- 27 Mar 2024
- 11 Minutes to read
-
Print
-
DarkLight
-
PDF
Domain-Spinning Workbench
- Updated on 27 Mar 2024
- 11 Minutes to read
-
Print
-
DarkLight
-
PDF
The ThreatConnect Domain-Spinning Workbench Spaces App is deprecated. It has been replaced by ThreatConnect Domain Thrasher.
Overview
The ThreatConnect® Domain-Spinning Workbench Spaces App provides four algorithms for identifying potential domain squats related to an input domain name. The list of domain names it provides can be used to take preventative measures against potential squats or actual squats. You can import selected domain names and registrant email addresses into ThreatConnect as Indicators. The methods for identifying squats include open-source algorithms and algorithms developed by the ThreatConnect Analytics team.
Before You Start
| Minimum Role(s) | Organization role of Standard User |
|---|---|
| Prerequisites |
|
App Features and Recommendations
Domain Squat Identification Algorithms
The Domain-Spinning Workbench App provides four algorithms for identifying domain squats:
- Bitsquatting: The Bitsquatting algorithm finds domains that would receive traffic if a bit flip occurs in an Internet device when a given domain is requested.
- DNSTwist: The DNSTwist algorithm finds domain names that look similar to a given domain name or are possible variants of a given domain name if a user makes a typo when entering in the domain name (“typosquatting”).
- URLCrazy: The URLCrazy algorithm detects many different variations of a domain, including basic bitsquatting, typosquatting, and common misspellings.
- XNTwist: The XNTwist algorithm detects internationalized domain names that may be squatting on a domain name.
WHOIS Lookup Options
The Domain-Spinning Workbench App provides two options for retrieving WHOIS data:
- DomainTools WHOIS Lookup: This option is the best choice for users who have a subscription to the DomainTools service.
- ThreatConnect WHOIS Lookup: This option is the best choice for users who do not have a subscription to the DomainTools service.
Preparatory Recommendations
It is recommended that all of the Playbook URLs be saved by an Organization Administrator as text variables in your Organization for easier entry into the App configuration and subsequent modification. For instructions on creating variables, see the “Variables” section of ThreatConnect Organization Administration Guide.
It is recommended that you set your Log Out Interval to at least 2 hours so that your logins do not time out during the spin. For instructions on changing your Log Out Interval, see the “Overview Tab” section of My Profile.
Adding and Configuring the App
- Follow the steps in the “Adding a Central Space and Configuring an App” section of Central Spaces to create a Space and add the TCS - Domain Spinning v1.0 App to the Space. The final screen in this process will look like Figure 1.
- Click Configure
 to configure the App. The Configure App screen will be displayed (Figure 2).
to configure the App. The Configure App screen will be displayed (Figure 2).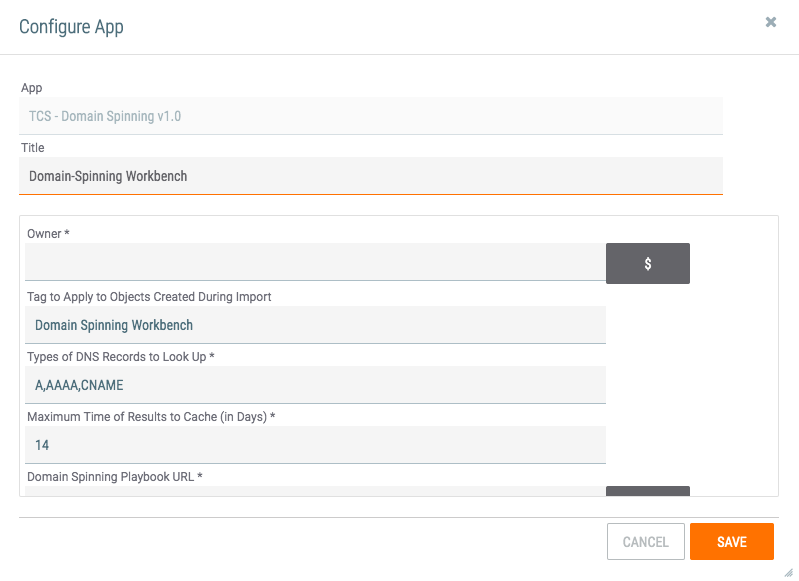
- Owner: Enter the name of the Organization that will own any Indicators and other objects imported from the Domain-Spinning Workbench App, or use the $ button to select an owner from the list of variables that is displayed.
- Tag to Apply to Objects Created During Import: Enter a Tag to apply to all objects imported from the App. A default Tag is provided, and it may be modified if desired.
- Types of DNS Records to Look Up: This field lists default DNS Lookup record types that the App will access. Add or remove any record types as desired.
