- 12 Aug 2023
- 9 Minutes to read
-
Print
-
DarkLight
-
PDF
Zscaler Internet Access Content Pack Use Cases
- Updated on 12 Aug 2023
- 9 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The Zscaler Internet Access™ Content Pack in ThreatConnect® supports the following use cases:
- Using the ZScaler Content Pack - Add URL or Host to ZIA Security Exceptions Playbook to add a URL or Host Indicator to the Security Exceptions list in the Advanced Threat Protection section of Zscaler Internet Access (ZIA).
- Using the ZScaler Content Pack - Remove URL or Host from ZIA Security Exceptions Playbook to remove a URL or Host Indicator from the Security Exceptions list in the Advanced Threat Protection section of ZIA.
- Using the Zscaler Content Pack - Add URL or Host to ZIA Blocked Malicious URLs Playbook to add a URL or Host Indicator to the Blocked Malicious URLs list in the Advanced Threat Protection section of ZIA.
- Using the Zscaler Content Pack - Remove URL or Host from ZIA Blocked Malicious URLs Playbook to remove a URL or Host Indicator from the Blocked Malicious URLs list in the Advanced Threat Protection section of ZIA.
Adding Indicators to ZIA Security Exceptions
The ZScaler Content Pack - Add URL or Host to ZIA Security Exceptions Playbook has a UserAction Trigger, which allows you to execute the Playbook from the Playbooks card on the Overview tab of a Host or URL Indicator’s Details screen or while viewing the Indicator in Threat Graph.
Details Screen
- Navigate to the Details screen for the Host or URL Indicator that you want to add to the ZIA Security Exceptions list.
- On the Playbooks card, click Run playbook
 for the Zscaler - Add URL or Host to ZIA Security Exceptions Playbook (Figure 1).
for the Zscaler - Add URL or Host to ZIA Security Exceptions Playbook (Figure 1).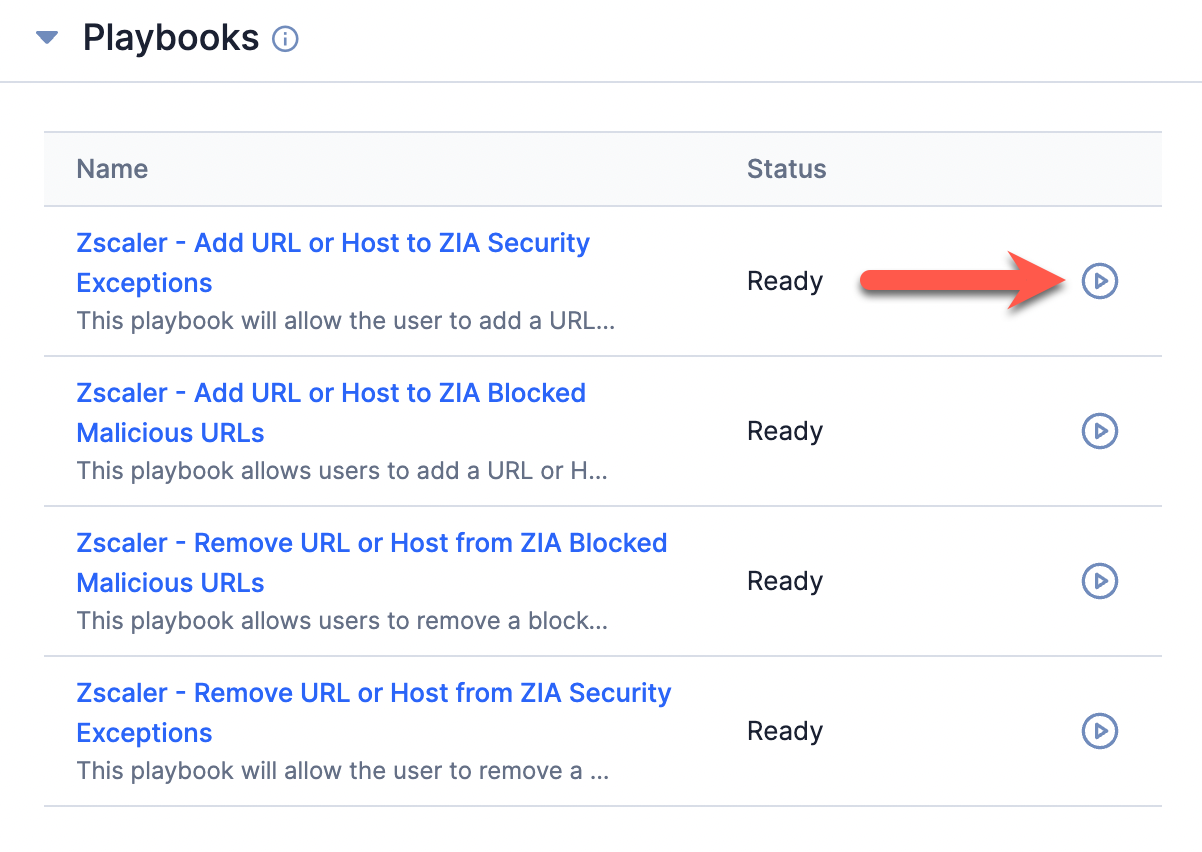
- A message stating “Starting playbook…” will be displayed at the lower-left corner of the screen. When the Playbook’s execution is complete, the Status of the Playbook will change to Complete, and a tooltip stating that the Indicator was added to the ZIA Security Exceptions list will be displayed (Figure 2).
