- 26 Jun 2025
- 10 Minutes to read
-
Print
-
DarkLight
-
PDF
CrowdStrike Falcon Intelligence Engine Integration User Guide
- Updated on 26 Jun 2025
- 10 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The CrowdStrike Falcon® Intelligence Engine integration with ThreatConnect® lets you ingest Group (Actor, Malware, Report, and Vulnerability) and Indicator data, along with all of their context, from the CrowdStrike Falcon Intelligence feed into ThreatConnect.
The following ThreatConnect Indicator types are supported for import from CrowdStrike Falcon Intelligence: Address, CIDR, Email Address, Email Subject, File, Host, Mutex, Registry Key, URL, and User Agent. Indicators are associated with Report and Intrusion Set Groups when imported into ThreatConnect. Reports Groups are also associated with Intrusion Set Groups when imported into ThreatConnect. In both cases, the Intrusion Set Groups represent related Actor Groups imported from CrowdStrike Falcon Intelligence.
Dependencies
ThreatConnect Dependencies
- Active ThreatConnect Application Programming Interface (API) Key
CrowdStrike Dependencies
- Active subscription to CrowdStrike Falcon Intelligence with API key with the following permissions:
- Actors: Read=Yes
- Indicators: Read=Yes
- Malware Families: Read=Yes
- Reports: Read=Yes
Application Setup and Configuration
Follow these steps to install the CrowdStrike Falcon Intelligence Engine App via TC Exchange™:
- Log into ThreatConnect with a System Administrator account.
- Hover over Settings
 on the top navigation bar and select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen.
on the top navigation bar and select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen. - Locate the CrowdStrike Falcon Intelligence Engine App on the Catalog tab. Then click Install
 in the Options column to install the App.
in the Options column to install the App. - After you install the CrowdStrike Falcon Intelligence Engine App, the Feed Deployer will open automatically. Use the Feed Deployer to set up and configure the App. See the “Configuration Parameters” section for more information on the parameters available during the configuration and deployment process.
Configuration Parameters
Parameter Definitions
The parameters defined in Table 1 apply to the configuration parameters available when using the Feed Deployer to configure the CrowdStrike Falcon Intelligence Engine App.
| Name | Description | Required? |
|---|---|---|
| Source Tab | ||
| Sources to Create | Enter the name of the Source for the feed. | Required |
| Owner | Select the Organization in which the Source will be created. | Required |
| Activate Deprecation | Select this checkbox to allow confidence deprecation rules to be created and applied to Indicators in the Source. | Optional |
| Create Attributes | Select this checkbox to allow custom Attribute Types to be created in the Source. | Optional |
| Parameters Tab | ||
| Launch Server | Select tc-job as the launch server for the Service corresponding to the Feed API Service App. | Required |
| CrowdStrike API Endpoint | Select the CrowdStrike® API endpoint from which to retrieve data. Available choices include the following:
| Required |
| Group Types | Select the Group types to import from CrowdStrike Falcon Intelligence. Available options include the following:
| Required |
| Indicator Types | Select the Indicator types to import from CrowdStrike Falcon Intelligence. Available options include the following:
| Required |
| Variables Tab | ||
| CrowdStrike Falcon Intelligence API Secret | Enter the CrowdStrike API secret. | Required |
| CrowdStrike Falcon Intelligence API ID | Enter the CrowdStrike API ID. | Required |
| Confirm Tab | ||
| Run Feeds after deployment | Select this checkbox to run the CrowdStrike Falcon Intelligence Engine App immediately after the deployment configuration is complete (i.e., after you click DEPLOY on the Feed Deployer window. | Optional |
| Confirm Deployment Over Existing Source | This checkbox will be displayed if the Source entered in the Sources to Create field has previously been deployed to the Organization selected in the Owner dropdown on the Source tab. Select this checkbox to confirm that you want the CrowdStrike Falcon Intelligence Engine App to write data to the same Source. This process will create a new Service for the CrowdStrike Falcon Intelligence Engine App. As such, it is recommended that you delete the old Service associated with the CrowdStrike Falcon Intelligence EngineApp after the new one is created. Important If you do not select this checkbox, the DEPLOY button will be grayed out, and you will not be able to deploy the Service. Return to the Source tab and enter a different Source or select a different Organization and then proceed through the tabs of the Feed Deployer window again. | Optional |
CrowdStrike Falcon Intelligence Engine UI
After successfully configuring and activating the Feed API Service, you can access the CrowdStrike Falcon Intelligence Engine user interface (UI). This UI allows you to interact with and manage the CrowdStrike Falcon Intelligence integration.
Follow these steps to access the CrowdStrike Falcon Intelligence Engine UI:
- Log into ThreatConnect with a System Administrator account.
- On the top navigation bar, hover over Playbooks and select Services.
- Locate the CrowdStrike Falcon Intelligence Engine Feed API Service.
- Click the link in the Service’s API Path field. The CrowdStrike Falcon Intelligence Engine UI will open in a new browser tab.
