- 20 Aug 2025
- 13 Minutes to read
-
Print
-
DarkLight
-
PDF
MITRE ATT&CK AI Classification in ThreatConnect
- Updated on 20 Aug 2025
- 13 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework is a knowledge base that uses metadata codes to standardize and classify adversary goals (tactics) and offensive actions (techniques). ThreatConnect® leverages the MITRE ATT&CK® framework in various areas across the platform to optimize the way you use your threat intelligence to understand adversaries, automate workflows, and mitigate threats.
Before You Start
User Roles
- To view and pivot on ATT&CK Tags, your user account can have any Organization role.
Prerequisites
- Activate the CAL Automated Threat Library Source to view Tags applied to Report Groups in this Source. To activate the CAL Automated Threat Library Source, turn on the Active toggle for CAL Automated Threat Library on the Feeds tab of the TC Exchange™ Settings screen (must be a System Administrator to perform this action).
- To leverage ATT&CK Tags in ThreatConnect Intelligence Anywhere, enable CAL on your ThreatConnect instance and in your Organization:
- To enable CAL for your ThreatConnect instance, select the CALEnabled checkbox on the Settings tab of the System Settings screen (must be a System Administrator to perform this action).
- To enable CAL in your Organization, edit your Organization on the Organizations tab of the Account Settings screen and select the Enable CAL Data checkbox on the Permissions tab of the Organization Information window (must be a System Administrator, Operations Administrator, or Accounts Administrator to perform this action).
- Verify your ThreatConnect instance can receive data from cal.threatconnect.com (if using an On Premises instance).
How MITRE ATT&CK AI Classification Works
ThreatConnect uses a proprietary artificial intelligence (AI) classification model to read unstructured text from documents like reports and blogs attached to Report Groups in the CAL Automated Threat Library (ATL) Source and assess the content for relevant context clues to related techniques and sub-techniques in the MITRE ATT&CK framework. The MITRE ATT&CK AI classification model can identify 608 techniques and sub-techniques at a 95% confidence level. It returns these techniques and sub-techniques as system-level ATT&CK Tags associated to the Report Group containing the unstructured-text file. You can use these ATT&CK Tags as “at-a-glance” reference points, enabling you to quickly assess and pivot through large amounts of information in CAL™ ATL Reports, as well as any threat intelligence object to which you or another user has manually applied an ATT&CK Tag.
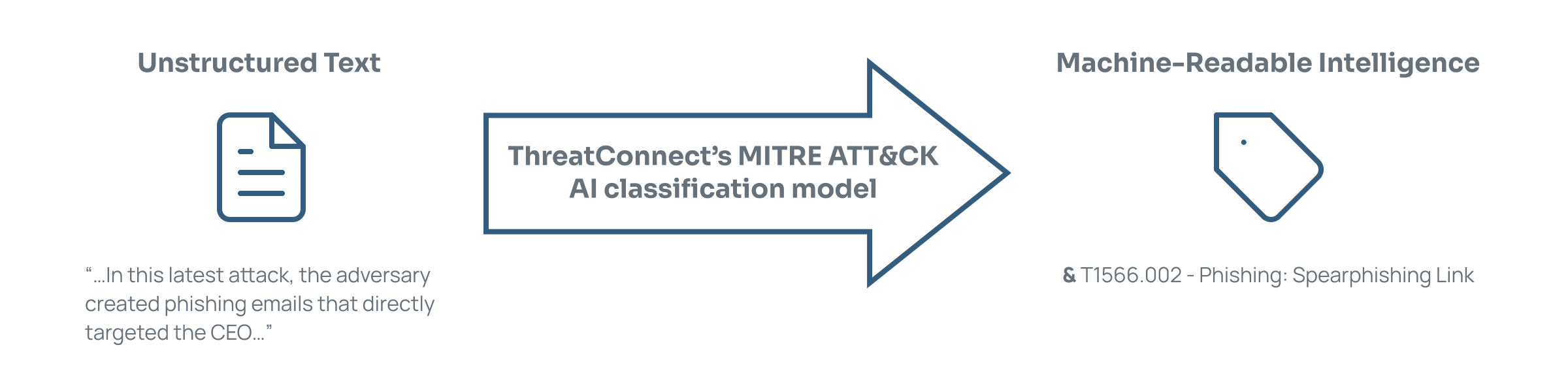
The model is monitored for accuracy and updated to support the latest version of the MITRE ATT&CK framework. When new techniques and sub-techniques are added to the framework, the model is trained to identify and “understand” them. Once the updates to the model meet ThreatConnect’s quality standards, the techniques and sub-techniques are released for use by the model.
