- 12 Jun 2024
- 4 Minutes to read
-
Print
-
DarkLight
-
PDF
Managing Data in All Organizations: Threat Intelligence
- Updated on 12 Jun 2024
- 4 Minutes to read
-
Print
-
DarkLight
-
PDF
As a Super User, you can view, create, import, filter, search for, modify, and delete threat intelligence in all Organizations on your ThreatConnect instance.
Browse
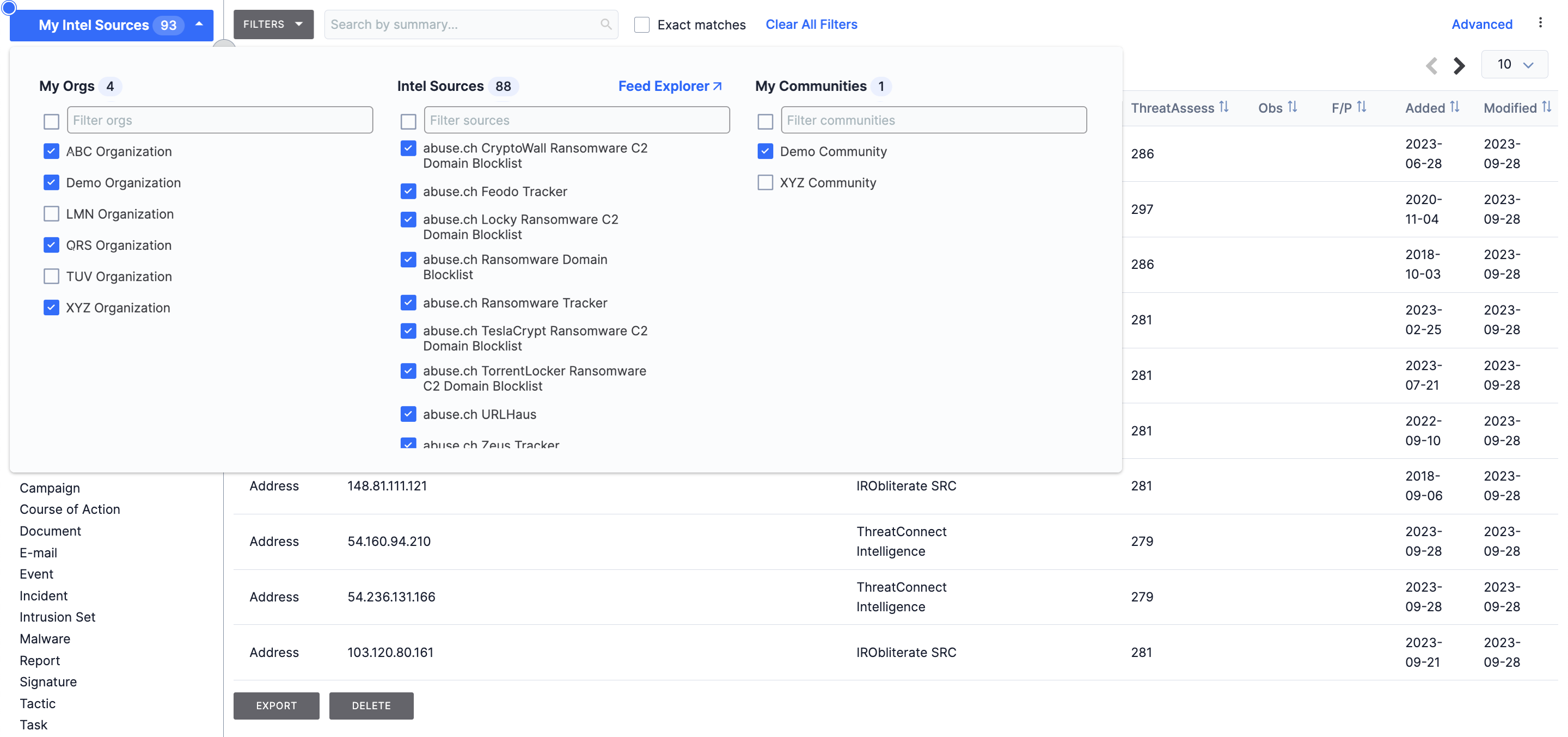
The My Intel Sources selector on the Browse screen will display a My Orgs list from which