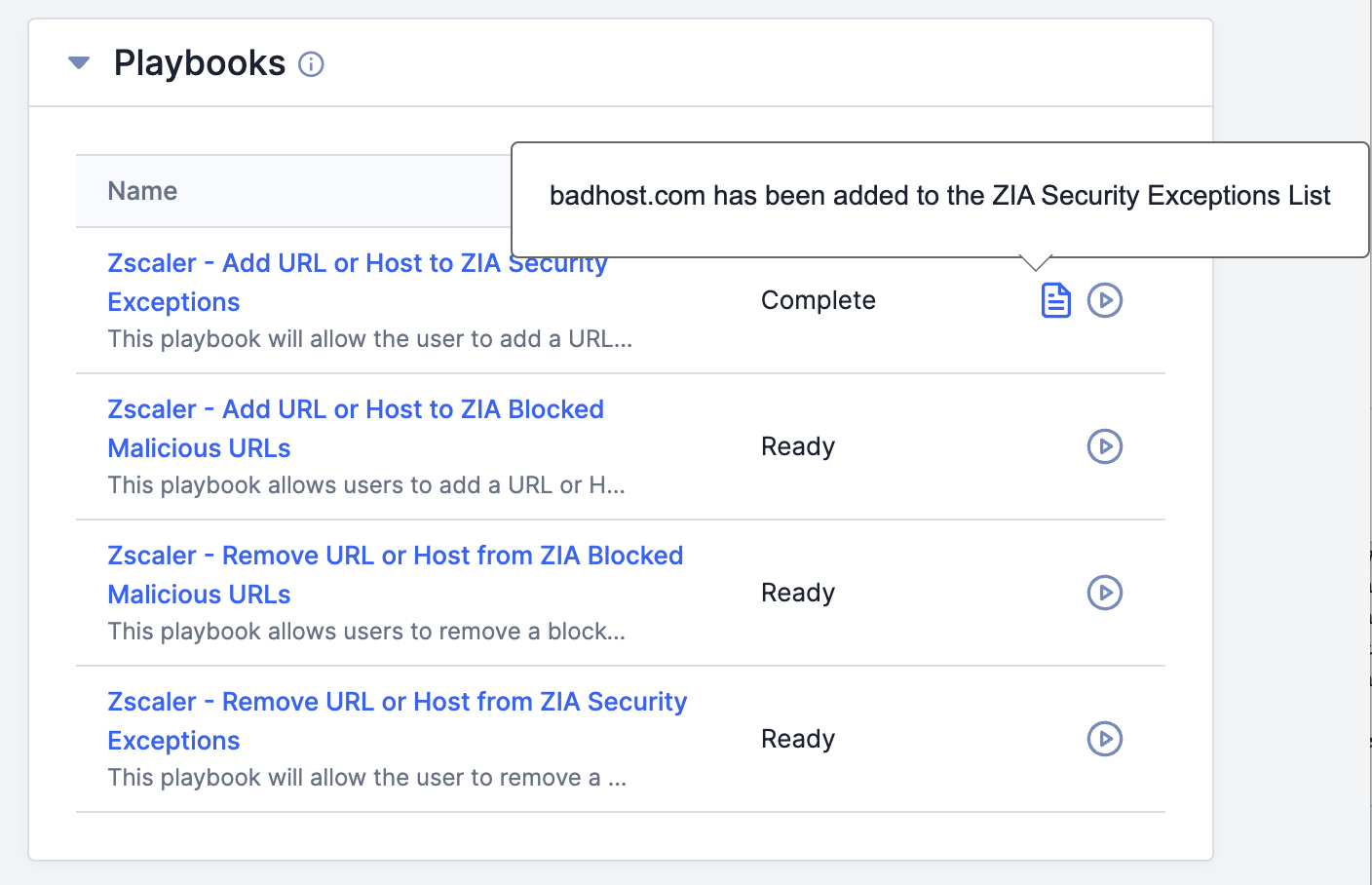
Threat Graph
- Navigate to Threat Graph for the Host or URL Indicator that you want to add to the ZIA Security Exceptions list.
- Select Run Playbook… from the contextual menu for the node representing the Indicator (Figure 3).
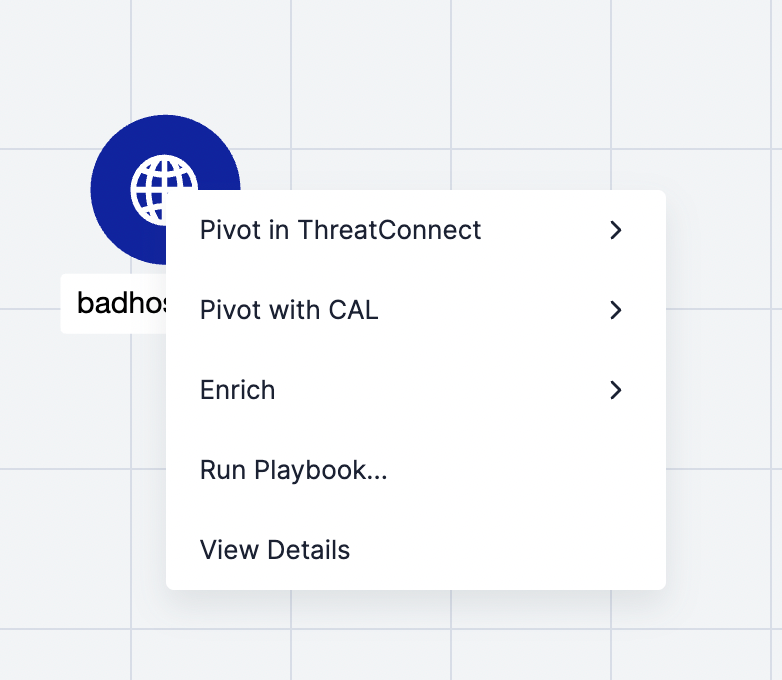
- The Select Playbook window will be displayed, showing all active Playbooks containing a UserAction Trigger configured for the Indicator’s type (Figure 4).
