- 28 Oct 2025
- 24 Minutes to read
-
Print
-
DarkLight
-
PDF
Wiz Cloud Security Intelligence Engine Integration User Guide
- Updated on 28 Oct 2025
- 24 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The Wiz Cloud Security Intelligence Engine Feed API Service App in ThreatConnect® leverages Wiz’s vulnerability scanning capabilities to help you identify, prioritize, and act on vulnerability findings in ThreatConnect.
The volume of the vulnerability findings in a dataset can be daunting. The Wiz Cloud Security Intelligence Engine App provides a simple, action-focused solution to this challenge. First, it ingests the Wiz Cloud Security set of Common Vulnerabilities and Exposures (CVE®) and related asset, source, and other data into a dedicated feed in ThreatConnect. The CVEs are created as Vulnerability Group objects and enriched with Attributes containing key metrics and other data from Wiz Cloud Security. For each ingested Vulnerability Group, the App creates, associates, and assigns a Workflow Case, ensuring that each CVE is tracked for further investigation and action in ThreatConnect. Each Case is enriched with a set of Attributes representing asset and other information, including severity count data from Wiz and links to corresponding sources in the Wiz Cloud Security UI. You can use this information to identify vulnerabilities with significant numbers of high-risk assets.
In addition to creating a feed of enriched vulnerability data from Wiz and corresponding Cases, the Wiz Cloud Security Intelligence Engine App can also cross-reference the CVE Identifiers (CVE-IDs) for the ingested Wiz Cloud Security dataset against the Tags on Groups and/or Indicators in a set of ThreatConnect owners. Each Group or Indicator with a matched Tag is then associated to the corresponding Vulnerability Group in the Source feed and to its Case and enriched with the Attributes with Wiz findings.
Dependencies
ThreatConnect Dependencies
- Active ThreatConnect Application Programming Interface (API) key
- ThreatConnect instance with 7.9.0 or newer installed
Wiz Cloud Security Dependencies
- Wiz subscription
- Wiz Service Account with read:vulnerabilities permission
- Wiz Client ID
- Wiz Client SecretImportantEach ThreatConnect Organization using the Wiz Cloud Security Intelligence Engine App on a ThreatConnect instance must have its own Wiz Client ID and Wiz Client Secret. Wiz authentication credentials cannot be shared between Organizations.
Application Setup and Configuration
The Wiz Cloud Security Intelligence Engine App must be deployed and configured for each Organization that will use it on a ThreatConnect instance. The configuration must be done by a user account in that Organization, either in the Feed Deployer by a user account with a System role of Administrator (“System Administrator”) in the Organization or, after feed deployment, on the Services screen by a user account in the Organization with an Organization role of Organization Administrator (“Organization Administrator”).
Follow these steps to install, deploy, and configure the Wiz Cloud Security Intelligence Engine App for an Organization on your ThreatConnect instance:
- Install the Wiz Cloud Security Intelligence Engine App. Skip this step if the Wiz Cloud Security Intelligence Engine App has already been installed on your ThreatConnect instance.
- Deploy the Wiz Cloud Security Intelligence Engine App.
- Configure the Wiz Cloud Security Intelligence Engine App.
Step 1: Install the Wiz Cloud Security Intelligence Engine App
Follow these steps to install the Wiz Cloud Security Intelligence Engine App via TC Exchange™:
- Log into ThreatConnect with a System Administrator account.
- From the Settings
 menu on the top navigation bar, select TC Exchange Settings.
menu on the top navigation bar, select TC Exchange Settings. - Select the Catalog tab on the TC Exchange Settings screen.
- Locate the Wiz Cloud Security Intelligence Engine App on the Catalog tab.
- Click Install
 in the Options column for the App.
in the Options column for the App. - Click INSTALL in the App’s Release Notes window.
- After you install the Wiz Cloud Security Intelligence Engine App, the Feed Deployer will open automatically. Follow the procedure in Step 2 to deploy the Wiz Cloud Security Intelligence Engine App.
Step 2: Deploy the Wiz Cloud Security Intelligence Engine App
Follow these steps to deploy the Wiz Cloud Security Intelligence Engine App to an Organization:
- Log into ThreatConnect with a System Administrator account.
- From the Settings
 menu on the top navigation bar, select TC Exchange Settings.
menu on the top navigation bar, select TC Exchange Settings. - Locate the Wiz Cloud Security Intelligence Engine App on the Installed tab. Then select Deploy from the Options ⋮ dropdown.
- Follow the instructions in Table 1 to fill out the fields in the Feed Deployer window for a deployment of the Wiz Cloud Security Intelligence Engine App’s Feed API Service.
Name Description Required? Source Tab Sources to Create Enter the name of the Source for the feed. ImportantReplace the default name (Wiz Cloud Security Threat Intelligence) with the name of a Source that is unique on your ThreatConnect instance and specific to the name of the Organization in which it is being deployed. The recommended format isWiz Cloud Security Threat Intelligence - <Organization name>(e.g.,Wiz Cloud Security Threat Intelligence - Demo Organization).Required Owner Select the Organization in which the Source will be created—that is, the Organization to which you are deploying the Wiz Cloud Security Intelligence Engine App. ImportantWorkflow must be enabled in the selected Organization so that the Wiz Cloud Security Intelligence Engine App can create Workflow Cases in it. To enable Workflow, select the Enable Workflow checkbox on the Permissions tab of the Organization Information window for the Organization on the Organizations tab of the Account Settings screen (must be a System Administrator, Operations Administrator, or Accounts Administrator to perform this action).Required Activate Deprecation Select this checkbox to allow confidence deprecation rules to be created and applied to Indicators in the Source. Optional Create Attributes Select this checkbox to allow custom Attribute Types to be created in the Source. Optional Parameters Tab Launch Server Select tc-job as the launch server for the Service corresponding to the Feed API Service App. Required Tenant Data Center Enter the regional data center for your Wiz account. NoteTo identify your Tenant Data Center, log into Wiz, click the User icon at the upper right of your Wiz portal, and then select Tenant Info. On the left, click Data Center and Regions.Required Environment Select your Wiz environment. Available choices include the following: - app.wiz.io
- app.wiz.us
- gov.wiz.io
Required Owners to Scan - If you are deploying the Wiz Cloud Security Intelligence Engine App to an Organization that is not your user account’s Organization, do not make any selections from this dropdown. Instead, an Organization Administrator for the Organization will configure this parameter from the Services screen.
- If you are deploying the Wiz Cloud Security Intelligence Engine App to your Organization, then you should select owners from this dropdown if you want it to scan Groups and Indicators for Tags matching CVE-IDs from Wiz Cloud Security and associate those objects to ingested Vulnerability Groups and the Cases created for them. If you do not select any owners, then the Wiz Cloud Security Intelligence Engine App will only ingest vulnerability findings and create Cases.
Optional Group Types to Scan - If you are deploying the Wiz Cloud Security Intelligence Engine App to an Organization that is not your user account’s Organization, do not make any selections from this dropdown. Instead, an Organization Administrator for the Organization will configure this parameter from the Services screen.
