- 23 Jun 2023
- 11 Minutes to read
-
Print
-
DarkLight
-
PDF
Microsoft Sentinel Content Pack Use Cases
- Updated on 23 Jun 2023
- 11 Minutes to read
-
Print
-
DarkLight
-
PDF
The Microsoft Sentinel™ Content Pack supports the following use cases:
- Using the ThreatConnect® TAXII™ 2.1 server to bulk import Indicators from ThreatConnect into Microsoft Sentinel
- Using Microsoft® Kusto Query Language (KQL) queries to import incidents and alerts from Microsoft Sentinel into ThreatConnect
- Retrieving incidents from Microsoft Sentinel and creating Incident Groups in ThreatConnect
- Retrieving incidents from Microsoft Sentinel and creating Workflow Cases in ThreatConnect
Using the ThreatConnect TAXII 2.1 Server to Bulk Import Indicators From ThreatConnect Into Microsoft Sentinel
Due to Microsoft API limits, which can cause large data transfers to take multiple days, it is recommended to use the ThreatConnect TAXII 2.1 server to bulk import Indicators from ThreatConnect into Microsoft Sentinel. The following sections describe the configuration that must be completed in ThreatConnect and Microsoft Sentinel in order to leverage the ThreatConnect TAXII 2.1 server for this use case.
ThreatConnect Configuration
Setting Up the ThreatConnect TAXII 2.1 Server
For Microsoft Sentinel to be able to retrieve Indicators from ThreatConnect, you must install, configure, and activate the TAXII 2.1 Server Service and then create a TAXII user account and configure it to use the TAXII 2.1 server in ThreatConnect.
Identifying a ThreatConnect Owner’s Collection ID
To configure Microsoft Sentinel to retrieve data from an owner (i.e., an Organization, Community, or Source) in ThreatConnect, you must first obtain the owner’s collection ID. You can use the ThreatConnect TAXII REST API or the Microsoft Sentinel - Get TAXII collection IDs R2 Playbook included in the Microsoft Sentinel Content Pack to retrieve a list of collection IDs for your ThreatConnect owners.
ThreatConnect TAXII REST API
To use the ThreatConnect TAXII REST API to retrieve a list of collection IDs, you must have the following information:
- The username and password of the TAXII user account configured to use the TAXII 2.1 serverImportantRequests to the ThreatConnect TAXII REST API use basic authentication. When sending an API request, you must include an Authorization header that contains the word Basic, followed by a space and a Base64-encoded username:password string, where the values for username and password are the username and password, respectively, of the TAXII user account.
- The URL of your ThreatConnect instance (e.g., https://companyabc.threatconnect.com)
- The API path for TAXII 2.1 Server Service created in ThreatConnect, which is typically /services/taxii2/v1
After you obtain this information, send a request in the following format to the /tc_taxii/collections endpoint:
curl --location 'https://companyabc.threatconnect.com/api/services/taxii2/v1/tc_taxii/collections' \
--header 'Accept: application/taxii+json;version=2.1' \
--header 'Authorization: Basic ZGVtbzpwQDU1dzByZA=='{
"collections": [
{
"id": "3f7deaee-4f49-5d5a-a7a7-94ec26d8286f",
"media_types": [
"application/taxii+json; version=2.1"
],
"title": "Demo Organization",
"alias": "Demo Organization",
"description": "ThreatConnect Organization: Demo Organization",
"type": "Organization",
"can_write": false,
"can_read": true
},
{
"id": "bf685577-c287-527a-924c-4ae45e962a78",
"media_types": [
"application/taxii+json; version=2.1"
],
"title": "Demo Source",
"alias": "Demo Source",
"description": "ThreatConnect Source: Demo Source",
"type": "Source",
"can_write": false,
"can_read": true
}
]
}The id field included in the response is the collection ID for the ThreatConnect owner. For example, the collection ID for Demo Source is bf685577-c287-527a-924c-4ae45e962a78.
Collection ID Playbook
The Microsoft Sentinel - Get TAXII collection IDs R2 Playbook (Figure 1) retrieves a list of collection IDs for your ThreatConnect owners.