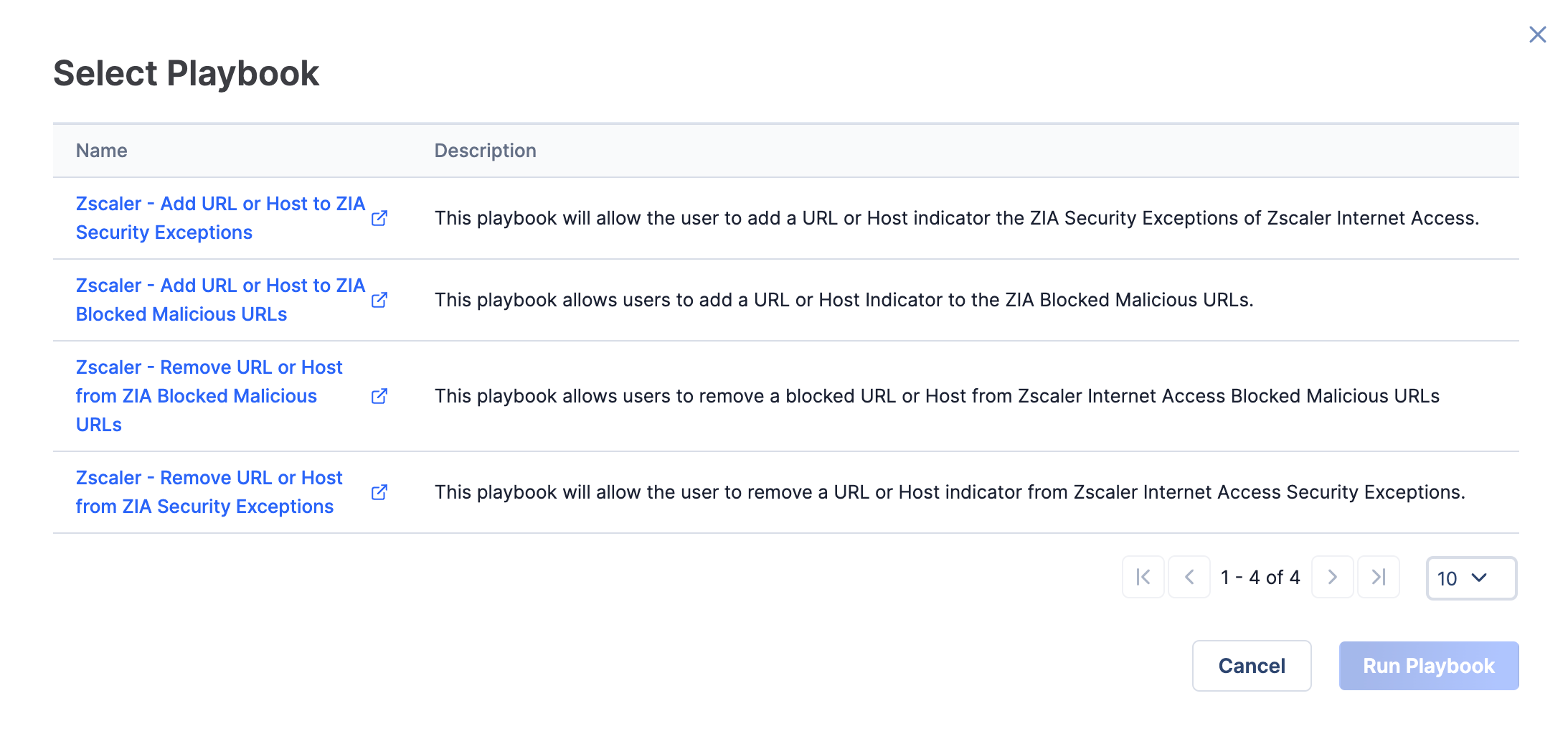
- Select the row containing the Zscaler - Add URL or Host to ZIA Security Exceptions Playbook, and click the Run Playbook button.NoteClicking on a Playbook’s name will open the Playbook in the Playbook Designer in a new browser tab. Clicking on a Playbook’s row will select the Playbook for execution.NoteNo confirmation message that the Playbook was run will be displayed. See the “Verifying Results” section for instructions about how to verify that the operation occurred.
Removing Indicators from ZIA Security Exceptions
The ZScaler Content Pack - Remove URL or Host from ZIA Security Exceptions Playbook has a UserAction Trigger, which allows you to execute the Playbook from the Playbooks card on the Overview tab of a Host or URL Indicator’s Details screen or while viewing the Indicator in Threat Graph.
Details Screen
- Navigate to the Details screen for the Host or URL Indicator that you want to remove from the ZIA Security Exceptions list.
- On the Playbooks card, click Run playbook
 for the Zscaler - Remove URL or Host from ZIA Security Exceptions Playbook (Figure 5).