- If you are deploying the Wiz Cloud Security Intelligence Engine App to your Organization, then you should select the Group types from this dropdown that you want the Wiz Cloud Security Intelligence Engine App to scan.
Optional Indicator Types to Scan - If you are deploying the Wiz Cloud Security Intelligence Engine App to an Organization that is not your user account’s Organization, do not make any selections from this dropdown. Instead, an Organization Administrator for the Organization will configure this parameter from the Services screen.
- If you are deploying the Wiz Cloud Security Intelligence Engine App to your Organization, then you should select the Indicator types from this dropdown that you want the Wiz Cloud Security Intelligence Engine App to scan.
Optional Assignee - If you are deploying the Wiz Cloud Security Intelligence Engine App to an Organization that is not your user account’s Organization, do not make any selections from this dropdown. Instead, an Organization Administrator for the Organization will configure this parameter from the Services screen.
- If you are deploying the Wiz Cloud Security Intelligence Engine App to your Organization, then you should select an assignee from this dropdown. If you do not select an assignee, then the Cases created by Wiz Cloud Security Intelligence App in your Organization will be unassigned.
Optional Enable hasExploit filter Select this checkbox to limit Tag matching only to CVEs that have a known exploit—that is, CVEs listed in the U.S. Cybersecurity & Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) Catalog. The checkbox is selected by default. NoteIf the Enable hasExploit filter checkbox is unselected, the daily run time of the Wiz Cloud Security Intelligence Engine App will be much longer than if the checkbox is selected.Optional Variables Tab Wiz Client ID Enter the Client ID for the Wiz Cloud Security account. ImportantThe Wiz Client ID must be unique to the Organization for which the Wiz Cloud Security Intelligence Engine App is being deployed. If another Organization on your ThreatConnect instance has deployed the Wiz Cloud Security Intelligence Engine App, you may not use its Wiz Client ID for this Organization’s deployment.Required Wiz Client Secret Enter the Client Secret for the Wiz Cloud Security account. ImportantThe Wiz Client Secret must be unique to the Organization for which the Wiz Cloud Security Intelligence Engine App is being deployed. If another Organization on your ThreatConnect instance has deployed the Wiz Cloud Security Intelligence Engine App, you may not use its Wiz Client Secret for this Organization’s deployment.Required Confirm Tab Run Feeds after deployment - If you are deploying the Wiz Cloud Security Intelligence Engine App to an Organization that is not your user account’s Organization, do not select this checkbox. The feed should be run after an Organization Administrator for the Organization finishes the App’s configuration from the Services screen
- If you are deploying the Wiz Cloud Security Intelligence Engine App to your Organization and have configured all parameters in the Feed Deployer, then selecting this dropdown is recommended.
Optional Confirm Deployment Over Existing Source This checkbox will be displayed if the Source entered in the Sources to Create field has previously been deployed to the Organization selected in the Owner dropdown on the Source tab. Select this checkbox to confirm that you want the Wiz Cloud Security Intelligence Engine App to write data to the same Source. This process will create a new Service for the Wiz Cloud Security Intelligence Engine App. As such, it is recommended that you delete the old Service associated with the Wiz Cloud Security Intelligence Engine App after the new one is created. ImportantIf you do not select this checkbox, the DEPLOY button will be grayed out, and you will not be able to deploy the Service. Return to the Source tab and enter a different Source or select a different Organization and then proceed through the tabs of the Feed Deployer window again.Optional - If you configured the Wiz Cloud Security Intelligence Engine App for your Organization in the Feed Deployer, then your application setup and configuration are complete. You should not perform Step 3. If you configured the Wiz Cloud Security Intelligence Engine App for an Organization that is not your user account’s Organization in the Feed Deployer, then an Organization Administrator in that Organization must follow the procedure in Step 3 to complete configuration of the Wiz Cloud Security Intelligence Engine App’s Feed API Service.
Step 3: Configure the Wiz Cloud Security Intelligence Engine App
Follow these steps to configure the Wiz Cloud Security Intelligence Engine App for your Organization:
- Log into ThreatConnect with an Organization Administrator account in the Organization for which you are configuring the Wiz Cloud Security Intelligence Engine App.
- From the Automation & Feeds dropdown on the top navigation bar, select Services.
- Locate the Feed Service for the Wiz Cloud Security Intelligence Engine App’s deployment for your Organization, which is likely formatted as
Wiz Cloud Security Intelligence Engine - <Organization name>).NoteSee the “Frequently Asked Questions (FAQ)” section for instructions on what to do if you do not see a Feed Service for your Organization’s deployment of the Wiz Cloud Security Intelligence Engine App. - Select Edit... from the Options ⋯ dropdown.
- On Step 1 (Select) of the Edit Service drawer, click Next. Do not change any parameters.
- On Step 2 (Configure) of the Edit Service drawer, click Next.ImportantDo not change the value of the Launch Server parameter. It is not recommended to change the value of the API Path parameter. It is optional to change the values of the Enable Notifications, Email Address, and Max restart attempts on failure parameters.