- Maximum Time of Results to Cache (in Days): The information generated by the App is stored in ThreatConnect’s DataStore. This field indicates the maximum amount of time the data are cached in the DataStore before they are refreshed upon another run of the App. The default amount of time is 14 days.
- Domain Spinning Playbook URL: Enter the URL for the Domain Spinning Playbook, or, if it has been entered as a variable (see the "Preparatory Recommendations" section), use the $ button to select it from the list of variables that is displayed. The following Playbooks are valid choices: Bitsquatting, DNSTwist, URLCrazy, and XNTwist. Each Playbook uses a different algorithm to identify domains.
- DNS Lookup Playbook URL: Enter the URL for the DNS Lookup Playbook, or, if it has been entered as a variable (see the "Preparatory Recommendations" section), use the $ button to select it from the list of variables that is displayed.
- WHOIS Lookup Playbook URL: Enter the URL for the Whois Lookup Playbook, or, if it has been entered as a variable (see the "Preparatory Recommendations" section), use the $ button to select it from the list of variables that is displayed. The following Playbooks are valid choices: DomainTools WHOIS Lookup (requires a key; available only to users who have purchased a subscription to DomainTools) and ThreatConnect WHOIS Lookup (available to all ThreatConnect users; note that this service does not produce emails).
- Import Playbook URL: Enter the URL for the Import Playbook (Domain Squat Import), or, if it has been entered as a variable (see the "Preparatory Recommendations" section), use the $ button to select it from the list of variables that is displayed.
- Click the SAVE button.NoteInstead of changing configuration settings in one instance of the Spaces App in order to toggle between Domain Spinning Playbooks or types of Whois Lookup Playbooks, you can add multiple instances of the App can be added to the Spaces screen, each with its own configuration settings (e.g., one that uses the Bitsquatting Playbook and DomainTools Whois Lookup, another that uses the DNSTwist Playbook and ThreatConnect Whois Lookup, etc.), so that a different instance of the Spaces App can be used instead of changing configuration settings in one instance.
- The Spin screen for the App will be displayed (Figure 3).
Using the App
- On the Spin screen (Figure 3), enter a domain name and then click the Spin button. This example uses “google.com”.NoteClicking on the down arrow to the left of the Spin button will display a list of previously searched domains, if any.NoteThe Spin button will be grayed out and unclickable until a period and the first letter of a top-level domain (e.g., .com, .edu) are added to the entry. To get results that make sense, enter the entire top-level domain (e.g., “google.com” rather than just “google.c”) before clicking the Spin button.
- The domain-spinning process will begin. If the domain has been spun within the Maximum Time of Results to Cache (Figure 2), then the spinning process will be short (i.e., a few seconds to several minutes), as the App will be searching only for new results since the last cache. If the domain has not been spun within the Maximum Time of Results to Cache, the process will probably take a long time (i.e., 15 minutes to 2 hours or more). Once the spin is initiated, the screen will indicate that it is collecting data for spun domains (Figure 4).NoteIf at any point, the spin gets interrupted (e.g., your login times out, you close out of ThreatConnect), a subsequent re-spin will take less time, because the results of the interrupted first spin will have been cached.
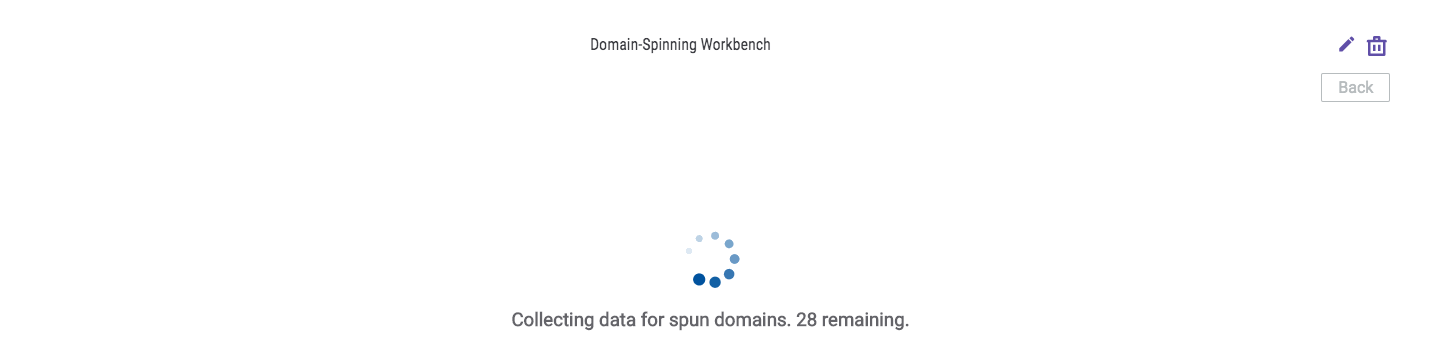
- After the spin is underway, the screen will change to a countdown indicating the number of domains in the spin that have not yet had their data collected (Figure 5).NoteThe countdown does not always move in real time. It is best used as a general measure of progress rather than an exact indicator of how many domains remain in the spinning process.
