- 08 Feb 2024
- 5 Minutes to read
-
Print
-
DarkLight
-
PDF
Artifacts Card
- Updated on 08 Feb 2024
- 5 Minutes to read
-
Print
-
DarkLight
-
PDF
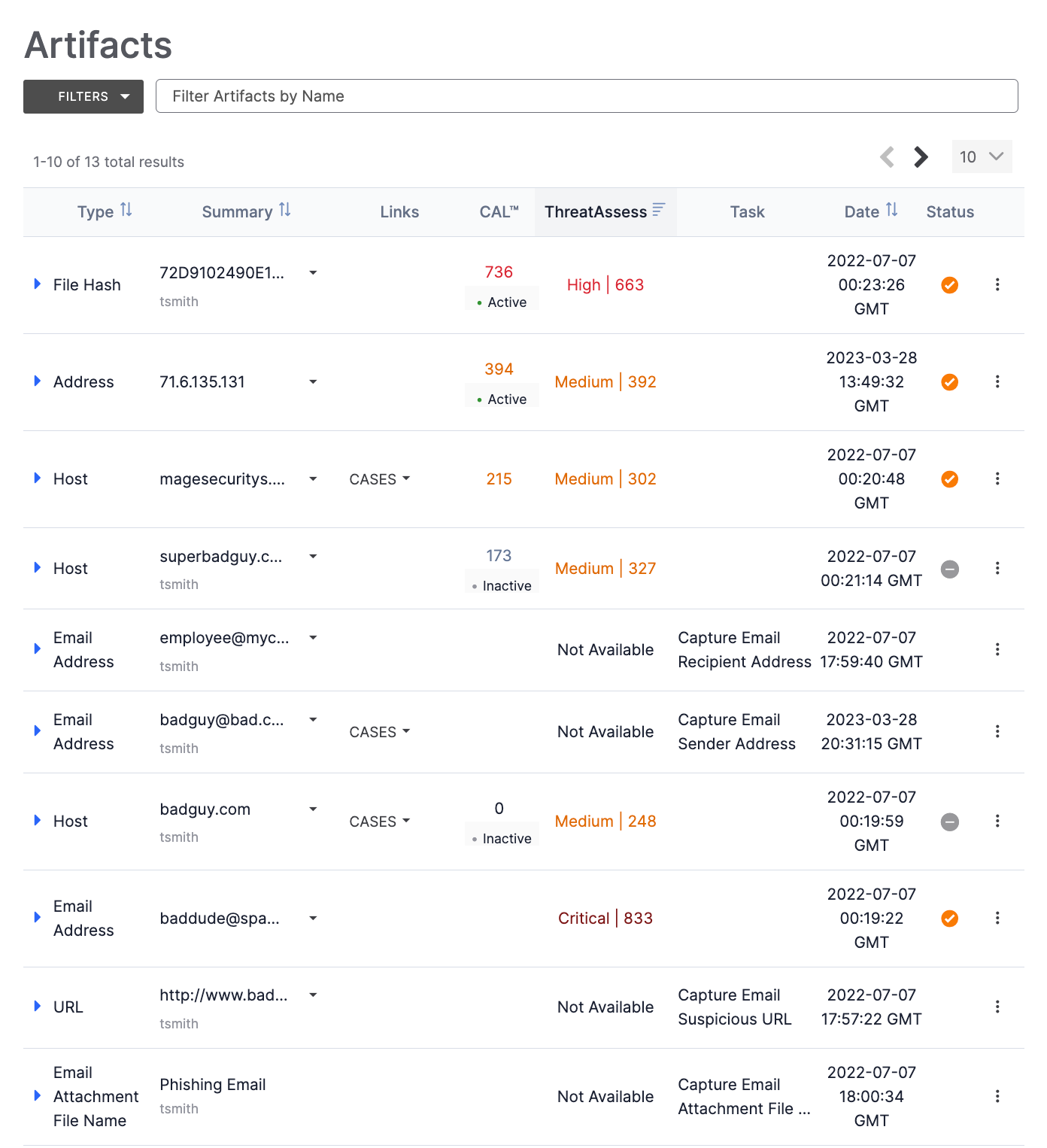
Figure 1 shows an example of a Workflow Case’s Artifacts card, which is located below the Potential Associations card on the right side of the screen displaying the Case. To collapse or expand the Artifacts card, click anywhere at the top of the card.
Artifacts Table
The Artifacts card displays all Artifacts added to the Case in a paginated table. To view more details about an Artifact, click the icon to the left of its value in the Type column.
icon to the left of its value in the Type column.