- Fill out the fields on Step 3 (Parameters) of the Edit Service drawer (Figure 1) as follows:
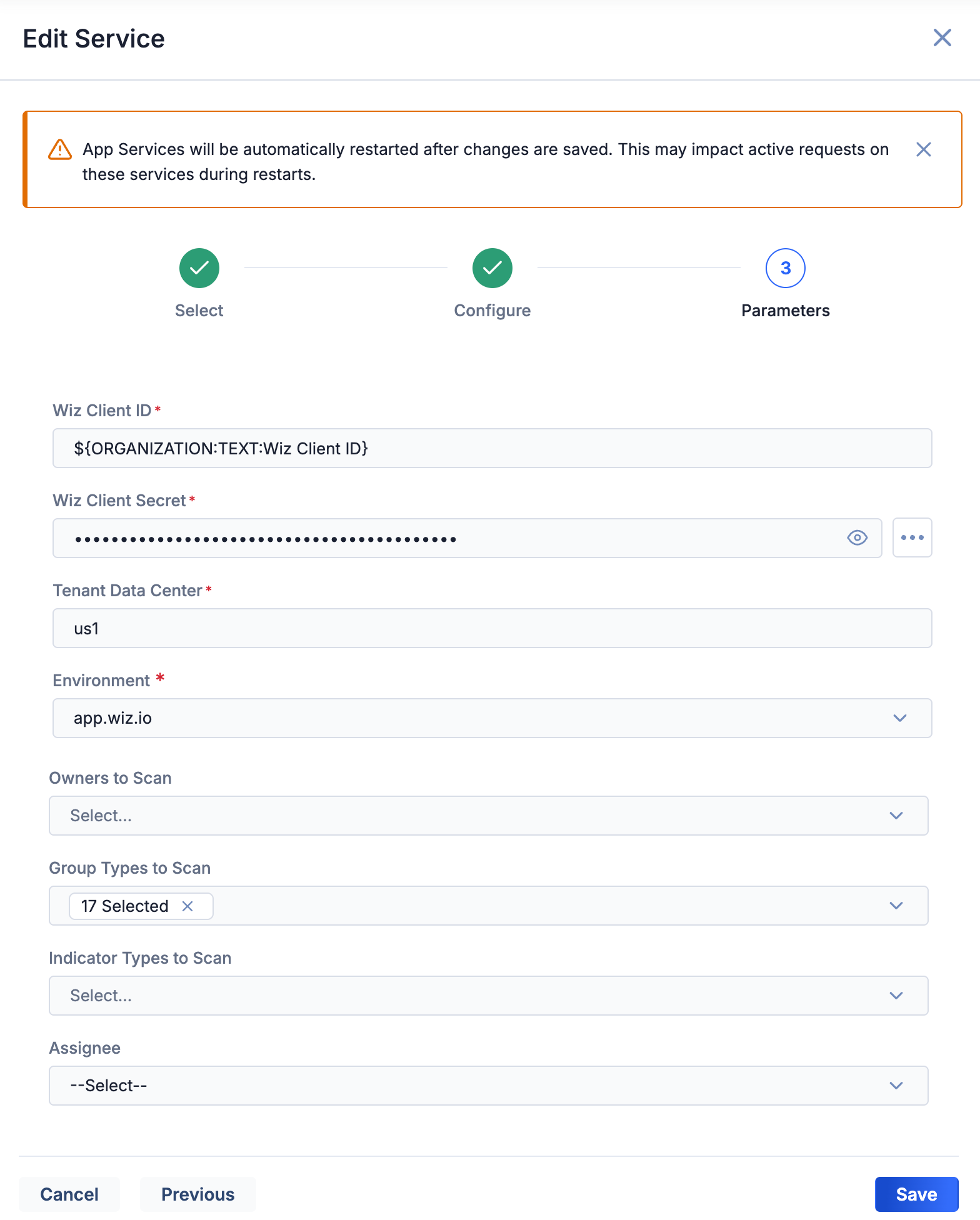
- Wiz Client ID: Do not change the value of this parameter unless it is currently incorrect.
- Wiz Client Secret: Do not change the value of this parameter unless it is currently incorrect.
- Tenant Data Center: Do not change the value of this parameter unless it is currently incorrect.
- Environment: Do not change the value of this parameter unless it is currently incorrect.
- Owners to Scan: Select the owners in which the Wiz Cloud Security Intelligence Engine App will scan for Tags that match the CVE data ingested from Wiz. The owners in this dropdown are your user account’s Organization and the Communities and Sources in which your Organization is a member.NoteYou should select owners from this dropdown if you want the Wiz Cloud Security Intelligence Engine App to scan Groups and Indicators for Tags matching CVE-IDs from Wiz Cloud Security and associate those objects to ingested Vulnerability Groups and the Cases created for them. If you do not select any owners, then the Wiz Cloud Security Intelligence Engine App will only ingest vulnerability findings and create Cases.
- Group Types to Scan: Select the Group types that the Wiz Cloud Security Intelligence Engine App will scan for Tags that match the CVE data ingested from Wiz Cloud Security. All Group types are selected by default.
- Indicator Types to Scan: Select the Indicator types that the Wiz Cloud Security Intelligence Engine App will scan for Tags that match the CVE data ingested from Wiz Cloud Security.
- Assignee: Select the ThreatConnect user to assign to Workflow Cases created to track matched CVEs from Wiz Cloud Security. Cases will be created in your Organization. The Assignee dropdown options are all user accounts in your Organization.NoteIf you do not select an assignee, then the Cases created by the Wiz Cloud Security Intelligence Engine App in your Organization will be unassigned.
- Click Save to save the configuration for the Wiz Cloud Security Intelligence Engine App for your Organization.
Wiz Cloud Security Intelligence Engine UI
After installing, deploying, and configuring the Wiz Cloud Security Intelligence Engine App, you can access the Wiz Cloud Security Intelligence Engine user interface (UI), where you can manage data ingestion from Wiz Cloud Security into ThreatConnect.
Follow these steps to access the Wiz Cloud Security Intelligence Engine UI:
- Log into ThreatConnect with a System Administrator or an Organization Administrator account.
- From the Automation & Feeds dropdown on the top navigation bar, select Services.
- Locate and turn on the Wiz Cloud Security Intelligence Engine Feed Service.ImportantIf there are multiple versions of the Wiz Cloud Service Intelligence Engine Feed Service on your ThreatConnect instance, make sure to access the Service configured for your Organization.
- Click the link in the Service’s API Path field. The Wiz Cloud Security Intelligence Engine UI will open in a new browser tab.
The following screens are available in the Wiz Cloud Security Intelligence Engine UI:
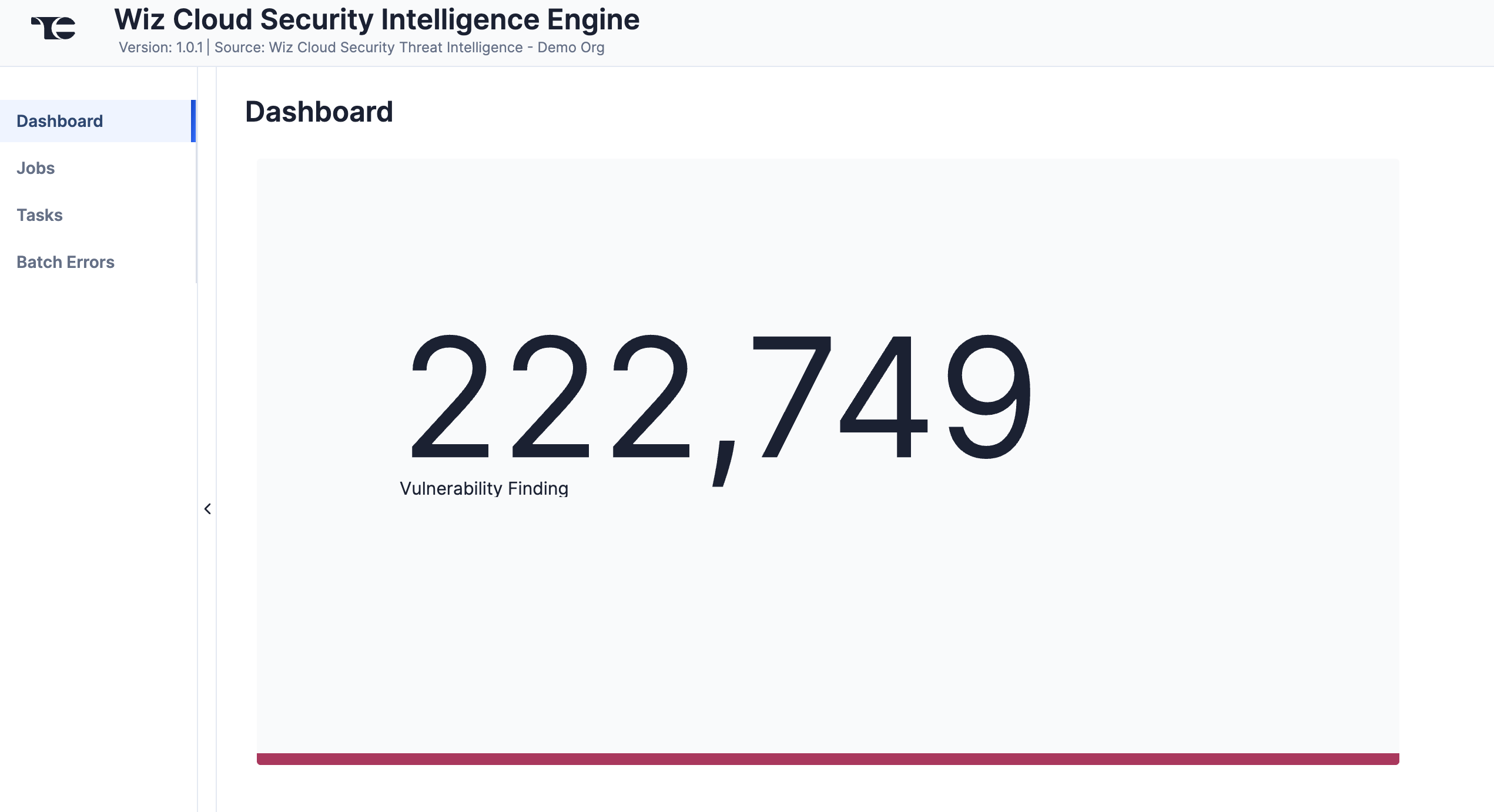
Dashboard
The Dashboard screen (Figure 2) provides an overview of the total number of Vulnerability Findings retrieved from Wiz Cloud Security, where a Vulnerability Finding is a CVE or an asset for a CVE. This number is a cumulative count of all Vulnerability Findings collected over the life of the App’s deployment in ThreatConnect.