you can select the Organizations whose data (i.e., Groups, Indicators, Intelligence Requirements, Tags, Tracks, Victims, and Victim Assets) you want to view (Figure 1).
Create
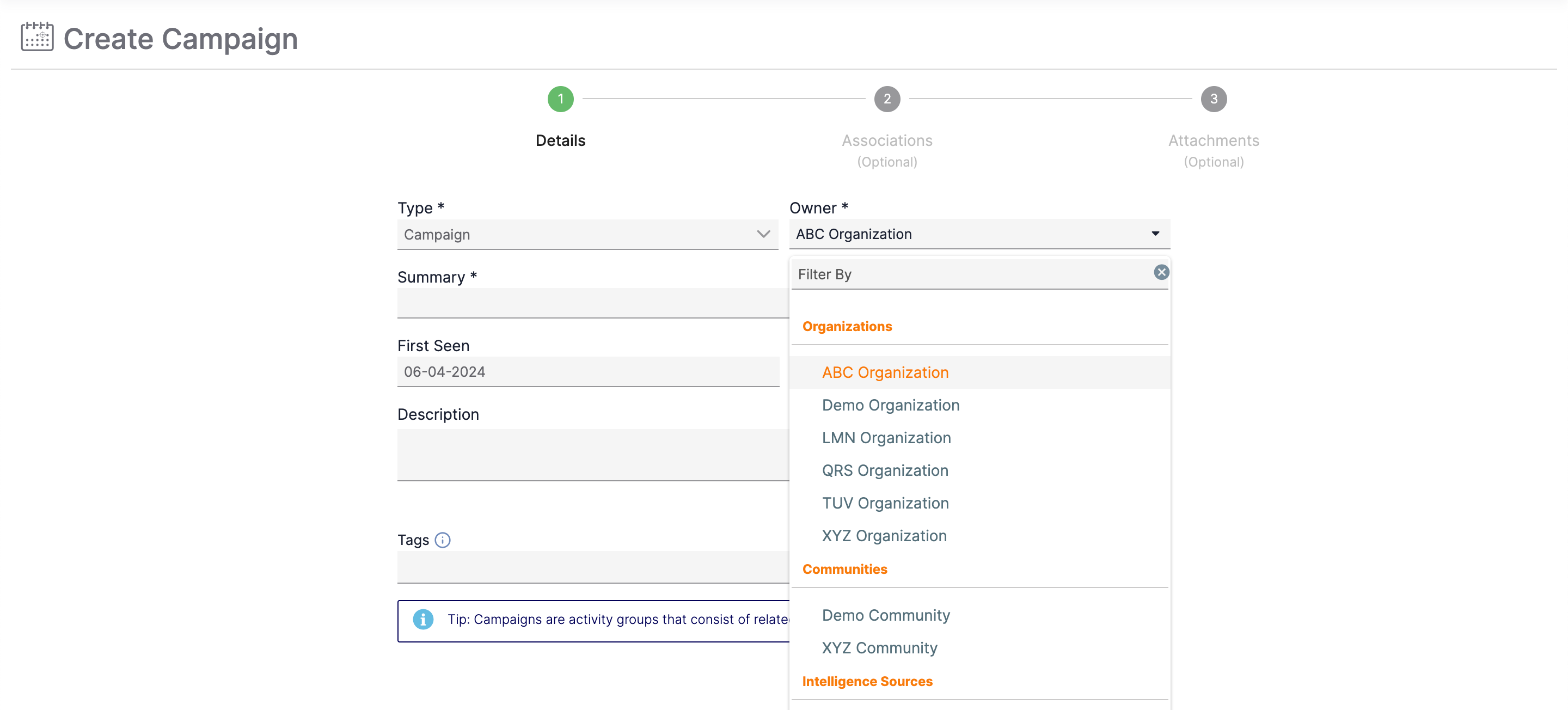
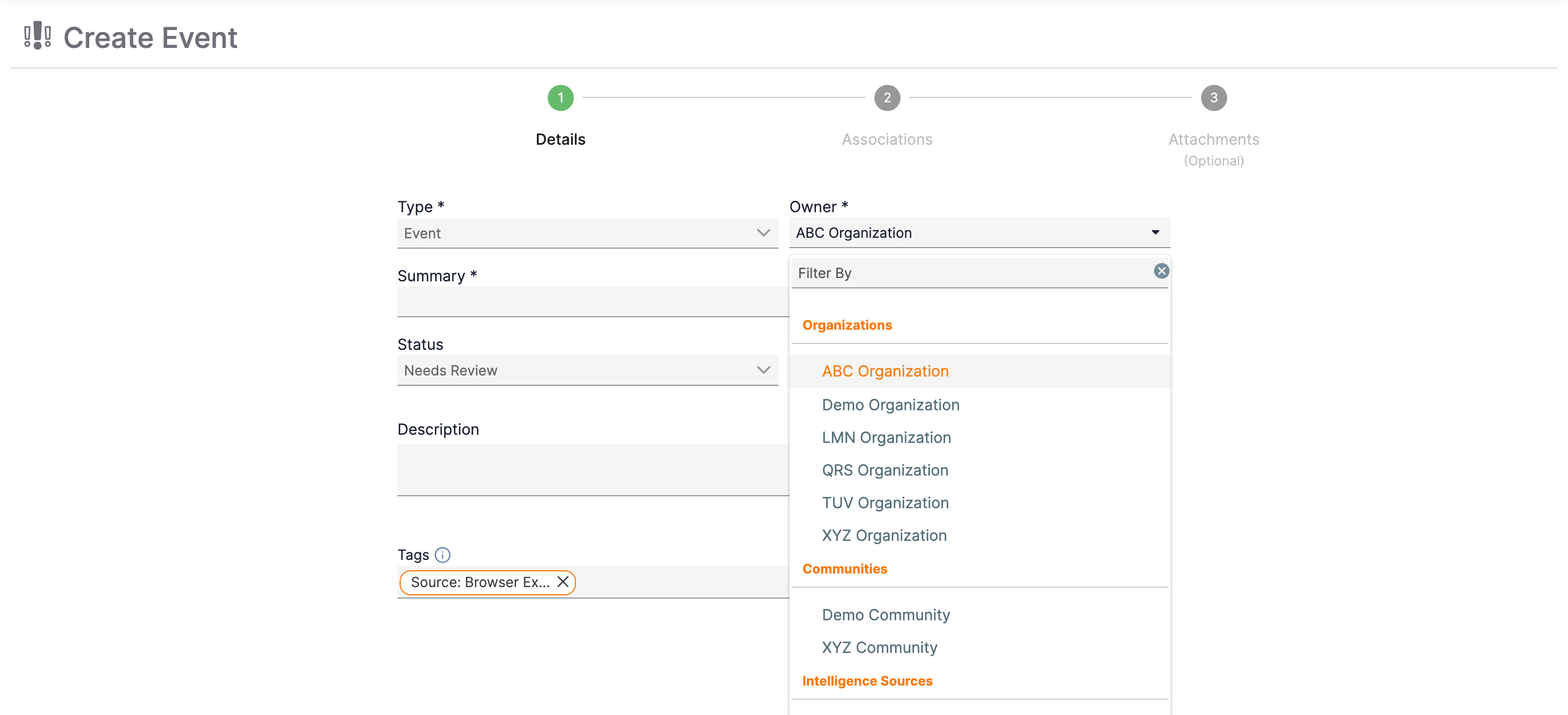
When using the Create option on the top navigation bar to add an object (Indicator, Group, Track, or Victim) to ThreatConnect, you can select any Organization on the ThreatConnect instance from the Owner menu (Figure 2).
