- 23 May 2025
- 8 Minutes to read
-
Print
-
DarkLight
-
PDF
CAL 3.12 Release Notes
- Updated on 23 May 2025
- 8 Minutes to read
-
Print
-
DarkLight
-
PDF
New Features
Enhancements for CAL ATL Reports on Zero-Day and Exploited Vulnerabilities
In version 3.12, CAL™ now helps you prioritize time-sensitive reports on zero-day and exploited vulnerabilities in the CAL Automated Threat Library (ATL) Source in ThreatConnect® by identifying and labeling Report Groups on these topics and providing a more specific and vulnerability-focused artificial intelligence (AI) summary for the Reports.
Intelligence teams often face challenges in efficiently identifying exploited vulnerabilities, leading to knowledge gaps and delayed responses to critical vulnerabilities. In particular, zero-day vulnerabilities are highly exploited and represent a significant threat vector requiring timely detection and action. Unfortunately, identifying information about vulnerabilities is more complex than simple word matching, because non-relevant slang, advertisements, and other references create “noise” that can be overwhelming, distract from pertinent information, and delay identification and response times. Being able to quickly identify and understand content on zero-day and other exploited vulnerabilities can critically influence an organization’s ability to build and deploy defensive strategies in a timely manner.
Machine-Readable Tags for Fast Prioritization
CAL ATL’s AI Exploited-Vulnerability Analyzer examines Description Attributes of Report Groups in the CAL Automated Threat Library Source for specific words and phrases to determine whether the content is likely about an exploited vulnerability in general, a zero-day vulnerability, or neither. For content related to exploited vulnerabilities, it adds one of the following Tags:
- Topic: Vulnerability - An AI classification Tag in ThreatConnect that identifies CAL ATL Report Groups whose Description Attribute contains content that is highly likely to be about a high-impact exploited vulnerability.