Jobs
The Jobs screen (Figure 3) breaks down the ingestion of Wiz Cloud Security data into manageable Job-like tasks, displaying all processes that are pending, in progress, complete, and failed. The ⋯ menu in a Job’s row provides the following options:
- Details: View details for the Job, such as download, convert, and upload start and complete times and counts of downloaded and batched Groups and Indicators.
- Download Files: Download metadata files for all Jobs and data (convert, download, and upload) files for completed Jobs.
- Batch Errors: View errors that have occurred for the Job on the Batch Errors screen.
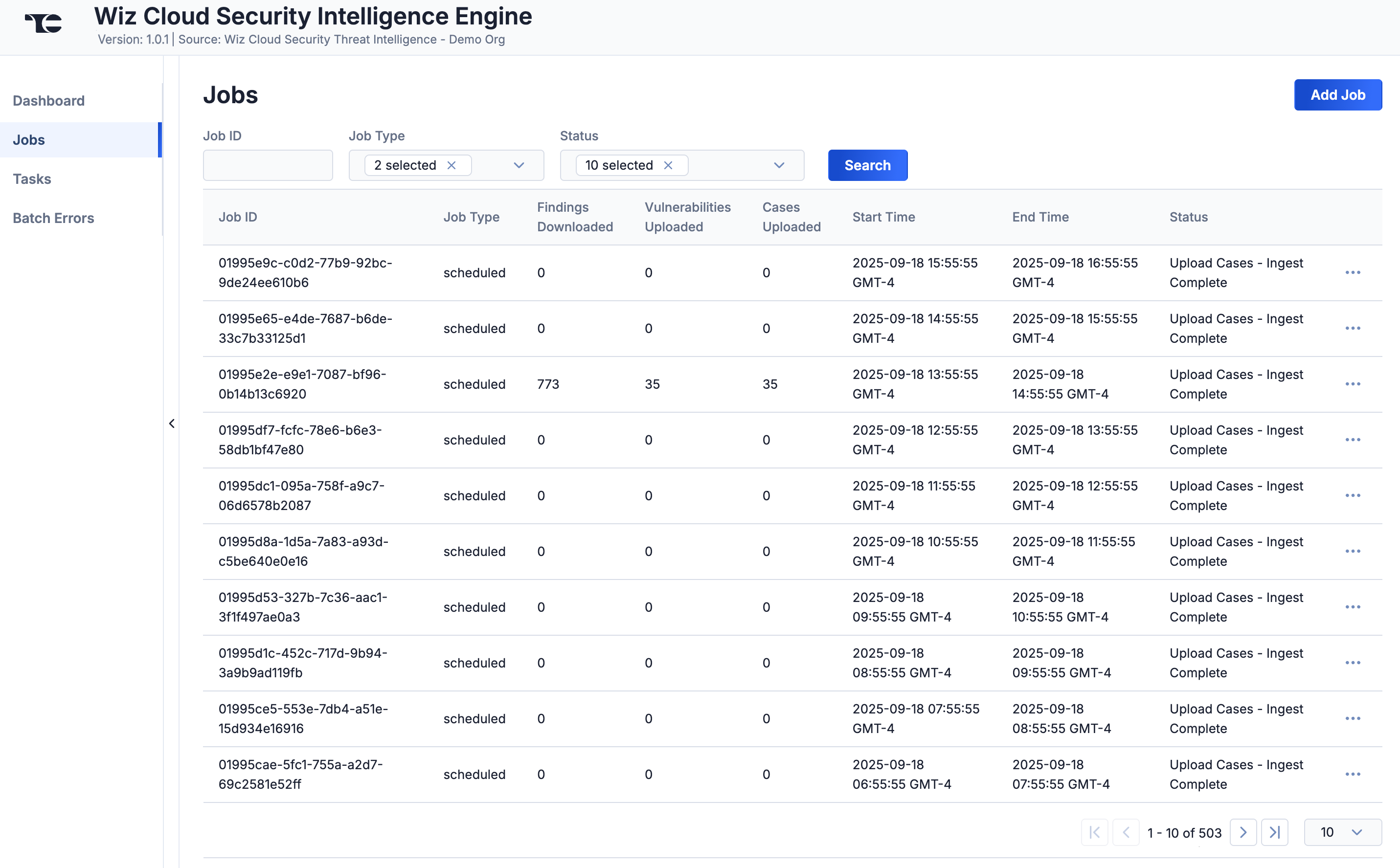
You can filter Wiz Cloud Security Intelligence Engine App Jobs by the following elements:
- Job ID: Enter text into this box to search for a Job by its Job ID.
- Job Type: Select Job types to display on the Jobs screen.
- Status: Select Job statuses to display on the Jobs screen.
Add a Job
You can add ad-hoc Jobs on the Jobs screen. Follow these steps to create a request for an ad-hoc Job for the Wiz Cloud Security Intelligence Engine App:
- Click Add Job (Figure 3).
