comes before the ATT&CK Tags heading. Scroll down to view the list of ATT&CK Tags under the ATT&CK Tags heading. - Select an ATT&CK Tag to add it to the Tags text box.
- Repeat Steps 2 and 3 for each ATT&CK Tag to apply to the object.
- Click Confirm
 to the right of the Tags text box.
to the right of the Tags text box.
Converting Standard Tags to ATT&CK Tags
Before Performing a Conversion
Before performing the ATT&CK Tag conversion process on an owner’s standard Tags, which is irreversible, review the following recommended tips:
- If an owner contains standard Tags with common names that match the names of ATT&CK techniques (e.g., Phishing, Rootkit, Email Collection, etc.), verify whether you want to convert them to ATT&CK Tags. If you do not want to convert them, rename the standard Tags, or use Tag normalization rules to convert them to a main Tag whose name does not match an ATT&CK technique. For example, if you use a standard Tag named Phishing and you do not want to convert it to the T1566 – Phishing ATT&CK Tag, use either of these methods to change that standard Tag’s name to something like Phishing Attack, which does not match an ATT&CK technique.
- If you leverage TQL queries (e.g., in dashboard cards), review those queries and determine whether they will need to be updated based on the results of the ATT&CK Tag conversion process. The following examples demonstrate scenarios where an existing query may need to be updated after completing the ATT&CK Tag conversion process:
- If you use a query such as
summary contains "t1001"to return only Tags whose summary contains the technique ID “T1001,”, usetechniqueId startswith "t1001"instead to return all ATT&CK Tags that map to the “T1001” technique ID. - If you use a query such as
summary contains "ent – att&ck"to return only Tags named after Enterprise techniques and sub-techniques, usetechniqueId is not nullinstead to return all ATT&CK Tags that map to Enterprise techniques and sub-techniques.
- If you use a query such as
- If you use Playbooks that execute when a specific Tag is applied to or removed from an object, review the Playbooks and verify whether they need to be updated based on the results of the ATT&CK Tag conversion process. For example, if you use a Playbook that executes when a Tag whose summary contains “ENT – ATT&CK” is applied to an Indicator, you may need to update the Trigger's configuration, as ATT&CK Tags do not include that specific text in their summaries.
ATT&CK Tag Conversion Rules
Table 1 describes the pre-configured ATT&CK Tag conversion rules that System Administrators can add owners to in order to convert standard Tags in the owners to ATT&CK Tags.
| Rule Name | Description | Example Matches |
|---|---|---|
| Exact Match | The Exact Match rule converts standard Tags that have the same name as an ATT&CK technique/sub-technique or the same combination of technique/sub-technique ID and name to the corresponding ATT&CK Tag. | The following Tags would be converted to the T1055 - Process Injection ATT&CK Tag:
|
| Approximate Match | The Approximate Match rule converts standard Tags that start with the letter “T” followed by a set of digits that map to a technique/sub-technique ID (e.g., T1055, T1055.001) to the corresponding ATT&CK Tag. | The following Tags would be converted to the T1055 - Process Injection ATT&CK Tag:
|
Adding an Owner to a Conversion Rule
Follow these steps to add a ThreatConnect owner to an ATT&CK Tag conversion rule:
- From the Settings
 menu on the top navigation bar, select System Settings.
menu on the top navigation bar, select System Settings. - On the System Settings screen, select the Tags tab. Then click ATT&CK Tag Conversion in the sidebar.
- On the ATT&CK Tag Conversion screen (Figure 3), expand the conversion rule you want to add an owner to, and then click + Add Owners.
