- 16 Feb 2024
- 16 Minutes to read
-
Print
-
DarkLight
-
PDF
Owner Role Permissions Definitions
- Updated on 16 Feb 2024
- 16 Minutes to read
-
Print
-
DarkLight
-
PDF
Intel Access Permissions
Organization
The settings defined in this section apply to a user’s permissions for Organization administration. They are available on the Access Control tab of the Create Owner Role (Figure 1) or Edit Owner Role window.
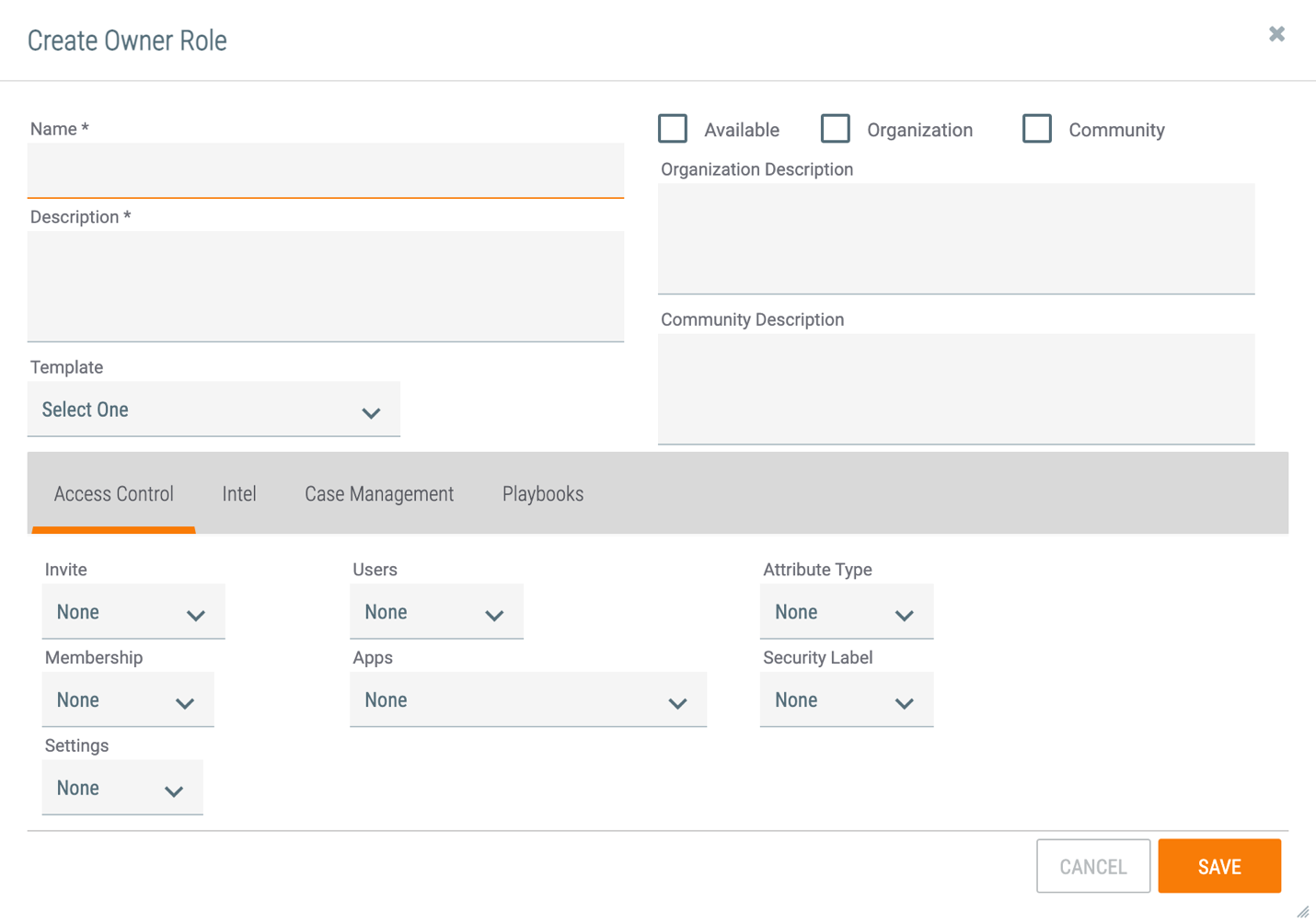
- Invite:
- None: The user may not view, accept, or delete invitations on behalf of the Organization to join a Community.