Import
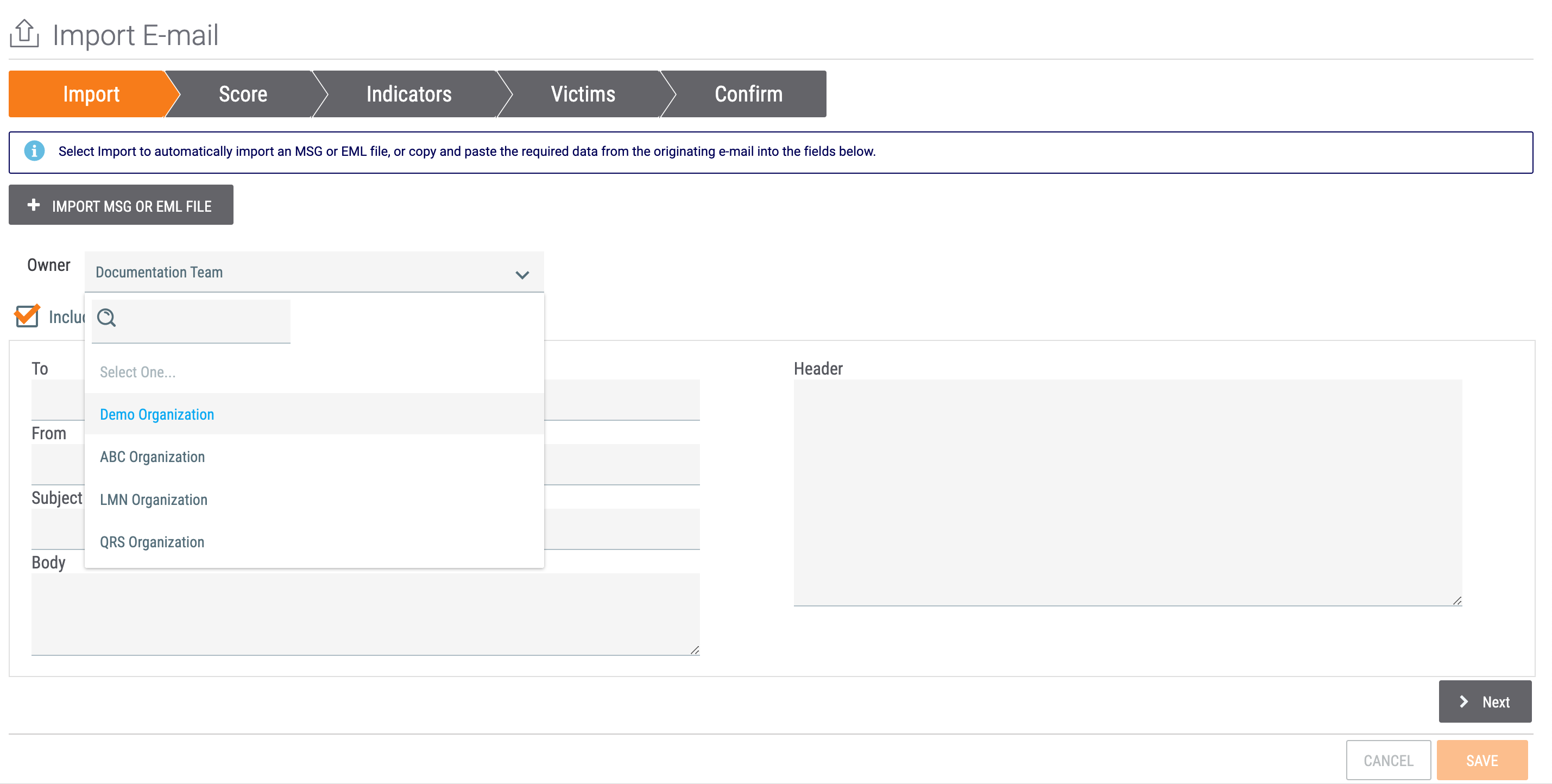
When using the Import option on the top navigation bar to import objects (Email import, structured Indicator import, unstructured Indicator import, Signature import, or Doc Analysis import) you can select any Organization on the ThreatConnect instance from the Owner menu (Figure 3).
Search and Analyze
Search Drawer (Legacy)
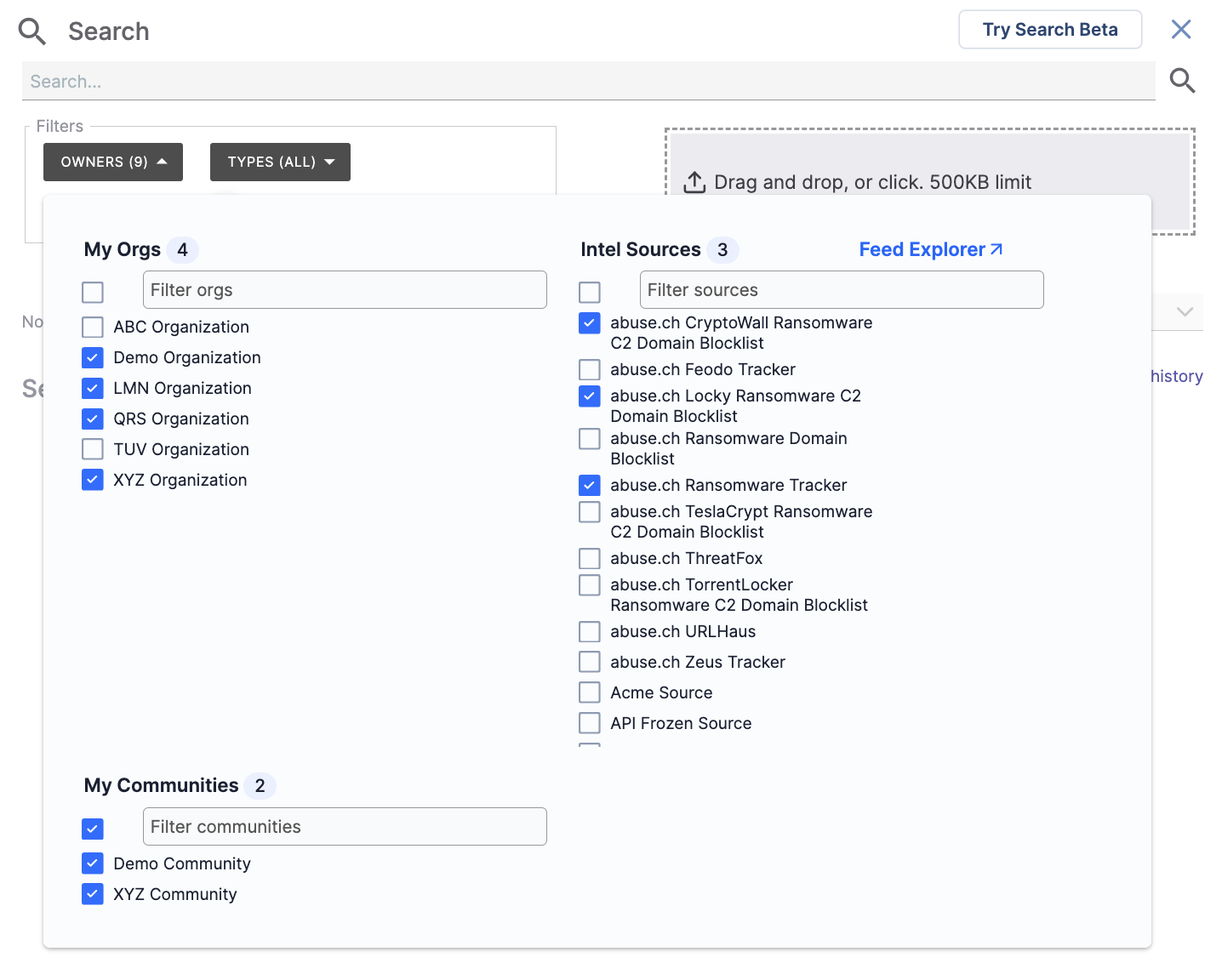
The OWNERS selector in the Search drawer will display a My Orgs list from which you can select the Organizations in which to search for data (Figure 4).