The following screens are available in the CrowdStrike Falcon Intelligence Engine UI:
Dashboard
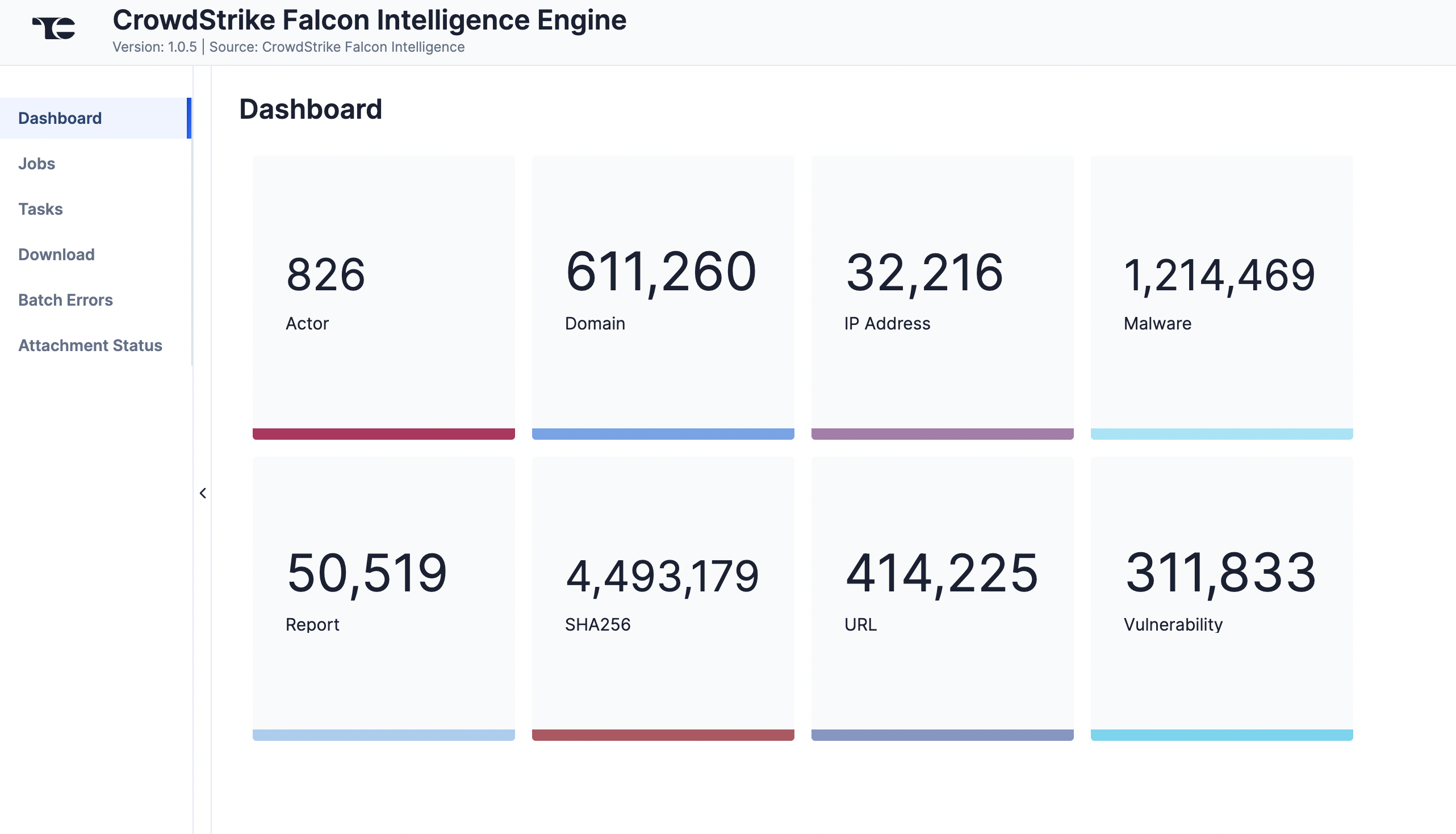
The Dashboard screen (Figure 1) provides an overview of the total number of each Group and Indicator type retrieved from CrowdStrike Falcon Intelligence. Depending on the available data, cards representing all or a subset of these objects will be displayed on the Dashboard screen.
Jobs
The Jobs screen (Figure 2) breaks down the ingestion of CrowdStrike Falcon Intelligence data into manageable Job-like tasks, displaying all processes that are pending, in progress, complete, and failed. The ⋯ menu in a Job’s row provides the following options:
- Details: View details for the Job, such as download, convert, and upload start and complete times and counts of downloaded and batched Groups and Indicators.
- Download Files: Download metadata files for all Jobs and data (convert, download, and upload) files for completed Jobs.
- Batch Errors: View errors that have occurred for the Job on the Batch Errors screen.
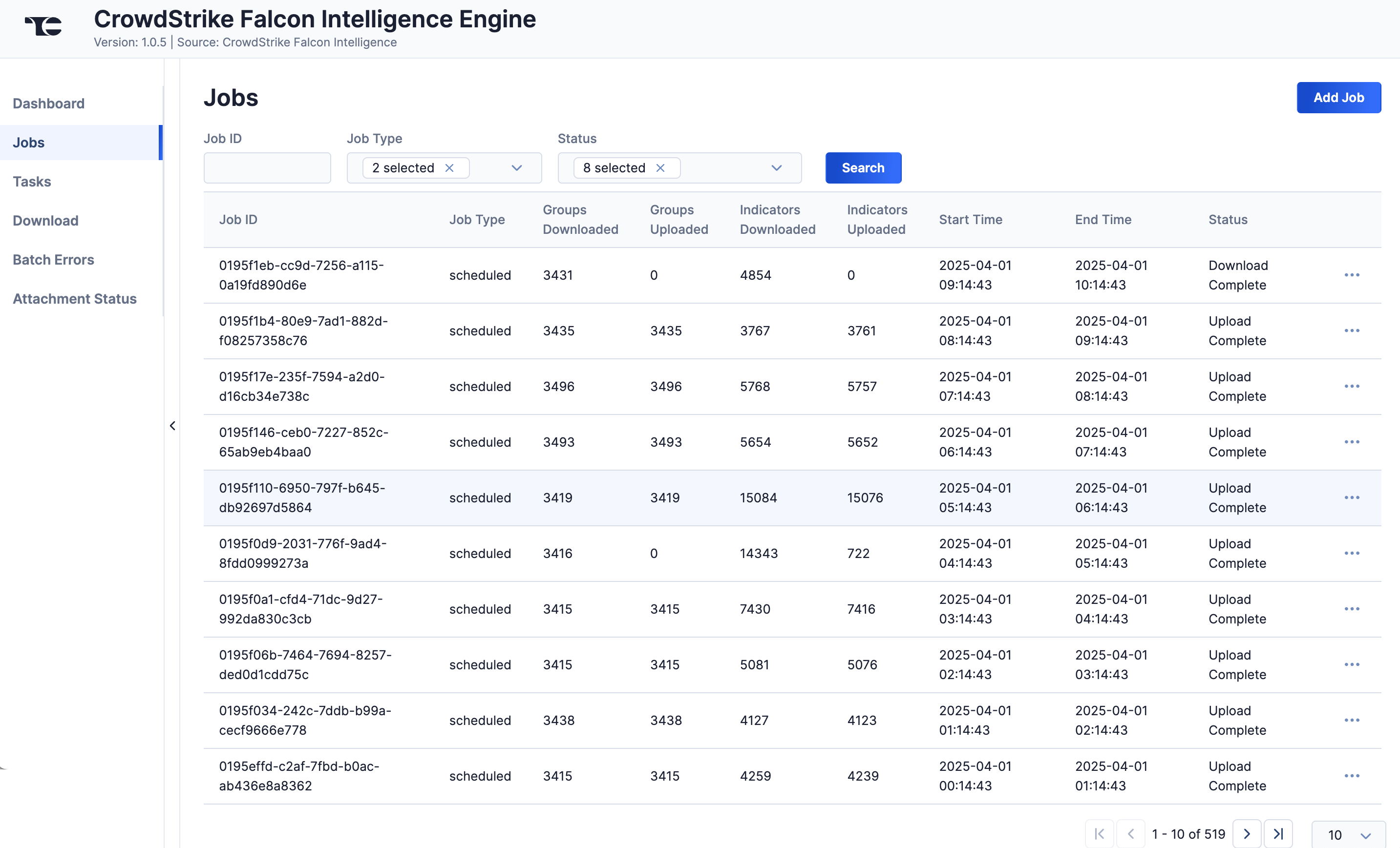
You can filter CrowdStrike Falcon Intelligence Engine App Jobs by the following elements:
- Job ID: Enter text into this box to search for a Job by its Job ID.
