- 10 Sep 2025
- 4 Minutes to read
-
Print
-
DarkLight
-
PDF
Searching Your Data (Legacy)
- Updated on 10 Sep 2025
- 4 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The ThreatConnect® search engine lets you search your entire dataset to quickly find data that are relevant to the item you are investigating. When you run a search from the Search drawer, the legacy search engine looks for Indicators, Groups, Tags, Victims, Workflow Cases, and Artifacts that match your search query. Search queries may include a single search term, multiple search terms, an exact phrase, or the contents of an uploaded file.
You cannot access the Search drawer from the new top navigation bar introduced in ThreatConnect 7.10. If you want to access this feature without switching between the new and legacy navigation, add a shortcut to it in your My Pages by doing the following:
1. From the Settings![]() menu on the top navigation bar, select Switch to Legacy Navigation.
menu on the top navigation bar, select Switch to Legacy Navigation.
2. Click Search![]() on the legacy top navigation bar.
on the legacy top navigation bar.
3. Click Open Legacy Search.
4. From the Settings![]() menu on the legacy top navigation bar, select Switch to New Navigation.
menu on the legacy top navigation bar, select Switch to New Navigation.
5. From the My Pages menu on the top navigation bar, select Add to My Pages.
6. On the Add My Page window, enter a name to identify the shortcut (e.g., Legacy Search Drawer), and then click Save Changes.
Before You Start
User Roles
- To search for Indicators, Groups, Tags, and Victims in an Organization, your user account can have any Organization role.
- To search for Indicators, Groups, Tags, and Victims in a Community or Source, your user account can have any Community role except Banned for that Community or Source.
- To search for Cases and Artifacts in an Organization, your user account can have any Organization role except App Developer.
Prerequisites
- To search for potential matches in ThreatConnect when using the Search drawer, turn on and configure OpenSearch® and initialize the search index for your ThreatConnect instance via the System Settings screen (must be a System Administrator to perform this action).
- To search for Cases and Artifacts, select the Enable Workflow checkbox on the Permissions tab of the Organization Information window when editing your Organization on the Organizations tab of the Account Settings screen (must be an Accounts Administrator, Operations Administrator, or System Administrator to perform this action).
Running a Search
Follow these steps to search your ThreatConnect data from the Search drawer:
- From the Search & Create dropdown on the top navigation bar, select All Object Types.
- Click Open Legacy Search at the upper-right corner of the Search: All Object Types screen to open the Search drawer (Figure 1).
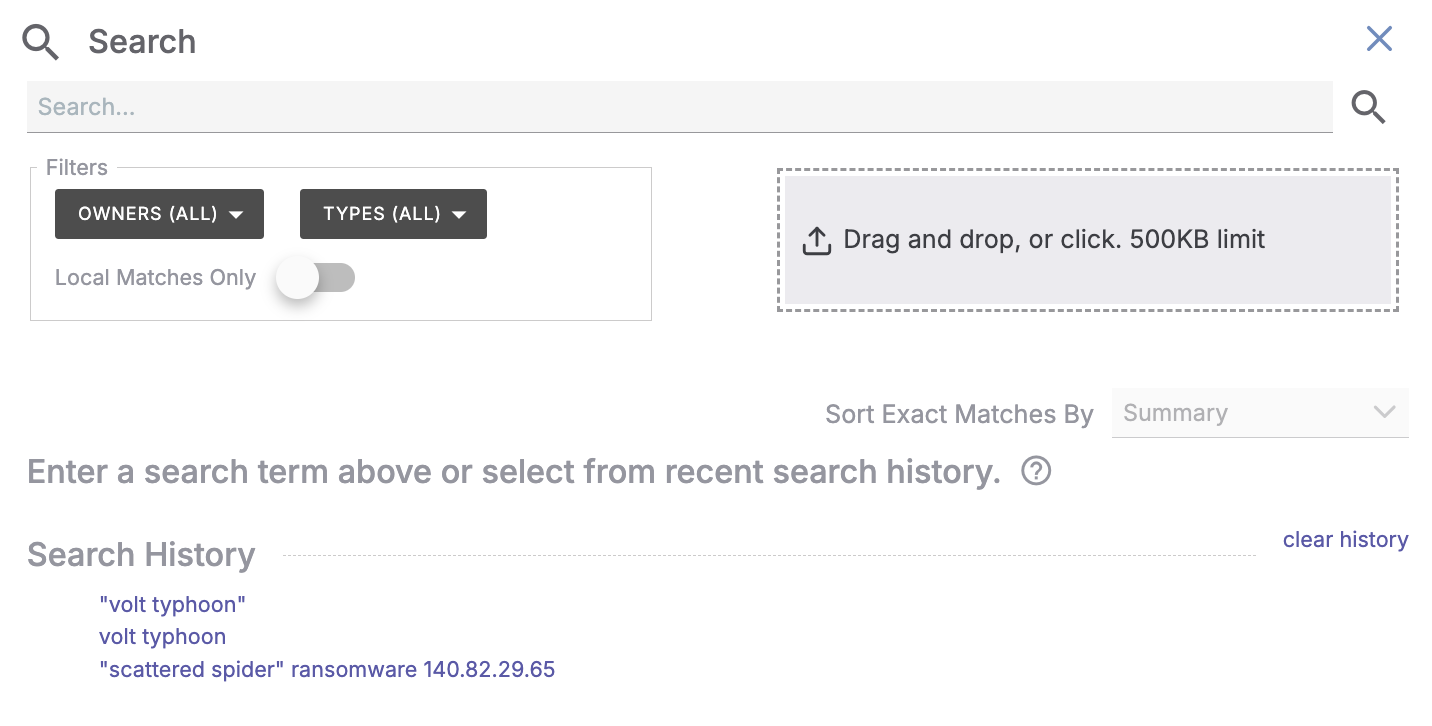
- Run a search using any of the following methods:
- Enter a search query into the search bar, and then press Enter on your keyboard or click Search
 to the right of the search bar. Search queries can include one or more terms, such as a keyword (e.g., spearphishing); the name of an Indicator, Group, Tag, Victim, Case, or Artifact; or the ID number of a Case. You can also search for an exact phrase by surrounding the phrase in straight quotes.ImportantThe search engine does not recognize smart quotes (
