- 16 Dec 2025
- 7 Minutes to read
-
Print
-
DarkLight
-
PDF
CAL 3.14 Release Notes
- Updated on 16 Dec 2025
- 7 Minutes to read
-
Print
-
DarkLight
-
PDF
CAL Doc Analysis Service Improvements
New Automated Detection-Signature Extraction
Every day, analysts comb through endless threat reports and technical blogs, searching for and extracting the critical detection logic hidden within walls of text. Now, with the Collective Analytics Layer (CAL™) 3.14 release, the CAL Doc Analysis Service’s new Automated Detection-Signature Extraction capability automates this time-consuming and tedious process. Harnessing the power of AI, it reads between the lines to identify, extract, and transform these elusive detection rules into actionable, machine-readable intelligence. Available for Report Groups in the CAL Automated Threat Library Source, this feature recognizes a wide array of code-based and product-specific signatures, extracts them in full, and enriches them with intelligent AI-generated metadata, making your workflow faster, sharper, and more effective.
Code Rules
The following rule types are generic detection formats often used across multiple platforms:
- Yara Rules
- Yara-L Rules
- Sigma (YAML) Rules
- Suricata Rules
- Falco Rules
- Zeek Rules
Product Query Rules
The following rule types are platform-specific query languages:
- Splunk® Search Processing Language (SPL)
- Elasticsearch™’s Event Query Language (EQL)
- Microsoft® Kusto Query Language (KQL)
- Crowdstrike Falcon® Query Language (FQL)
CAL Doc Analysis Model Improvements
New updated models introduced throughout the CAL Doc Analysis Service improve natural-language understanding and response consistency, allowing ThreatConnect®’s AI features to more accurately interpret complex user intent and produce higher-quality, contextually relevant outputs:
- For AI Summaries, this means more coherent and concise overviews of reports and search results, preserving key technical details while improving readability.
- For NAICS Industry Classification, this means greater precision when mapping unstructured text to industry sectors, reducing misclassifications and improving coverage across diverse open-source intelligence (OSINT) sources.
- For the AI Exploited-Vulnerability Analyzer, this means enhanced comprehension that allows the model to distinguish more effectively between zero-day and exploited vulnerabilities, with improved consistency and precision in tagging and summarization.
For specific model and feature details, please ask your Customer Success representative for the ThreatConnect ML and AI Overview.
MITRE ATT&CK Version 18
ThreatConnect is now updated to MITRE ATT&CK® 18.0, which adds 12 new techniques and sub-techniques, 29 new types of software, 6 new groups, and 5 new campaigns. Version 18.0 focuses on making detection guidance more actionable, structured, and aligned with how real attacks unfold. It introduces new data models, reorganizes techniques, and expands coverage across modern infrastructure and threat activity.
MITRE ATT&CK Supported Features
MITRE ATT&CK in ThreatConnect
The following ThreatConnect features support MITRE ATT&CK:
- The CAL Automated Threat Library feed
- Document Parsing Import
- ATT&CK Visualizer
- The Search screen
- The Legacy Browse screen
- Intelligence Requirements
- The Details screen for ATT&CK Tags
- Pivoting with CAL in Threat Graph
- CAL Doc Analysis Service features
MITRE ATT&CK in Polarity
The ThreatConnect CAL Integration with Polarity enables ATT&CK technique lookups for enriched contextual analysis.
Bringing AI Threat Defense Into Focus: CAL Now Powered by MITRE ATLAS 4.9.1
Artificial intelligence is reshaping how organizations detect, analyze, and respond to threats, but it’s also creating a new battleground. As adversaries learn to evade, poison, and manipulate machine-learning (ML) systems, defenders need clearer visibility into how these attacks unfold.
With this release, CAL takes a major step forward with its incorporation of MITRE ATLAS™ version 4.9.1, giving teams a deeper understanding of adversarial behaviors targeting AI and ML systems. This enhanced knowledge foundation immediately strengthens data processing across multiple ThreatConnect and Polarity features, unlocking richer context and more resilient analytics.
Why ATLAS Matters
MITRE ATLAS (the Adversarial Threat Landscape for Artificial-Intelligence Systems) extends the familiar ATT&CK framework into the world of AI. While ATT&CK maps how human-driven cyberattacks compromise traditional IT environments, ATLAS focuses on how adversaries exploit AI models themselves.