- Topic: Zero Day - An AI classification Tag in ThreatConnect that identifies CAL ATL Report Groups whose Description Attribute contains content that is highly likely to be about a high-impact zero-day vulnerability.
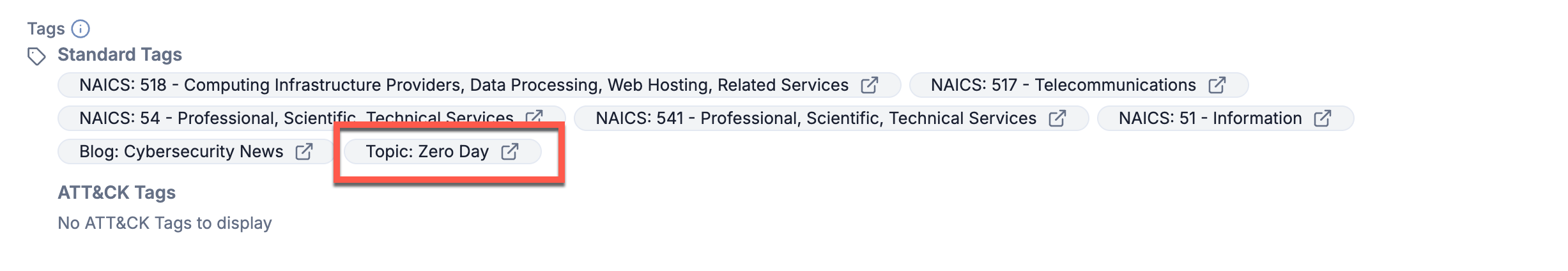 The Topic: Zero Day Tag quickly identifies CAL ATL Reports covering zero-day vulnerabilities
The Topic: Zero Day Tag quickly identifies CAL ATL Reports covering zero-day vulnerabilities
Vulnerability-Focused AI Summaries
In CAL 3.12, AI summaries for CAL ATL Reports with the Topic: Zero Day or Topic: Vulnerability Tag now provide more contextually relevant data from the text of the Report’s Description Attribute in the same short summary, covering the following topics to the extent that they are covered by the Description:
- The authority describing the zero-day vulnerability
- CVE ID and/or vulnerability name
- Affected systems
- Description of the exploit or attack
- Information on any available fixes
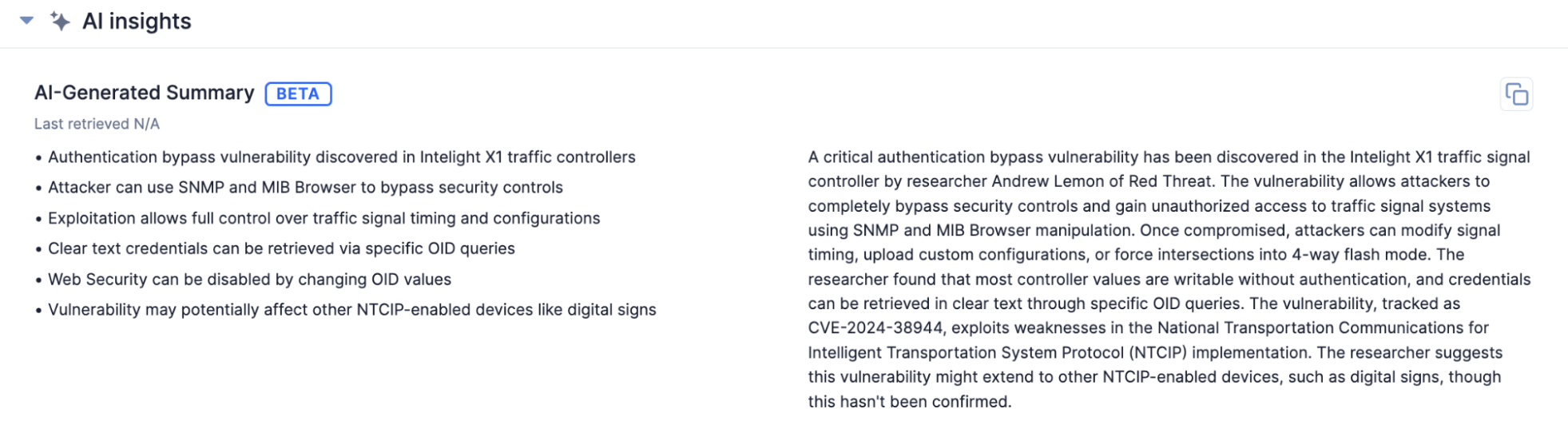 AI summaries for CAL ATL Reports on vulnerabilities are more contextually relevant
AI summaries for CAL ATL Reports on vulnerabilities are more contextually relevant
Improved CAL ATL Zero-Day Indicator Capture
Indicators related to zero-day vulnerabilities are often hard to identify in report content because, as a new threat and risk, they have little enrichment and scoring information available. Because CAL ATL takes many different steps—such as manual safelist review, known-good infrastructure enrichment, and use of scoring thresholds—to filter out “noise” so that you can stay focused on threats, it’s important that we prevent information on new vulnerabilities from being filtered out as well. To ensure that zero-day Indicators are captured in CAL ATL content, Reports with the Topic: Zero Day Tag have the normal CAL ATL scoring threshold lowered.
Zero-Day Vulnerability Updates for Intelligence Requirements
Intelligence Requirement Keyword Suggestions
When creating Intelligence Requirements (IRs),if you enter keywords related to zero-day vulnerabilities, you will receive keyword suggestions for additional zero-day-specific synonyms.