for the Zscaler - Remove URL or Host from ZIA Security Exceptions Playbook (Figure 5).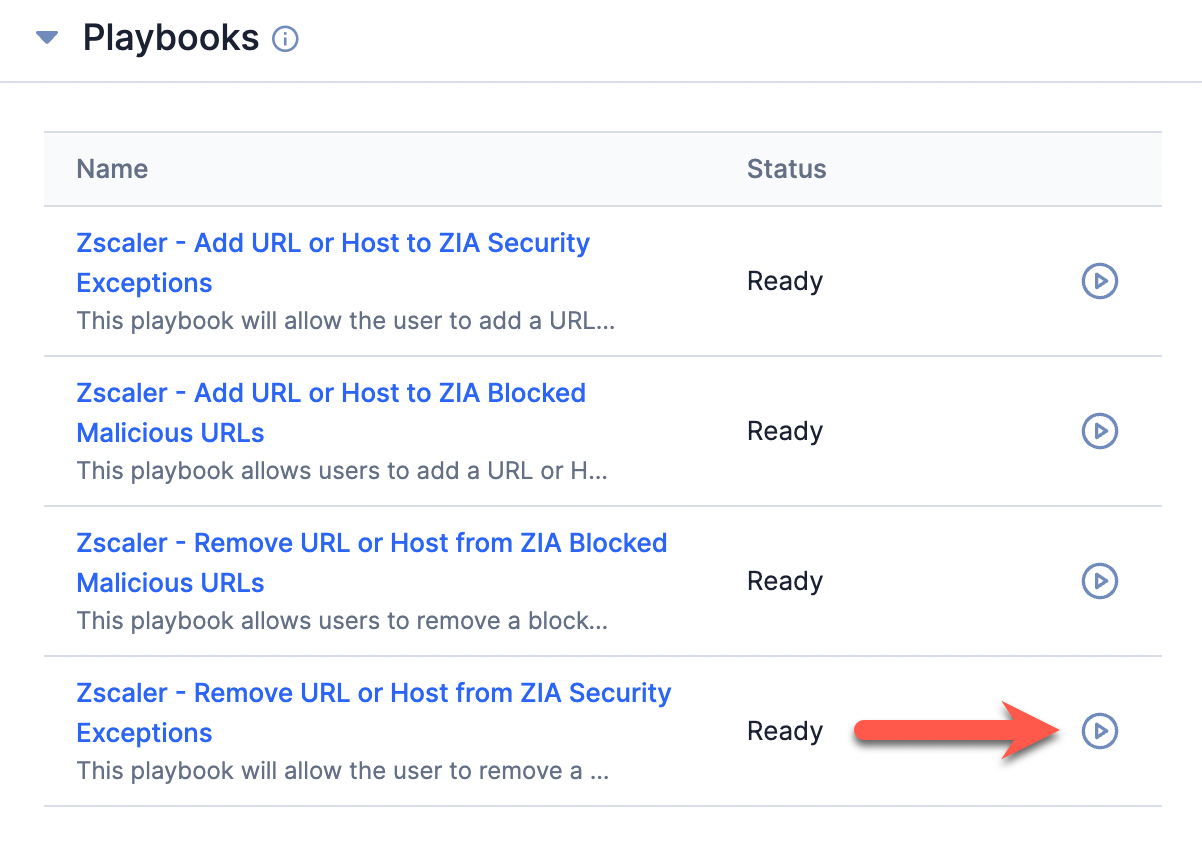
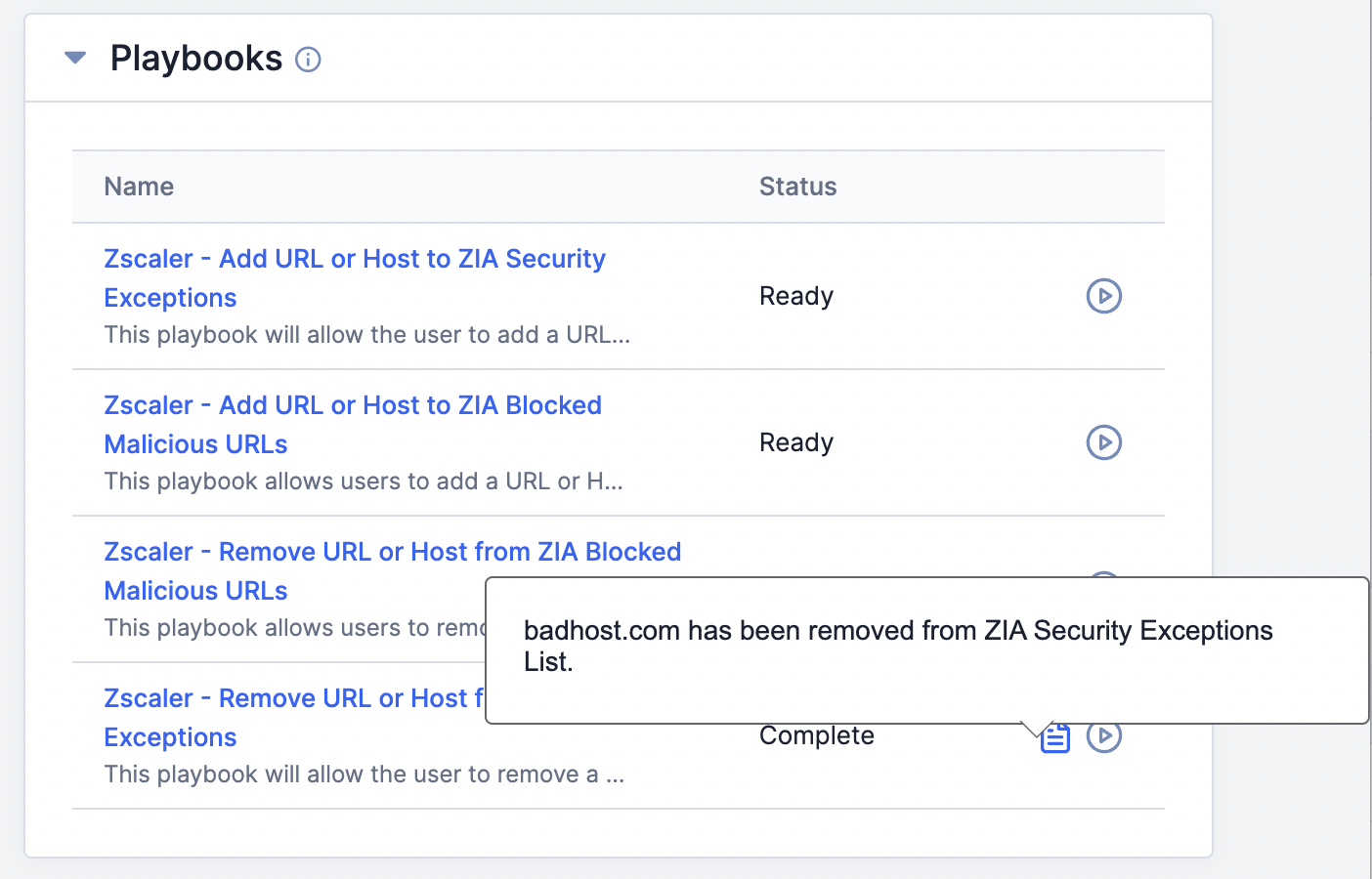
- A message stating “Starting playbook…” will be displayed at the lower-left corner of the screen. When the Playbook’s execution is complete, the Status of the Playbook will change to Complete, and a tooltip stating that the Indicator was removed from the ZIA Security Exceptions list will be displayed (Figure 6).