- Allowed: The user may view, accept, and delete invitations on behalf of the Organization to join a Community.
- Membership:
- None: The user may not view the profile page for users and Organizations by clicking on the user’s or Organization’s name throughout ThreatConnect.NoteThis restriction applies only to profile pages belonging to the Organization within which the permission has been set.
- Read or Modify: The user may view the profile page for users and Organizations by clicking on the user’s or Organization’s name throughout ThreatConnect.
- None: The user may not view the profile page for users and Organizations by clicking on the user’s or Organization’s name throughout ThreatConnect.
- Settings:
- None: The user may not view or administrate the settings of the Organization. That is, the Org Settings option will not be available in the Settings
 menu.
menu. - Read: The user may view, but not administrate, the settings of the Organization. They may edit the default dashboard for the Organization and any shared dashboards, but may not set the default dashboard for the Organization.
- Full: The user may view and administrate the settings of the Organization. They may edit and delete any dashboard in the Organization, and they have permission to set the default dashboard for the Organization.
- None: The user may not view or administrate the settings of the Organization. That is, the Org Settings option will not be available in the Settings
- Users:
- None: The user may not view, create, modify, or delete Users in the Organization on the Membership tab of the Organization Settings screen. The only user they will be able to view in this tab is themselves.
- Read: The user may view, but not create, modify, or delete, users in the Organization on the Membership tab of the Organization Settings screen.
- Create: The user may view, create, modify, but not delete, users in the Organization on the Membership tab of the Organization Settings screen.
- Full: The user may view, create, modify, and delete users in the Organization on the Membership tab of the Organization Settings screen.NoteUsers with Create or Full permission cannot create, modify, or delete users whose System role ranks higher than theirs. For example, a user with a System role of User and an Organization role of Organization Administrator cannot create, modify, or delete a user with a System role of Operations Administrator.
- Apps:
- None: The user may not access the App Builder.
- App Builder build allowed: The user may view and build apps in the App Builder.
- App Builder release allowed: The user may view, build, and release apps in the App Builder.
- Attribute Type:
- Read: The user may view System and non-System Attribute Types, but not create, modify, or delete any Attribute Types in the Organization.
- Create: The user may view System Attribute Types and view, create, modify, but not delete, Attribute Types in the Organization.
- Full: The user may view System Attribute Types and view, create, modify, and delete non-System Attribute Types in the Organization.
- Security Label:
- Read: The user may view, but not apply or administrate, Security Labels in the Organization.
- Create: The user may view Security Labels and apply them to and remove them from intelligence objects, but they may not administrate Security Labels in the Organization.
- Full: The user may view Security Labels, applythem to and remove them from intelligence objects, and administrate them in the Organization.NoteAdministration of Security Labels includes creating, editing, deleting, and consolidation new, non-Systemwide Security Label. See the “Security Labels” section in the ThreatConnect Organization Administration Guide for more information.
Community
The settings defined in this section apply to a user’s permissions for Community administration. They are available on the Access Control tab of the Create Owner Role (Figure 1) or Edit Owner Role window.
- Invite:
- None: The user may not send invitations to join the Community.
- Allowed: The user user may send invitations to join the Community.
- Membership:
- None: The user may not access or change membership information for the Community.
- Read: The user may view the membership of the Community, but may not change Community roles.
- Modify: The user may view the membership of the Community, change Community roles for existing membership, and change default Community roles for new members.
- Settings:
- None: The user may not view or administrate the settings of the Community.
- Read: The user may view, but not administrate, the settings of the Community.
- Full: The user may view and administrate the settings of the Community.