- Fill out the fields on the Add Job drawer (Figure 4) as follows:
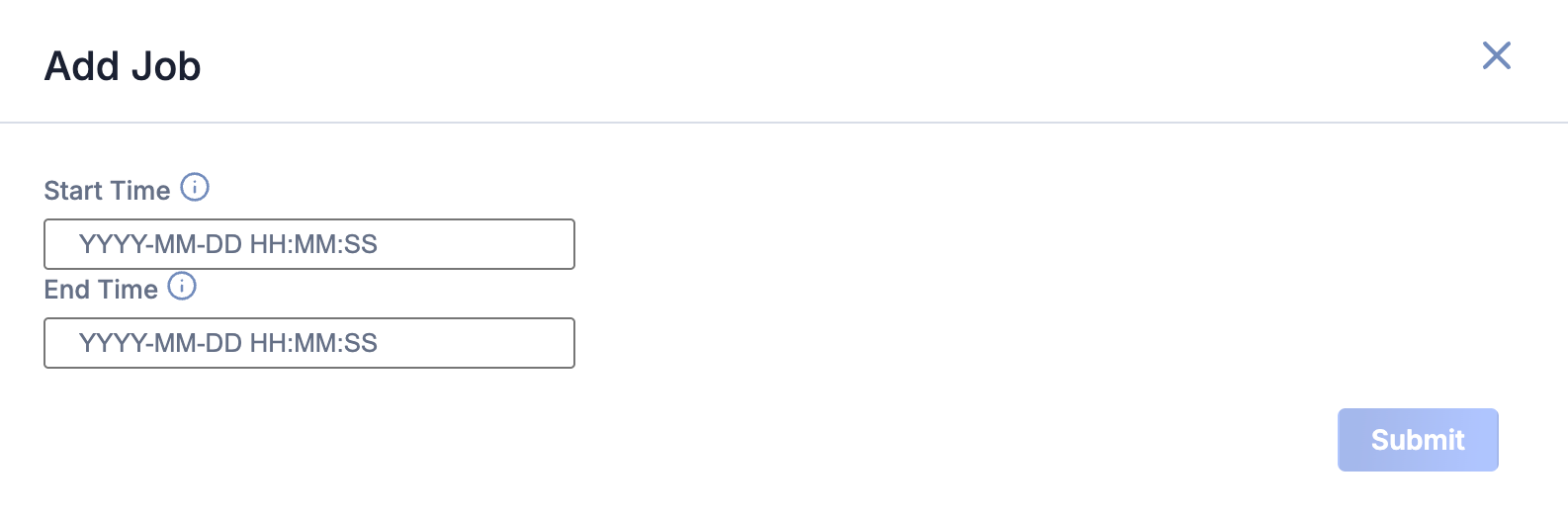
- Start Time: (Optional) Enter the time at which the Job should start.
- End Time: (Optional) Enter the time by which the Job should end.
- Click Submit to submit the request for the ad-hoc Job.
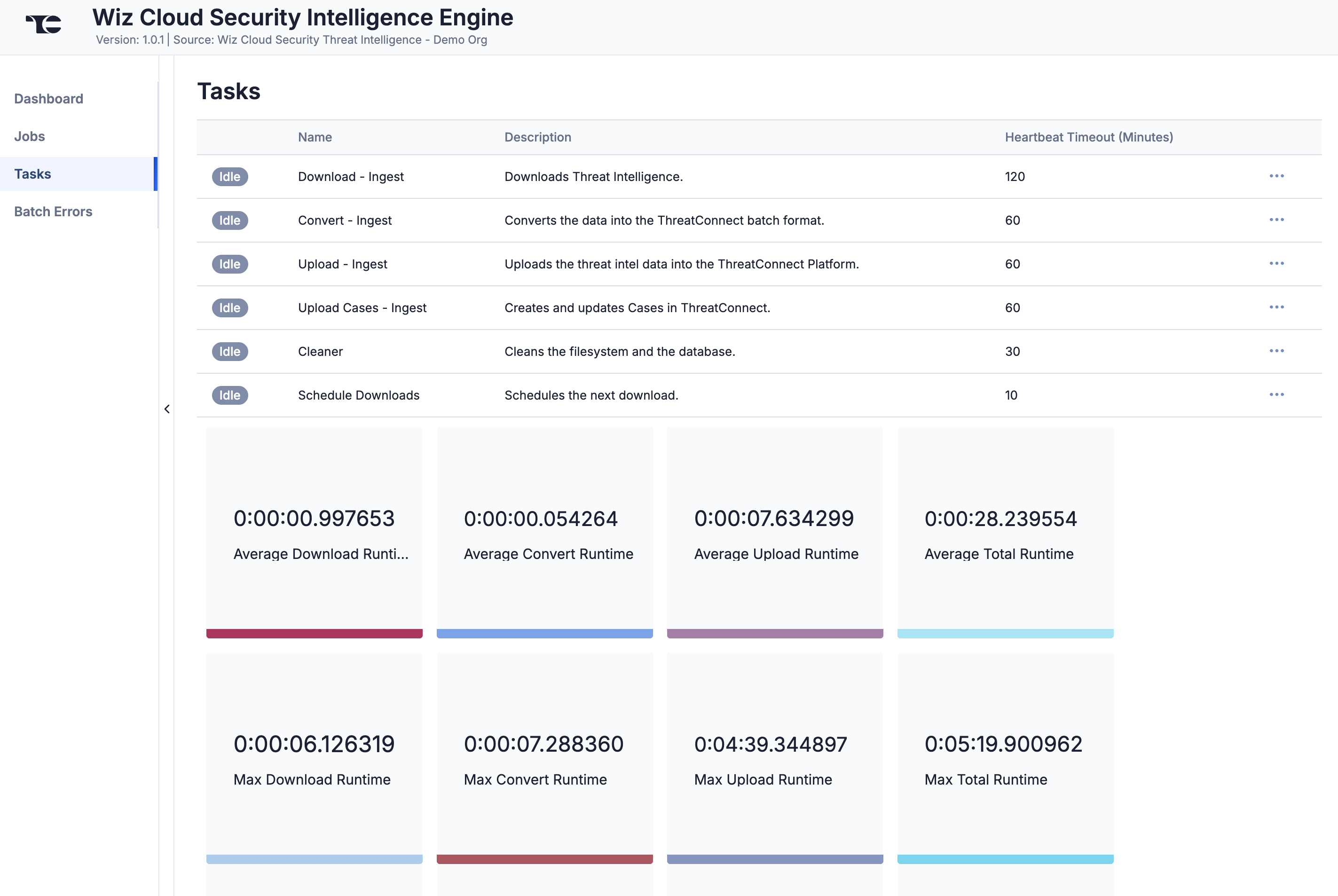
Tasks
The Tasks screen (Figure 5) displays all Tasks that may be part of a Job, including each step of the download, convert, and upload processes, as well as Tasks for the Wiz Cloud Security Intelligence Engine App, such as Monitor, Scheduler, and Cleaner. The current status (Idle, Paused, or Running), name, description, and heartbeat timeout length, in minutes, are displayed for each Task. The ⋯ menu in a Task’s row provides the following options, depending on the Task’s status:
- Run (idle and paused Tasks only)
- Pause (idle and running Tasks only)
- Resume (paused Tasks only)
- Kill (running Tasks only)
Under the table is a dashboard where you can view runtime analytics.