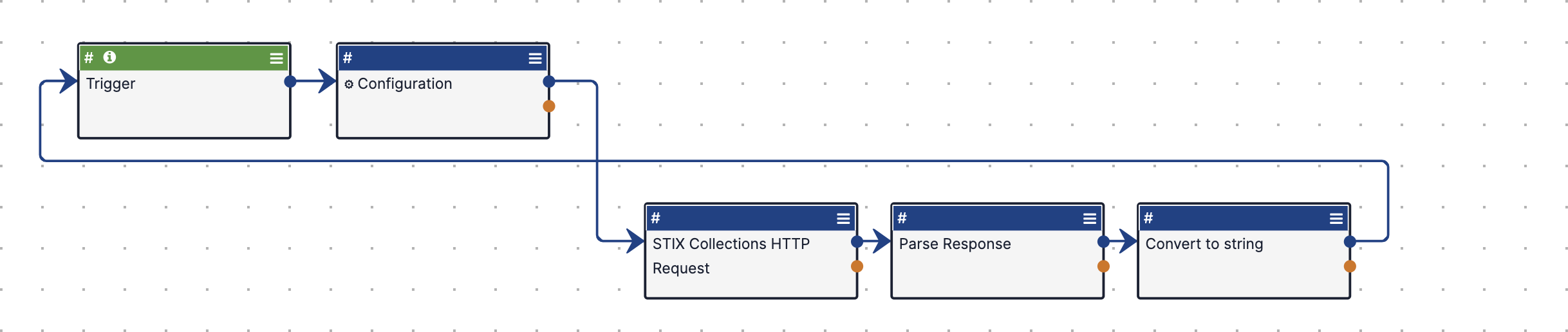
To use this Playbook, import the Microsoft Sentinel - Get TAXII collection IDs R2 Playbook Template into your Organization as a Playbook, open it in the Playbook Designer, edit the Configuration App, and update the values of the following variables used in the App:
- api_path: The API path of the TAXII 2.1 Server Service setup on your ThreatConnect instance. This value is typically /services/taxii2/v1.
- base_url: The URL of your ThreatConnect instance (e.g., https://companyabc.threatconnect.com)
- username: The username of the TAXII user account configured to use the TAXII 2.1 server.
- password: The password of the TAXII user account configured to use the TAXII 2.1 server.NoteAfter editing a variable’s value, click
 to save the new value.
to save the new value.
After updating the values of these variables, activate the Playbook and then click Execute Endpoint![]() at the upper-right corner of the design pane on the Playbook Designer to execute it. A new tab will open in your browser, and a list of collection IDs for your ThreatConnect owners will be displayed in this tab after a few moments.
at the upper-right corner of the design pane on the Playbook Designer to execute it. A new tab will open in your browser, and a list of collection IDs for your ThreatConnect owners will be displayed in this tab after a few moments.
Microsoft Sentinel Configuration
In Microsoft Sentinel, install and configure the Threat Intelligence - TAXII data connector to stream data from the desired collection on the ThreatConnect TAXII 2.1 server (Figure 2).