- When the spinning process finishes, a screen with the results will be displayed (Figure 6).
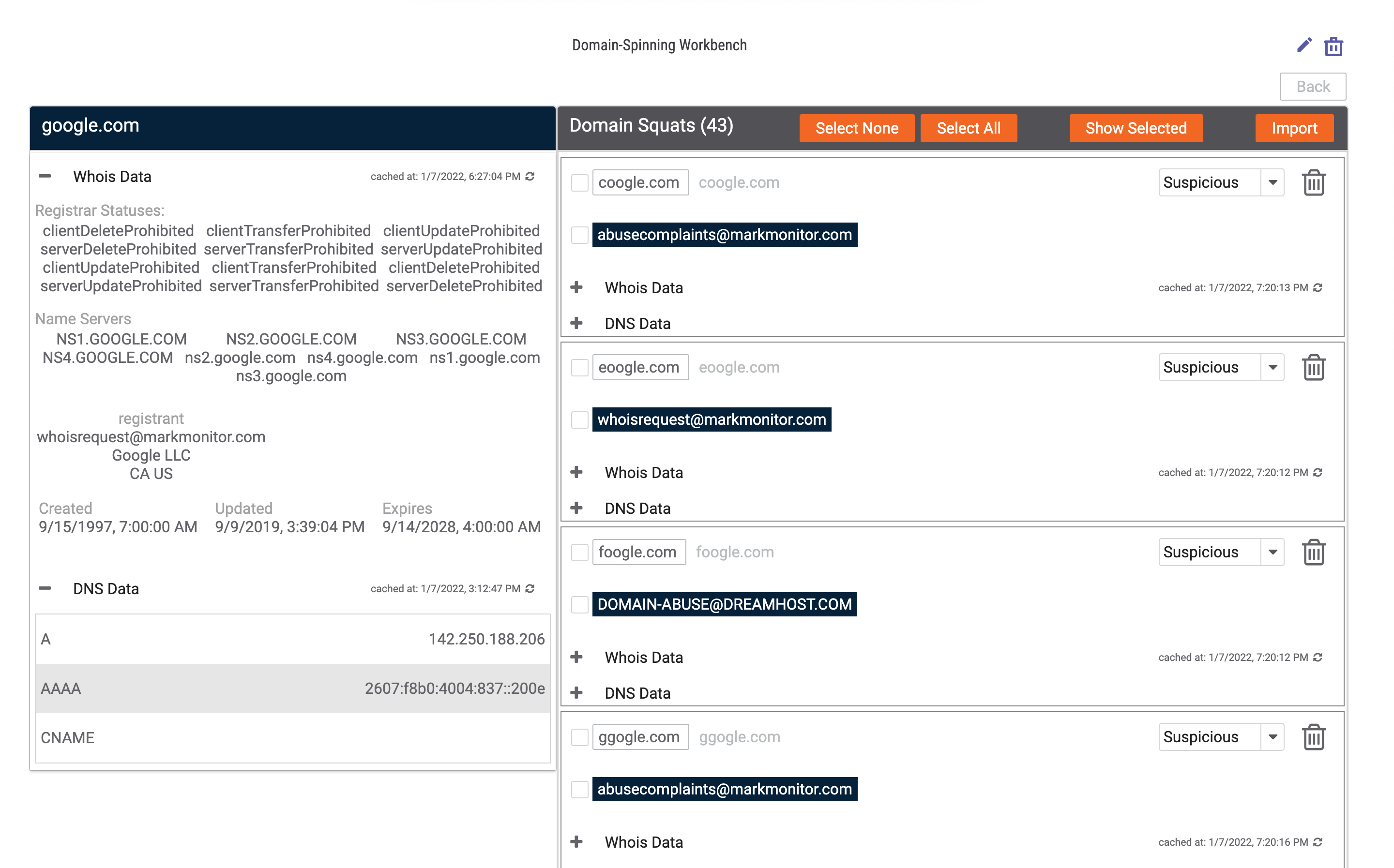
- The box on the left side of the screen in Figure 6 provides Whois Data and DNS Data for the spun domain. Both sections may be collapsed by clicking on the minus sign to the left of their respective section header. The text to the right of each section’s header shows when the data in that section was last cached. To refresh the data, click Refresh
 to the right of the cache information.
to the right of the cache information. - The Domain Squats box on the right side of the screen in Figure 6 provides all potential domain squats identified by the Domain-Spinning Workbench App. The number of squats found is shown in parentheses next to the Domain Squats label. A detailed explanation of these results is provided in the “Viewing Domain Squats Results” section.