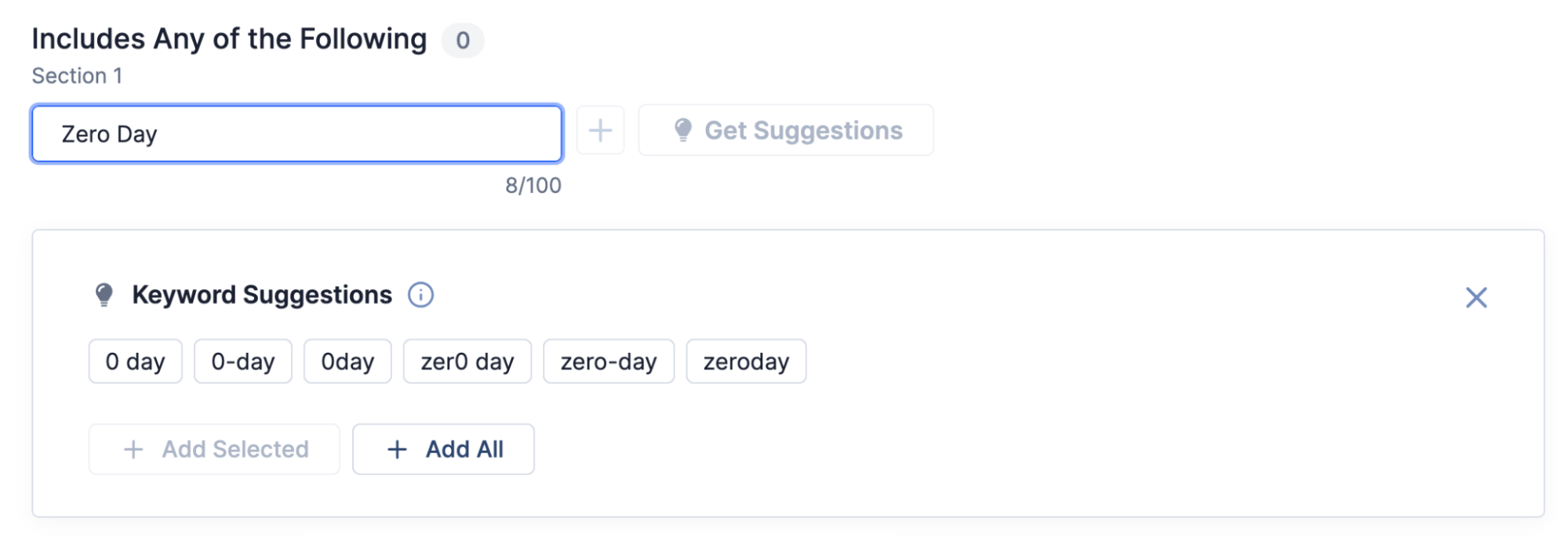 Zero-day synonyms are provided as IR keyword suggestions
Zero-day synonyms are provided as IR keyword suggestions
Intelligence Requirement Global Results
Global results for IRs using zero-day keywords will return CAL ATL Reports with the Topic: Zero Day Tag.
CAL It Like You See It!
Did you know that when you provide feedback on AI features like AI summaries for CAL ATL Reports, your feedback goes directly to the ThreatConnect Product Team for review and improvement planning? Tell us what is working and what is not, and we will work to make AI summaries work for you.
 We manually review all of your feedback and use it to shape future improvements
We manually review all of your feedback and use it to shape future improvements
Updated Features
MITRE ATT&CK 17.0 Update
ThreatConnect is now updated to MITRE ATT&CK® 17.0, which adds 24 new techniques and sub-techniques, 45 new types of software, 7 new groups, and 13 new campaigns. Version 17.0 tracks more software, groups, campaigns, and software that focus on state-directed and criminal operations targeting a range of environments with versatile tools aimed at both data theft and disruption.