- Users: The Users permissions do not apply to Communities. Making selections from this dropdown menu has no effect on the user’s Community administration permissions.
- Apps: The Apps permissions do not apply to Communities. Making selections from this dropdown menu has no effect on the user’s Community administration permissions.
- Attribute Type:
- Read: The user may view System and non-System Attribute Types, but not create, modify, or delete any Attribute Types in the Community.
- Create: The user may view System Attribute Types and view, create, modify, but not delete, Attribute Types in the Community.
- Full: The user may view System Attribute Types and view, create, modify, and delete non-System Attribute Types in the Community.
- Security Label:
- None: The user may not access threat intelligence in the Community.
- Read: The user may view, but not apply or administrate, Security Labels in the Community.
- Create: The user may view Security Labels and apply them to and remove them from intelligence objects, but they may not administrate Security Labels in the Community.
- Full: The user may view Security Labels, applythem to and remove them from intelligence objects, and administrate them in the Community.NoteAdministration of Security Labels includes creating, editing, deleting, and consolidation new, non-Systemwide Security Label. See the “Security Labels” section in the ThreatConnect Organization Administration Guide for more information.
Threat Intelligence Permissions
Organization
The settings defined in this section apply to a user’s permissions for threat intelligence in their Organization. They are available on the Intel tab of the Create Owner Role or Edit Owner Role window (Figure 2).
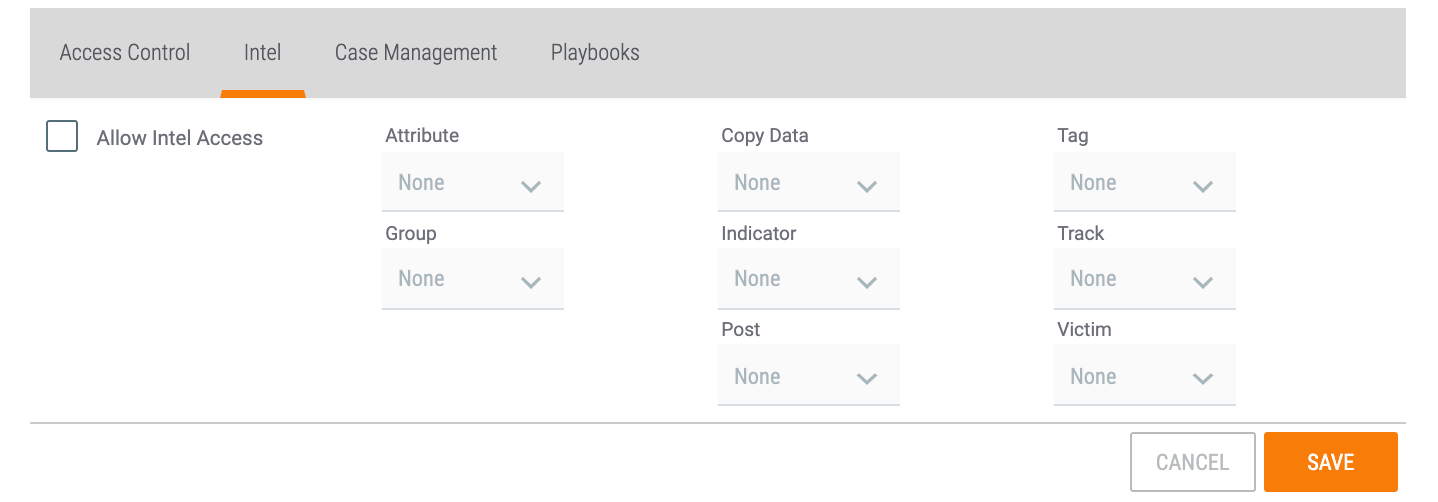
- Attribute:
- None: The user may not access threat intelligence in the Organization.
- Read: The user may view, but not create, modify, or delete, Attributes in the Organization.
- Create: The user may view, create, and modify, but not delete, Attributes in the Organization.
- Full: The user may view, create, modify, and delete Attributes in the Organization.