This first ATLAS-powered CAL release sets the foundation for the following improvements:
- Better enriched data across ThreatConnect and Polarity workflows
- More precise context around threats interacting with AI systems
- Future automation and analytics that treat AI-focused threats as first-class intelligence
MITRE ATLAS Supported Features
MITRE ATLAS in ThreatConnect
The following ThreatConnect features support MITRE ATLAS:
- The CAL Automated Threat Library feed: Applies Tags and creates objects when tactics, techniques, or mitigations are found in reports.
- Document Parsing Import: Detects and associates tactics, techniques, and mitigations from text.
- CAL Doc Analysis Service: Extracts identified tactics, techniques, and mitigations from text.
TQL Generator Improvements
Being able to write ThreatConnect Query Language (TQL) shouldn’t be a barrier to gathering insights from ThreatConnect data. As analysts race to keep pace with fast-moving threats, they need tools that remove friction in their workflows. That’s why the TQL Generator continues to evolve as one of ThreatConnect’s most impactful AI-assisted features.
With this release, the TQL Generator becomes more accurate, context aware, and aligned with the latest updates to TQL syntax and the supporting AI model, including enhanced coverage of common investigative patterns, such as Attributes, Tags, and Group associations. It doesn’t just help you write queries; it also helps you think more clearly about your data, move faster, and find the right answers without wrestling with syntax.
Enhanced TQL Awareness and Validation
The TQL Generator now leverages the latest TQL documentation to better align generated queries with the platform’s supported syntax and data model. This improvement ensures that you always receive valid, up-to-date TQL output, minimizing errors such as unsupported fields or object mismatches when running queries on the Search and Legacy Browse screens.
Expanded Support for File Hash and Triplet Syntax
The TQL Generator now correctly interprets and constructs TQL queries for File Indicators, including MD5, SHA1, and SHA256 hashes. When you enter single or multiple hashes—or a complete triplet (MD5: SHA1: SHA256)—the TQL Generator automatically determines the correct hash type and applies the appropriate TQL field syntax. This update also enhances mixed-hash support, enabling the simultaneous querying of combinations of hash types.
Smarter Tag Handling
The TQL Generator now produces precise and consistent syntax for Tag-related prompts. In particular, it supports enhanced logic for Tag fields, such as those using the techniqueID parameter for ATT&CK Tags. This improvement allows you to easily find or associate objects by Tag content, names, or ATT&CK context.
Attribute Logic Improvements
The TQL Generator has improved recognition and validation for Attribute-based logic, including the following:
- Support for numerical and string comparisons (e.g.,
<,>,=). - Clear handling of
NULLvalues and unsupported operators. - Recognition of Attribute-based counts (e.g.,
more than 3 attributes,no attributes). - Improved logic for negation (e.g.,
does not have a specific attribute).
These improvements help ensure that Attributes like CVSS Score, VirusTotal Score, and dateAdded fields are applied with valid syntax and consistent results.
CAL Polarity Integration Updates
Community Reporting for False Positives in Polarity
False-positive reporting is an essential component for Indicator scoring, Indicator status, and for the analyst’s context, helping you determine whether there is a clear understanding of the information presented for an Indicator or if it requires additional review. The False Positives subsection in Polarity displays false-positive data submitted to CAL from customers, and now Polarity users can also provide feedback via the new Report False Positive button, creating a better community knowledge that can help defenders move faster on the best information.