to the right of the search bar. Search queries can include one or more terms, such as a keyword (e.g., spearphishing); the name of an Indicator, Group, Tag, Victim, Case, or Artifact; or the ID number of a Case. You can also search for an exact phrase by surrounding the phrase in straight quotes.ImportantThe search engine does not recognize smart quotes (“”). If you copied a search phrase from an application and pasted it into the search bar, replace all smart quotes with straight quotes (") before running your search. - Drag and drop a file into the Drag and drop, or click. box, or click the box to browse for and select a file. After you upload a file, its contents will populate into the search bar, and a search based on the file contents will run automatically.NoteThe Drag and drop, or click. box displays the maximum file size that you can upload to ThreatConnect, as configured by your System Administrator.
- Select a previously used search query from the Search History section. After you select a query, a search that uses the query will run automatically.NoteTo clear your search history, click clear history at the top right of the Search History section.
- Enter a search query into the search bar, and then press Enter on your keyboard or click Search
After a search runs, the Search drawer will display the search results. When looking for matches to a search query, the legacy search engine employs the following search methodologies:
- “Exact”-matching algorithms that search for Indicators, Groups, Tags, Victims, Cases, and Artifacts based on a “direct hit” to a known item summary or, for Indicators only, a pattern for a ThreatConnect Indicator type.
- “Potential”-matching algorithms that search for intelligence data by leveraging the OpenSearch engine. When looking for potential matches, the search engine searches all data, including object summaries and descriptions, Attributes and Case Attributes, Notes, Tasks, and the contents of document uploads, to form a relevance-ordered result set based on a scoring system that filters out common words and phrases while prioritizing applicable matches.
Searching for Defanged Indicators
The ThreatConnect search engine refangs defanged Indicators automatically. The term “defang” refers to the process of altering an Indicator so that a user cannot click on it by accident and navigate to a malicious website. The term “refang” refers to the process of taking a defanged Indicator (e.g., bad[.]com) and returning it to its original state (bad.com). For example, if you run a search for bad[.]com, the search engine will return results for bad.com.
Table 1 lists all of the defanged character sequences recognized by the legacy search engine and their corresponding refanged character.
| Defanged Character Sequence | Refanged Character |
|---|---|
| [.] | . |
| [:] | : |
| [@] | @ |
| [dot] | . |
| h..p:// | http:// |
| h..ps:// | https:// |
| f.p:// | ftp:// |
. can be any character (e.g., x or X). For example, the ThreatConnect search engine will refang hxxp:// as http://.ThreatConnect® is a registered trademark of ThreatConnect, Inc.
OpenSearch® is a registered trademark of Amazon Web Services.
20075-02 v.08.B