Threat Graph
- Navigate to Threat Graph for the Host or URL Indicator that you want to remove from the ZIA Security Exceptions list.
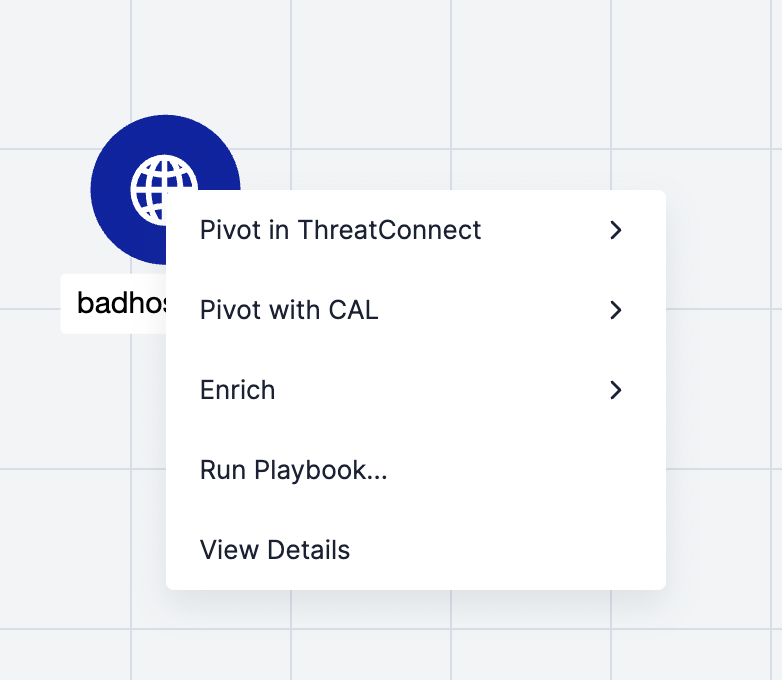
- Select Run Playbook… from the contextual menu for the node representing the Indicator (Figure 7).
- The Select Playbook window will be displayed, showing all active Playbooks containing a UserAction Trigger configured for the Indicator’s type (Figure 8).
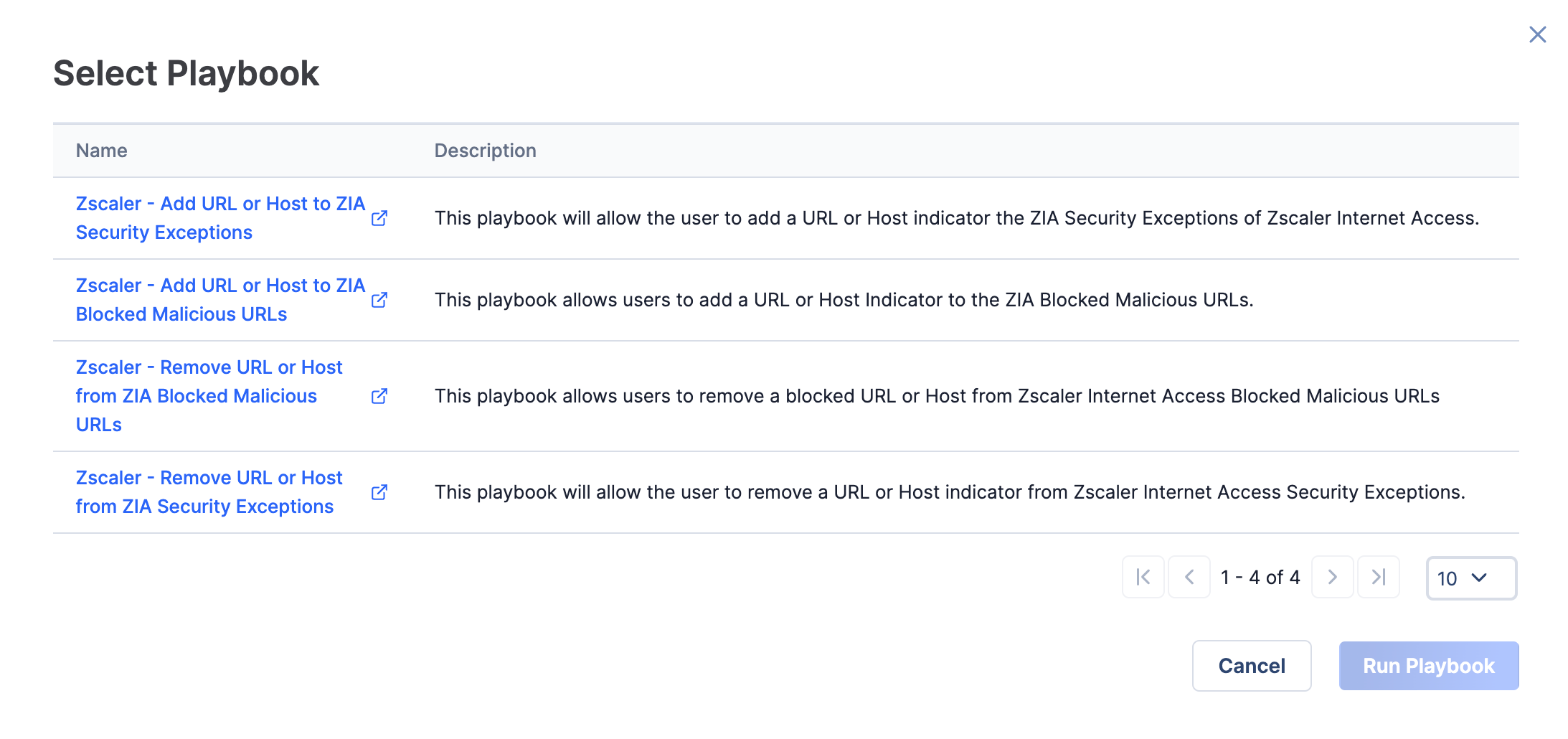
- Select the row containing the Zscaler - Remove URL or Host from ZIA Security Exceptions Playbook, and click the Run Playbook button.NoteClicking on a Playbook’s name will open the Playbook in the Playbook Designer in a new browser tab. Clicking on a Playbook’s row