CAL ATL–Empowered Search
Speed up your research by seeing exactly what articles have been discussing an Indicator online. The ThreatConnect CAL Integration with Polarity now provides direct references to any CAL ATL Report that mentions the Indicator so you can quickly review the most relevant reports and news.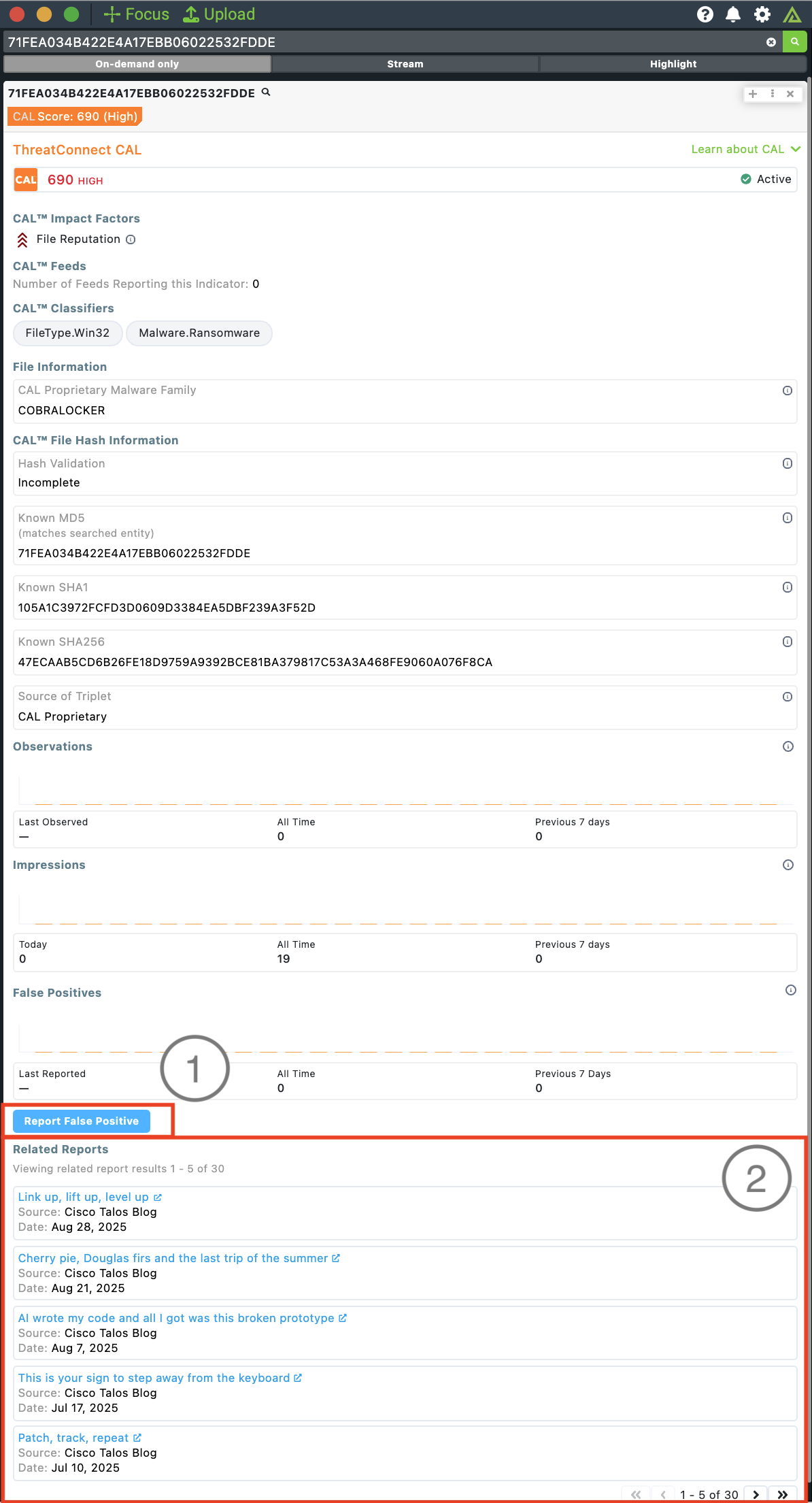
Report false positives (1) and view CAL ATL Reports related to Indicators (2) in Polarity
New On-Demand References for MITRE ATT&CK and CVEs
MITRE ATT&CK
Now you can easily reference techniques and adversaries in Polarity within your normal workflows, allowing you to quickly identify their aliases and descriptions.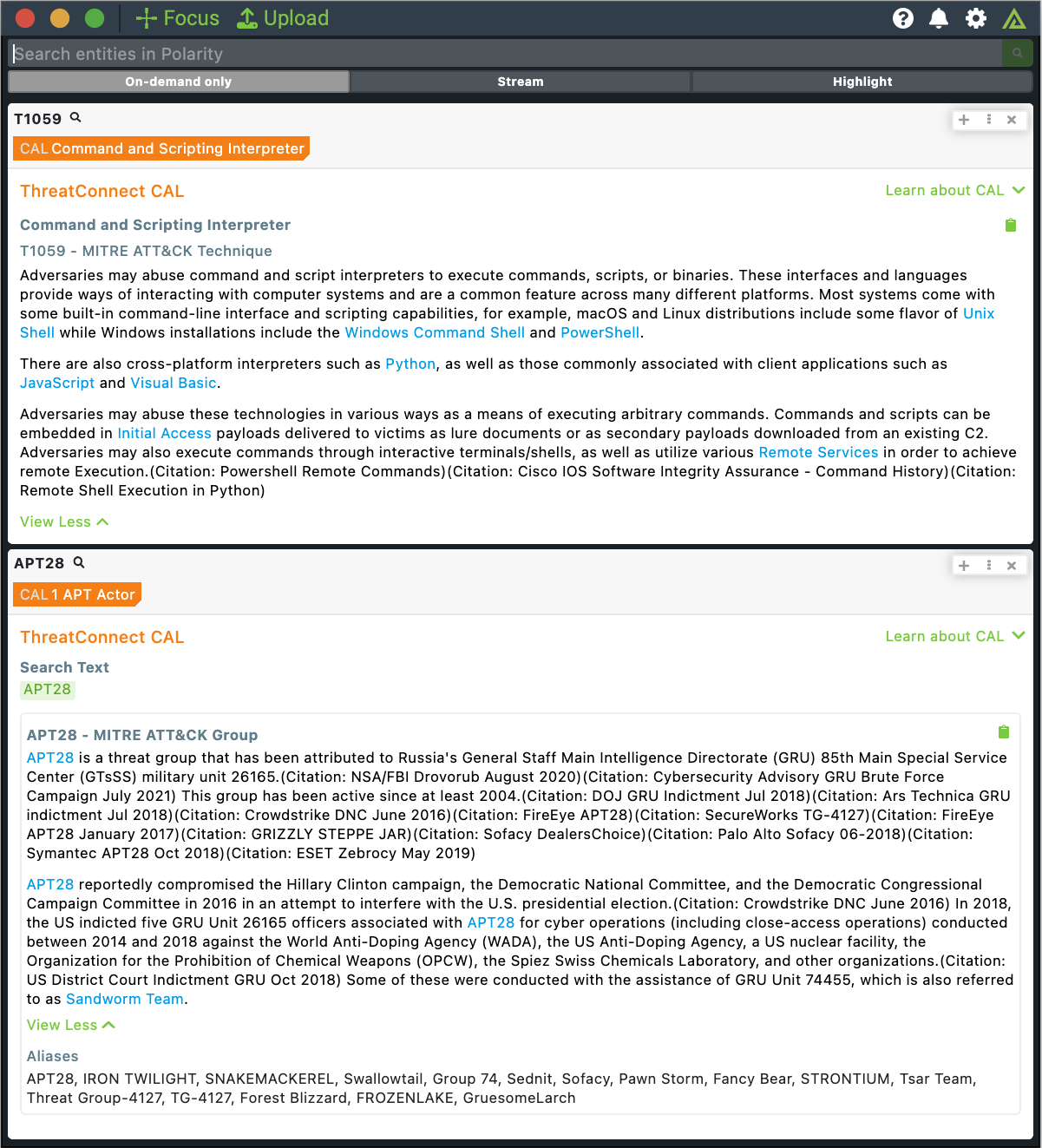
CAL-powered MITRE ATT&CK technique and adversary lookups in Polarity
CVEs
Powered by Vulncheck, the ThreatConnect CAL Integration with Polarity now supports analysts looking for key information related to Common Vulnerabilities and Exposures (CVE®s). Providing both National Vulnerability Database (NVD) and Known Exploited Vulnerabilities (KEV) data, this new feature puts the information you need directly at your fingertips.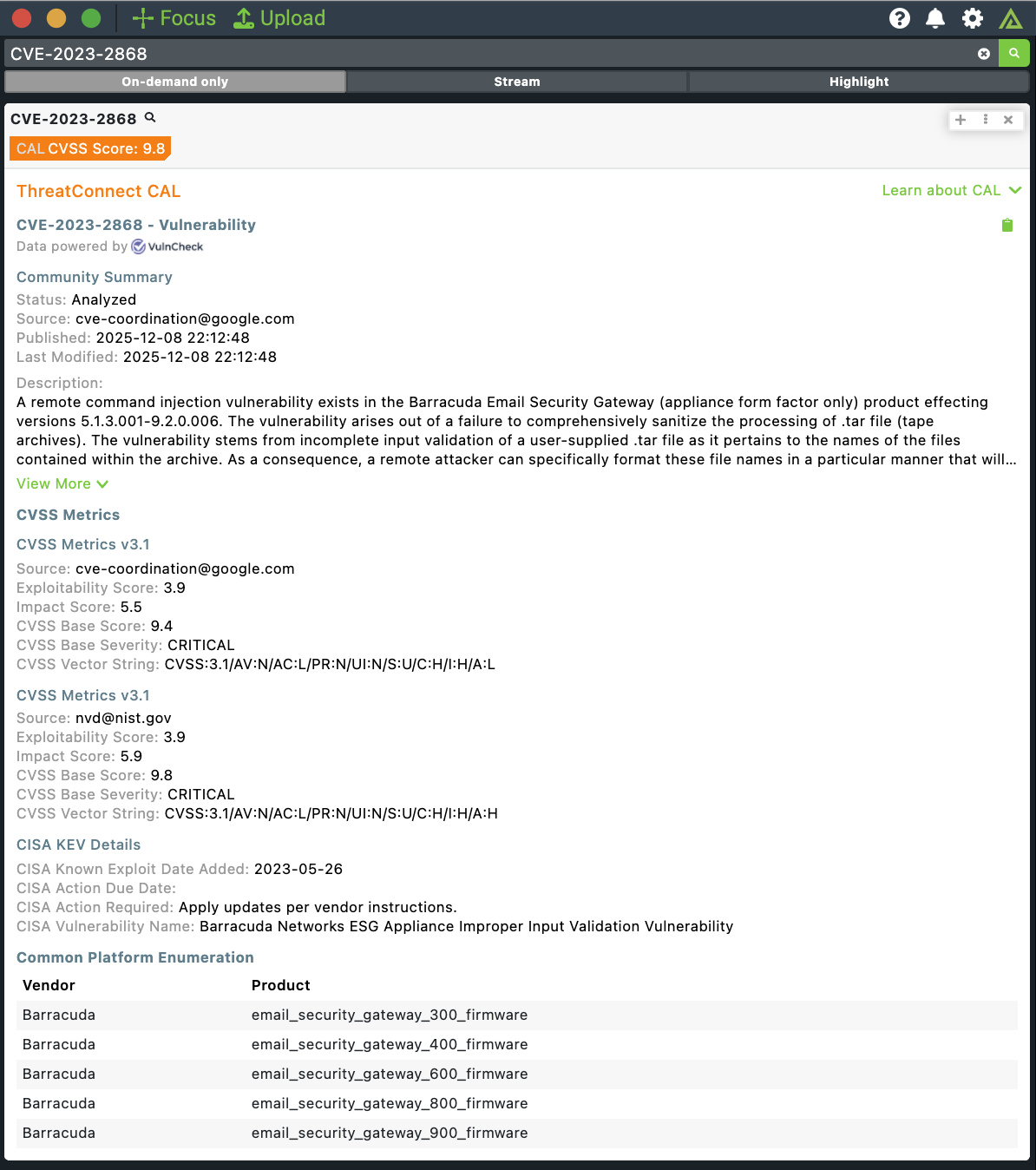