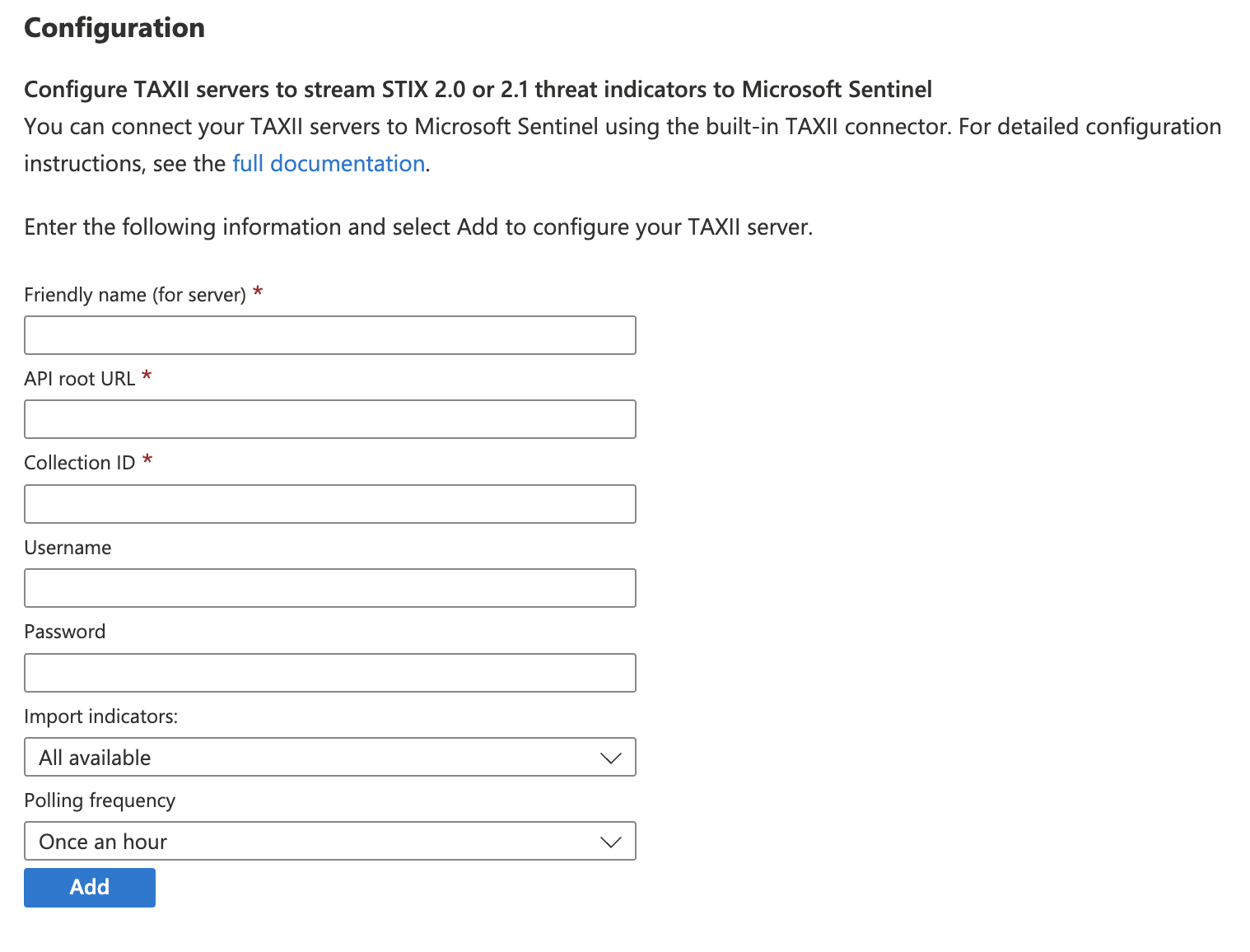
- Friendly name (for server): The name of the source in Microsoft Sentinel (e.g., ThreatConnect_TAXII). Note that this name must not contain any spaces.
- API root URL: The full path to the ThreatConnect TAXII REST API /tc_taxii endpoint (e.g., https://companyabc.threatconnect.com/api/services/taxii2/v1/tc_taxii).
- Collection ID: The collection ID of the ThreatConnect owner whose Indicators will be imported into Microsoft Sentinel.
- Username: The username of the TAXII user account configured to use the TAXII 2.1 server.
- Password: The password of the TAXII user account configured to use the TAXII 2.1 server.
- Import indicators: Select the batch of Indicators to be imported.
- Polling frequency: Select how often Microsoft Sentinel should poll the ThreatConnect TAXII 2.1 server.
- Click the Add button to complete the configuration.
After you configure the Threat Intelligence - TAXII data connector, the ThreatConnect TAXII 2.1 server, along with the collection ID of the selected owner, will be displayed in the List of configured TAXII servers in Microsoft Sentinel (Figure 3).