will select the Playbook for execution.NoteNo confirmation message that the Playbook was run will be displayed. See the “Verifying Results” section for instructions about how to verify that the operation occurred.
Adding Indicators to ZIA Blocked Malicious URLs
The ZScaler Content Pack - Add URL or Host to ZIA Blocked Malicious URLs Playbook has a UserAction Trigger, which allows you to execute the Playbook from the Playbooks card on the Overview tab of a Host or URL Indicator’s Details screen or while viewing the Indicator in Threat Graph.
Details Screen
- Navigate to the Details screen for the Host or URL Indicator that you want to add to the ZIA Blocked Malicious URLs list.
- On the Playbooks card, click Run playbook
 for the Zscaler - Add URL or Host to ZIA Blocked Malicious URLs Playbook (Figure 9).
for the Zscaler - Add URL or Host to ZIA Blocked Malicious URLs Playbook (Figure 9).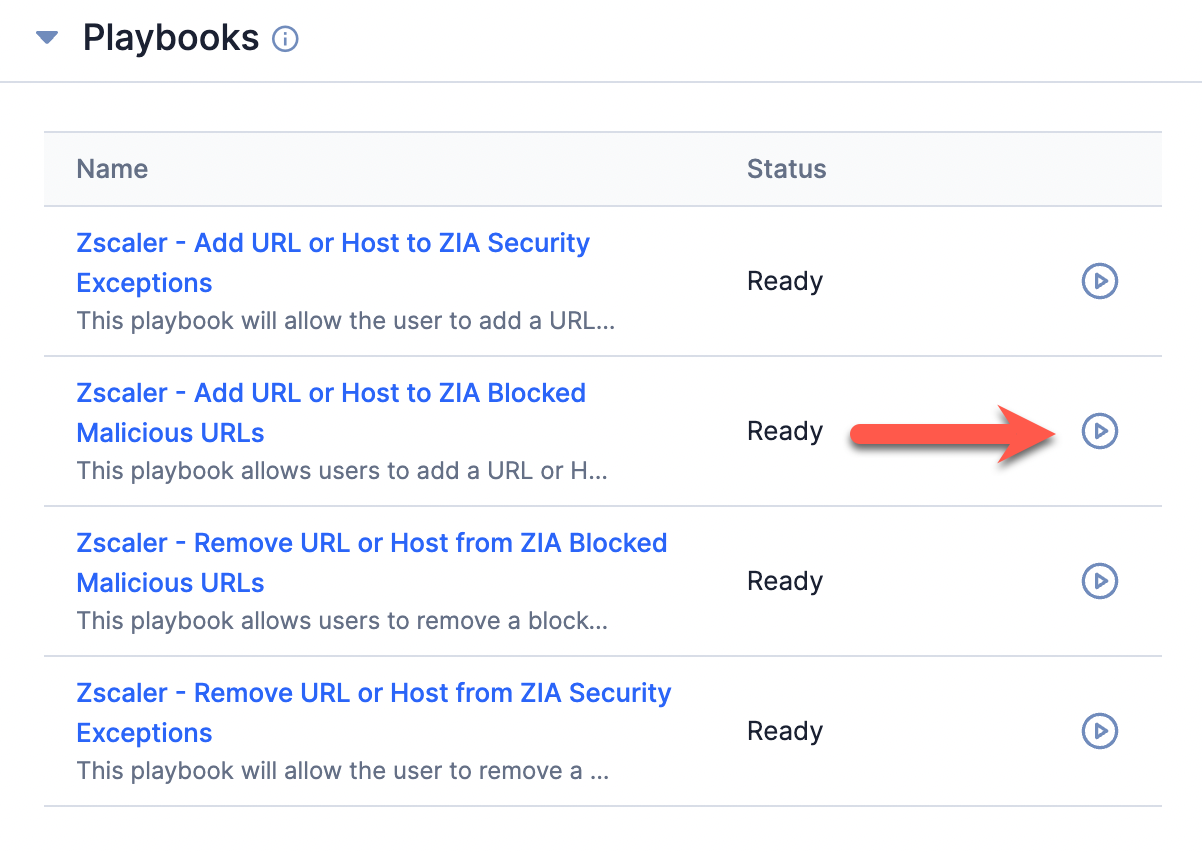
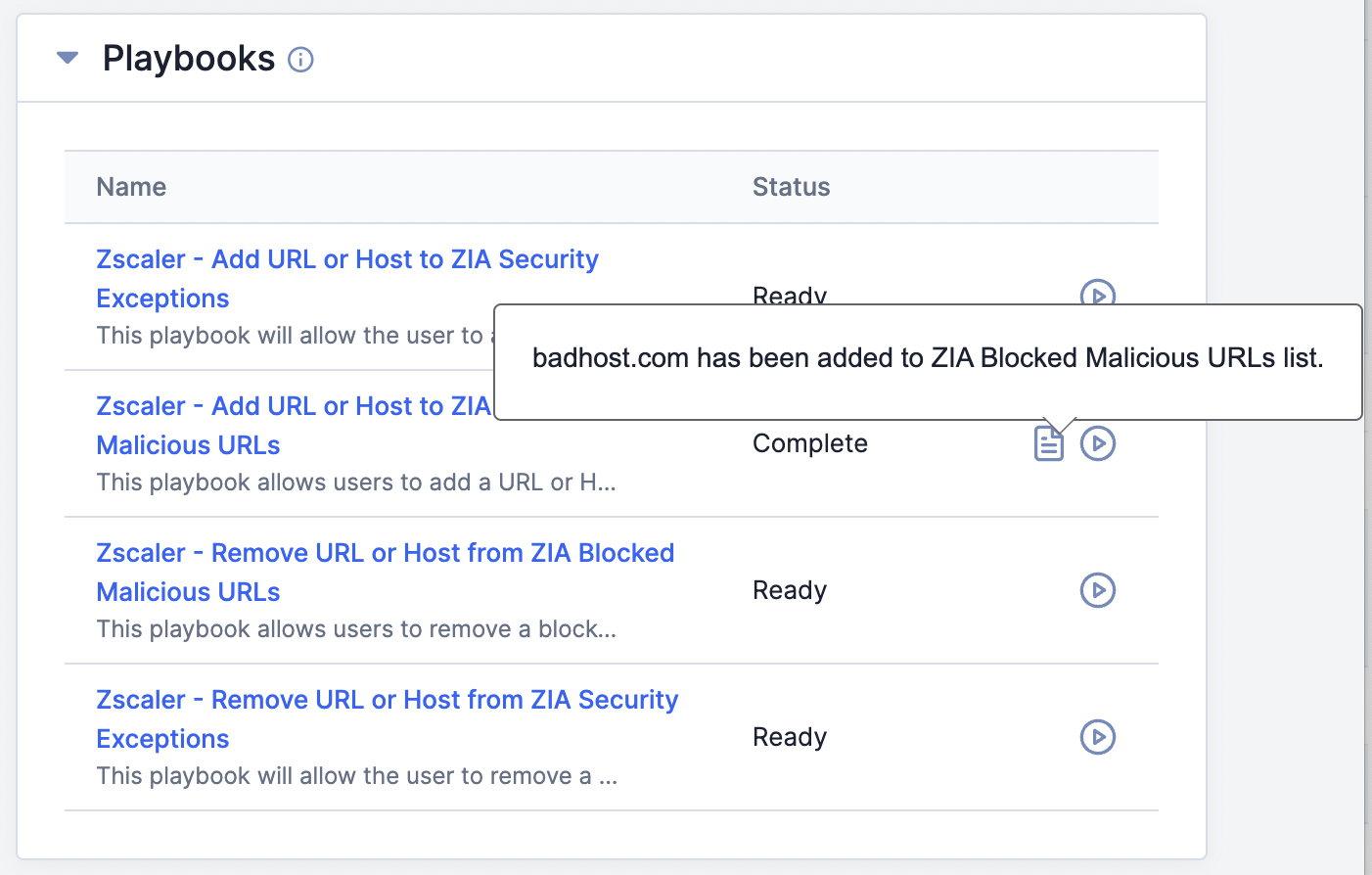
- A message stating “Starting playbook…” will be displayed at the lower-left corner of the screen. When the Playbook’s execution is complete, the Status of the Playbook will change to Complete, and then a tooltip stating that the Indicator was added to the ZIA Blocked Malicious URLs list will be displayed (Figure 10).
Threat Graph
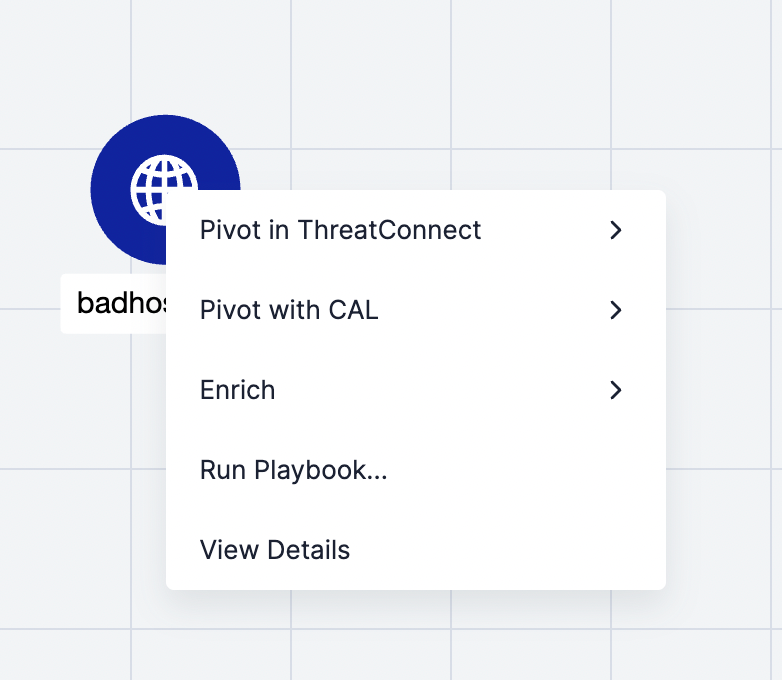
- Navigate to Threat Graph for the Host or URL Indicator that you want to add to the ZIA Blocked Malicious URLs list.