Type
The Type column displays the Artifact’s type. Available Artifact types include all ThreatConnect Indicator types and other data types determined by ThreatConnect and your System Administrator. To sort Artifacts by type, click the Type column header.
Summary
The Summary column displays the data that the Artifact contains (or, for Artifacts that are files, the name of the file), as well as the source (i.e., the name of the user) that added the Artifact to the Case. To sort Artifacts in alphanumeric order by summary, click the Summary column header.
If an Artifact is a ThreatConnect Indicator type, an icon will be displayed to the right of its summary. If a matching Indicator exists in one of your ThreatConnect owners (i.e., Organization, Communities, and Sources), a dropdown with all of those owners will be displayed when you click this icon. Select an owner to display the Details drawer for the copy of the Indicator in that owner.
icon will be displayed to the right of its summary. If a matching Indicator exists in one of your ThreatConnect owners (i.e., Organization, Communities, and Sources), a dropdown with all of those owners will be displayed when you click this icon. Select an owner to display the Details drawer for the copy of the Indicator in that owner.
For Indicators that do not exist in one of your owners, a dropdown containing a Learn more about it will be displayed when you click the icon. Select this option to display a modified Details drawer for the Indicator (Figure 2).
icon. Select this option to display a modified Details drawer for the Indicator (Figure 2).
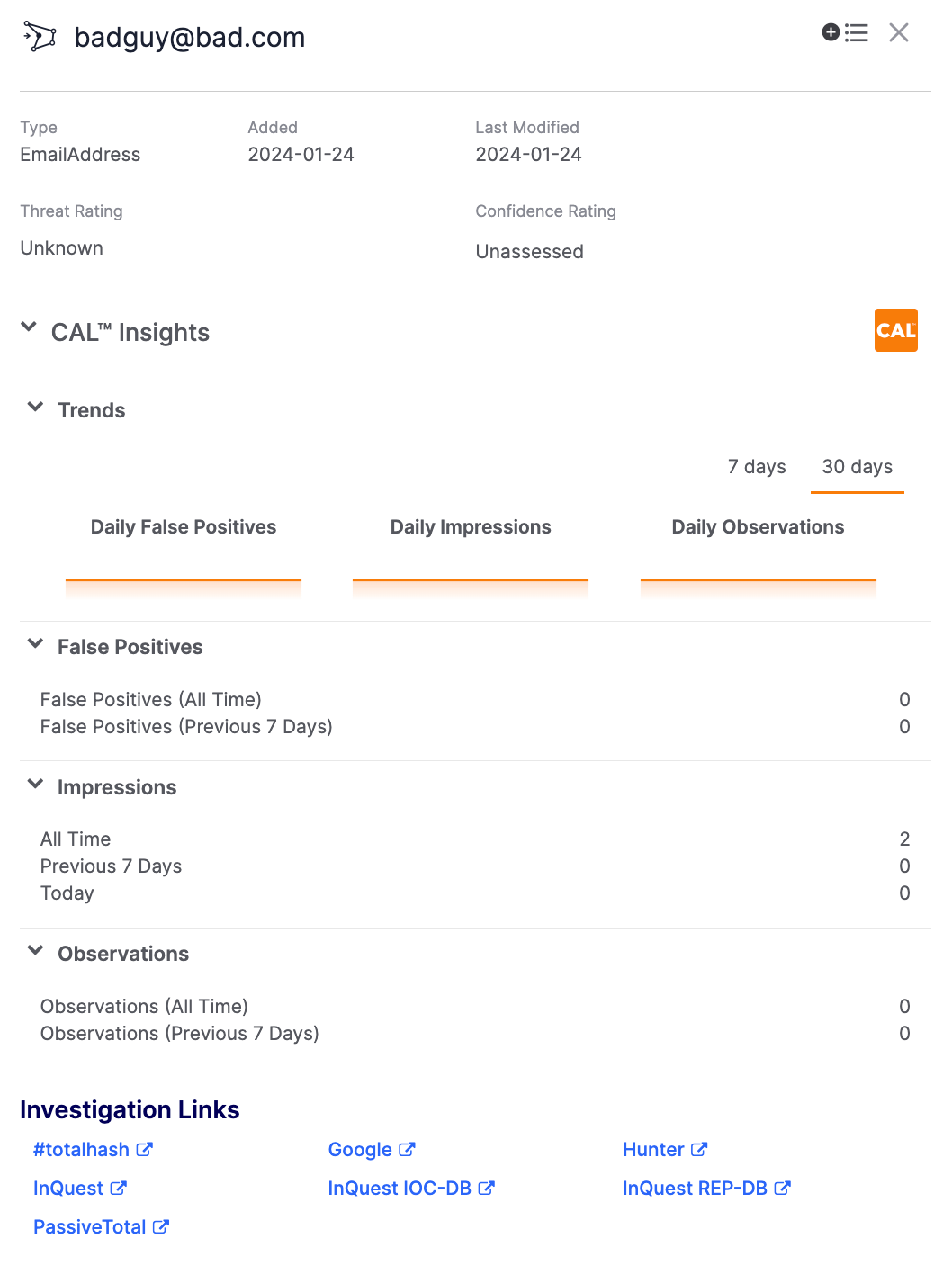
This drawer can be used to view information that CAL™ has on the Indicator, if any, or to follow the investigation links to further explore the Indicator. To add the Indicator to one of your owners, click Add![]() at the upper-right corner of the drawer and select the desired owner.