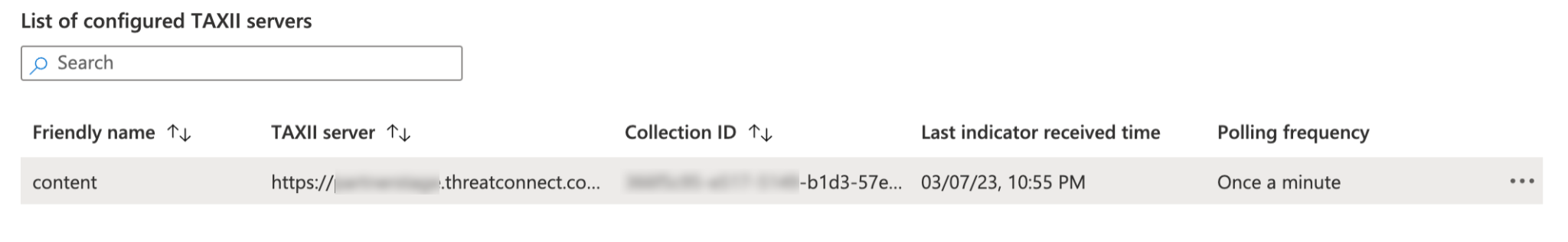
If you are importing data from multiple collections on the ThreatConnect TAXII 2.1 server, repeat this configuration process for each one.
Using KQL Queries to Import Incidents and Alerts From Microsoft Sentinel Into ThreatConnect
In Microsoft Sentinel, you can use KQL to search for and scan log data. This use case features two Playbooks that leverage KQL queries to retrieve incidents and alerts in Microsoft Sentinel and then import them into ThreatConnect as Group objects.
Send KQL Query to Pull Incidents or Alerts Playbook
The Microsoft Sentinel - Send KQL Query to pull Incidents or Alerts R2 Playbook (Figure 4) sends user-configured KQL queries to Microsoft Sentinel to retrieve incidents or alerts and then creates corresponding Incident and Event Groups in ThreatConnect. For alerts, the Playbook also parses indicators associated to an alert in Microsoft Sentinel, creates corresponding Indicators in ThreatConnect, and associates them to the Event Group created for the alert. Lastly, the Playbook saves the KQL queries it used as Signature Groups in ThreatConnect and associates them to the Incident and Event Groups it created.
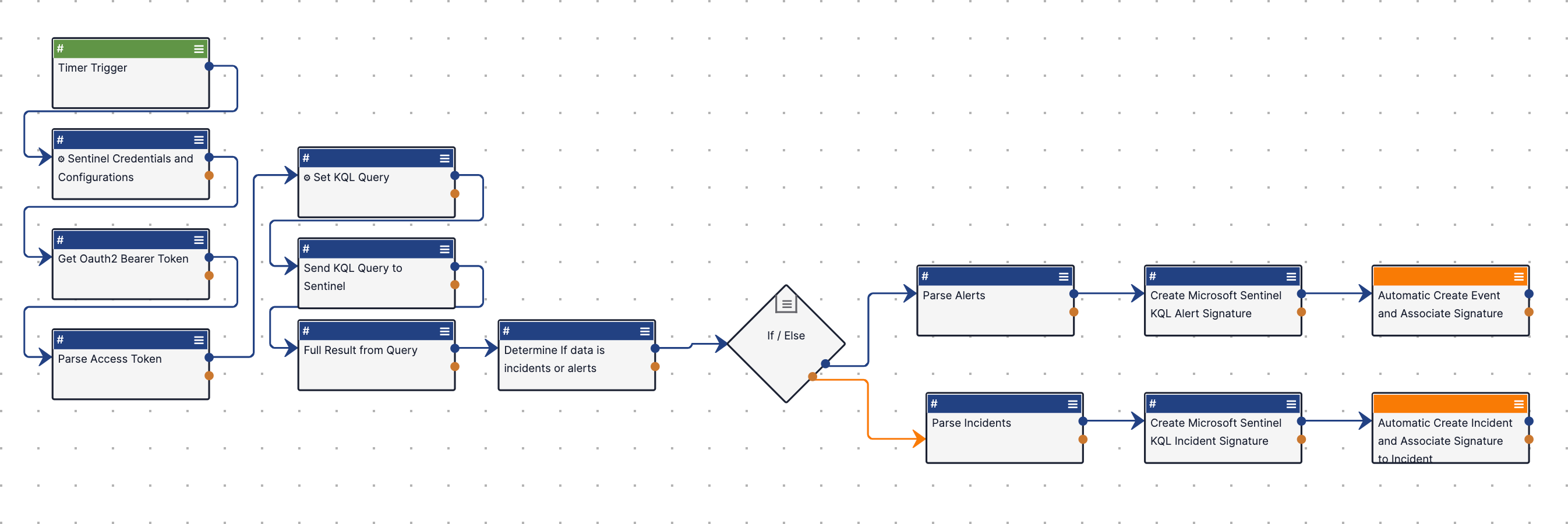
Playbook Configuration
To use this Playbook, import the Microsoft Sentinel - Send KQL Query to pull Incidents or Alerts R2 Playbook Template into your Organization as a Playbook, open it in the Playbook Designer, and make the following changes:
- Edit the Timer Trigger and specify the frequency at which the Playbook will run.