You can leverage the MITRE ATT&CK 17.0 update when exploring relationships in the ATT&CK Visualizer and pivoting with CAL in Threat Graph. In addition, data from the version 17.0 update may be found in the following ThreatConnect features:
- The Search screen
- The Browse screen
- Intelligence Requirements
- The Details screen for ATT&CK Tags
- CAL Doc Analysis Service features (see the “CAL Doc Analysis Service Improvements” section)
CAL Doc Analysis Service Improvements
The CAL Doc Analysis Service is leveraged in a variety of ways throughout ThreatConnect, as detailed in the following table:
ThreatConnect Feature | |||||
|---|---|---|---|---|---|
| CAL Doc Analysis Service Feature | Description | Doc Analysis Import | ThreatConnect Intelligence Anywhere Browser Extension | ThreatConnect Doc Analysis Playbook App | CAL Automated Threat Library Source |
| Alias Extraction | Extracts explicit MITRE ATT&CK Enterprise techniques, sub-techniques, tactics, malware, tools, intrusion sets, and courses of action, as well as Common Vulnerabilities and Exposures (CVEs), from the provided content. | ✔ | ✔ | ✔ | ✔ |
| IOC Extraction | Extracts explicit indicators within the content, including addresses, email addresses, file hashes (MD5, SHA1, and SHA256), Hosts, URLs, ASNs, and CIDRs. | ✔ | ✔ | ✔ | ✔ |
| MITRE ATT&CK AI Classification | Classifies CAL ATL Report text identified as MITRE ATT&CK techniques and sub-techniques. | ✔ | ✔ | ✔ | ✔ |
| CAL ATL Report AI Summarization | Uses an artificial intelligence (AI) large language model (LLM) to summarize reports into 200-word summaries and three to five bullet points. | ✔ | ✔ | ||
| NAICS AI Industry Classification | Uses CAL ATL industry classification to categorize subsector-related industries and their corresponding sectors based on the North American Industry Classification System (NAICS) framework. | ✔ | ✔ | ||
| AI Exploited-Vulnerability Analyzer | Examines CAL ATL Reports for specific qualities to determine whether the content is likely about a zero-day or exploited vulnerability and, if so, to add a vulnerability-specific Tag and customize the AI summary for key vulnerability-focused details. | ✔ | |||
In CAL 3.12, updates to the CAL Doc Analysis Service bring improvements to three of these features.
MITRE ATT&CK AI Classification Update
ThreatConnect’s MITRE ATT&CK AI classification feature can now identify 60% of all MITRE ATT&CK techniques and sub-techniques from implicit mentions in reports, bringing the number of techniques and sub-techniques it can recognize from 121 to 408. This extra level of analysis and extraction provides even more information and insights to help you better understand your adversaries.
What can AI-based identification of 408 MITRE ATT&CK classifications do for your workflows?
- Identify Tactics, Techniques, and Procedures (TTPs) not explicitly called out in reports
- Identify four times the number of MITRE ATT&CK tactics and techniques identified by traditional matching methods
- Prioritize the most essential reports, based on identified TTPs
- Save time by removing irrelevant content from queries and IRs
- Support visual more informed exploration within ThreatConnect’s ATT&CK Visualizer and Threat Graph
CAL ATL NAICS Industry Classification Update
CAL Doc Analysis Service updates in CAL 3.12 enable the model to provide you with even more precise industry classifications for CAL ATL Reports. Use CAL ATL industry classification to prioritize the most essential CAL ATL Reports for review and identify focused information to help you to stay on top of emerging industry topics and threats.
More AI Features in CAL’s Doc Analysis Playbook App
You can now leverage a number of the key AI features found in the CAL Automated Threat Library Source directly in your automated workflows with the ThreatConnect Doc Analysis Playbook App:
- Alias Extraction: Extract explicitly mentioned MITRE ATT&CK Enterprise techniques, sub-techniques, tactics, malware, tools, intrusion sets, courses of action, and CVEs from a document such as an intelligence report.
- IOC Extraction: Extract explicitly mentioned Indicators from a document such as an email.
- AI MITRE ATT&CK Classification: Label report text identified as MITRE ATT&CK techniques and sub-techniques to find implicit TTPs in online blogs.
- NEW! NAICS industry classification: Classify subsector-related industries and their related sectors to find industry information within online blogs.
- NEW! AI summaries for CAL ATL Reports: Leverage AI summaries of reports to triage and process material on topics such as vulnerabilities in your environment.