- Job Type: Select Job types to display on the Jobs screen.
- Status: Select Job statuses to display on the Jobs screen.
Add a Job
You can add ad-hoc Jobs on the Jobs screen. Follow these steps to create a request for an ad-hoc Job for the CrowdStrike Falcon Intelligence Engine App:
- Click the Add Job button at the upper right of the Jobs screen (Figure 2).
- Fill out the fields on the Add Job drawer (Figure 3) as follows:
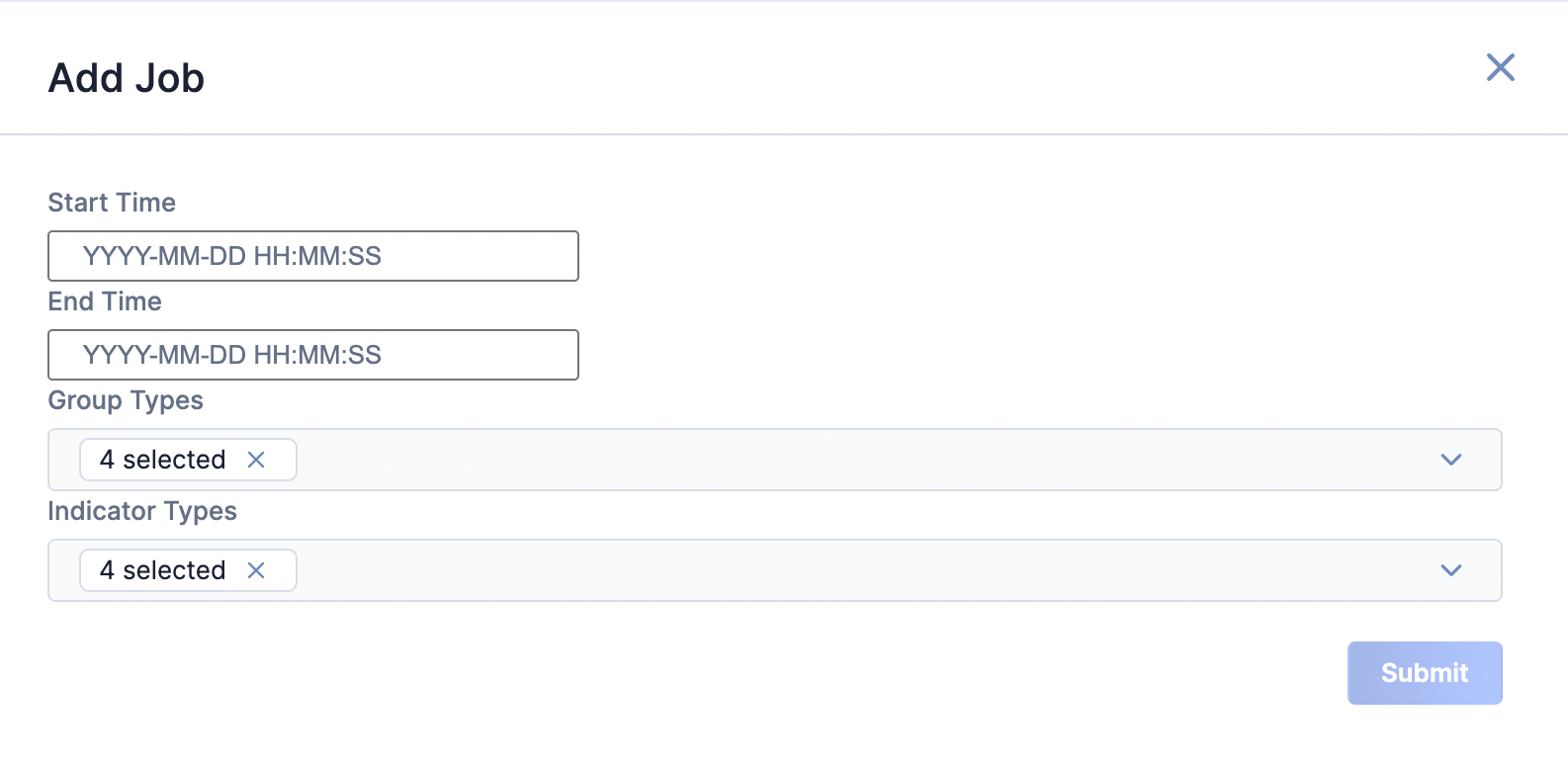
- Start Time: (Optional) Enter the time at which the Job should start.
- End Time: (Optional) Enter the time by which the Job should end.
- Group Types: (Optional) Select the CrowdStrike Falcon Intelligence Group types to include in the ad-hoc Job.
- Indicator Types: (Optional) Select the CrowdStrike Falcon Intelligence Indicator types to include in the ad-hoc Job.
- Click Submit to submit the request for the ad-hoc Job.