at the upper-right corner of the drawer and select the desired owner.
You can also view a modified Details screen for the Indicator by clicking View full details at the upper-right corner of the Details drawer (Figure 3).
at the upper-right corner of the Details drawer (Figure 3).
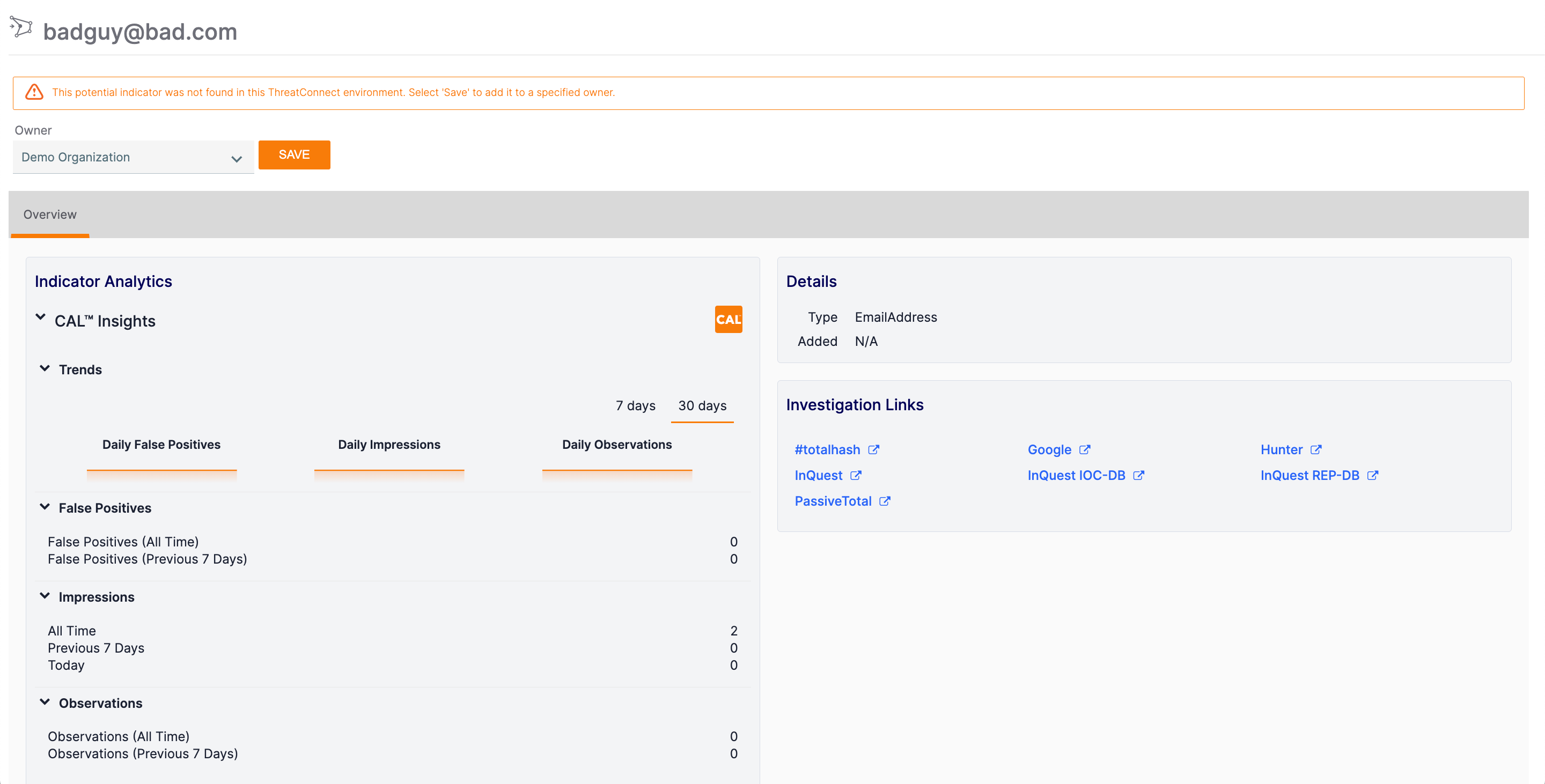
Use the Indicator Analytics section to view information CAL has on the Indicator, or follow the links in the Investigation Links section to explore the Indicator further. To add the Indicator to one of your owners, select the desired owner from the Owner dropdown at the top left of the screen and then click the SAVE button.