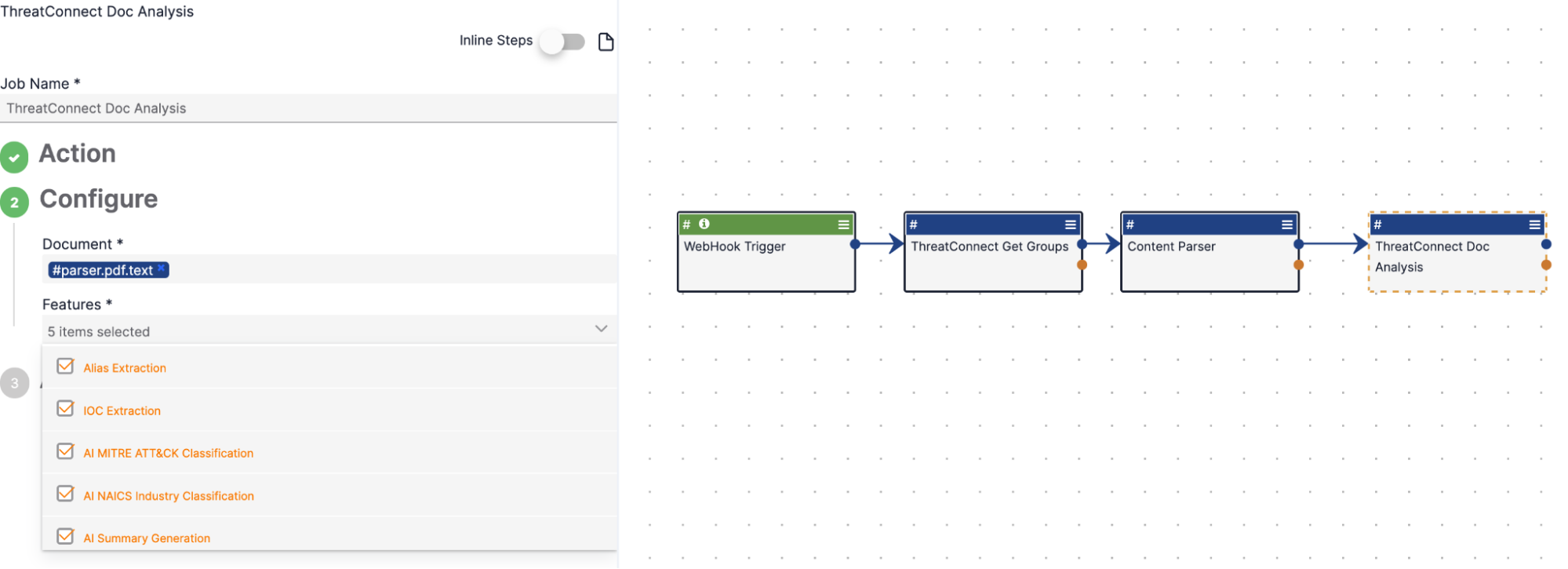 The ThreatConnect Doc Analysis Playbook App provides five ways to use CAL Doc Analysis Service AI features to process information in documents
The ThreatConnect Doc Analysis Playbook App provides five ways to use CAL Doc Analysis Service AI features to process information in documents
The ThreatConnect Doc Analysis Playbook App has a default limit of 1000 API calls per day per customer instance. Please reach out to your Customer Success Manager if your use case requires additional calls.
If you are interested in using CAL Doc Analysis Service features, but do not use ThreatConnect Playbooks, we want to hear from you! Our team is looking at how to better provide these services within customer workflows. Please reach out to your Customer Success Manager so we can discuss your needs in more detail.
Retired OSINT Sources
The following open-source intelligence (OSINT) feeds have been retired in ThreatConnect:
| Retired Feed Name | Data Last Received |
|---|---|
| Maldun Malware Analysis URLs | 9/2022 |
| VXVault | 4/2025 |
| OpenPhish | 4/2025 |
Although the OpenPhish website lists it as an unpaid feed, OpenPhish has confirmed that it no longer allows its Community feed to be leveraged by businesses for free.
Are the data from retired OSINT feeds still available?
Retired OSINT feeds may no longer be downloadable via TC Exchange™, but they are still available via CAL Indicator enrichment (that is, the information that CAL provides on Indicators—for example, on an Indicator’s Details screen) when you have CAL enabled on your instance. In other words, the data from retired OSINT feeds are still accessible, just not via a direct feed. To determine whether an Indicator has ever been seen by these feeds, refer to the CAL Feeds section of the Owners & Feeds card on the Indicator’s Details screen. Information from retired feeds is also available via automation with the Get CAL Enrichment Playbook App and in the ThreatConnect CAL Integration with Polarity.