CAL-powered CVE lookups in Polarity
CAL NSRL Enrichment
With the 3.14 update, CAL has integrated almost 20 million new “Known Good” hashes from the National Software Reference Library (NSRL), an initiative backed by the U.S. Department of Homeland Security and Federal Bureau of Investigation (FBI) to assist in identifying benign software during criminal investigations. This expanded coverage spans PC, Android™, and iOS™ platforms.
For analysts, this update translates directly into greater speed, clarity, and confidence during investigations. CAL’s integration with NSRL enables near-instant enrichment of benign, traceable software artifacts, allowing teams to focus their energy on unknowns and actual threats. Whether analysts respond to incidents, review threat reports, or build detection logic, this enrichment layer helps streamline workflows, minimize alert fatigue, and ensure higher fidelity in threat assessments. Data from the CAL NSRL enrichment are now available via the Get CAL Enrichment Playbook App, the Details screen for Indicators, and the ThreatConnect CAL Integration with Polarity, bringing known-good intelligence exactly where analysts need it.
CAL Safelist Improvements
The CAL Safelist now offers improved precision and control for managing trusted domains. With this update, you can continue to trust entire domains while excluding specific subdomains that may be unnecessary or potentially risky. This added flexibility enhances accuracy and boosts confidence when handling trusted Indicators in complex environments.
Additionally, this update introduces 113 new entries to the CAL Safelist, preventing more than 6.3 million Indicators from cluttering analyst workflows. By marking non-IOCs as inactive, the CAL Safelist helps reduce alert fatigue and improve response times in both automated workflows and analyst-driven queries.
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
iOS™ is a trademark of Cisco Systems, Inc.
CrowdStrike Falcon® is a registered trademark of CrowdStrike, Inc.
Elasticsearch™ is a trademark of Elasticsearch BV.
Android™ is a trademark of Google LLC.
Microsoft® is a registered trademark of Microsoft Corporation.
MITRE ATT&CK®, ATT&CK®, and CVE® are registered trademarks, and MITRE ATLAS™ is a trademark, of The MITRE Corporation.
Splunk® is a registered trademark of Splunk, Inc.