Using MITRE ATT&CK AI Classification
You can leverage ATT&CK Tags, including those applied automatically to CAL ATL Reports by the MITRE ATT&CK AI classification model, in a number of places in ThreatConnect, including the following:
- the Search screen
- the Browse screen
- Intelligence Requirements
- the ThreatConnect ATT&CK Visualizer
- Threat Graph
You can leverage MITRE ATT&CK AI classification directly in ThreatConnect Intelligence Anywhere (ThreatConnect’s browser extension), the Doc Analysis Import feature, and the ThreatConnect Doc Analysis Playbook App. In addition, the CAL Automated Threat Library Source contains all ATT&CK Tags, including the ATT&CK Tags that are included in the MITRE ATT&CK AI classification model. You can query for ATT&CK Tags on the Browse screen using ThreatConnect Query Language (TQL), and you can search for ATT&CK Tags when searching all object types on the Search screen or when searching and browsing Tags on the Search: Tags screen.
Techniques and Sub-techniques in the MITRE ATT&CK AI Classification Model
| Technique | Sub-techniques |
|---|---|
| T1001 - Data Obfuscation |
|
| T1003 - OS Credential Dumping |
|
| T1005 - Data from Local System | |
| T1007 - System Service Discovery | |
| T1008 - Fallback Channels | |
| T1010 - Application Window Discovery | |
| T1011 - Exfiltration Over Other Network Medium | T1011.001 - Exfiltration Over Bluetooth |
| T1012 - Query Registry | |
| T1016 - System Network Configuration Discovery | T1016.002 - Wi-Fi Discovery |
| T1018 - Remote System Discovery | |
| T1020 - Automated Exfiltration | T1020.001 - Traffic Duplication |
| T1021 - Remote Services |
|
| T1025 - Data from Removable Media | |
| T1027 - Obfuscated Files or Information |
|
| T1029 - Scheduled Transfer | |
| T1030 - Data Transfer Size Limits | |
| T1033 - System Owner/User Discovery | |
| T1036 - Masquerading |
|
| T1037 - Boot or Logon Initialization Scripts |
|
| T1039 - Data from Network Shared Drive | |
| T1040 - Network Sniffing | |
| T1041 - Exfiltration Over C2 Channel | |
| T1046 - Network Service Discovery | |
| T1047 - Windows Management Instrumentation | |
| T1048 - Exfiltration Over Alternative Protocol |
|
| T1049 - System Network Connections Discovery | |
| T1053 - Scheduled Task/Job |
|
| T1055 - Process Injection |
|
| T1056 - Input Capture |
|
| T1057 - Process Discovery | |
| T1059 - Command and Scripting Interpreter |
|
| T1068 - Exploitation for Privilege Escalation | |
| T1069 - Permission Groups Discovery | T1069.003 - Cloud Groups |
| T1070 - Indicator Removal |
|
| T1071 - Application Layer Protocol |
|
| T1074 - Data Staged | T1074.001 - Local Data Staging |
| T1078 - Valid Accounts |
|
| T1082 - System Information Discovery | |
| T1083 - File and Directory Discovery | |
| T1087 - Account Discovery |
|
| T1090 - Proxy | T1090.004 - Domain Fronting |
| T1091 - Replication Through Removable Media | |
| T1092 - Communication Through Removable Media | |
| T1095 - Non-Application Layer Protocol | |
| T1098 - Account Manipulation |
|
| T1102 - Web Service | T1102.002 - Bidirectional Communication |
| T1104 - Multi-Stage Channels | |
| T1105 - Ingress Tool Transfer | |
| T1106 - Native API | |
| T1110 - Brute Force |
|
| T1111 - Multi-Factor Authentication Interception | |
| T1112 - Modify Registry | |
| T1113 - Screen Capture | |
| T1114 - Email Collection |
|
| T1115 - Clipboard Data | |
| T1119 - Automated Collection | |
| T1120 - Peripheral Device Discovery | |
| T1123 - Audio Capture | |
| T1124 - System Time Discovery | |
| T1125 - Video Capture | |
| T1127 - Trusted Developer Utilities Proxy Execution |
|
| T1132 - Data Encoding |
|
| T1133 - External Remote Services | |
| T1134 - Access Token Manipulation |
|
| T1135 - Network Share Discovery | |
| T1136 - Create Account |
|
| T1137 - Office Application Startup |
|
| T1140 - Deobfuscate/Decode Files or Information | |
| T1176 - Software Extensions |
|
| T1187 - Forced Authentication | |
| T1190 - Exploit Public-Facing Application | |
| T1195 - Supply Chain Compromise |
|
| T1199 - Trusted Relationship | |
| T1200 - Hardware Additions | |
| T1201 - Password Policy Discovery | |
| T1202 - Indirect Command Execution | |
| T1203 - Exploitation for Client Execution | |
| T1204 - User Execution |
|
| T1205 - Traffic Signaling |
|
| T1207 - Rogue Domain Controller | |
| T1210 - Exploitation of Remote Services | |