- Edit the Sentinel Credentials and Configurations App and update each variable’s value to the respective credential value outlined in the “Setting Up Credentials for Playbooks” section of Installing and Configuring the Microsoft Sentinel Content Pack.
- Edit the Set KQL Query App and update the value of the kql_json_query_to_run variable to the desired KQL query in JSON format. The following JSON examples contain KQL queries that use the SecurityAlert and SecurityIncident log tables, where the italicized portion is the KQL query:
- {"query":"SecurityAlert| where TimeGenerated >= ago(30d)| limit 20"}
- {"query":"SecurityIncident | where TimeGenerated >= ago(30d)| limit 20"}
- {"query":"SecurityAlert | where Entities contains \"97.81\""}NoteIf extra quotation marks (")are needed, you must escape them with a slash (\).
- Edit the Create Microsoft Sentinel KQL Alert Signature and Create Microsoft Sentinel KQL Incident Signature Apps and update the value of the Owner parameter for each App to the ThreatConnect owner in which you want the Playbook to create data.
Playbook Component Configuration
The Microsoft Sentinel - Send KQL Query to pull Incidents or Alerts R2 Playbook uses the following Playbook Components, each of which is created in your Organization automatically when you import the corresponding Playbook Template into your Organization:
- Automatic Create Event and Associate Signature to Event
- Automatic Create Incident and Associate Signature to Incident
- Parse Sentinel Entities from Alerts
After the import process is complete, edit each Component and make the changes described in the following subsections.
Automatic Create Event and Associate Signature to Event
Edit the ThreatConnect Create Groups App and update the value of the Owner parameter to the ThreatConnect owner in which you want the Playbook to create data.
Automatic Create Incident and Associate Signature to Incident
Edit the Create Incident with converted status and Create Incident Group with Regular Status Apps and update the value of the Owner parameter for each App to the ThreatConnect owner in which you want the Playbook to create data.
Parse Sentinel Entities from Alerts
Edit the following Apps and update the value of the Owner parameter for each App to the ThreatConnect owner in which you want the Playbook to create data:
- Create Address Indicator
- Create Email Address
- Create Host Indicator
- Create Malware Entry
- Create MD5 File Indicator
- Create MD5 File Indicator from File
- Create Registry Key
- Create Registry Value as Registry Key
- Create SHA1 File Indicator
- Create SHA1 File Indicator from File
- Create SHA256 File Indicator
- Create SHA256 File Indicator from File
- Create URL Indicator
Parse KQL Query From Signature Group and Pull Incidents or Alerts Playbook
The Microsoft Sentinel - Parse KQL Query From Signature Group and pull Incidents or Alerts R2 Playbook (Figure 5) parses a ThreatConnect Signature Group containing a KQL query, sends the query to Microsoft Sentinel to retrieve incidents or alerts, and creates corresponding Incident and Event Groups in ThreatConnect. For alerts, the Playbook also parses indicators associated to an alert in Microsoft Sentinel, creates corresponding Indicators in ThreatConnect, and associates them to the Event Group created for the alert. Lastly, the Playbook saves the KQL queries it used as Signature Groups in ThreatConnect and associates them to the Incident or Event Groups it created.
