- 18 Mar 2025
- 3 Minutes to read
-
Print
-
DarkLight
-
PDF
CAL 3.11 Release Notes
- Updated on 18 Mar 2025
- 3 Minutes to read
-
Print
-
DarkLight
-
PDF
New Features
CAL ATL Sources
ThreatConnect®’s CAL™ Automated Threat Library (ATL) is a powerful artificial intelligence (AI)–, machine learning (ML)–driven source that significantly enhances threat intelligence operations. It efficiently distills 74 trusted open-source intelligence (OSINT) sources into structured, ready-to-use threat intel mapped to the ThreatConnect data model and the MITRE ATT&CK® framework. It extracts Indicators of Compromise (IOCs), provides summaries, and identifies related industries via AI. This automation saves analysts hours of manual effort daily by aggregating and analyzing data using AI/ML and natural language processing (NLP).
A complete list of CAL Automated Threat Library Source blogs can be found in the ThreatConnect Knowledge Base. Newly added sources include the following:
- Tenable
- GreyNoise
- Red Canary
- Have I Been Pwned
Updated Features
CAL Document Analysis Improvements
The CAL Document Analysis service is leveraged throughout the ThreatConnect platform via the CAL Automated Threat Library Source, the ThreatConnect Doc Analysis import feature, the ThreatConnect Intelligence Anywhere browser extension, and within Playbooks via the ThreatConnect Doc Analysis App. The following updates were made to the CAL Document Analysis service in CAL 3.11:
- Substantial improvements were made in identification of MITRE ATT&CK techniques, sub-techniques, courses of action, tactics, and campaigns in submitted documents to account for some formatting issues.
- Improvements were made in identification of embedded links in submitted documents that, in turn, identify additional Indicators in other documents.
CAL Safelist Updates