- Click the Back button above the Domain Squats box to return to the main spin page (Figure 3).
- The box on the left side of the screen in Figure 6 provides Whois Data and DNS Data for the spun domain. Both sections may be collapsed by clicking on the minus sign to the left of their respective section header. The text to the right of each section’s header shows when the data in that section was last cached. To refresh the data, click Refresh
Viewing Domain Squats Results
The results of the Domain-Spinning Workbench, as shown in Figure 6, are provided on the right-hand side of the screen. Each result consists of several components, as shown in Figure 7.
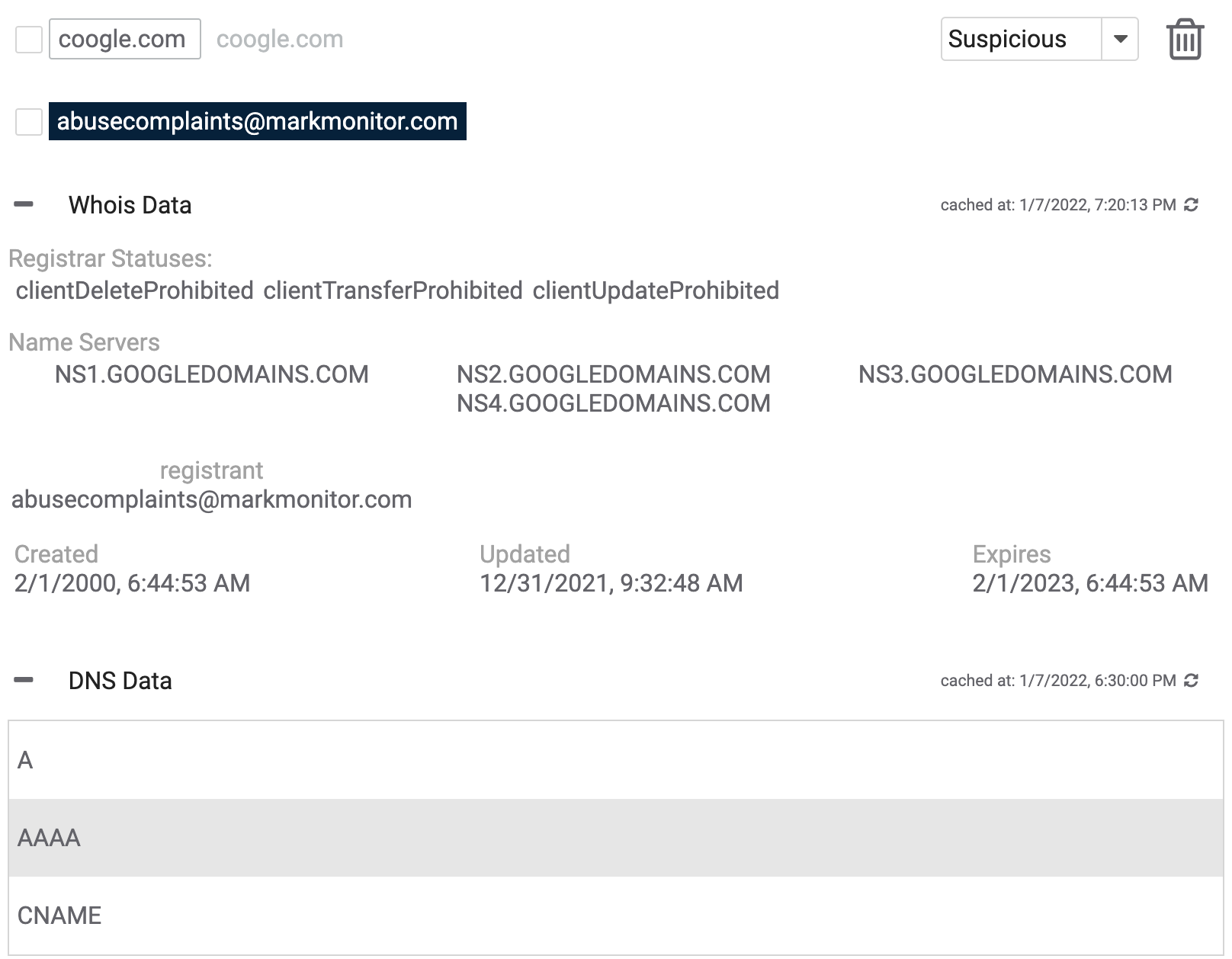
- Squat domain name: The domain name of the potential squat. The name is displayed twice, once in a box and once in light-gray text. If the domain has Unicode characters in it, the light-gray text will display the Unicode characters, while the text in the box will display an IDNA-encoded (punycode) domain name.
- Registrant email address: The email address under which the domain name is registered with Whois.
