- 10 Jan 2026
- 8 Minutes to read
-
Print
-
DarkLight
-
PDF
Viewing Search Results for All Object Types
- Updated on 10 Jan 2026
- 8 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The ThreatConnect® search engine lets you search your entire dataset to quickly find data relevant to the item you are investigating. After you run a search of all object types , the search engine returns a results set of Indicators, Groups, Tags, Victims, and Workflow Cases that match the search query, which you can then review and analyze as part of your investigation.
When looking for matches to a search query, the search engine searches an object’s summary and metadata—including Attributes; Descriptions; Case Artifacts, Notes, and Tasks; file and signature contents; Tags; and Victim Assets and Victim details—and provides a relevance-ordered result set based on how closely each result matches the query.
Before You Start
User Roles
- To view and export Indicators, Groups, Tags, or Victims in an Organization, your user account can have any Organization role.
- To view and export Indicators, Groups, Tags, or Victims in a Community or Source, your user account must have a Community role of User, Commenter, Contributor, Editor, or Director for that Community or Source.
- To view and export Cases in an Organization, your user account can have any Organization role except App Developer.
- To create copies of Indicators and add them to an Organization, your user account must have an Organization role of Standard User, Sharing User, Organization Administrator, or App Developer.
- To delete Indicators, Groups, standard Tags, or Victims in an Organization, your user account must have an Organization role of Standard User, Sharing User, Organization Administrator, or App Developer.
- To delete Indicators, Groups, standard Tags, or Victims in a Community or Source, your user account must have a Community role of Editor or Director for that Community or Source.
- To delete Cases in an Organization, your user account must have an Organization role of Organization Administrator.
- To apply Tags to Indicators, Groups, and Victims in an Organization, your user account must have an Organization role of Standard User, Sharing User, Organization Administrator, or App Developer.
- To apply Tags to Cases in an Organization, you must have an Organization role of Standard User, Sharing User, or Organization Administrator.
- To apply Tags to Indicators, Groups, and Victims in a Community or Source, your user account must have a Community role of Contributor, Editor, or Director for that Community or Source.
Prerequisites
- To search your ThreatConnect data and view search results on the Search: All Object Types screen, turn on and configure OpenSearch® and initialize the search index for your ThreatConnect instance on the System Settings screen (must be a System Administrator to perform this action).
- To view and manage search results that are Cases, select the Enable Workflow checkbox on the Permissions tab of the Organization Information window when editing your Organization on the Organizations tab of the Account Settings screen (must be an Accounts Administrator, Operations Administrator, or System Administrator to perform this action).
Viewing Search Results
After you run a search of all object types, the Search: All Object Types screen displays the search results in a paginated table with the following columns (Figure 1):