| T1213 - Data from Information Repositories |
|
| T1216 - System Script Proxy Execution |
|
| T1217 - Browser Information Discovery | |
| T1218 - System Binary Proxy Execution |
|
| T1219 - Remote Access Tools |
|
| T1220 - XSL Script Processing | |
| T1221 - Template Injection | |
| T1222 - File and Directory Permissions Modification |
|
| T1480 - Execution Guardrails |
|
| T1482 - Domain Trust Discovery | |
| T1485 - Data Destruction | T1485.001 - Lifecycle-Triggered Deletion |
| T1486 - Data Encrypted for Impact | |
| T1490 - Inhibit System Recovery | |
| T1491 - Defacement |
|
| T1495 - Firmware Corruption | |
| T1496 - Resource Hijacking |
|
| T1498 - Network Denial of Service |
|
| T1499 - Endpoint Denial of Service |
|
| T1505 - Server Software Component |
|
| T1518 - Software Discovery | T1518.001 - Security Software Discovery |
| T1525 - Implant Internal Image | |
| T1526 - Cloud Service Discovery | |
| T1529 - System Shutdown/Reboot | |
| T1530 - Data from Cloud Storage | |
| T1535 - Unused/Unsupported Cloud Regions | |
| T1537 - Transfer Data to Cloud Account | |
| T1538 - Cloud Service Dashboard | |
| T1542 - Pre-OS Boot |
|
| T1543 - Create or Modify System Process |
|
| T1546 - Event Triggered Execution |
|
| T1547 - Boot or Logon Autostart Execution |
|
| T1548 - Abuse Elevation Control Mechanism |
|
| T1550 - Use Alternate Authentication Material |
|
| T1552 - Unsecured Credentials |
|
| T1553 - Subvert Trust Controls |
|
| T1555 - Credentials from Password Stores |
|
| T1556 - Modify Authentication Process |
|
| T1557 - Adversary-in-the-Middle |
|
| T1558 - Steal or Forge Kerberos Tickets |
|
| T1559 - Inter-Process Communication |
|
| T1560 - Archive Collected Data |
|
| T1561 - Disk Wipe | T1561.002 - Disk Structure Wipe |
| T1562 - Impair Defenses |
|
| T1563 - Remote Service Session Hijacking |
|
| T1564 - Hide Artifacts |
|
| T1565 - Data Manipulation |
|
| T1566 - Phishing |
|
| T1567 - Exfiltration Over Web Service |
|
| T1568 - Dynamic Resolution |
|
| T1569 - System Services |
|
| T1570 - Lateral Tool Transfer | |
| T1571 - Non-Standard Port | |
| T1573 - Encrypted Channel |
|
| T1574 - Hijack Execution Flow |
|
| T1578 - Modify Cloud Compute Infrastructure |
|
| T1583 - Acquire Infrastructure |
|
| T1584 - Compromise Infrastructure |
|
| T1585 - Establish Accounts |
|
| T1586 - Compromise Accounts |
|
| T1587 - Develop Capabilities |
|
| T1588 - Obtain Capabilities |
|
| T1589 - Gather Victim Identity Information |
|
| T1590 - Gather Victim Network Information |
|
| T1591 - Gather Victim Org Information |
|
| T1592 - Gather Victim Host Information |
|
| T1593 - Search Open Websites/Domains |
|
| T1594 - Search Victim-Owned Websites | |
| T1595 - Active Scanning |
|
| T1596 - Search Open Technical Databases |
|
| T1597 - Search Closed Sources |
|
| T1598 - Phishing for Information |
|
| T1599 - Network Boundary Bridging | T1599.001 - Network Address Translation Traversal |
| T1600 - Weaken Encryption |
|
| T1601 - Modify System Image |
|
| T1602 - Data from Configuration Repository |
|
| T1606 - Forge Web Credentials |
|
| T1608 - Stage Capabilities |
|
| T1609 - Container Administration Command | |
| T1610 - Deploy Container | |
| T1611 - Escape to Host | |
| T1612 - Build Image on Host | |
| T1613 - Container and Resource Discovery | |
| T1615 - Group Policy Discovery | |
| T1619 - Cloud Storage Object Discovery | |
| T1620 - Reflective Code Loading | |
| T1621 - Multi-Factor Authentication Request Generation | |
| T1647 - Plist File Modification | |
| T1648 - Serverless Execution | |
| T1649 - Steal or Forge Authentication Certificates | |
| T1650 - Acquire Access | |
| T1651 - Cloud Administration Command | |
| T1652 - Device Driver Discovery | |
| T1653 - Power Settings | |
| T1654 - Log Enumeration | |
| T1656 - Impersonation | |
| T1657 - Financial Theft | |
| T1659 - Content Injection | |
| T1665 - Hide Infrastructure | |
| T1666 - Modify Cloud Resource Hierarchy | |
| T1667 - Email Bombing | |
| T1668 - Exclusive Control | |
| T1669 - Wi-Fi Networks | |
| T1671 - Cloud Application Integration | |
| T1672 - Email Spoofing | |
| T1673 - Virtual Machine Discovery | |
| T1674 - Input Injection | |
| T1675 - ESXi Administration Command |
ThreatConnect® is a registered trademark, and CAL™ and TC Exchange™ are trademarks, of ThreatConnect, Inc.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.
20166-01 v.03.A