- Whois Data: Whois information for the potential squat. Click the plus sign (Figure 6) to expand this section. The “cached at” text on the right-hand side of this element shows when the data in this section was last cached. To refresh the data, click Refresh
 to the right of the cache information.
to the right of the cache information. - DNS Data: DNS information for the potential squat. Click the plus sign (Figure 6) to expand this section. The “cached at” text on the right-hand side of this element shows when the data in this section was last cached. To refresh the data, click Refresh
 to the right of the cache information.
to the right of the cache information. - Label: The dropdown box at the upper-right corner provides three options (Suspicious, Potential, and Malicious) for classifying the danger level of the squat. Domains that have a registrant email address (i.e., the domain name is registered) have Suspicious as their default label. Domains that do not have a registrant email address (i.e., the domain name is not registered; “Domain Not Registered” is displayed in place of the registrant email address) have Potential as their default label. Users can change the label for each item to reflect their assessment of the danger level of the squat. Thus, changing a squat’s label to Malicious indicates that you have determined that the domain is malicious.NoteThe label applies to both the squat domain name and the registrant email address.
- Delete
 icon: Deletes the domain from the results set. Note that clicking Delete
icon: Deletes the domain from the results set. Note that clicking Delete will immediately delete the domain. No confirmation window will be displayed.