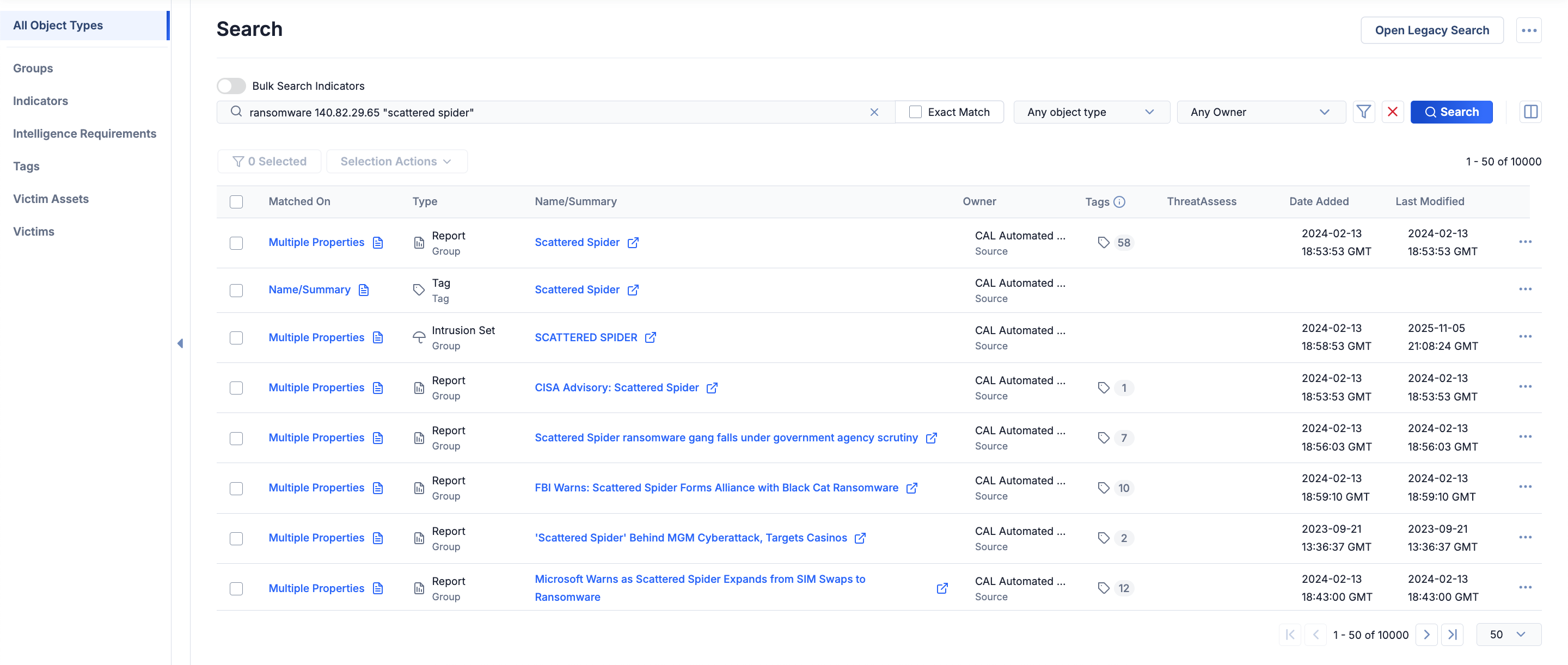
- Matched On: The property of the result that matched the search query. To view details about each property of a result that matched the search query, click the value or
 icon in the Matched On column. Table 1 defines the possible values for this column and the applicable result type for each value.
icon in the Matched On column. Table 1 defines the possible values for this column and the applicable result type for each value. - Type: The result’s type. For Groups and Indicators, the Type column also displays the result's subtype (e.g., Address, Vulnerability).
- Name/Summary: The result’s name/summary.
- Owner: The result’s owner.
- Tags: The Tags applied to the result.
- ThreatAssess: (Indicators only) The result’s ThreatAssess score.
- Date Added: The date and time the result was created in its owner.
- Last Modified: The date and time the result was last modified in its owner.
 in the upper right, selecting the columns to display, and clicking Apply.
in the upper right, selecting the columns to display, and clicking Apply.
| “Matched On” Value | Description | Result Types |
|---|---|---|
| Artifact | The summary of one or more of the result’s Artifacts was a match. | Case |
| Attribute | The value of one or more of the result’s Attributes was a match. | Case, Indicator, Group, Tag, Victim |
| Case Description | The description of the result was a match. | Case |
| Description | The value of one or more of the result’s Description Attributes (default or non-default) was a match. | Indicator, Group, Tag, Victim |
| File Content | The contents of the file uploaded to the result were a match. | Group (Document and Report only) |
| Multiple Properties | Two or more of the result’s properties were a match. | Case, Indicator, Group, Tag, Victim |
| Name/Summary | The result’s name/summary was a match. | Case, Indicator, Group, Tag, Victim |
| Note | The contents of one or more of the result’s Case Notes were a match. | Case |
| Signature | The contents of the signature file uploaded to the result were a match. | Group (Signature only) |
| Tag | The name of one or more standard Tags or ATT&CK® Tags applied to the result was a match. | Case, Indicator, Group, Victim |
| Task | The name of one or more of the result’s Tasks was a match. | Case |
| Task Description | The description of one or more of the result’s Tasks was a match. | Case |
| Victim Asset | The summary of one or more of the result’s Victim Assets was a match. | Victim |
| Victim Nationality | The result’s nationality was a match. | Victim |
| Victim Organization | The result’s organization was a match. | Victim |
| Victim Sub-Organization | The result’s sub-organization was a match. | Victim |
| Victim Work Location | The result’s work location was a match. | Victim |
Viewing Match Details for Search Results
A search result’s Result Details drawer displays each of the result’s properties that matched the search query, with each part of the property that matched the query highlighted in blue. For example, in Figure 2, the following properties of the result matched the search query from Figure 1 (ransomware 140.82.29.65 "scattered spider"): the result’s name/summary, the value of the result’s Source Attribute, the value of the result’s Description Attribute, and the name of one of the result’s standard Tags.