You can also add objects found during searches to any Organization on your instance (Figure 5).
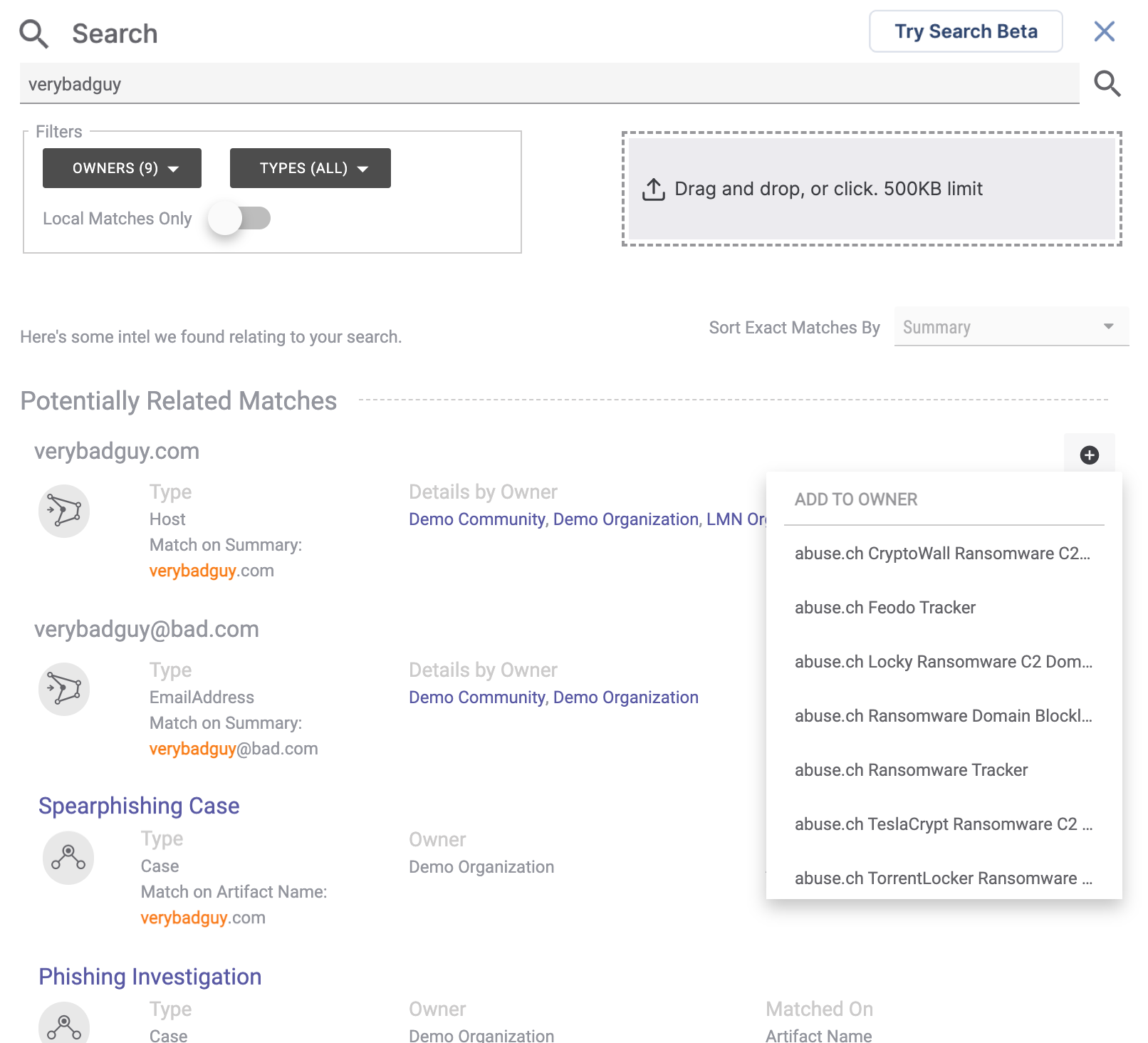
Search Screen (Beta)
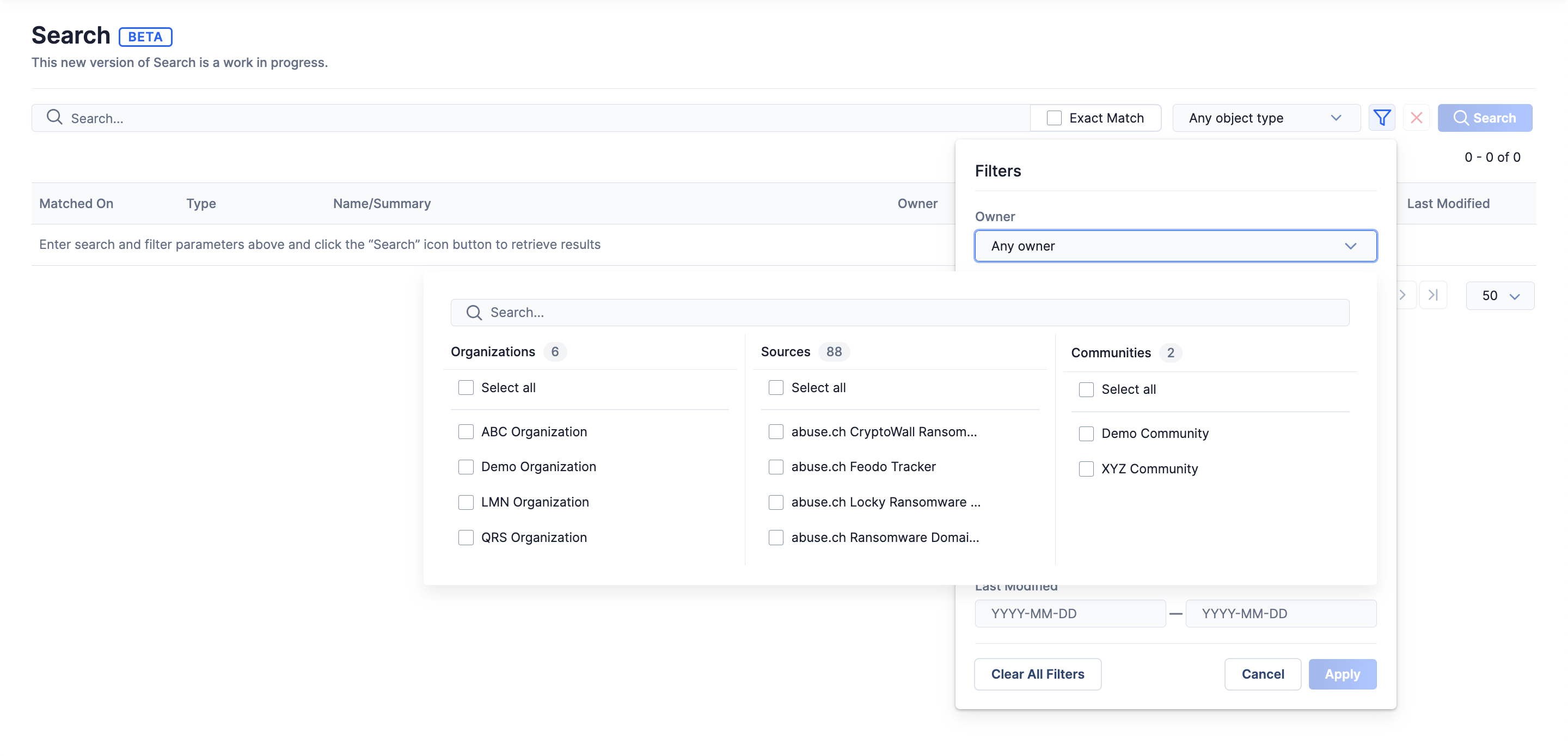
The Owner filter in the Filters menu on the Search screen will display all Organizations in which you can search for data (Figure 6).
menu on the Search screen will display all Organizations in which you can search for data (Figure 6).
The Details Screen
In addition to Communities and Sources, the Owners & Feeds card on the new Details screen and Details drawer (Figure 7) and the Additional Owners card on the legacy Details screen (Figure 8) list all of the other Organizations that