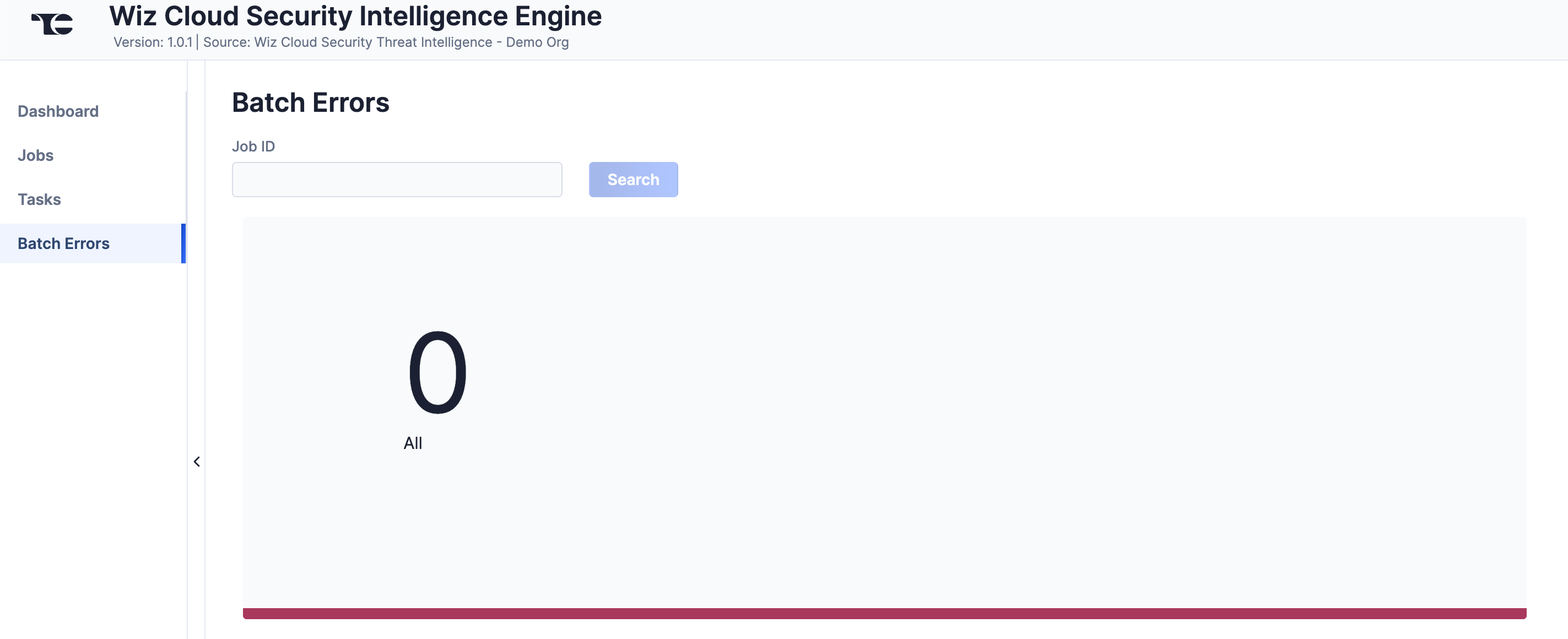
Batch Errors
The Batch Errors screen (Figure 6) displays an overview of the batch error types that have occurred for Job requests. You can enter keywords to filter by Job ID.
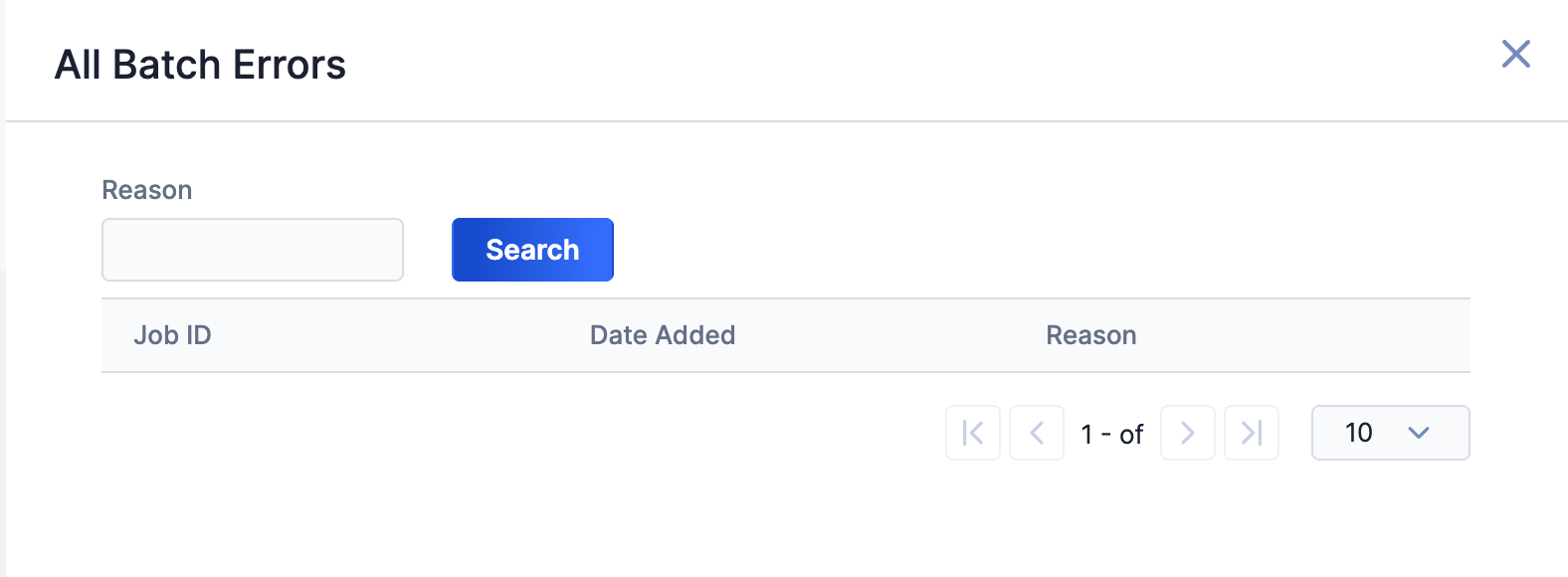
Click on an error type to open a drawer containing a table with details on all batch errors of that type (Figure 7). You can enter keywords to filter by reason for error.
Data Mappings
The data mappings in Table 2 and Table 3 illustrate how data are mapped from Wiz Cloud Security API endpoints to the ThreatConnect data model.