- Indicator:
- None: The user may not access threat intelligence in the Organization.
- Read: The user may view, but not create, modify, or delete, Indicators in the Organization.
- Create: The user may view, create, and modify, but not delete, Indicators in the Organization.NoteThis permission level allows the user to modify an Indicator’s Confidence Rating, Threat Rating, and associations and to report the Indicator as a false positive. It does not allow the user to modify Indicator Status.
- Full: The user may view, create, modify, and delete Indicators in the Organization.NoteThis permission level allows the user to modify an Indicator’s Confidence Rating, Threat Rating, and associations and to report the Indicator as a false positive. It also allows the user to modify Indicator Status.
- Group:NotePermission levels for Groups in an Organization also apply to Intelligence Requirements (IRs) in an Organization.
- None: The user may not access threat intelligence in the Organization.
- Read: The user may view, but not create, update analysis for, or delete, Groups in the Organization.
- Create: The user may view, create, and update analysis for, but not delete, Groups in the Organization. This permission level also allows the user to modify a Group’s associations.
- Full: The user may view, create, update analysis for, and delete Groups in the Organization. This permission level also allows the user to modify a Group’s associations.
- Track:
- None: The user may not access threat intelligence in the Organization.
- Read: The user may view, but not create, modify, or delete, Tracks in the Organization.
- Create: The user may view, create, and modify, but not delete, Tracks in the Organization.
- Full: The user may view, create, modify, and delete Tracks in the Organization.
- Victim:
- None: The user may not access threat intelligence in the Organization.
- Read: The user may view, but not create, modify, or delete, Victims in the Organization.
- Create: The user may view, create, and modify, but not delete, Victims in the Organization. The user may also add, but not modify or delete, Victim Assets via the Assets tab of a Victim’s Details screen.NoteThis permission level allows the user to modify information on the Details card on the Overview tab of a Victim’s Details screen and to modify a Victim’s associations.
- Full: The user may view, create, modify, and delete Victims in the Organization. The user may also add, modify, and delete Victim Assets via the Assets tab of a Victim’s Details screen.NoteThis permission level allows the user to modify information on the Details card on the Overview tab of a Victim’s Details screen, to modify a Victim’s associations, and to edit the name of a Victim.
- Tag:
- None: The user may not access threat intelligence in the Organization.
- Read: The user may view, but not apply/remove, create, modify, or delete, Tags in the Organization.
- Full: The user may view, apply/remove, create, modify, and delete Tags in the Organization.
- Copy Data:
- None: The user may not contribute Groups from the Organization to Communities and Sources or copy Groups from Communities and Sources to the Organization.
- Allowed: The user may contribute Groups from the Organization to Communities and Sources and copy Groups from Communities and Sources to the Organization.ImportantIn order to copy data from or contribute data to an Organization, the user must have a Community role of Editor, Director, or Contributor.
- Post:
- None: The user may not access threat intelligence in the Organization.
- Read: The user may view, but not create, modify, or delete, Posts in the Organization. If the user once had permission to create Posts, they may still delete Posts they created in the past, but they may not delete the Posts of other users.
- Create: The user may view, create, and reply to Posts in the Organization. They may delete Posts they have created, but not the Posts of other users.
- Full: The user may view, create, reply to, and delete Posts in the Organization.
Community
The settings defined in this section apply to a user’s permissions for threat intelligence in their Community. They are available on the Intel tab of the Create Owner Role or Edit Owner Role window (Figure 2).
- Attribute:
- None: The user may not access threat intelligence in the Community.
- Read: The user may view, but not create, modify, or delete, Attributes in the Community.
- Create: The user may view, create, and modify, but not delete, Attributes in the Community.
- Full: The user may view, create, modify, and delete Attributes in the Community.
- Indicator:
- None: The user may not access threat intelligence in the Community.
- Read: The user may view, but not create, modify, or delete, Indicators in the Community.
- Create: The user may view, create, and modify, but not delete, Indicators in the Community.NoteThis permission level allows the user to modify an Indicator’s Confidence Rating, Threat Rating, and associations and to report the Indicator as a false positive. It does not allow the user to modify Indicator Status.