will immediately delete the domain. No confirmation window will be displayed.
Importing Domain Squat Results into ThreatConnect
Follow these steps to import and save squat domain names and registrant email addresses as Indicators in ThreatConnect:
- Select the checkbox for each item that you want to import, or click the Select All button at the top of the Domain Squats box to select everything. To clear all selected items, click the Select button.NoteClicking the Select All button will select all items in the search, not just the ones on the current page.ImportantIf a squat domain name is selected, but the registrant email address associated with it is not, the registrant email address will not be imported. However, if a registrant email address is selected, but the squat domain name associated with it is not selected, the squat domain name will still be imported.
- To view all selected items, click the Show Selected button. The Domain Squat Results pane will display only items that were selected (Figure 8). Click the Show All button to go back to displaying all squat results.
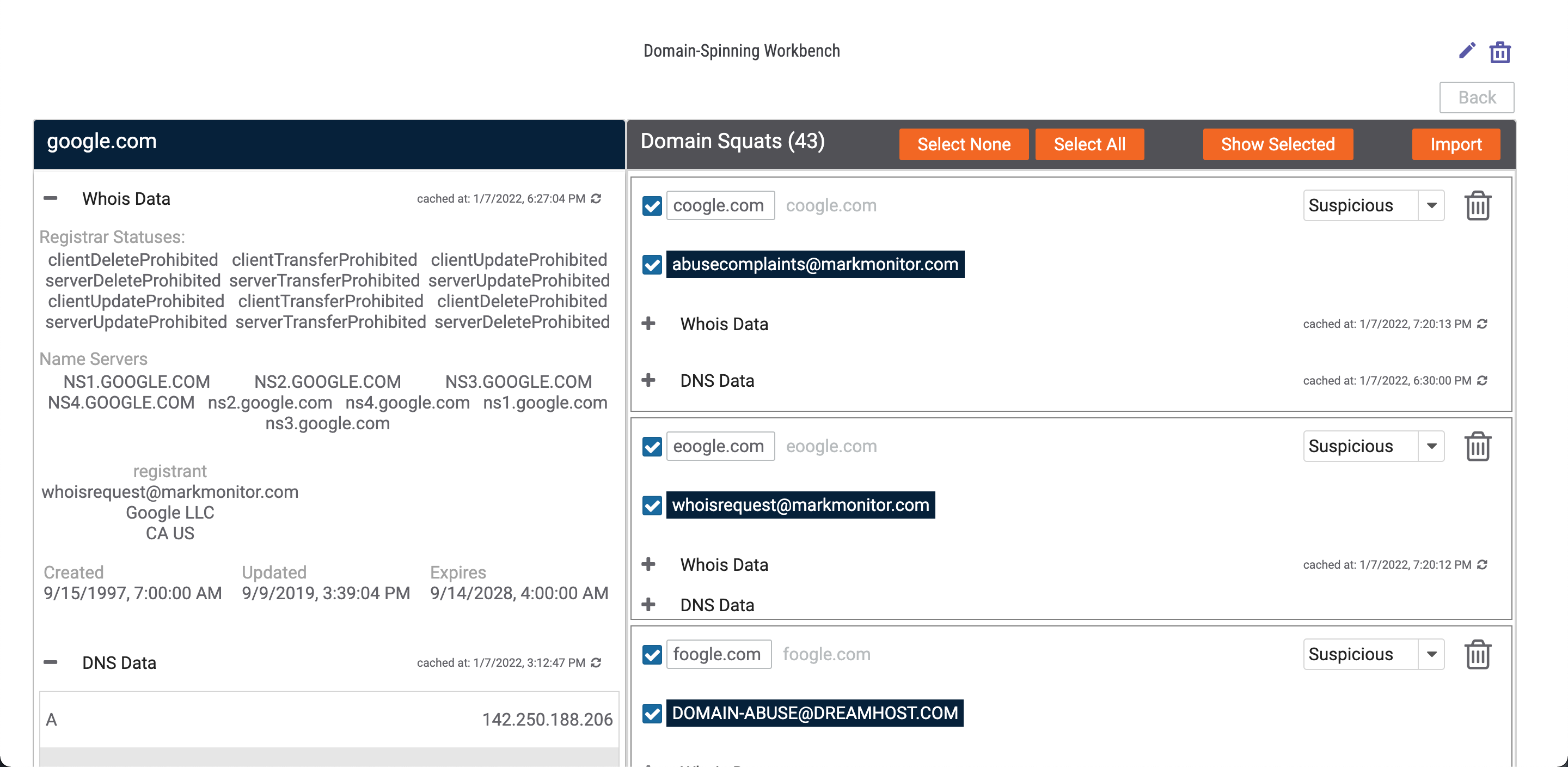
- Click the Import button to import all selected items. The Do you want to create these entities? window will be displayed with selected items asking for confirmation to import the queried domain name as an Incident and the selected squat domain names and registrant email addresses as Indicators in ThreatConnect (Figure 9).
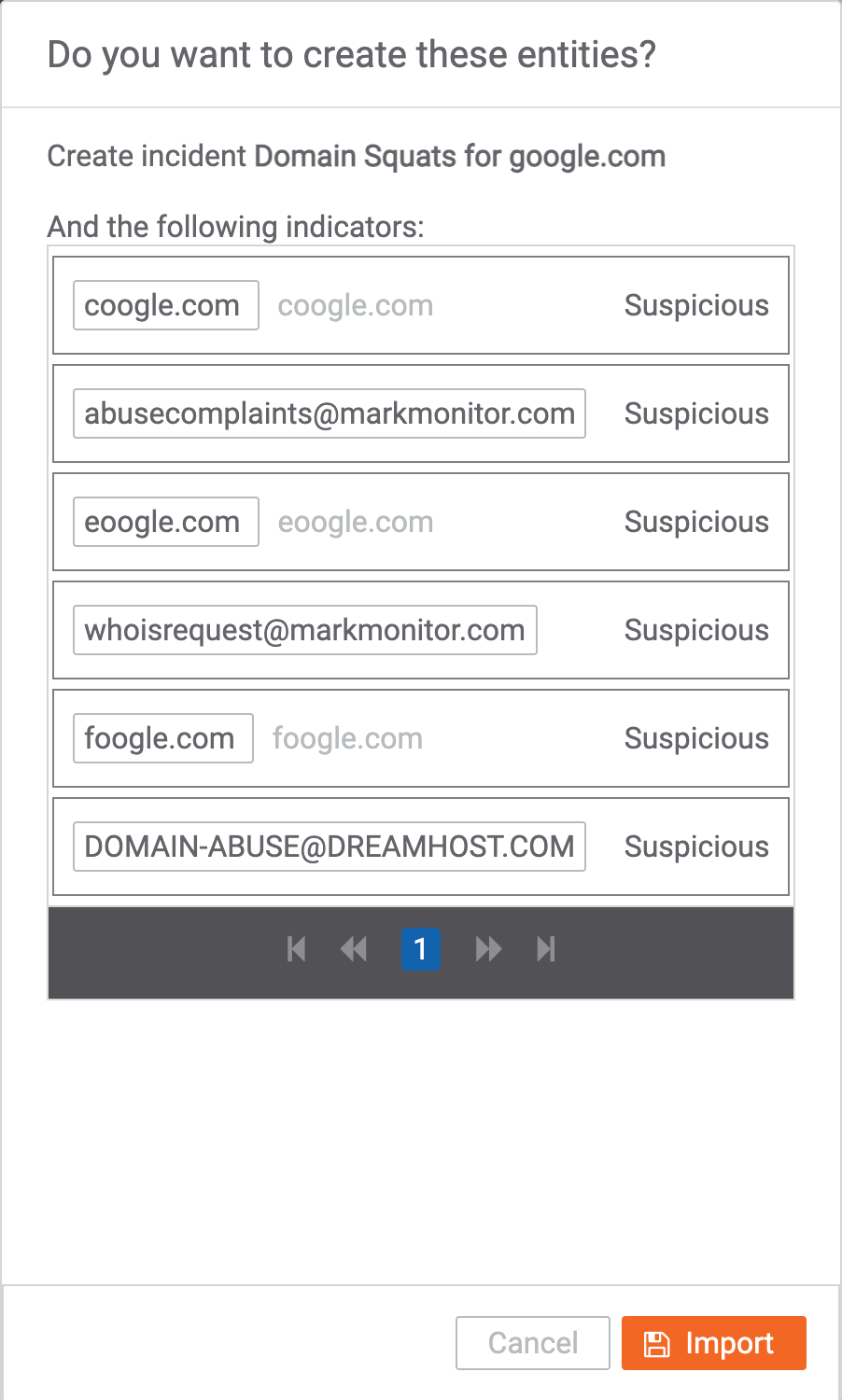
- Click the Import button on the Do you want to create these entities? window to create the Incident and import the Indicators.