Tasks
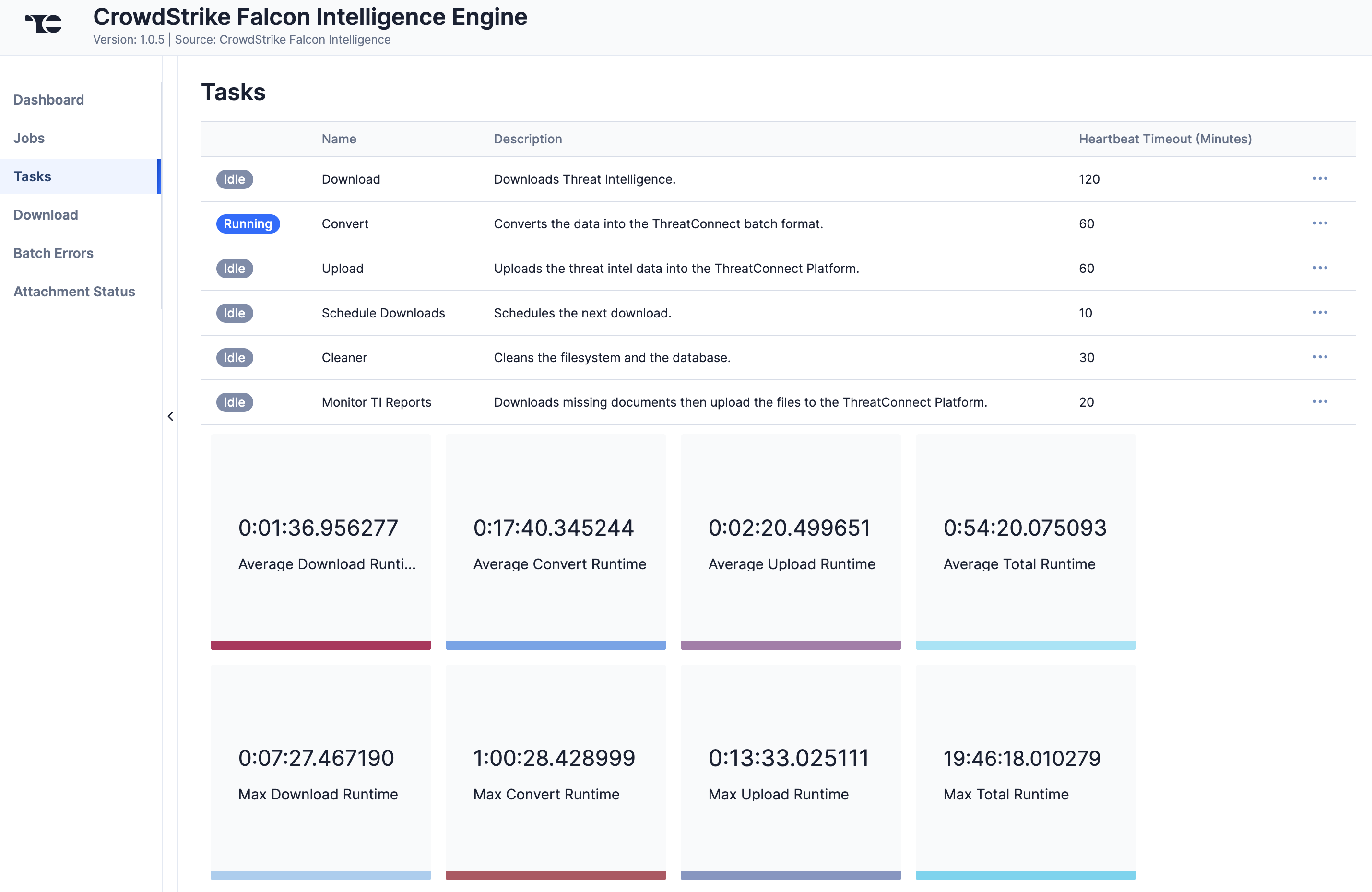
The Tasks screen (Figure 4) displays all Tasks that may be part of a Job, including each step of the download, convert, and upload processes, as well as Tasks for the CrowdStrike Falcon Intelligence Engine App, such as Monitor, Scheduler, and Cleaner. The current status (Idle, Paused, or Running), name, description, and heartbeat timeout length, in minutes, are displayed for each Task. The ⋯ menu in a Task’s row provides the following options, depending on the Task’s status:
- Run (idle and paused Tasks only)
- Pause (idle and running Tasks only)
- Resume (paused Tasks only)
- Kill (running Tasks only)
Under the table is a dashboard where you can view runtime analytics.
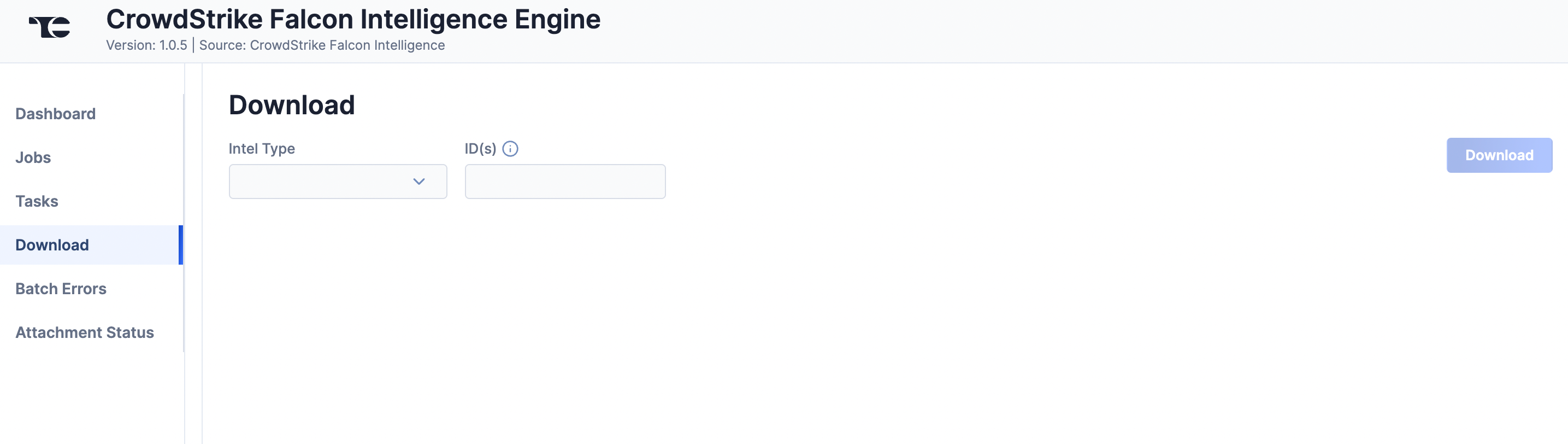
Download
The Download screen (Figure 5) lets you download JavaScript® Object Notation (JSON) data for CrowdStrike Falcon Intelligence objects and then upload the data into ThreatConnect.
Follow these steps to download JSON data for a CrowdStrike Falcon Intelligence object on the Download screen and then upload the data into ThreatConnect:
- Intel Type: Select a CrowdStrike Falcon Intelligence Group type (Actor, Malware, Report, or Vulnerability), or Indicator for all available CrowdStrike Falcon Intelligence Indicator types, to download.
- ID(s): Enter one or more CrowdStrike External IDs for the objects to download, separating each ID with a comma. The Actor, Malware, and Vulnerability types can also take a name as input.ImportantWhen entering multiple IDs or names, do not add a space before or after the comma.ImportantIf you enter a name that has a space in it (e.g.,
cobalt strike) and no results are returned, remove the space and try again (e.g.,cobaltstrike). Actor types usually allow, but do not require, spaces (e.g.,fancy bearandfancybearboth yield results), whereas Malware types usually do not allow spaces. - Click Download. The JSON data will be displayed in two columns: Results (raw JSON data) and Converted (JSON data in ThreatConnect batch format) (Figure 6).