- Full: The user may view, create, modify, and delete Indicators in the Community.NoteThis permission level allows the user to modify an Indicator’s Confidence Rating, Threat Rating, and associations and to report the Indicator as a false positive. It also allows the user to modify Indicator Status.
- Group:
- None: The user may not access threat intelligence in the Community.
- Read: The user may view, but not create, update analysis for, or delete, Groups in the Community.
- Create: The user may view, create, and update analysis for, but not delete, Groups in the Community. This permission level also allows the user to modify a Group’s associations.
- Full: The user may view, create, update analysis for, and delete Groups in the Community. This permission level also allows the user to modify a Group’s associations.
- Track:
- None: The user may not access threat intelligence in the Community.
- Read: The user may view, but not create, modify, or delete, Tracks in the Community.
- Create: The user may view, create, and modify, but not delete, Tracks in the Community.
- Full: The user may view, create, modify, and delete Tracks in the Community.
- Victim:
- None: The user may not access threat intelligence in the Community.
- Read: The user may view, but not create, modify, or delete, Victims in the Community.
- Create: The user may view, create, and modify, but not delete, Victims in the Community. The user may also add, but not modify or delete, Victim Assets via the Assets tab of a Victim’s Details screen.NoteThis permission level allows the user to modify information on the Details card on the Overview tab of a Victim’s Details screen and to modify a Victim’s associations.
- Full: The user may view, create, modify, and delete Victims in the Community. The user may also add, modify, and delete Victim Assets via the Assets tab of a Victim’s Details screen.NoteThis permission level allows the user to modify information on the Details card on the Overview tab of a Victim’s Details screen, to modify a Victim’s associations, and to edit the name of a Victim.
- Tag:
- None: The user may not access threat intelligence in the Community.
- Read: The user may view, but not apply/remove, create, modify, or delete,Tags in the Community.
- Full: The user may view, apply/remove, create, modify, and delete Tags in the Community.
- Copy Data:
- None: The user may not copy Groups from the Community to their Organization or contribute Groups from their Organization to the Community.
- Allowed: The user may copy Groups from the Community to the default Organization and contribute Groups from their Organization to the Community.ImportantIn order to contribute data to or copy data from a Community, the user must have an Organization Role of Sharing User or Organization Administrator.
- Post:
- None: The user may not access threat intelligence in the Community.
- Read: The user may view, but not create or modify, Posts in the Community. If the user once had permission to create Posts, they may still delete Posts they created in the past, but they may not delete the Posts of other users.
- Create: The user may view, create, and reply to Posts in the Community. They may delete Posts they have created, but not the Posts of other users.
- Full: The user may view, create, reply to, and delete Posts in the Community.
Workflow Permissions
The settings defined in this section apply to a user’s permissions for Workflow in their Organization. They are available on the Case Management tab of the Create Owner Role or Edit Owner Role window (Figure 3).