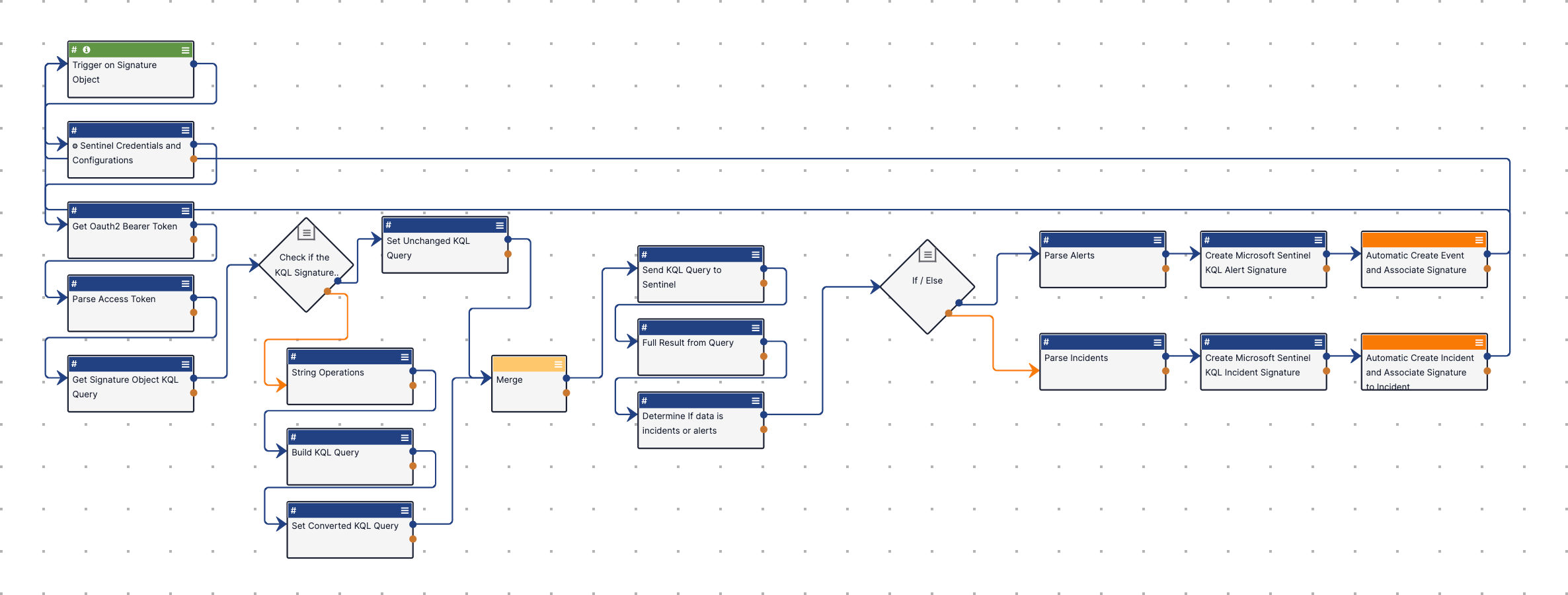
Playbook Configuration
To use this Playbook, import the Microsoft Sentinel - Parse KQL Query From Signature Group and pull Incidents or Alerts R2 Playbook Template into your Organization as a Playbook, open it in the Playbook Designer, and make the following changes:
- Edit the Sentinel Credentials and Configurations App and update each variable’s value to the respective credential value outlined in the “Setting Up Credentials for Playbooks” section of Installing and Configuring the Microsoft Sentinel Content Pack.
- Edit the Create Microsoft Sentinel KQL Alert Signature and Create Microsoft Sentinel KQL Incident Signature Apps and update the value of the Owner parameter for each App to the ThreatConnect owner in which you want the Playbook to create data.