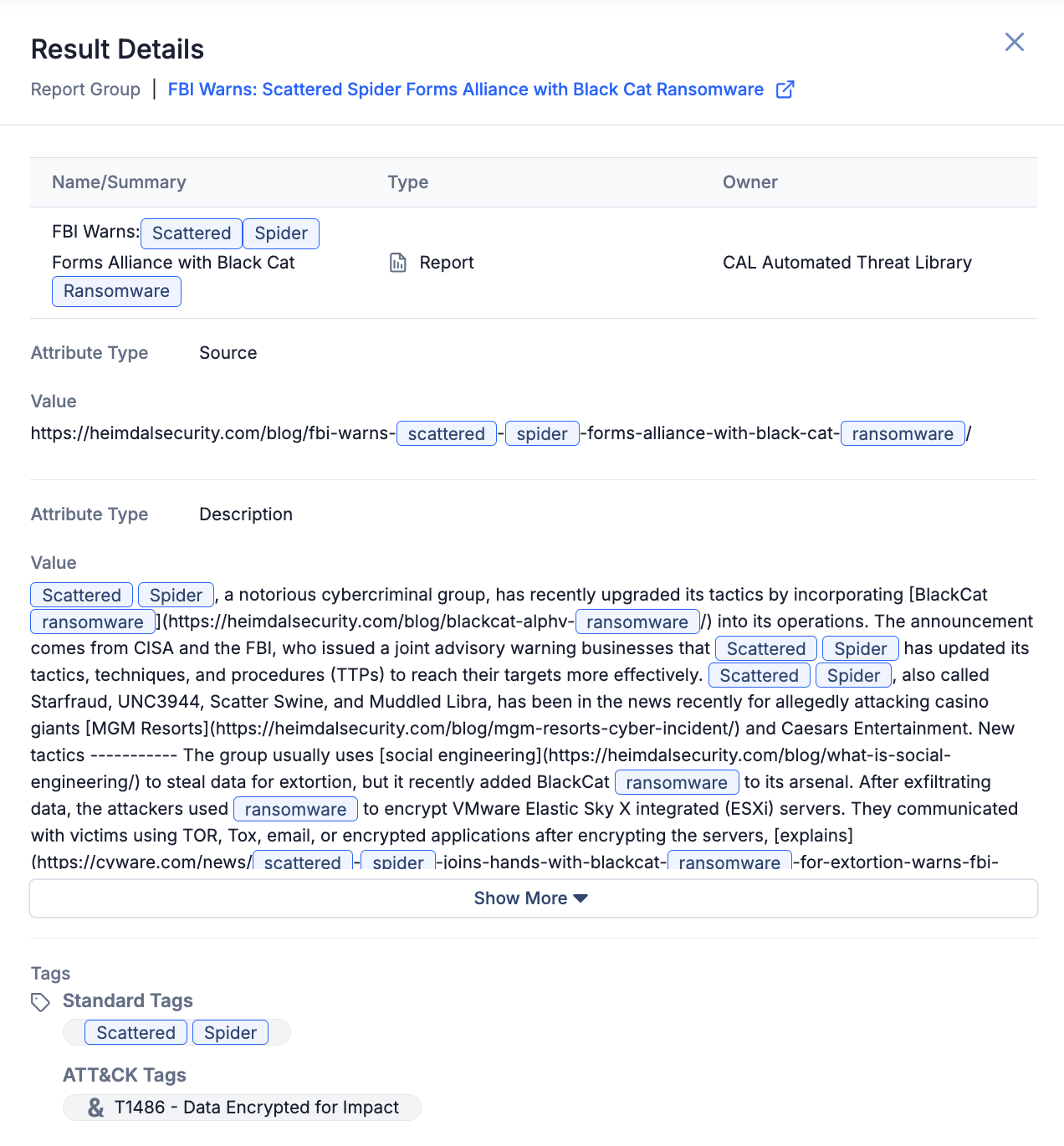
There are two ways to open a search result’s Result Details drawer on the Search: All Object Types screen:
- Click the value or
 icon in the result’s Matched On column.
icon in the result’s Matched On column. - Click the result’s ⋯ menu and select View Match Details.
Viewing Search Result Details
Click a search result’s table row, or click a result’s ⋯ menu and select View Details, to open the Details drawer for the corresponding Case, Group, Indicator, Tag, or Victim and view detailed information about the result.