Vulnerability Finding
ThreatConnect object type: Vulnerability Group
| Wiz Cloud Security API Field | ThreatConnect Field |
|---|---|
| id | xid |
| name |
|
| CVEDescription | Description |
| firstDetectedAt | External Date Added |
| lastDetectedAt | External Last Modified |
| severity | Attribute: "Severity" |
| nvdSeverity | Attribute: "NVD Severity" |
| weightedSeverity | Attribute: "Weighted Severity" |
| impactScore | Attribute: "CVSS v3 Impact Score" |
| dataSourceName | Attribute: "Data Source Name" |
| hasExploit | Attribute: "Has Exploit" |
| hasCisaKevExploit | Attribute: "Has CISA KEV Exploit" |
| status | Attribute: "Status" |
| isHighProfileThreat | Attribute: "Is High Profile Threat" |
| vendorSeverity | Attribute: "Vendor Severity" |
| resolvedAt | Attribute: "Resolved" |
| detectionMethod | Attribute: "Detection Method" |
| locationPath | Attribute: "Location Path" |
| resolutionReason | Attribute: "Resolution Reason" |
| epssSeverity | Attribute: "EPSS Severity" |
| epssPercentile | Attribute: "EPSS Percentile" |
| epssProbability | Attribute: "EPSS Probability" |
| validatedInRuntime | Attribute: "Validated In Runtime" |
| layerMetadata | Attribute: "Layer Metadata" |
| cvssv2/attackVector | Attribute: "CVSS v2 Attack Vector" |
| cvssv2/attackComplexity | Attribute: "CVSS v2 Attack Complexity" |
| cvssv2/confidentialityImpact | Attribute: "CVSS v2 Confidentiality Impact" |
| cvssv2/integrityImpact | Attribute: "CVSS v2 Integrity Impact" |
| cvssv2/privilegesRequired | Attribute: "CVSS v2 Privileges Required" |
| cvssv2/userInteractionRequired | Attribute: "CVSS v2 User Interaction Required" |
| cvssv3/attackVector | Attribute: "CVSS v3 Attack Vector" |
| cvssv3/attackComplexity | Attribute: "CVSS v3 Attack Complexity" |
| cvssv3/confidentialityImpact | Attribute: "CVSS v3 Confidentiality Impact" |
| cvssv3/integrityImpact | Attribute: "CVSS v3 Integrity Impact" |
| cvssv3/privilegesRequired | Attribute: "CVSS v3 Privileges Required" |
| cvssv3/userInteractionRequired | Attribute: "CVSS v3 User Interaction Required" |
| cnaScore | Attribute: "CNA Score" |
ThreatConnect object type: Workflow Case
| Wiz Cloud Security API Field | ThreatConnect Field |
|---|---|
| name |
|
| portalUrl | Attribute: "Source" |
| Severity Count Summary | Attribute: "Severity Count Summary" See the “Frequently Asked Questions (FAQ)” section for more information. |
| Total Asset Count | Attribute: "Total Asset Count" |
| Total Issues Count | Attribute: "Total Issues Count" |
| Average Critical Severity Count | Attribute: "Average Critical Severity Count" |
| Average High Severity Count | Attribute: "Average High Severity Count" |
| Average Medium Severity Count | Attribute: "Average Medium Severity Count" |
| Average Low Severity Count | Attribute: "Average Low Severity Count" |
| Average Informational Severity Count | Attribute: "Average Informational Severity Count" |
| Max Critical Severity Count | Attribute: "Max Critical Severity Count" |
| Max High Severity Count | Attribute: "Max High Severity Count" |
| Max Medium Severity Count | Attribute: "Max Medium Severity Count" |
| Max Low Severity Count | Attribute: "Max Low Severity Count" |
| Max Informational Severity Count | Attribute: "Max Informational Severity Count" |
Leveraging Wiz Cloud Security Vulnerability Findings in ThreatConnect
Wiz Cloud Security identifies a high volume of vulnerabilities at varying severity levels across a large number of cloud resources like virtual machines, container images, and serverless instances. The Wiz Cloud Security Intelligence Engine App ingests these vulnerabilities and their context into ThreatConnect, making it convenient to cross-reference them against your other ThreatConnect data and correlate them to known vulnerability details from other threat intelligence sources like Flashpoint® and VulnCheck.
ThreatConnect captures vulnerability findings from Wiz Cloud Security in two object types:
- Vulnerability Group: Each Vulnerability Group object in the Source feed ingested from Wiz Cloud Security captures a known vulnerability (i.e., CVE) and, in the Vulnerability Group’s Attributes, its details and context.
- Workflow Case. A Workflow Case is created in your Organization for each Vulnerability Group created in the Source feed ingested from Wiz Cloud Security. The Vulnerability’s assets identified by Wiz and related source information are captured in the Case’s Attributes.NoteIf the Enable hasExploit filter is turned on in the Wiz Cloud Security Intelligence Engine App’s configuration, then Cases will be created only for CVEs that have a known exploit—that is, CVEs listed in the U.S. Cybersecurity & Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) Catalog. This setup is recommended to limit the daily runtime of the Wiz Cloud Security Intelligence Engine App, as well as to limit the Cases created to the CVEs most likely to pose a threat to your organization.
Wiz Cloud Security Vulnerability Groups
The vulnerability findings ingested from Wiz Cloud Security are collected as Vulnerability Groups in the Source feed created in the Wiz Cloud Security Intelligence Engine App’s configuration. Each Vulnerability includes a set of Attributes representing all the available data on that Vulnerability from Wiz Cloud Security. You can use the unified view for Vulnerabilities introduced in ThreatConnect 7.10, including Common Vulnerability Scoring System (CVSS) and Known Exploited Vulnerabilities (KEV) data, to find additional threat intelligence context for a vulnerability finding from Wiz Cloud Security and use this information to determine whether your organization may be susceptible to it.