Links
If an Artifact belongs to multiple Cases in your Organization, a CASES dropdown will be displayed in the Links column. Click this dropdown to select another Case in which the Artifact exists to open the Case in a new browser tab.
CAL
The CAL column displays the CAL reputation score and status for all Artifacts that are ThreatConnect Indicator types. The status (• Active for the 71.6.135.131 Address Artifact in Figure 1) indicates CAL’s assessment of whether the corresponding Indicator is an active Indicator of Compromise (IOC) at the current time. Depending on this assessment, one of the following statuses may be displayed below the Indicator’s CAL reputation score:
- • Active: CAL has identified the Indicator as an active IOC at the current time.
- • Inactive: CAL has identified the Indicator as an inactive IOC at the current time.
If CAL did not return data identifying whether the corresponding Indicator is active or inactive at the current time, no status will be displayed below the Artifact's CAL reputation score.
ThreatAssess
The ThreatAssess column displays the ThreatAssess score and assessment for all Artifacts that are ThreatConnect Indicator types. By default, Artifacts are sorted from highest to lowest ThreatAssess score, followed by items without a ThreatAssess score (i.e., Artifacts that are not ThreatConnect Indicator types). To reverse this sort order, click the ThreatAssess column header.
Task
The Task column displays the name of a Task for which the Artifact was collected. If an Artifact was not collected for a Task, then no value will be displayed in the column.
Date
The Date column displays the date and time when the Artifact was added to the Case. To sort Artifacts by date, click the Date column header.
Status
The Status column displays the Indicator Status for all Artifacts that are ThreatConnect Indicator types:
- Active
 : This icon indicates that the Indicator corresponding to the Artifact has an active status. It is displayed for Artifacts corresponding to any Indicator, regardless of whether the Indicator exists in a ThreatConnect owner.
: This icon indicates that the Indicator corresponding to the Artifact has an active status. It is displayed for Artifacts corresponding to any Indicator, regardless of whether the Indicator exists in a ThreatConnect owner. - Inactive
 : This icon indicates that the Indicator corresponding to the Artifact has an inactive status. It is displayed only for Artifacts corresponding to Indicators that exist in a ThreatConnect owner.
: This icon indicates that the Indicator corresponding to the Artifact has an inactive status. It is displayed only for Artifacts corresponding to Indicators that exist in a ThreatConnect owner.
Filtering Artifacts
FILTERS Selector
The FILTERS selector provides the following options for filtering Artifacts on the Artifacts card:
- Type: Use this option to filter Artifacts by type.
- Status: Use this option to filter Artifacts that are Indicator types by their corresponding Indicator Status (Active or Inactive). Selecting options from this menu is a way to exclude Artifacts without an Indicator Status.
- Analytics Score: Use this option to filter Artifacts that are Indicator types by their corresponding ThreatAssess assessment levels. Selecting options from this menu is a way to exclude Artifacts without a ThreatAssess score.
- Source: Use this option to filter Artifacts by their source (i.e., the username of the user that entered them).
After configuring the desired filters, click the APPLY button on the FILTERS selector. To reset the filters, click the CLEAR button on the FILTERS selector.
When filters are applied, an orange circle is displayed at the upper-left corner of the FILTERS selector. This element helps alert you to the fact that you might be viewing an “incomplete” set of data.
is displayed at the upper-left corner of the FILTERS selector. This element helps alert you to the fact that you might be viewing an “incomplete” set of data.
Filtering Artifacts by Summary
To filter Artifacts by summary, use the search bar at the top of the Artifacts card.
ThreatConnect® is a registered trademark, and CAL™ is a trademark, of ThreatConnect, Inc.
20123-02 v.02.D