In this release, we have expanded the CAL Safelist to include more trusted domains, based on customer requests and internal review. Over 250 updates have been made, resulting in over 11,200,000 items being marked as safe in CAL. These Safelist updates are also included in the data available from the ThreatConnect CAL Integration with Polarity. CAL is working to constantly improve the accuracy of your threat intelligence, allowing you to focus on real threats by providing contextual insights and minimizing unnecessary noise in analyst research, document analysis, Indicator queries, and automated workflows across both ThreatConnect and Polarity.
Retired OSINT Sources in TC Exchange
As part of an ongoing effort to improve collection accuracy and relevance, retired OSINT feeds in TC Exchange™ will no longer be downloadable as Sources in ThreatConnect. Most of the retired feeds have not produced data in several years and contain mainly outdated information that can cause confusion and congestion in ThreatConnect.
Are the data from the retired feeds still available?
Yes, the data from retired OSINT feeds are still accessible, just not via a direct feed. To see if an Indicator has ever been seen by these feeds, refer to the CAL Feeds section of the Owners & Feeds card on the Indicator’s Details screen. Information from retired feeds is also available via automation with the Get CAL Enrichment Playbook App, and in the ThreatConnect CAL Integration with Polarity.
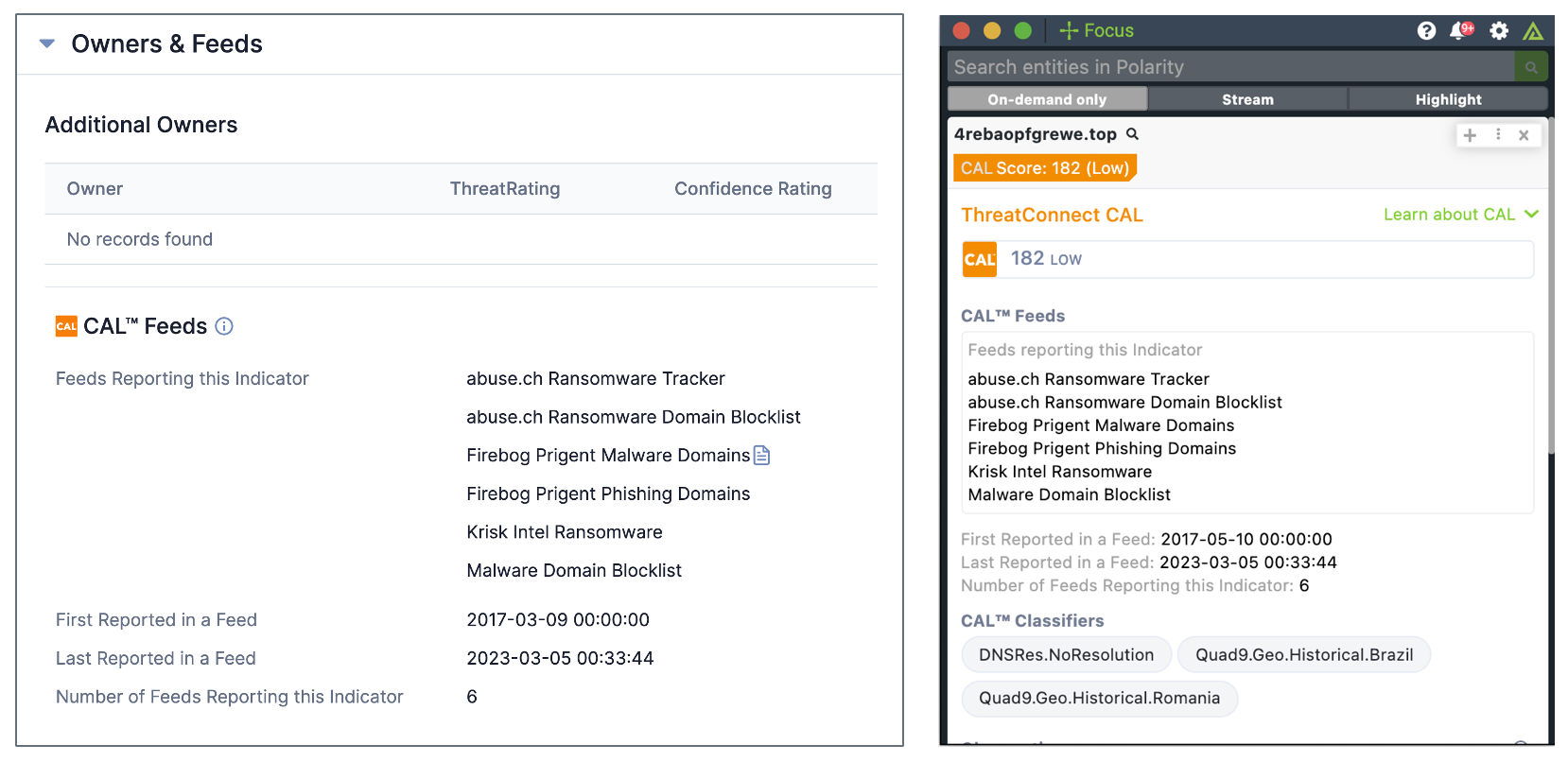
Data from retired OSINT feeds are available on Indicator Details screens and via the ThreatConnect CAL Integration with Polarity
How can I tell if a feed is retired?
On the TC Exchange Settings screen, when viewing the report card for a retired feed, you will see an Inactive![]() icon to the left of the feed’s name, and its report card will be blank.
icon to the left of the feed’s name, and its report card will be blank.
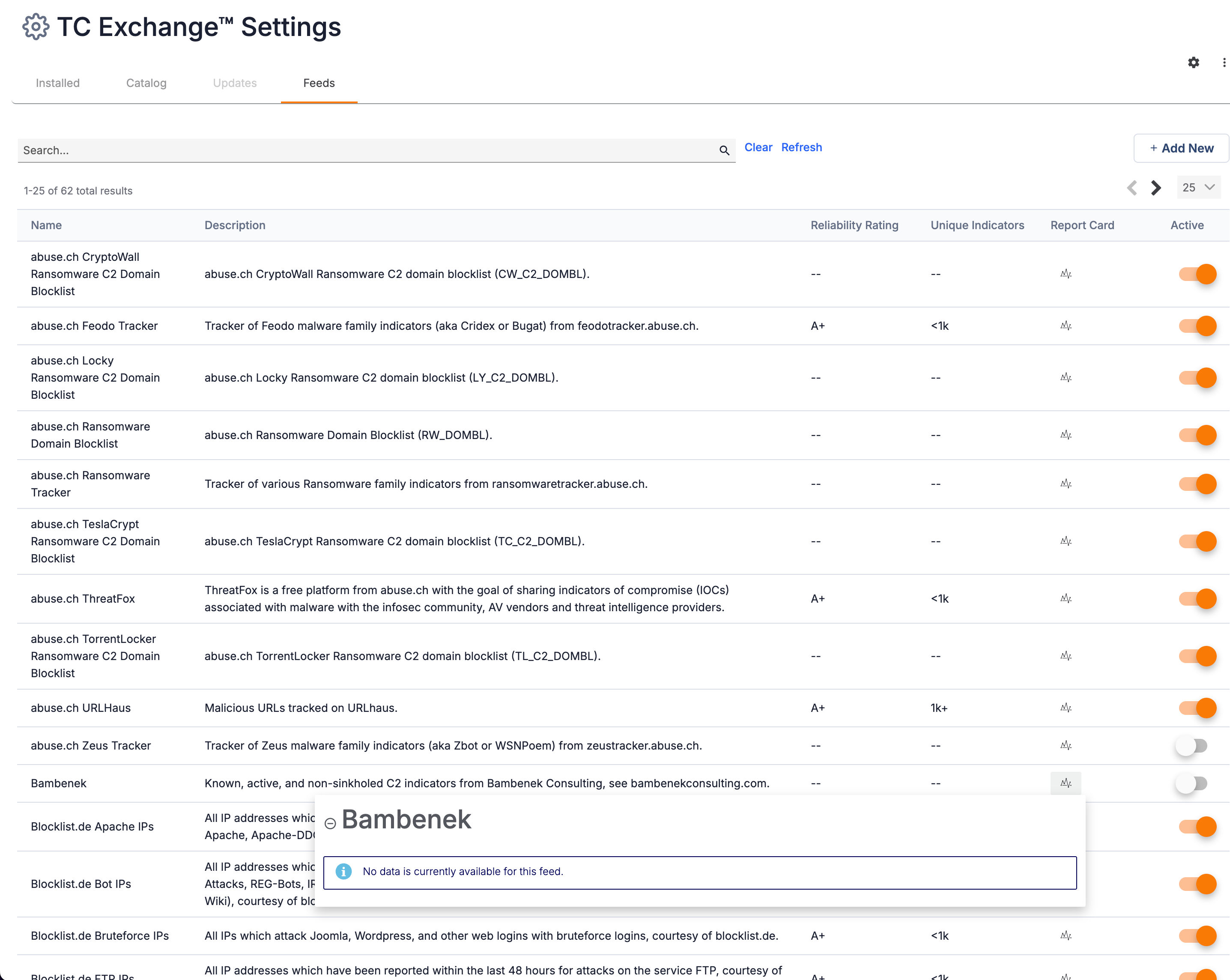