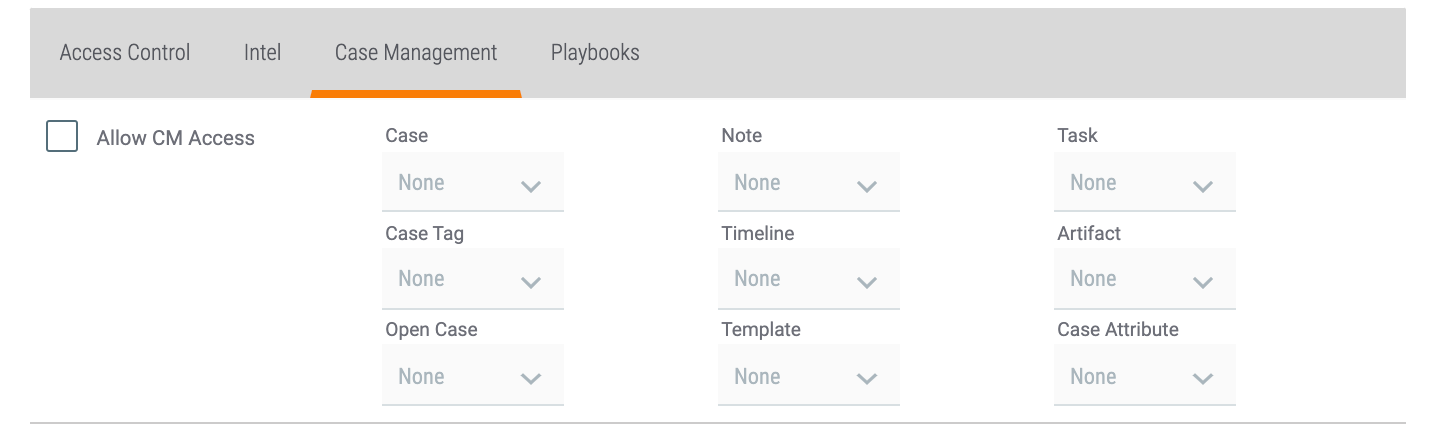
- Case:
- None: The user may not access any of the Workflow functionality in ThreatConnect.
- Read: The user may view, but not edit or delete, Cases in the Organization.
- Edit: The user may view and edit, but not delete, Cases in the Organization.
- Full: The user may view, edit, and delete Cases in the Organization.
- Case Tag:
- None: The user may not access any of the Workflow functionality in ThreatConnect.
- Read: The user may view, but not create, edit, or delete, Case Tags in the Organization.
- Edit Own: The user may view and create Case Tags in the Organization. They may edit and delete only Case Tags in Cases that are assigned to them.
- Edit All: The user may view, create, edit, or delete any Case Tag in the Organization.
- Open Case:
- None: The user may not create a Workflow Case.
- Create From Template: The user may create new Cases in the Organization from Workflows. They may not create Cases without a Workflow.
- Create All: The user may create new Cases in the Organization from, or without, Workflows.
- Note:
- None: The user may not view, create, edit, or delete Notes in Cases in the Organization.
- Read: The user may view, but not create, edit, or delete, Notes in Cases in the Organization.
- Create: The user may view and create Notes in Cases in the Organization. The user may also edit Notes they have created. The user may not edit the Notes created by other users, and they may not delete any Notes in Cases in the Organization.NoteCase Notes “belong” to the last user who edited them. A user with Create permission will not be able to edit a Note they have created if the Note has been edited by a user with Full permission.
- Full: The user may view, create, edit, and delete Notes in Cases in the Organization.
- Timeline:
- None: The user may not access any of the Workflow functionality in ThreatConnect.
- Read: The user may view, but not create, edit, or delete, Timeline Events in Cases in the Organization.
- Create: The user may view, create, and edit, but not delete, Timeline Events in Cases in the Organization.NoteSystem-created Timeline Events may not be edited or deleted.
- Full: The user may view, create, edit, and delete Timeline Events in Cases in the Organization.NoteSystem-created Timeline Events may not be edited or deleted.
- Template:
- None: The user may not access any of the Workflow functionality in ThreatConnect.
- Read: The user may view, but not create, edit, or delete, Workflows in the Organization.
- Edit: The user may view, create, and edit, but not delete, existing Workflows in the Organization.
- Full: The user may view, create, edit, and delete Workflows in the Organization.NoteThese permissions apply to the Workflows tab. The Templates tab, which displays all System-level and TC Exchange™ Templates available for copy into Organizations as Workflows, is not available to Read Only Users, Read Only Commenters, and users who cannot access Workflow in general (i.e., App Developers). All other Organization roles may access the Templates tab and copy Templates into an Organization as Workflows. Only users with a System role of Administrator may add Templates to this tab (via the TC Exchange Settings screen or by using the + button on this tab to import a new Template).
- Task:
- None: The user may not access any of the Workflow functionality in ThreatConnect.
- Read: The user may view, but not create, edit, or delete, Workflow Tasks in the Organization.