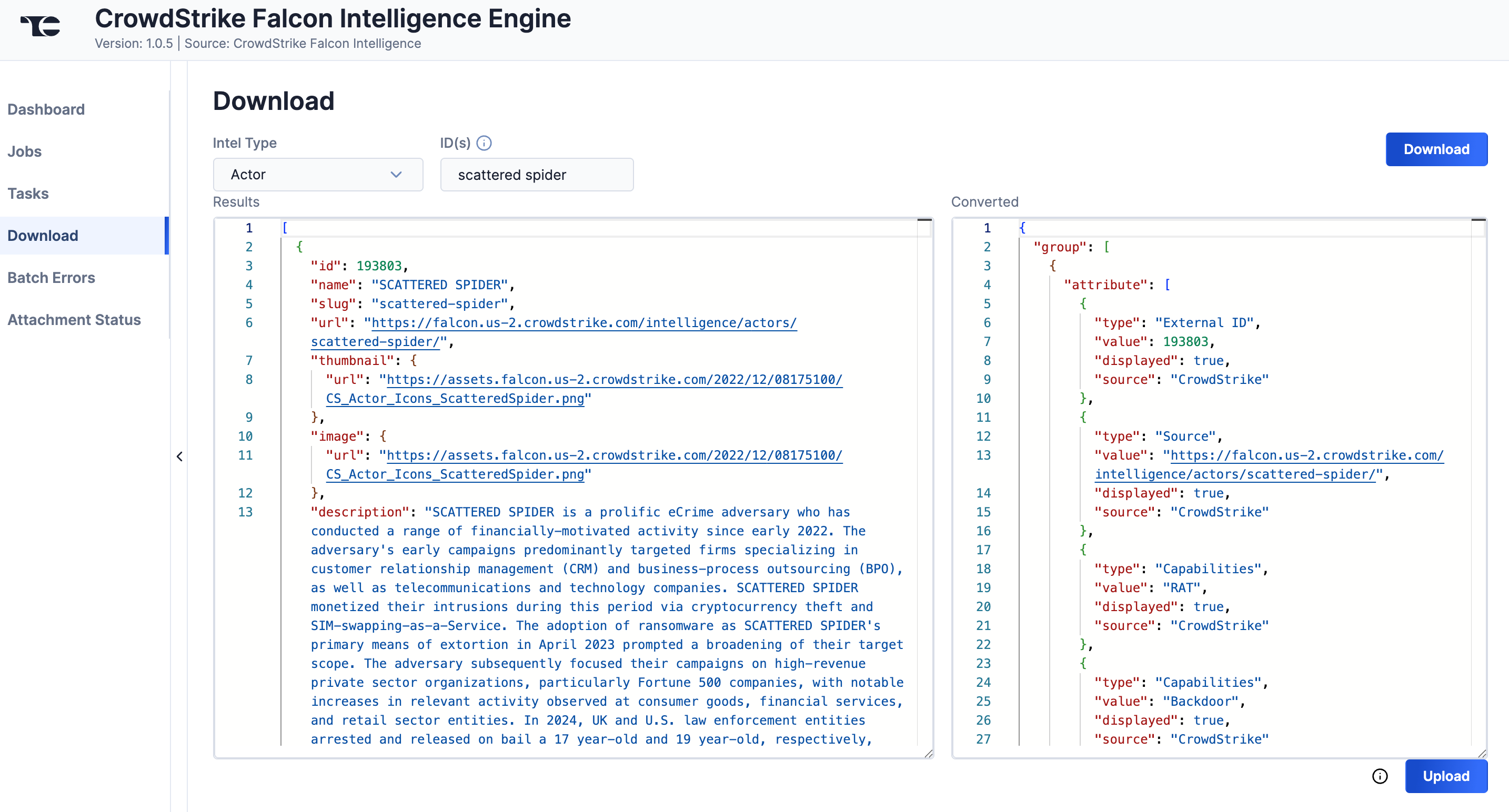
- Click Upload to submit the converted threat intelligence data via the ThreatConnect Batch API.
Batch Errors
The Batch Errors screen (Figure 7) displays an overview of the batch error types that have occurred for Job requests. You can enter keywords to filter by Job ID.