Inactive feeds have an Inactive icon next to their name and a blank report card
In a future version of ThreatConnect, retired feeds will be removed from the TC Exchange Settings screen.
Which feeds have been retired?
| Retired Feed Name | Data Last Received |
|---|---|
| abuse.ch CryptoWall Ransomware C2 Domain Blocklist | 12/2019 |
| abuse.ch Locky Ransomware C2 Domain Blocklist | 12/2019 |
| abuse.ch Ransomware Domain Blocklist | 12/2019 |
| abuse.ch Ransomware Tracker | 11/2020 |
| abuse.ch TeslaCrypt Ransomware C2 Domain Blocklist | 12/2019 |
| abuse.ch TorrentLocker Ransomware C2 Domain Blocklist | 12/2019 |
| abuse.ch ZeuS Tracker | 6/2020 |
| Bambanek | 2/2021 |
| Cedia.org.ec Immortal Domains | 2/2021 |
| Cert-pa.it Latest Malware Analysis | 6/2022 |
| Cryptam | 5/2020 |
| Firebog Airelle Hrsk Domains | 3/2022 |
| Firebog Prigent Phishing Domains | 9/2022 |
| Firebog Shalla Malware Domains | 9/2022 |
| Haley SSH Bruteforce IPs | 1/2025 |
| hpHosts Exploit Domains | 3/2020 |
| hpHosts Malware Distribution Domains | 3/2020 |
| hpHosts Phishing Domains | 3/2020 |
| Krisk Intel Malicious Domains | 3/2023 |
| Krisk Intel Malicious IPs | 3/2023 |
| Krisk Intel Malware Hashes | 3/2023 |
| Krisk Intel Ransomware | 3/2023 |
| Malware Domain Blocklist | 8/2021 |
| MalwareConfig | 5/2019 |
| Manwe Mac Malware | 3/2020 |
| Minotaur URLs | 5/2019 |
| PDFExaminer | 5/2020 |
| PUP Names Blocklist | 6/2023 |
| SARVAM | 11/2023 |
| WSTNPHX Malware Email Addresses | 3/2020 |
Other Updates
- The temporary gap in coverage for Bleeping Computer in the CAL Automated Threat Library Source was resolved.
- The CAL COVID-19–themed newly registered domains (NRDs) were retired due to lack of new data.
- The Haley SSH Bruteforce IPs were deprecated due to owner retirement.
ThreatConnect® is a registered trademark, and CAL™ and TC Exchange™ are trademarks, of ThreatConnect, Inc.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.