own the object you are viewing. Click on the name of an Organization to view the object within that Organization.
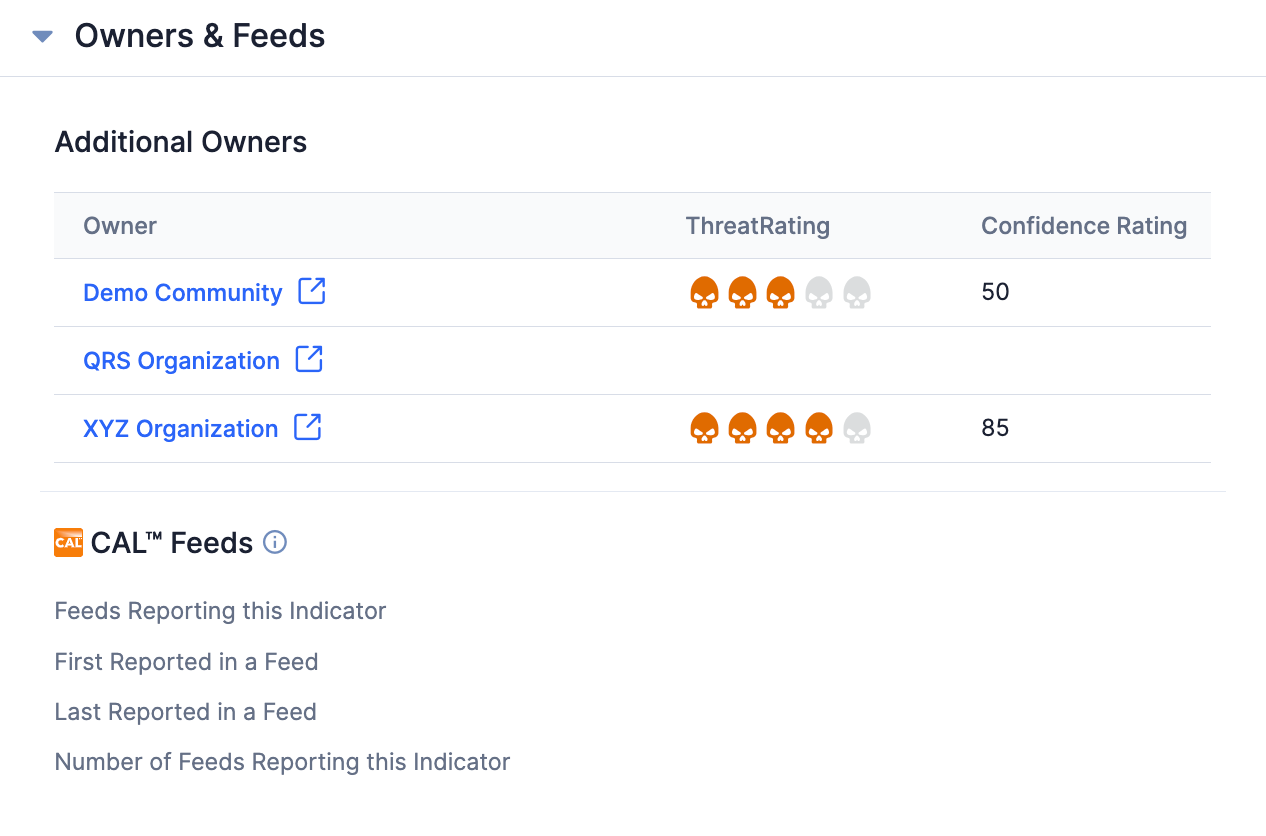
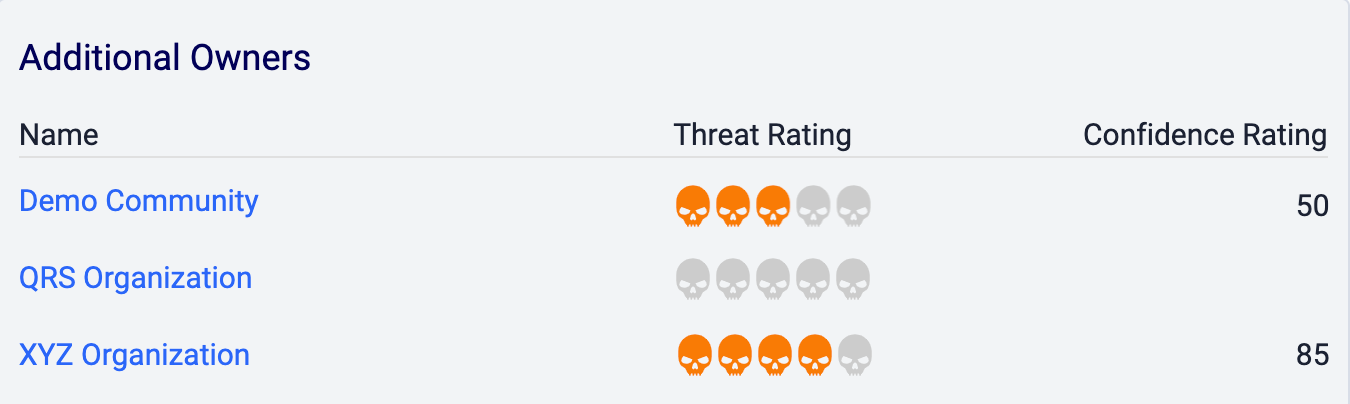
On the new Details screen, you can also use the dropdown at the top left of the header section to select the owners in which to view the object. On the legacy Details screen, you can also use the selector at the upper-right corner of the screen to choose owners in which to view the object. When viewing the object in an Organization other than your home Organization on the legacy Details screen, the label at the upper-left corner of the screen will be SHARED instead of ORGANIZATION.