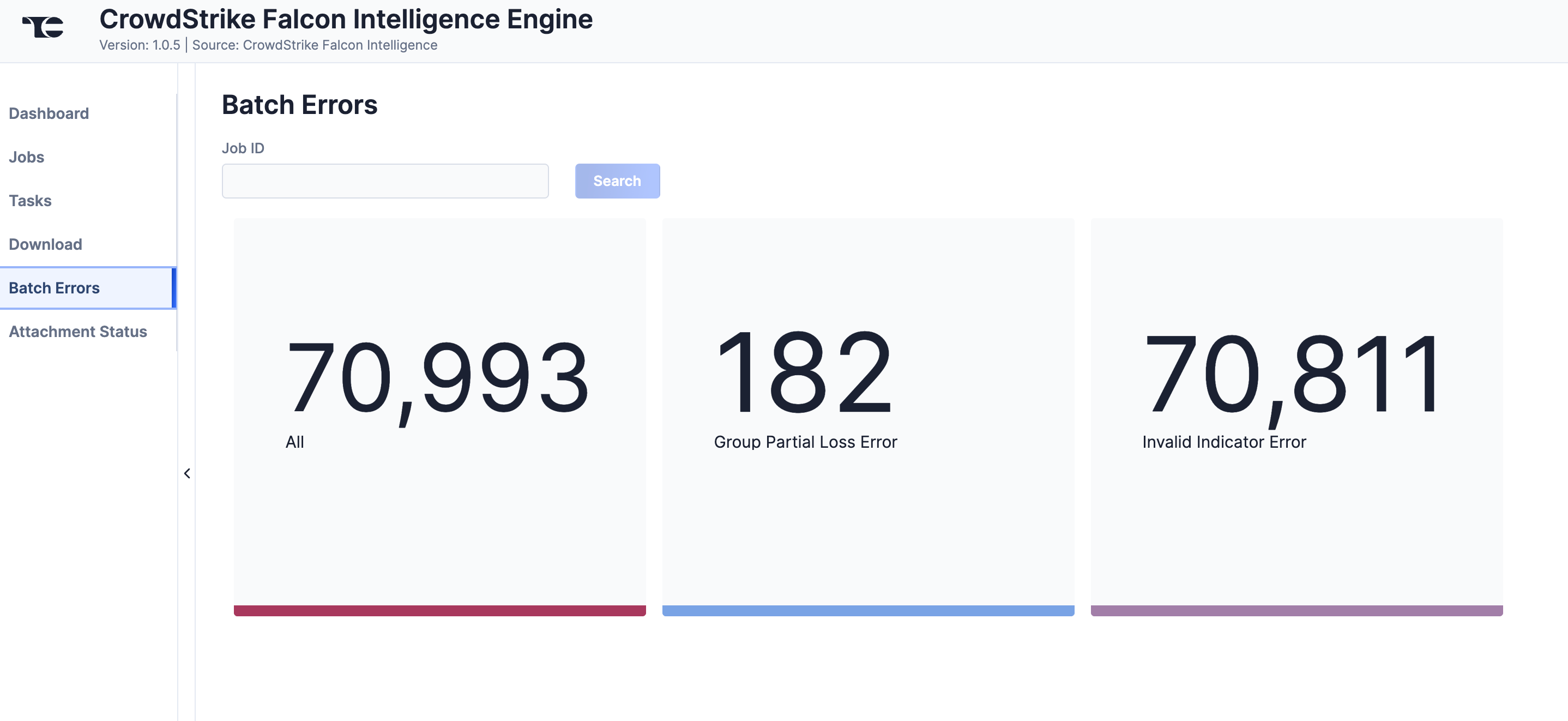
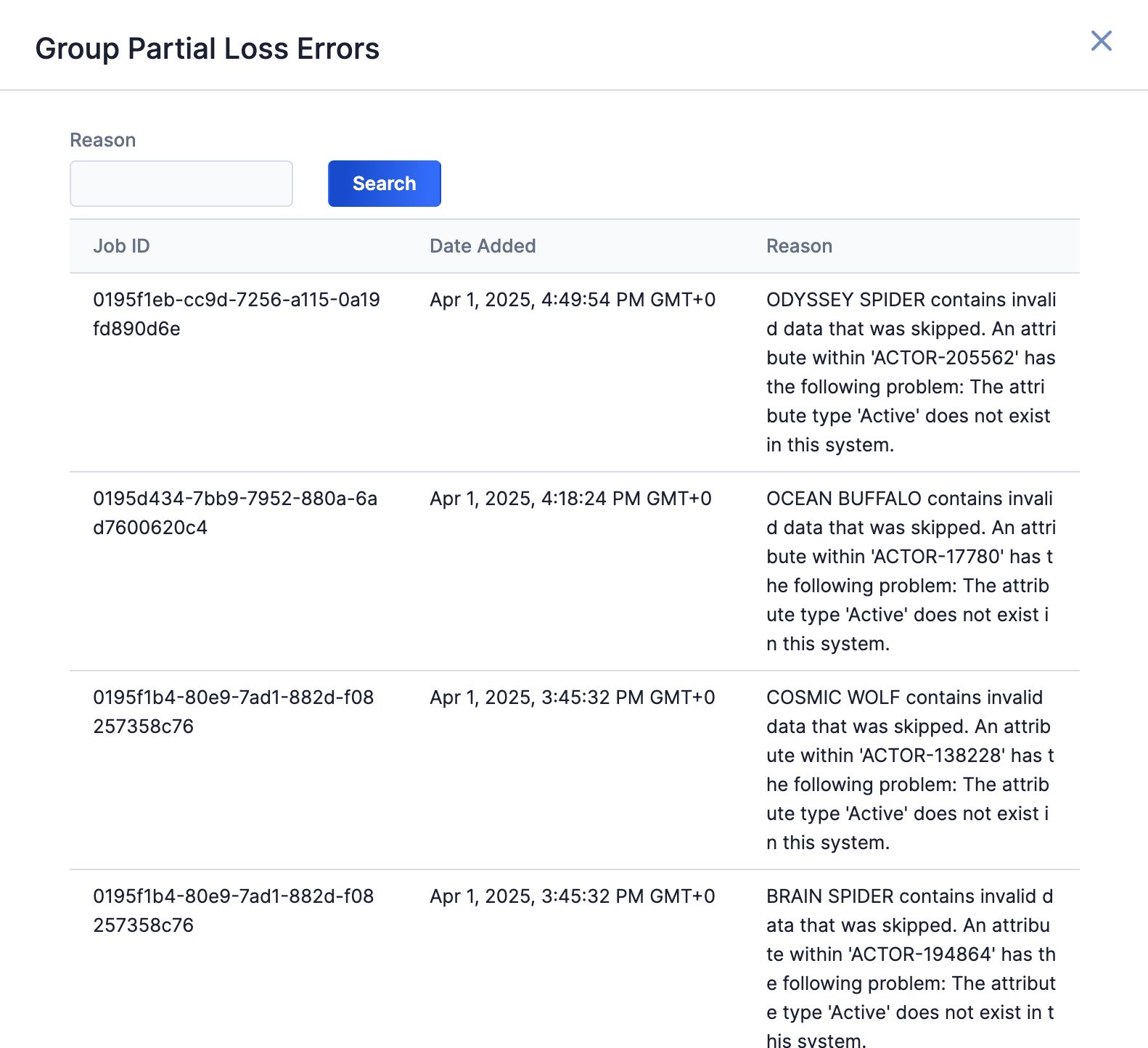
Click on an error type to open a drawer containing a table with details on all batch errors of that type (Figure 8). You can enter keywords to filter by reason for error.