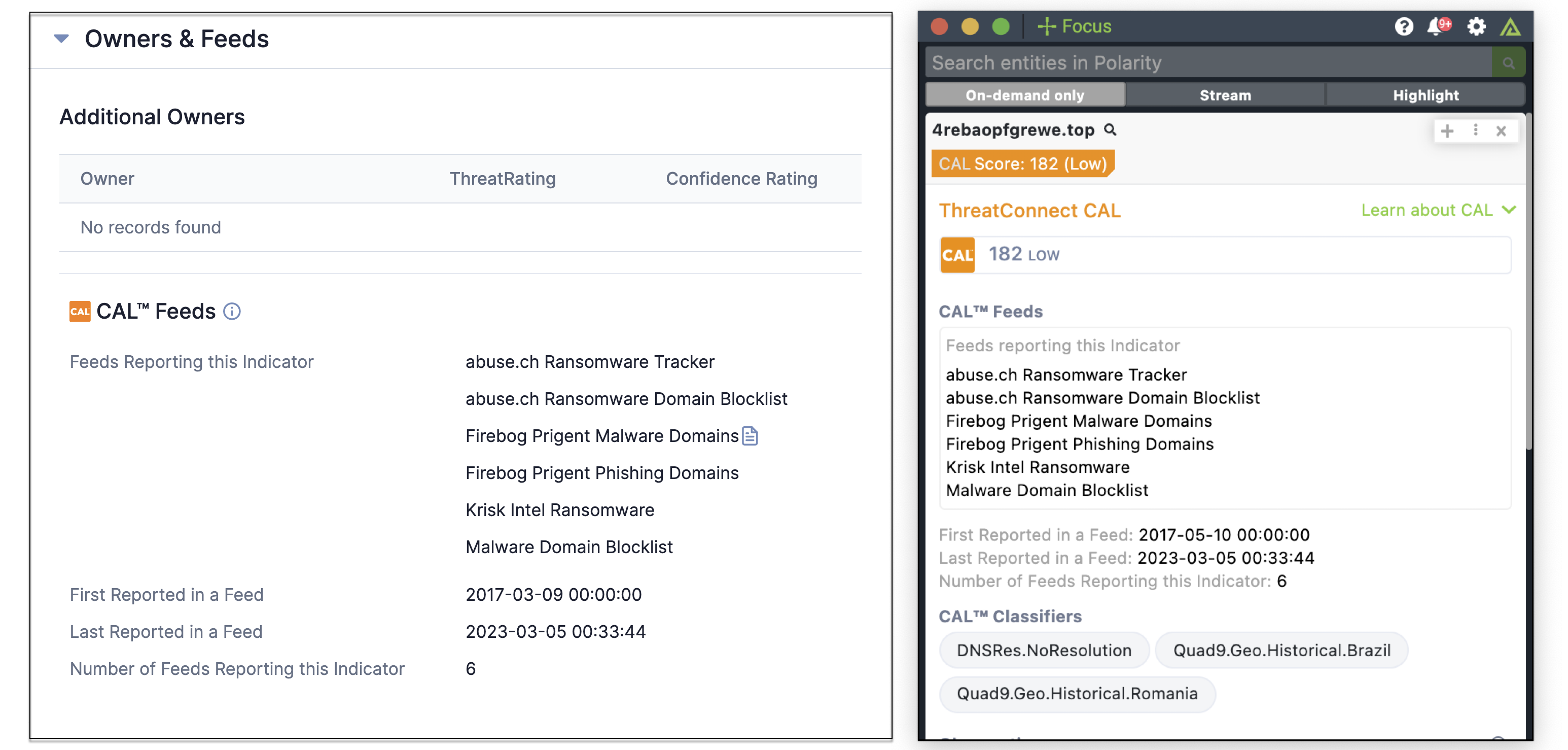 Data from retired OSINT feeds are available on Indicator Details screens and via the ThreatConnect CAL integration with Polarity
Data from retired OSINT feeds are available on Indicator Details screens and via the ThreatConnect CAL integration with Polarity
Other Updates
- The CAL Safelist has been expanded to include more trusted domains. These changes are based on information derived from customer requests, continuous audits, and internal review.
- The API for the Malshare Daily Malware OSINT feed has been updated This transition will ensure consistent access to the most recent malware hashes shared from this feed.
ThreatConnect® is a registered trademark, and CAL™ and TC Exchange™ are trademarks, of ThreatConnect, Inc.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.