Cross-Owner Associations
If cross-owner associations are enabled on your ThreatConnect instance, you can view and create associations between objects in the Organizations on your instance and between those in the Communities and Sources to which you have access. In other words, in addition to being able to create associations between objects in your home Organization, Communities, and Sources, you can create associations between objects in the Organizations on your instance (i.e., Organization-to-Organization associations) and associations between objects in any Organization on your instance and the Communities and Sources to which you have access.
Indicator Status
If the ability to change Indicator Status is enabled for your Organization, you can modify Indicator Status in any owner on your ThreatConnect instance.
Threat Graph
When viewing an object that exists in multiple Organizations on your instance while using Threat Graph, you can use the Pivot in ThreatConnect option to explore the object’s associations in each Organization.
ThreatConnect Query Language
You can write TQL queries that search for objects existing in multiple Organizations on your instance. See the “Query for Objects Belonging to Multiple Owners” section of Constructing Query Expressions for more information.
ThreatConnect Intelligence Anywhere
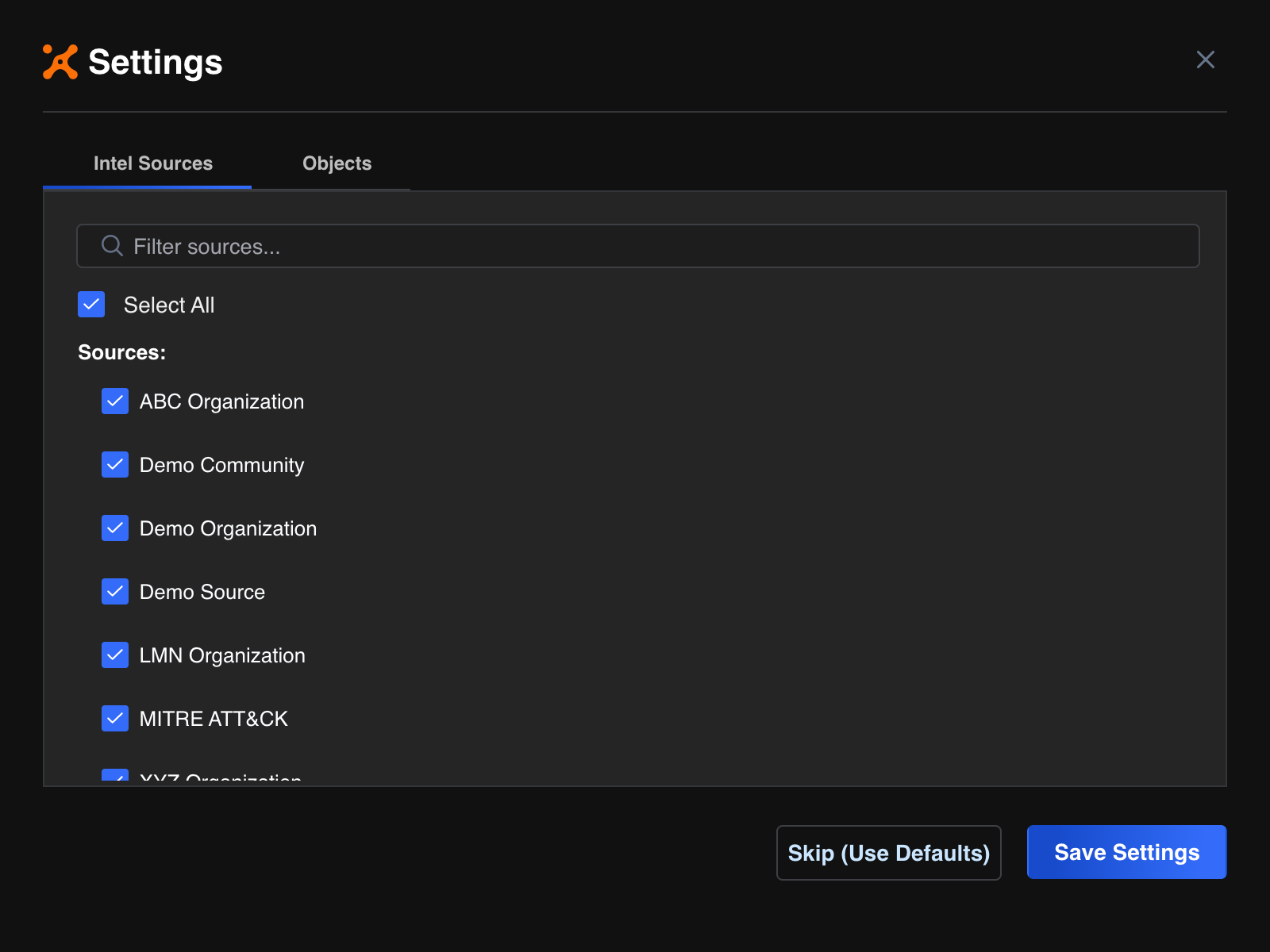
When selecting sources for ThreatConnect Intelligence Anywhere to scan for potential Indicators and Groups, you can select multiple Organizations on your instance (Figure 9).