- Edit Own: The user may view and create Workflow Tasks in the Organization. They may edit only Tasks for which they are the assignee. They may not delete any Tasks.
- Edit All: The user may view, create, and edit, but not delete, any Workflow Task, regardless of assignee, in the Organization.
- Full: The user may view, create, edit, and delete any Workflow Task, regardless of assignee, in the Organization.
- Artifact:
- None: The user may not access any of the Workflow functionality in ThreatConnect.
- Read: The user may view, but not create, edit, or delete, Artifacts in the Organization.
- Edit Own: The user may view and create Artifacts in the Organization. They may edit only Artifacts that they have created. They may not delete any Artifacts.
- Delete Own: The user may view and create Artifacts in the Organization. They may edit and delete only Artifacts that they have created. They may not edit or delete Artifacts created by other users.
- Edit All: The user may view and create Artifacts in the Organization. They may edit any Artifact created by any user in the Organization. They may not delete any Artifacts.
- Delete All: The user may view and create Artifacts in the Organization. They may edit and delete any Artifact.
- Case Attribute:
- None: The user may not access any of the Workflow functionality in ThreatConnect.
- Read: The user may view, but not edit or delete, Case Attributes in the Organization.
- Create: The user may view and create, but not delete, Case Attributes in the Organization.
- Full: The user may view, create, and delete Case Attributes in the Organization.
Playbooks Permissions
The settings defined in this section apply to a user’s permissions for Playbooks in their Organization. They are available on the Playbooks tab of the Create Owner Role or Edit Owner Role window (Figure 4).
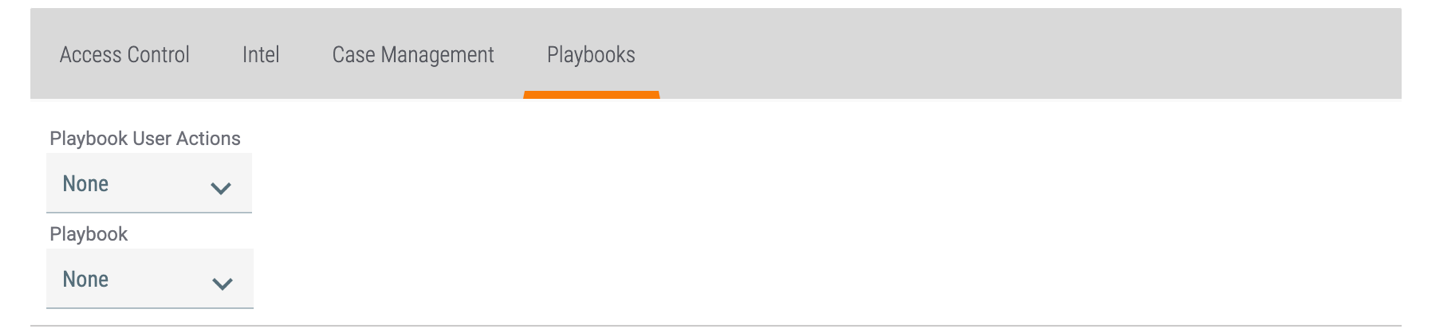
- Playbook User Actions:
- None: The user may not execute Playbooks with UserAction Triggers from the Details screen for Indicators, Groups, Tracks, or Victims or within Threat Graph for Indicators.
- Execute: The user may execute Playbooks with UserAction Triggers from the Details screen for Indicators, Groups, Tracks, or Victims or within Threat Graph for Indicators.
- Playbook:
- None: The user may not access Playbooks in the Organization.
- Read: The user may view, but not create, modify, activate, or delete, Playbooks in the Organization.
- Create: The user may view, create, and modify, but not activate or delete, Playbooks in the Organization.
- Activate: The user may view, create, modify, and activate, but not delete, Playbooks in the Organization.
- Full: The user may view, create, activate, modify, and delete Playbooks in the Organization.
ThreatConnect® is a registered trademark, and TC Exchange™ is a trademark, of ThreatConnect, Inc.
20095-06 v.05.A