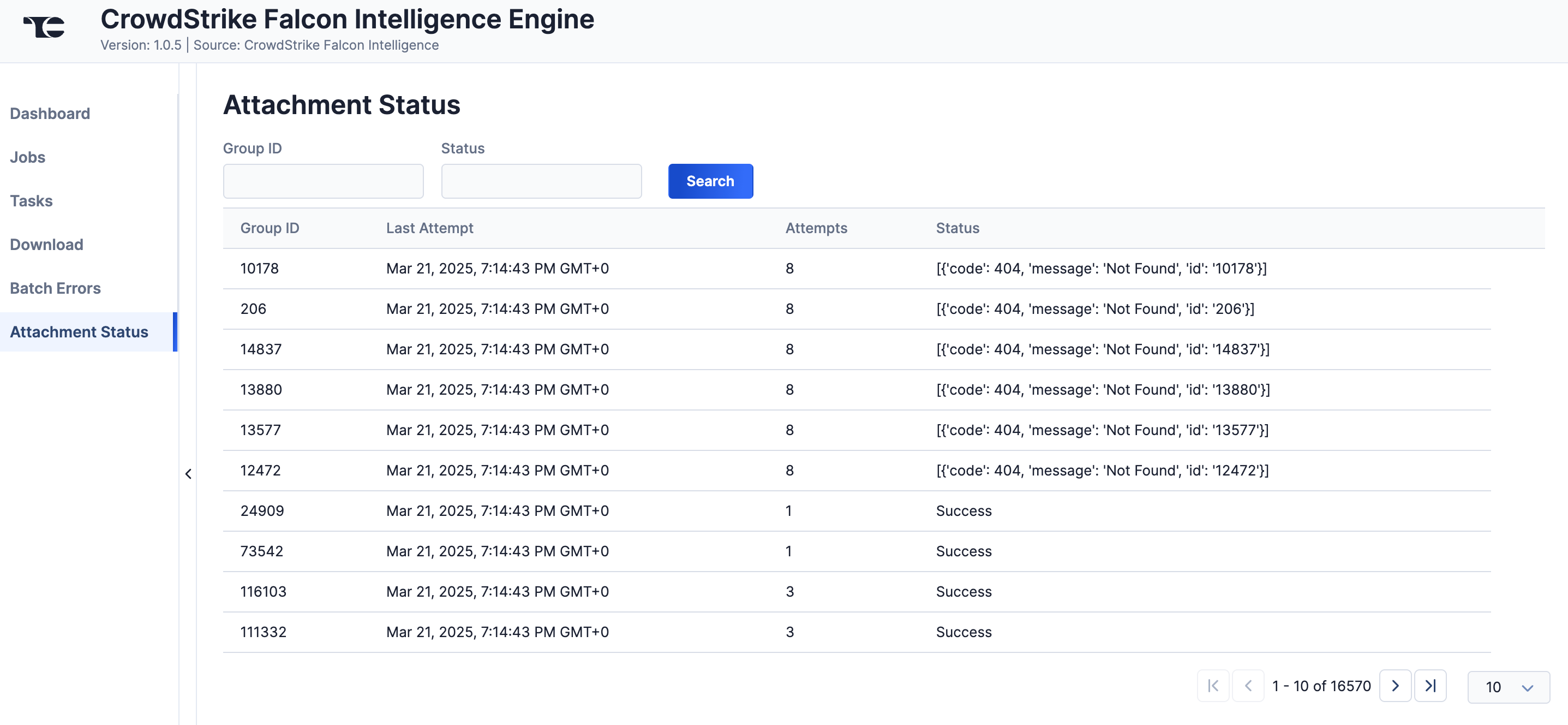
Attachment Status
The Attachment Status screen (Figure 9) displays a table with details on ThreatConnect's attempts to download Report attachments from CrowdStrike Falcon Intelligence. You can enter CrowdStrike External IDs for Groups to filter the table by Group ID, which can be useful if you do not see a CrowdStrike Falcon Intelligence attachment in ThreatConnect as expected, or by status.
Data Mappings
The data mappings in Table 2 through Table 10 illustrate how data are mapped from CrowdStrike Falcon Intelligence API endpoints to the ThreatConnect data model.
Reports
ThreatConnect object type: Report Group
| CrowdStrike API Field | ThreatConnect Field |
|---|---|
| resources.id | Attribute: "Report ID" |
| resources.name | Attribute: "Report Title" |
| resource.slug | N/A |
| resources.type | Attribute: "Report Type" |
| resources.sub_type | N/A |
| resources.url | Attribute: "Source" |
| resources.short_description | Attribute: "Description" |
| resources.created_date | Attribute: "External Date Created" |
| resources.last_modified_date | Attribute: "External Date Last Modified" |
| resources.thumbnail.url | N/A |
| resources.actor.id | N/A |
| resources.actor.name | (Actor Association) Note Actor Association refers to the association between the Report Group object and its related Actor object, which is imported into ThreatConnect as an Intrusion Set Group object. In ThreatConnect, you can see the Actor as an associated Intrusion Set Group object on the Associations tab of the Report Group's Details screen. |
| resources.actor.url | N/A |
| resources.tags | Tag |
| resources.target_industries | Attribute: "Target Industry Sector" |
| resources.target_countries | Attribute: "Target Country" |
| resources.motivations | Attribute: "Adversary Motivation Type" |
Actors
ThreatConnect object type: Intrusion Set Group
| CrowdStrike API Field | ThreatConnect Field |
|---|---|
| resources.name | Name/Summary |
| resources.id | Attribute: "External ID" |
| resources.url | Attribute: "Source" |
| resources.description | Attribute: "Description" |
| resources.created_date | Attribute: "External Date Created" |
| resources.last_modified_date | Attribute: "External Date Last Modified" |
| resources.first_activity_date | Attribute: "First Seen" |
| resources.last_activity_date | Attribute: "Last Seen" |
| resources.active | Attribute: "Active" |
| resources.known_as | Attribute: "Aliases" (/n Separated) |
| resources.motivations | Attribute: "Adversary Motivation Type" |
| resources.objectives | Attribute: "Goals" |
| resources.capabilities | Attribute: "Capabilities" |
| resources.origins | Attribute: "Origin Country" |
| resources.target_countries | Attribute: "Target Country" |
| resources.target_industries | Attribute: "Targeted Industry Sector" |
| resources.kill_chain | Attribute: "Reconnaissance" |
| Attribute: "Weaponization" | |
| Attribute: "Delivery" | |
| Attribute: "Actions and Objectives" | |
| resources.group | N/A |
Actors-MITRE
ThreatConnect object type: Intrusion Set Group
| CrowdStrike API Field | ThreatConnect Field |
|---|---|
| technique_id | ATT&CK® Tag |
Indicators
ThreatConnect object type: Indicator (all types)
| CrowdStrike API Field | ThreatConnect Field |
|---|---|
| resources.id | Attribute: "External ID" |
| resources.indicator | Name/Summary |
| resources.type | Indicator Type Note Table 6 shows how CrowdStrike Falcon Intelligence Indicator types are mapped to ThreatConnect Indicator types. |
| resources.last_updated | Attribute: "External Date Last Modified" |
| resources.published_date | Attribute: "External Date Created" |
| resources.malicious_confidence | Confidence Rating Note Table 7 shows how CrowdStrike Falcon Intelligence malicious confidence values are mapped to ThreatConnect Threat Rating and Confidence Rating. |
| resources._marker | N/A |
| resources.reports | (Report Association) Note Report Association refers to the association between the Indicator and its related Report Group object. In ThreatConnect, you can see the Report Group object on the Associations tab of the Indicator’s Details screen. |
| resources.actors | (Actor Association) Note Actor Association refers to the association between the Indicator and its related Actor object, which is imported into ThreatConnect as an Intrusion Set Group object. In ThreatConnect, you can see the Actor as an associated Intrusion Set Group object on the Associations tab of the Indicator’s Details screen. |
| resources.malware_families | N/A |
| resources.kill_chains | Attribute: "Phase of Intrusion" |
| resources.labels | Tag (If resources.labels.name starts with "MitreATTCK," an ATT&CK Tag will be applied to the Indicator.) |
| resources.domain_types | Tag |
| resources.ip_address_types | Tag |
| resources.relations | Attribute: "File Occurrence" |
| resources.targets | Attribute: "Targeted Industry Sector" |
| resources.threat_types | Tag |
| resources.vulnerabilities | Tag |
| CrowdStrike Indicator Type | ThreatConnect Indicator Type |
|---|---|
| Domain | Host |
| Email Address | Email Address |
| Email Subject | Email Subject |