To open a search result’s Details screen , click the result’s name/summary in the results table on the Search: All Object Types screen.
Managing Search Results
Selection Actions
You can select one or more search results and then use Selection Actions dropdown to perform the following actions:
- Add Tags…: Enter and apply Tags to all selected objects.NoteTags are applied only to objects in owners for which your user account has permission to create data. Tags are not applied to other Tags.
- Export…: Export all selected objects to a comma-separated values (CSV) file.NoteYou can export all objects in the results table, including those on other table pages, to a CSV file by clicking the ⋯ menu at the upper right of the Search: All Object Types screen and selecting Export Returned Objects….
- Add to Organization…: Create copies of all selected Indicators and add them to your Organization.NoteIf no Indicators are selected, the Add to Organization… option will not be available. If both Indicators and other object types (e.g., Groups) are selected, only the Indicators will be added to your Organization.
Search Result Options
You can use a search result’s ⋯ menu to manage and analyze the result. Table 2 describes the options available in the ⋯ menu and the applicable result types for each option.
| Search Result Option | Description | Result Types |
|---|---|---|
| Add to Exclusion List | Add the result to your Organization-level Exclusion List. This option is available only if your user account has an Organization role of Organization Administrator and if the excludeFromDetailsEnabledsystem setting is turned on for your ThreatConnect instance. Important You cannot remove an Indicator from your Organization’s Exclusion List from the Search: All Object Types screen. | Indicator |
| Change Status to Active / Change Status to Inactive | Change the Indicator Status of the result. This option is available only if your user account has permission to modify Indicator Status in the result's owner. | Indicator |
| Create Custom Report | Create a report for the result from scratch or from a report template. This option is available only if your user account has permission to create reports. | Case, Group |
| Delete… | Delete the result from its owner. This option is available only if your user account has the requisite permissions in the result’s owner. Note ATT&CK Tags may not be deleted. | Case, Indicator, Group, Tag, Victim |
| Threat Graph | Open Threat Graph to visualize, explore, and analyze the result’s associations. Note The Threat Graph option is in the Visual Analysis dropdown for Group results. | Case, Indicator, Group, Tag |
| View Details | Open the result’s Details drawer . | Case, Indicator, Group, Tag, Victim |
| View Match Details | Open the Result Details drawer and view details about the result’s properties that matched the search query. | Case, Indicator, Group, Tag, Victim |
| Visual Analysis | Dropdown with the Threat Graph and Visualize ATT&CK options. | Group |
| Visualize ATT&CK | Open the ATT&CK Visualizer and create a standard ATT&CK view with the Group added as an analysis layer. Note The Visualize ATT&CK option is in the Visual Analysis dropdown for Group results. | Group |
Sorting Search Results
You can sort search results by any table column except Matched On. By default, search results are sorted by how closely they match the search query, where objects whose name/summary matches the query are listed at the top, followed by objects with metadata (e.g., an Attribute, a Tag) that matches the query.
Filtering Search Results
The Search: All Object Types screen provides the following options for filtering search results:
- The object type dropdown next to the Exact Match checkbox lets you filter results by the following ThreatConnect object types: Cases, Indicators, Groups, Tags, and Victims. Results are filtered automatically as you select options in the dropdown.
- The owner dropdown next to the Filters
 menu lets you filter results by one or more owners. Results are filtered automatically as you select options in the dropdown.
menu lets you filter results by one or more owners. Results are filtered automatically as you select options in the dropdown. - The Filters
 menu lets you filter results by object metadata. After selecting and configuring filters, click Apply. Results may be filtered by the following metadata:
menu lets you filter results by object metadata. After selecting and configuring filters, click Apply. Results may be filtered by the following metadata:- Object Subtypes (Indicators and Groups only)
- Date Added
- Last Modified
- Matched On (i.e., the property that matched the search query)
- ThreatAssess (Indicators only)
 menu apply only to results that are Groups and Indicators, respectively. If you configure the object type dropdown to exclude Groups or Indicators from the search results, the Group Type or Indicator Type filter, respectively, will be grayed out.
menu apply only to results that are Groups and Indicators, respectively. If you configure the object type dropdown to exclude Groups or Indicators from the search results, the Group Type or Indicator Type filter, respectively, will be grayed out.ThreatConnect® is a registered trademark of ThreatConnect, Inc.
OpenSearch® is a registered trademark of Amazon Web Services.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.
20075-06 v.04.A