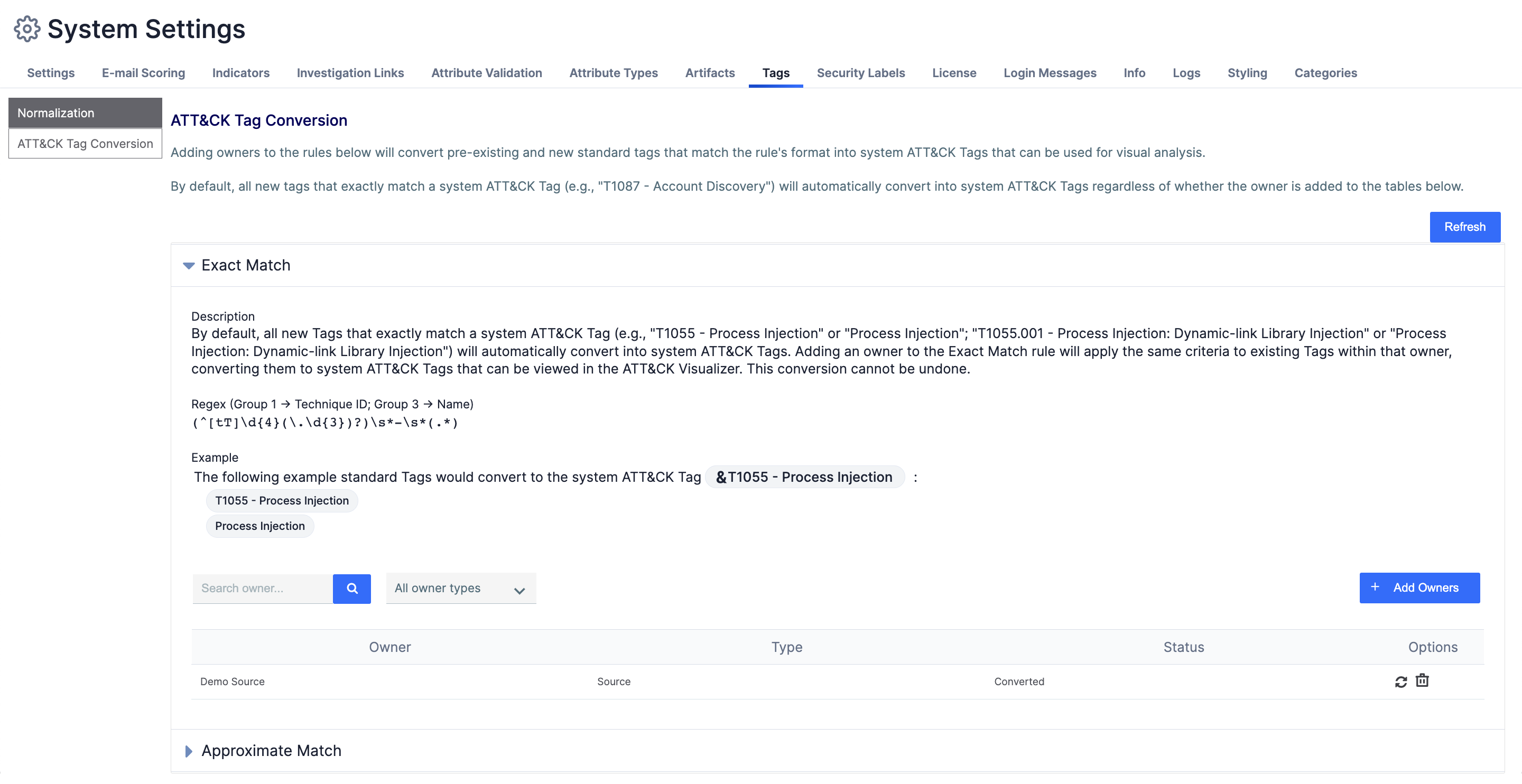
- On the Add Owners window (Figure 4), do the following to add one or more owners to the conversion rule:
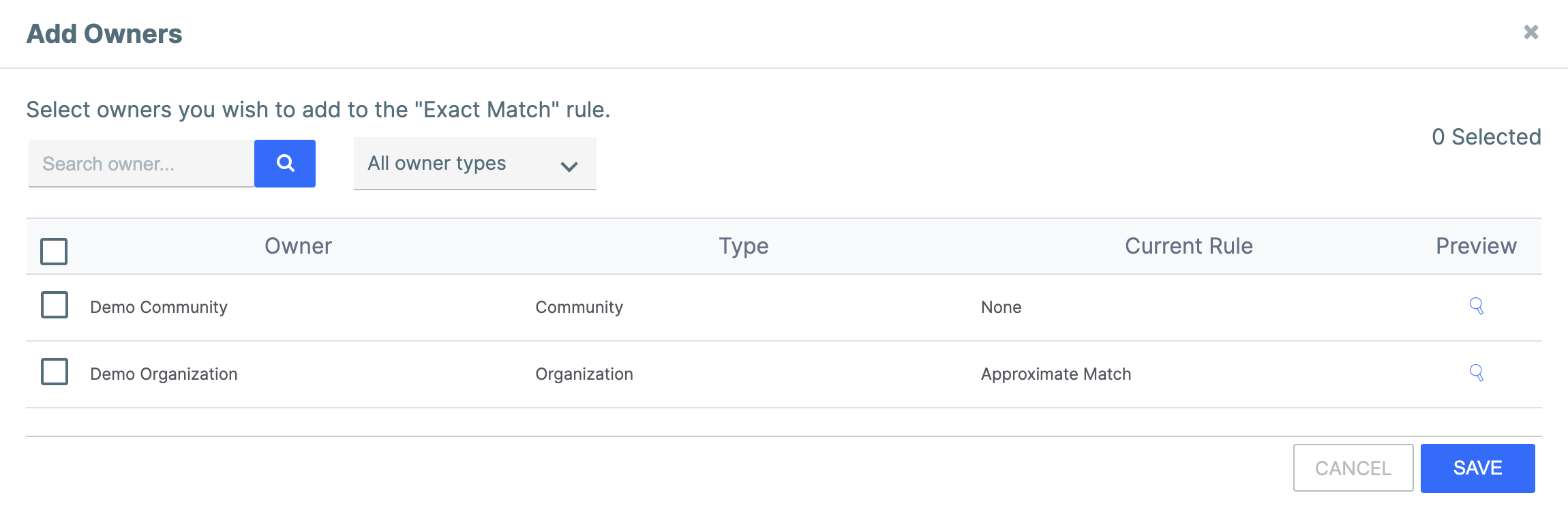
- Select each owner to add to the conversion rule.ImportantYou can add an owner to only one conversion rule. If an owner is already added to a conversion rule, that rule will be listed in the Current Rule column on the Add Owners window. Adding an owner to another conversion rule while it is already added to a conversion rule will remove it from the previous rule.
- (Optional) To view the standard Tags in an owner that match the conversion rule and the ATT&CK Tags they will be converted to, click Preview
 on the right side of the owner’s row. It is recommended to preview the standard Tags that will be converted to ATT&CK Tags for each selected owner, as the conversion process will remove the standard Tags from the owners.
on the right side of the owner’s row. It is recommended to preview the standard Tags that will be converted to ATT&CK Tags for each selected owner, as the conversion process will remove the standard Tags from the owners. - Click SAVE.
- Select each owner to add to the conversion rule.
- On the Convert Existing Tags window, click Convert to start the conversion process for each owner added to the conversion rule.WarningThe conversion process cannot be stopped once started and is irreversible. As part of the conversion process, standard Tags that are converted to ATT&CK Tags will be removed from the selected owners.
The Status column on the ATT&CK Tag Conversion screen displays the status of the conversion process for each owner. If the conversion process is queued or in progress, the Status column will display Queued for the owner. After the conversion process is complete, the Status column will display Converted for the owner. To refresh the Status column manually, click Refresh at the upper right of the ATT&CK Tag Conversion screen.
Rerunning the Conversion Process
To rerun the conversion process for an owner added to a conversion rule, expand the conversion rule on the ATT&CK Tag Conversion screen, and then click Rerun Merge![]() on the right side of the owner’s row. The conversion process will start immediately, and you will not be prompted for confirmation.
on the right side of the owner’s row. The conversion process will start immediately, and you will not be prompted for confirmation.
Removing an Owner From a Conversion Rule
To remove an owner from a conversion rule, expand the conversion rule on the ATT&CK Tag Conversion screen, and then click Delete![]() on the right side of the owner’s row.
on the right side of the owner’s row.
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.
20151-02 v.02.A