| IP Address | Address |
| IP Address Block | CIDR |
| Mutex Name | Mutex |
| Registry | Registry Key |
| URL | URL |
| User Agent | User Agent |
| Hash MD5 | File |
| Hash SHA1 | |
| Hash SHA256 |
| CrowdStrike malicious_confidence | ThreatConnect Threat Rating and Confidence Rating |
|---|---|
| Unverified | 1 skull and 10 Confidence Rating |
| Low | 2 skulls and 40 Confidence Rating |
| Medium | 4 skulls and 75 Confidence Rating |
| High | 5 skulls and 95 Confidence Rating |
Malware Families
ThreatConnect object type: Malware Group
| CrowdStrike API Field | ThreatConnect Field |
|---|---|
| malware_families |
|
| all_systems[] | Attribute: "Affected Systems" |
| associated_actors[].name | Tag: "Intrusion Set: " |
| capabilities[] | Attribute: "Capabilities" |
| community_identifiers[] | Attribute: "Identifier" |
| created_timestamp |
|
| description | Attribute: "Description" |
| developed_by[].name |
|
| kill_chain[] | Attribute: "Phase of Intrusion" |
| last_updated |
|
| mitre[].technique_id | Tag |
| motivation[] | Attribute: "Motivation" |
| name |
|
| next_stages[].name | Tag: "Malware: " |
| sold_by[].name |
|
| status | status |
| successor_of[].name |
|
| target_industries[].name | Attribute: "Targeted Industry Sector" |
| targeting_profile[] | Attribute: "Targeted Information" |
| targets_systems[].customer_target | Attribute: "Targeted System" |
| threat_properties[] | Attribute: "Malware Threat Type" |
| used_by[].name |
|
| variant_of[].name |
|
| variants[].name |
|
Malware Families-MITRE
ThreatConnect object type: Malware Group
| CrowdStrike API Field | ThreatConnect Field |
|---|---|
| resources | ATT&CK Tag |
Vulnerabilities
ThreatConnect object type: Vulnerability Group
| CrowdStrike API Field | ThreatConnect Field |
|---|---|
| resources.vulnerabilities | Tag |
| affected_products[].product | Tag: "CPE Product: " |
| affected_products[].vendor | Tag: "CPE Vendor: " |
| affected_products[] | Attribute: "Vulnerable Product" |
| cve |
|
| cvss_v2_base.access_complexity | Attribute: "CVSS v2 Access Complexity" |
| cvss_v2_base.access_vector | Attribute: "CVSS v2 Access Vector" |
| cvss_v2_base.authentication | Attribute: "CVSS v2 Authentication" |
| cvss_v2_base.availability_impact | Attribute: "CVSS v2 Availability Impact" |
| cvss_v2_base.confidentiality_impact | Attribute: "CVSS v2 Confidentiality Impact" |
| cvss_v2_base.integrity_impact | Attribute: "CVSS v2 Integrity Impact" |
| cvss_v2_base.score | Attribute: "CVSS Score v2" |
| cvss_v2_base.severity | Attribute: "CVSS v2 Base Severity" |
| cvss_v3_base.attack_complexity | Attribute: "CVSS v3 Attack Complexity" |
| cvss_v3_base.attack_vector | Attribute: "CVSS v3 Attack Vector" |
| cvss_v3_base.availability_impact | Attribute: "CVSS v3 Availability Impact" |
| cvss_v3_base.confidentiality_impact | Attribute: "CVSS v3 Confidentiality Impact" |
| cvss_v3_base.integrity_impact | Attribute: "CVSS v3 Integrity Impact" |
| cvss_v3_base.privileges_required | Attribute: "CVSS v3 Privileges Required" |
| cvss_v3_base.scope | Attribute: "CVSS v3 Scope" |
| cvss_v3_base.score | Attribute: "CVSS Score v3" |
| cvss_v3_base.severity | Attribute: "CVSS v3 Base Severity" |
| cvss_v3_base.user_interaction | Attribute: "CVSS v3 User Interaction" |
| exploit_status | Attribute: "Exploitation State" |
| publish_date | externalDateAdded |
| Severity | Attribute: "Threat Level" |
| updated_timestamp | externalLastModified |
| {description: description, cvss_v2_score: cvss_v2_base.score, cvss_v3_score: cvss_v3_base.score} | Attribute: "Description" |
Troubleshooting
The CrowdStrike Falcon Intelligence Engine App is a Python®-based App that requires certificate verification. Organizations using SSL inspection solutions will need to import their internal CA certificate to the OS-trusted root certificate store in order for the connection to CrowdStrike to be initiated.
Frequently Asked Questions (FAQ)
Why are some ATT&CK techniques represented as standard Tags instead of ATT&CK Tags in ThreatConnect?
ThreatConnect converts Tags that match an active ATT&CK technique name or ID into ATT&CK Tags automatically. When ThreatConnect ingests deprecated or inactive ATT&CK techniques from CrowdStrike, they are mapped to standard Tags to keep the data consistent between ThreatConnect and CrowdStrike. Note that standard Tags representing deprecated or inactive ATT&CK techniques will be applied only to Indicators in ThreatConnect, as these ATT&CK techniques are dropped for Actors and Malware.
Why are there no ATT&CK Tags applied to Reports?
ATT&CK Tag support for Reports is planned for a future update of the CrowdStrike Falcon Intelligence Engine App. If you need this update sooner, please contact your Customer Success Manager (CSM) or submit feedback via Productboard.
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
CrowdStrike® and CrowdStrike Falcon® are registered trademarks of CrowdStrike, Inc.
JavaScript® is a registered trademark of Oracle Corporation.
Python® is a registered trademark of the Python Software Foundation.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.
30039-010 EN Rev. A