Wiz Cloud Security Workflow Cases
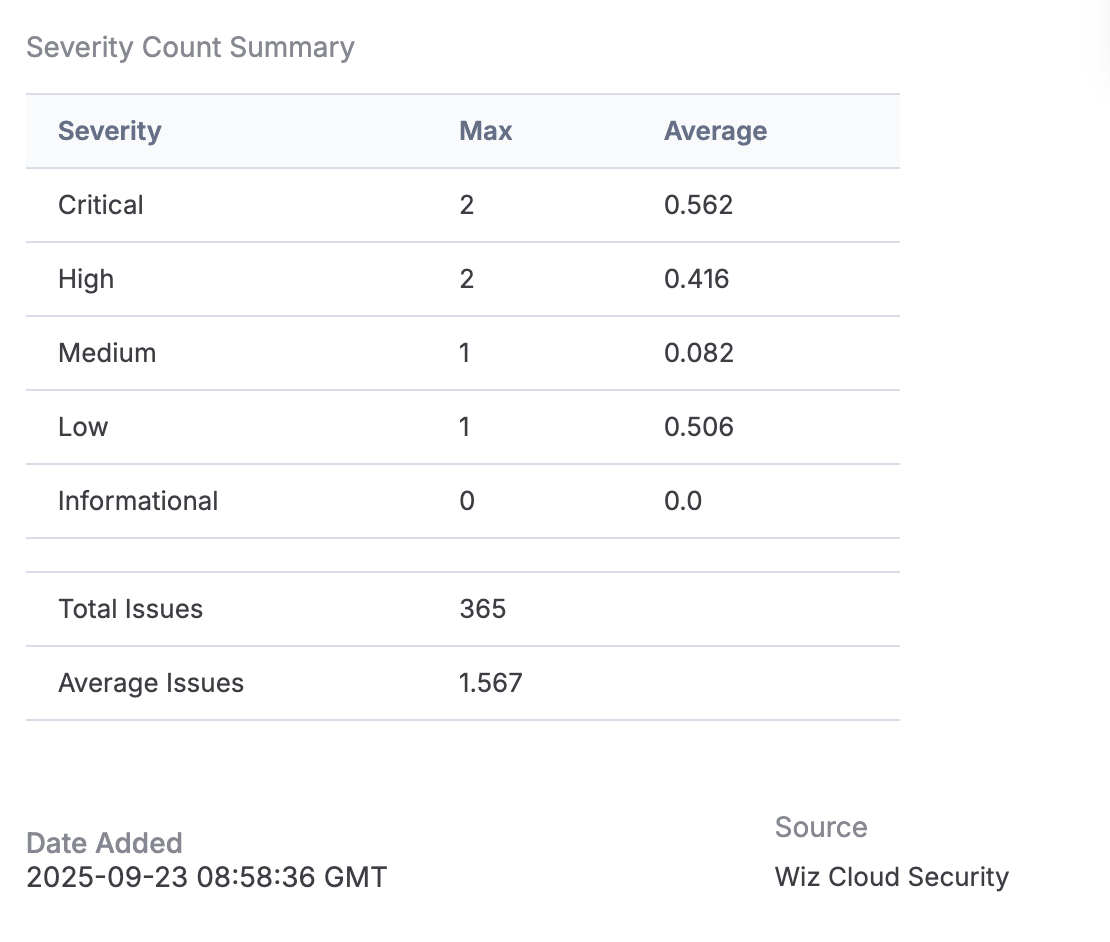
A Workflow Case is created for each ingested Vulnerability Group, allowing you to track and triage Wiz Cloud Security vulnerability findings for further research and operationalization. Each Case includes a set of Attributes aggregating information on every asset identified by Wiz Cloud Security as having that known vulnerability finding, including the Max and Average of each identified severity type (Critical, High, Medium, and Informational). In addition, each Case has a Severity Count Summary Attribute that summarizes all Wiz Cloud Security issue severity counts (Figure 8).
Recommended Wiz Cloud Security Intelligence Engine Workflow
The following steps are a recommended workflow for using the Wiz Cloud Security Intelligence Engine App to identify, analyze, and act on vulnerability findings in your ThreatConnect data:
- Identify a vulnerability that you want to investigate and resolve (e.g., CVE-2025-27363).
- Search for the Vulnerability Group for that vulnerability in ThreatConnect. For example, from the Search: Groups screen, filter the owners dropdown to only your Organization’s Source for the Wiz Cloud Security Intelligence Engine App, and then search for
CVE-2025-27363. - Open the Vulnerability Group’s Details screen.
- Explore the information in the unified view to identify any relevant CVSS, KEV, or other data that provide insight into the Vulnerability’s severity.HintIf the unified view is not your default view for the Vulnerability Details screen, select Unified View from the owner dropdown in the Details screen header.
- Select your Organization’s Source for the Wiz Cloud Security Intelligence Engine App in the owner dropdown in the Vulnerability Group’s Details screen header to view only that Source’s data on the Vulnerability Group.
- Select the Associations tab. The Case Associations card shows the associated Workflow Case created in your Organization for the Vulnerability.HintIf you do not see a Case Associations card on the Associations tab of the Details screen, make sure that your Organization’s Source for the Wiz Cloud Security Intelligence Engine App is selected in the owner dropdown in the screen’s header. The Case Associations card is not displayed on the Associations tab for the unified view.
- Click the link in the Name column for the associated Case to open the Case.
- Scroll to the Attributes card and, if necessary, increase the number of results shown per page.
- Find the Severity Count Summary Attribute. The Max and Average counts for the Critical severity level are the most important to resolve first. The Max count for the Critical severity level is the highest number of critical issues found on any cloud asset that has this vulnerability. The Average count for the Critical severity level is the average number of critical issues found on each asset that has this vulnerability. If the difference between the Max count and the Average count is less than 1, then Wiz has identified issues on nearly 100% of the assets, and it is crucial to address the vulnerability.
- Each Source Attribute has a Critical Severity Count. Find the Source Attributes with the highest Critical Severity Count, which represent the assets with the most critical issues found. Follow the link in these Attributes to the Wiz Cloud Security UI for more details.HintThe Max count for the Critical severity level in the table in the Severity Count Summary Attribute provides the highest Critical Severity Count for the Vulnerability. Search for all Source Attributes with that count. For example, if the Max count for the Critical severity level is
2, as in Figure 8, use the Find (Ctrl-F or command-F) feature to search forCritical Severity Count: 2to identify all Source Attributes with the highest Critical Severity Count.NoteThe Wiz Cloud Security Intelligence Engine App stores the 50 most recent Source links to the Wiz Cloud Security UI. - Take appropriate action on the cloud assets with Wiz-identified issues, such as by adding Tasks to the Case to carry out an investigation or remediation, or by closing the Case if no further action is required.
 to open the Vulnerability’s Details screen and access the unified view.
to open the Vulnerability’s Details screen and access the unified view.Frequently Asked Questions (FAQ)
How much data does the Wiz Cloud Security Intelligence Engine App ingest during its initial run?
The Wiz Cloud Security Intelligence Engine App ingests the past 30 days of vulnerability findings data from Wiz Cloud Security.
After its initial run, how frequently does the Wiz Cloud Security Intelligence Engine App ingest data?
The Wiz Cloud Security Intelligence Engine App runs on an hourly schedule. If any run takes longer than an hour to complete, which the initial run is likely to do, the next run will start an hour after the prior run completes and collect data from when the prior run started.
Why don’t I see a Service for the Wiz Cloud Security Intelligence Engine App for my Organization on the Services screen?
If you are an Organization Administrator attempting to configure a Service for the Wiz Cloud Security Intelligence Engine App for your Organization, but you do not see a Service for the App on the Services screen, then your System Administrator has not deployed the App for your Organization.
ThreatConnect® is a registered trademark, and TC Exchange™ is a trademark, of ThreatConnect, Inc.
Flashpoint® is a registered trademark of Flashpoint.
CVE® is a registered trademark of The MITRE Corporation.
30093-02 EN Rev. A