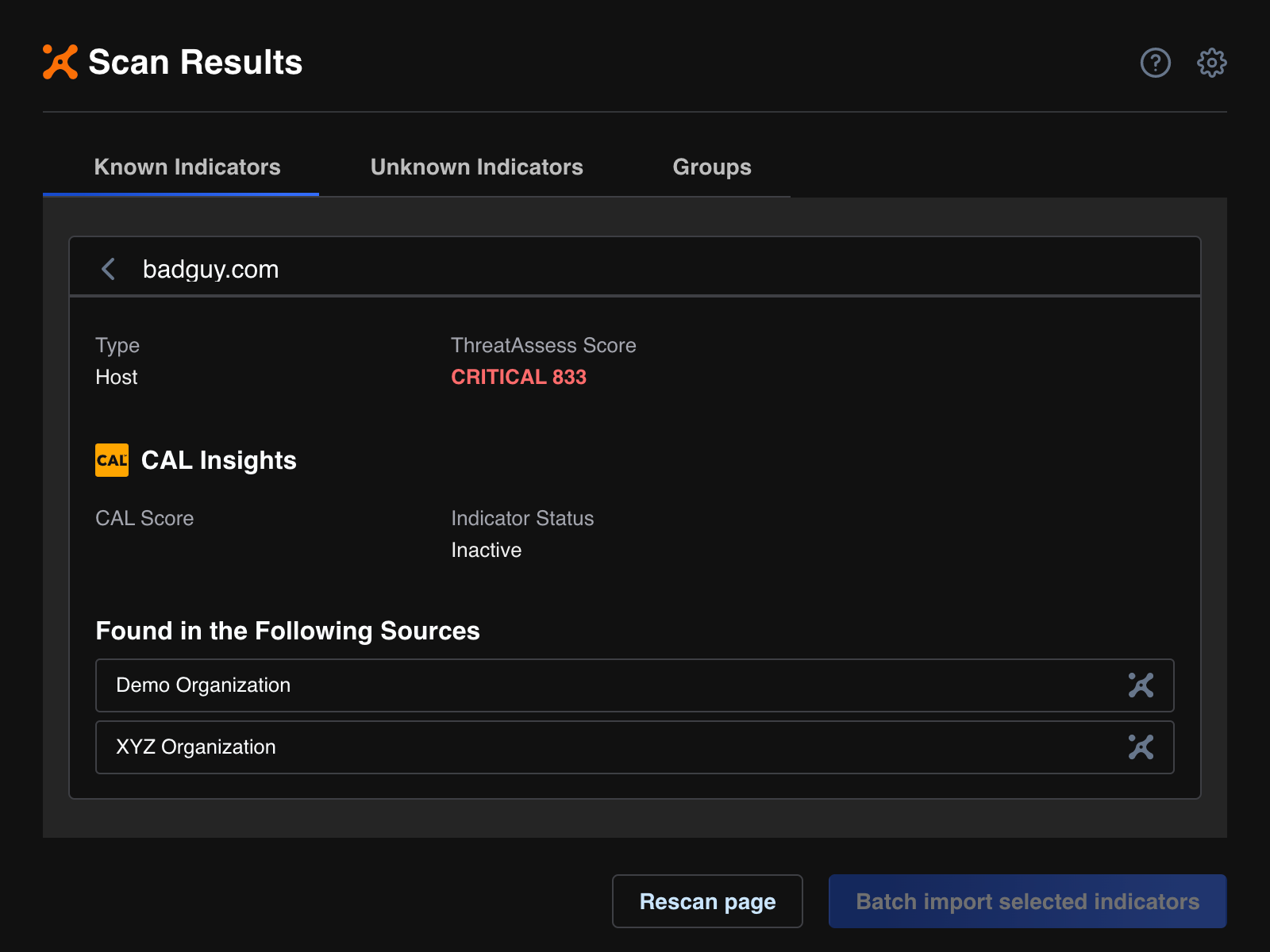
Intelligence Anywhere will indicate when a scan finds objects that are known to exist in multiple Organizations on your instance (Figure 10).
When importing scanned Indicators into ThreatConnect, you can select any Organization on your ThreatConnect instance as the destination owner (Figure 11).
ATT&CK Visualizer
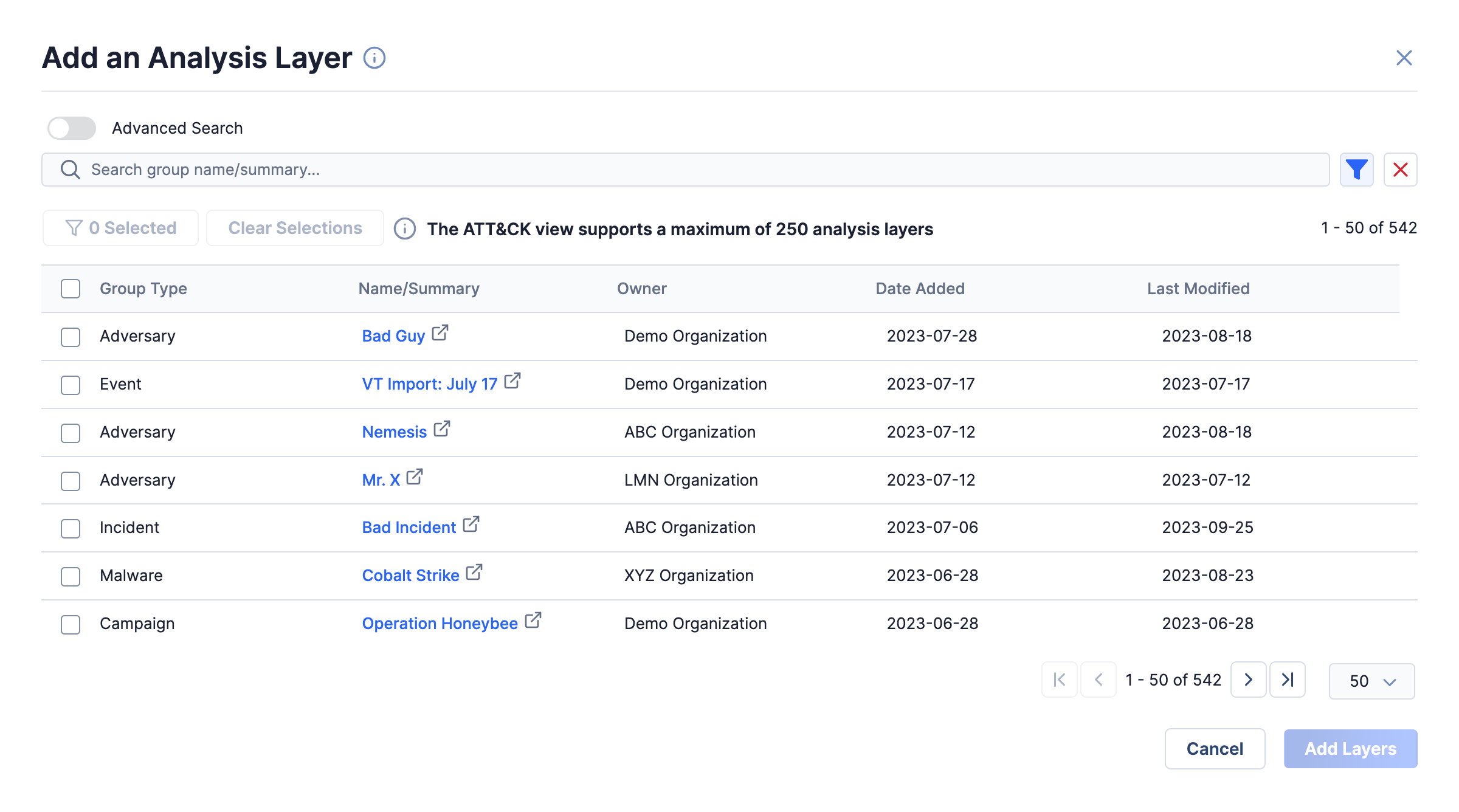
In the ATT&CK® Visualizer, you can add Groups that belong to any Organization on the ThreatConnect instance as analysis layers to a standard ATT&CK view and visualize the MITRE ATT&CK® Enterprise tactics, techniques, and sub-techniques used by the Groups (Figure 12). When selecting Groups to add as analysis