Playbook Component Configuration
The Microsoft Sentinel - Parse KQL Query From Signature Group and pull Incidents or Alerts R2 Playbook uses the following Playbook Components, each of which is created in your Organization automatically when you import the corresponding Playbook Template into your Organization:
- Automatic Create Event and Associate Signature to Event
- Automatic Create Incident and Associate Signature to Incident
- Parse Sentinel Entities from Alerts
After the import process is complete, edit each Component and make the changes described in the “Automatic Create Event and Associate Signature to Event,” “Automatic Create Incident and Associate Signature to Incident,” and “Parse Sentinel Entities from Alerts” sections if you did not make them when updating the Microsoft Sentinel - Send KQL Query to pull Incidents or Alerts R2 Playbook.
Retrieving Incidents From Microsoft Sentinel and Creating Incident Groups in ThreatConnect
This use case leverages the Microsoft Sentinel - Pull Incidents and Create TC Incidents R2 Playbook (Figure 6) to retrieve incidents from Microsoft Sentinel and create corresponding Incident Groups in ThreatConnect.
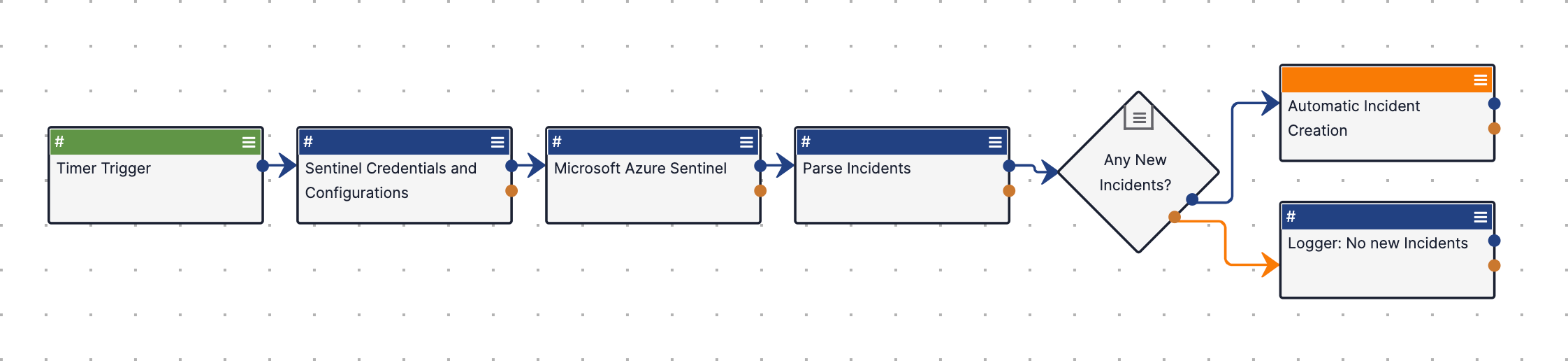
Playbook Configuration
To use this Playbook, import the Microsoft Sentinel - Pull Incidents and Create TC Incidents R2 Playbook Template into your Organization as a Playbook, open it in the Playbook Designer, and make the following changes:
- Edit the Timer Trigger and specify the frequency at which the Playbook will run.
- Edit the Sentinel Credentials and Configurations App and update each variable’s value to the respective credential value outlined in the “Setting Up Credentials for Playbooks” section of Installing and Configuring the Microsoft Sentinel Content Pack.ImportantWhen updating the value of the sentinel_api_version variable, use the latest stable Microsoft Sentinel REST API version (e.g., 2023-02-01).
- Edit the Microsoft Azure Sentinel App and update the value of the Client Secret parameter to the client secret created when you registered an app in the Azure® portal.
Playbook Component Configuration
The Microsoft Sentinel - Pull Incidents and Create TC Incidents R2 Playbook uses the Automatic Incident Creation Playbook Component, which is created in your Organization automatically when you import the corresponding Playbook Template into your Organization. After the import process is complete, edit the Component, edit the Create Incident With Converted Status and Create Incident with regular status Apps, and update the value of the Owner parameter for each App to the ThreatConnect owner in which you want the Playbook to create data.