When the import process is complete, the Details screen for the new Incident will be displayed. The Indicators will all be associated with the Incident, and the Incident will be tagged with the text entered in the Tag to apply to objects created during import field in Figure 2 (Domain Spinning Workbench in this example). The squat domain names will be imported as Hosts, and the registrant email addresses will be imported as Email Addresses. Figure 10 shows the Associations tab of the Incident’s Details screen, demonstrating that the six selected Indicators have been associated to the Incident.
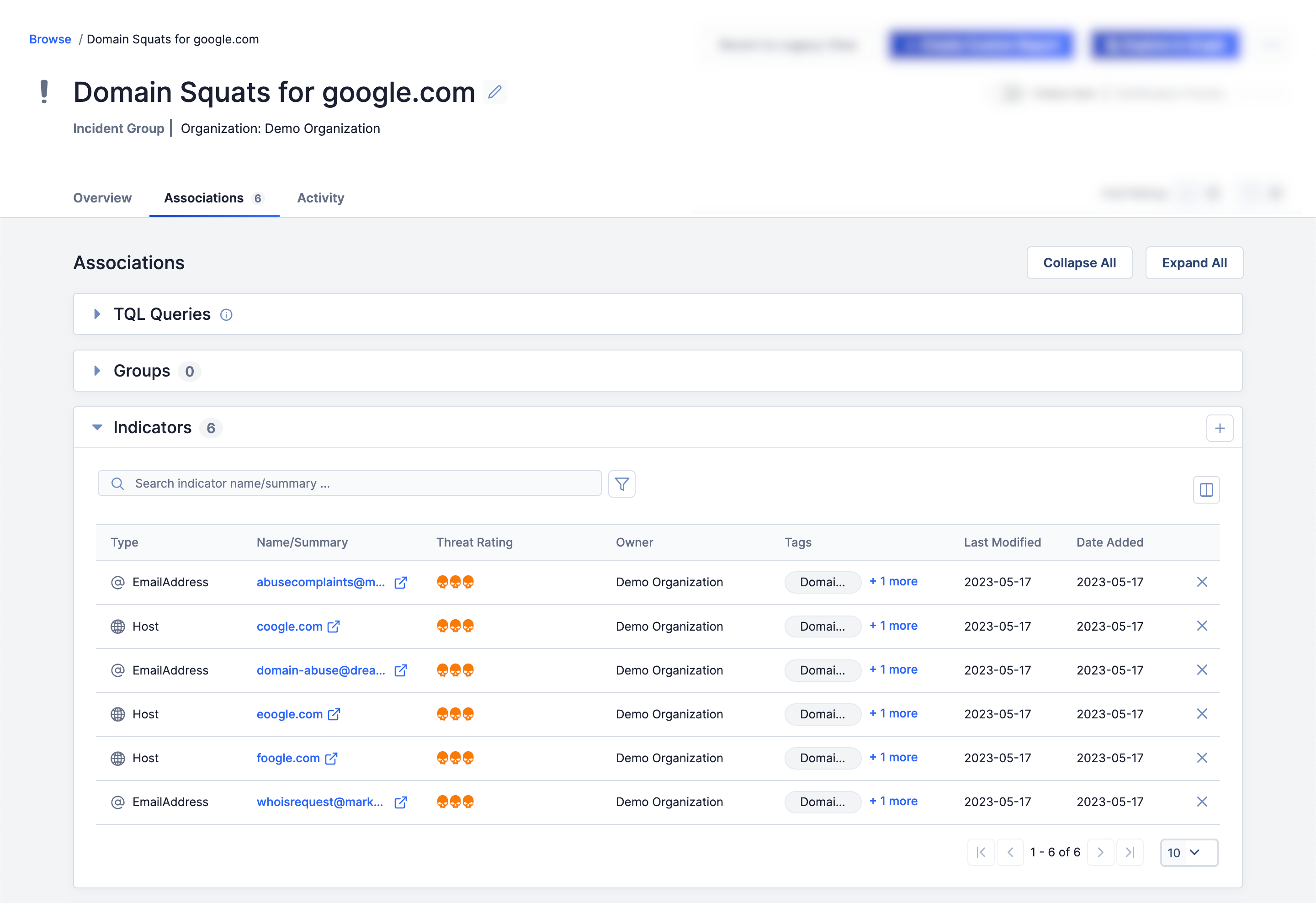
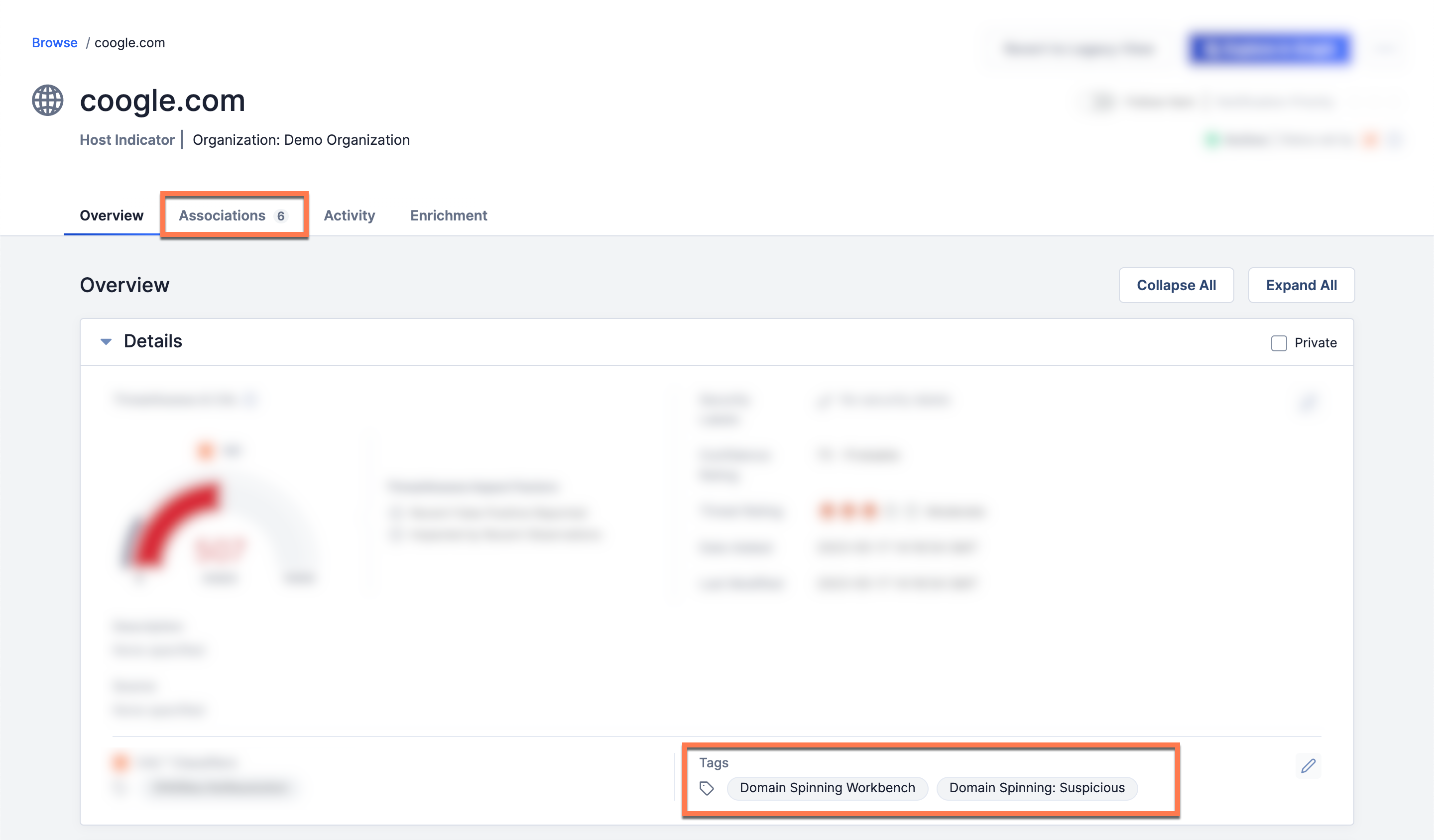
Figure 11 shows the Details screen for one of the imported Indicators. It is associated to the Incident created by the Domain-Spinning Workbench App and the other five Indicators imported into ThreatConnect, as indicated by the 6 to the right of the Associations tab name. Also, in addition to the Tag specified in the Tag to apply to objects created during import field in Figure 2 (Domain Spinning Workbench in this example), a Tag for the Suspicious label was created and applied to the Indicator (Domain Spinning: Suspicious in this example).
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
DomainTools® is a registered trademark of DomainTools, LLC.
20071-01 v.01.I