layers, you can filter Groups by Organization using the Filters option at the top right of the Add an Analysis Layer window.
option at the top right of the Add an Analysis Layer window.
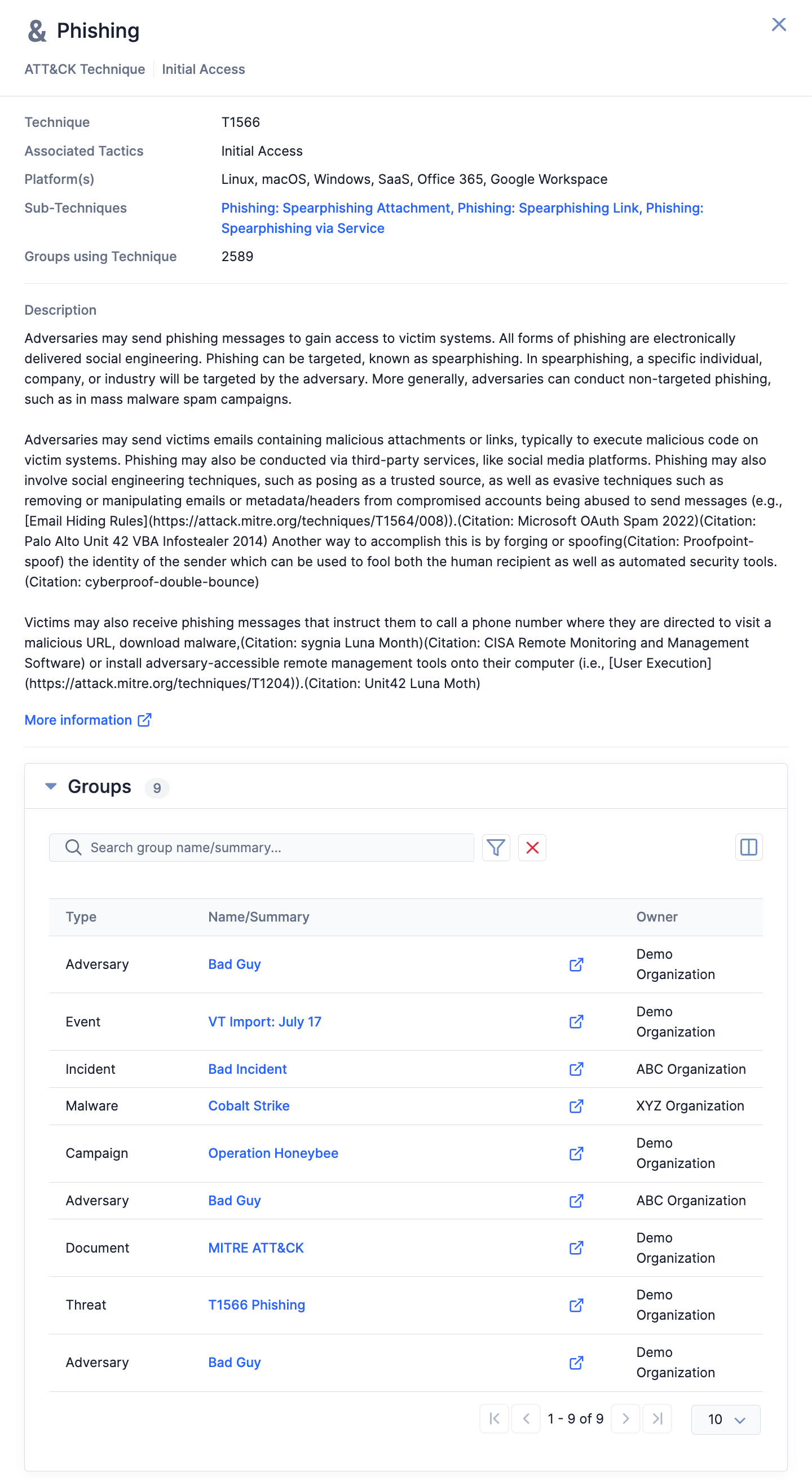
When you select one or more techniques or sub-techniques in the ATT&CK Visualizer, the Selection Details drawer will display Groups across all Organizations with ATT&CK Tags representing the selected items applied to them (Figure 13). Use the Filters  option to the right of the search bar to filter these Groups by Organization, if desired.
option to the right of the search bar to filter these Groups by Organization, if desired.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.