Retrieving Incidents From Microsoft Sentinel and Creating Workflow Cases in ThreatConnect
This use case leverages the Microsoft Sentinel - Pull Sentinel Incidents and create Desired Cases R2 Playbook (Figure 7) to retrieve incidents from Microsoft Sentinel and create Workflow Cases in ThreatConnect that analysts can use to further investigate the incidents.
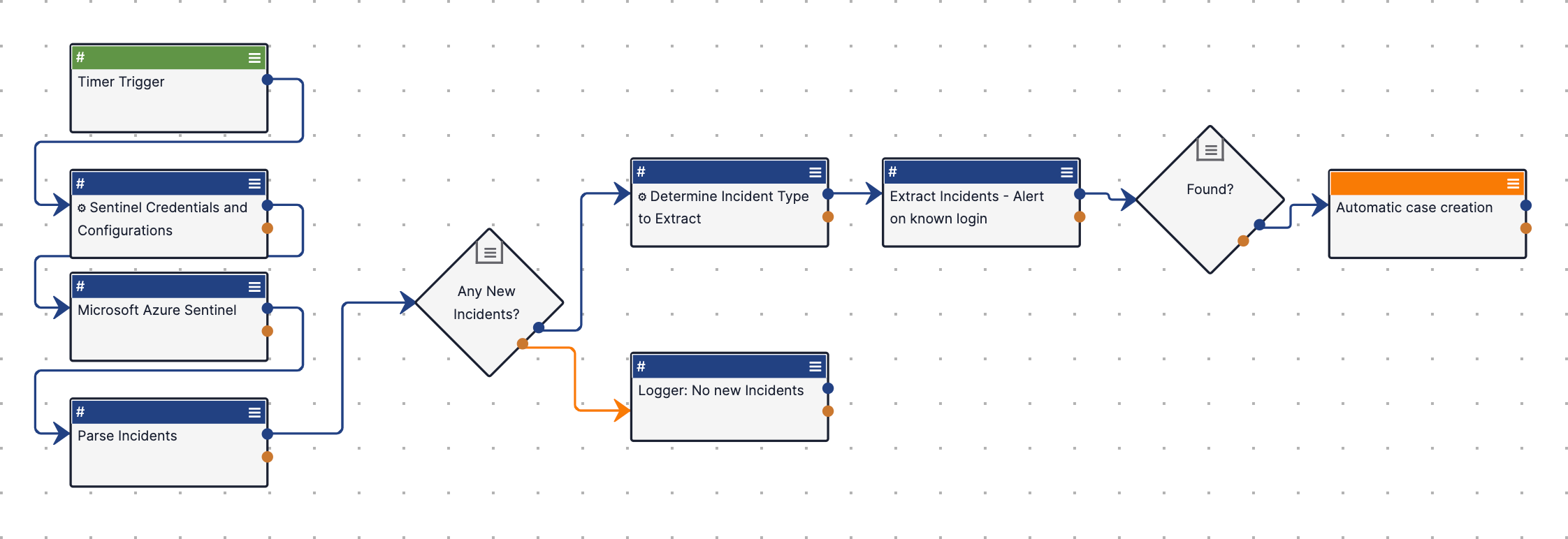
Playbook Configuration
- Edit the Timer Trigger and specify the frequency at which the Playbook will run.
- Edit the Sentinel Credentials and Configurations App and update each variable’s value to the respective credential value outlined in the “Setting Up Credentials for Playbooks” section of Installing and Configuring the Microsoft Sentinel Content Pack.ImportantWhen updating the value of the sentinel_api_version variable, use the latest stable Microsoft Sentinel REST API version (e.g., 2023-02-01).
- Edit the Microsoft Azure Sentinel App and update the value of the Client Secret parameter to the client secret created when you registered an app in the Azure portal.
- Edit the Determine Incident Type to Extract App and update the value of the incident.type variable to the name(s) of the incident(s) to retrieve from Sentinel. If one or more of the incidents are found in Microsoft Sentinel, the Playbook will create a Case for each one.
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
Azure® and Microsoft® are registered trademarks, and Microsoft Sentinel™ is a trademark, of Microsoft Corporation.
TAXII™ is a trademark of The MITRE Corporation.
20153-03 v.01.A