- Select Run Playbook… from the contextual menu for the node representing the Indicator (Figure 11).
- The Select Playbook window will be displayed, showing all active Playbooks containing a UserAction Trigger configured for the Indicator’s type (Figure 12).
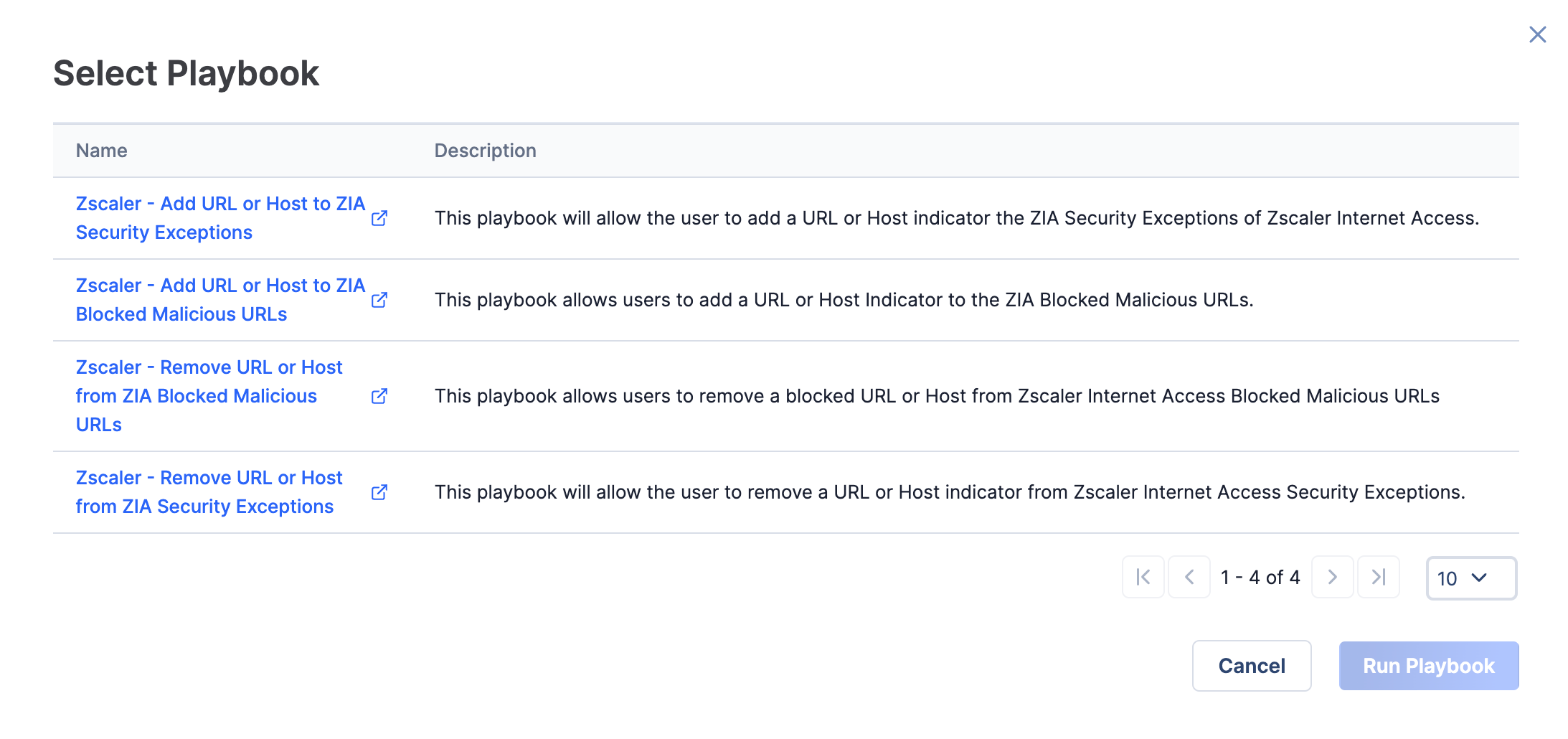
- Select the row containing the Zscaler - Add URL or Host to ZIA Blocked Malicious URLs Playbook, and click the Run Playbook button.NoteClicking on a Playbook’s name will open the Playbook in the Playbook Designer in a new browser tab. Clicking on a Playbook’s row will select the Playbook for execution.NoteNo confirmation message that the Playbook was run will be displayed. See the “Verifying Results” section for instructions about how to verify that the operation occurred.
Removing Indicators from ZIA Blocked Malicious URLs
The ZScaler Content Pack - Remove URL or Host from ZIA Blocked Malicious URLs Playbook has a UserAction Trigger, which allows you to execute the Playbook from the Playbooks card on the Overview tab of a Host or URL Indicator’s Details screen or while viewing the Indicator in Threat Graph.
Details Screen
- Navigate to the Details screen for the Host or URL Indicator that you want to remove from the ZIA Blocked Malicious URLs list.
- On the Playbooks card, click Run playbook
 for the Zscaler - Remove URL or Host from ZIA Blocked Malicious URLs Playbook (Figure 13).
for the Zscaler - Remove URL or Host from ZIA Blocked Malicious URLs Playbook (Figure 13).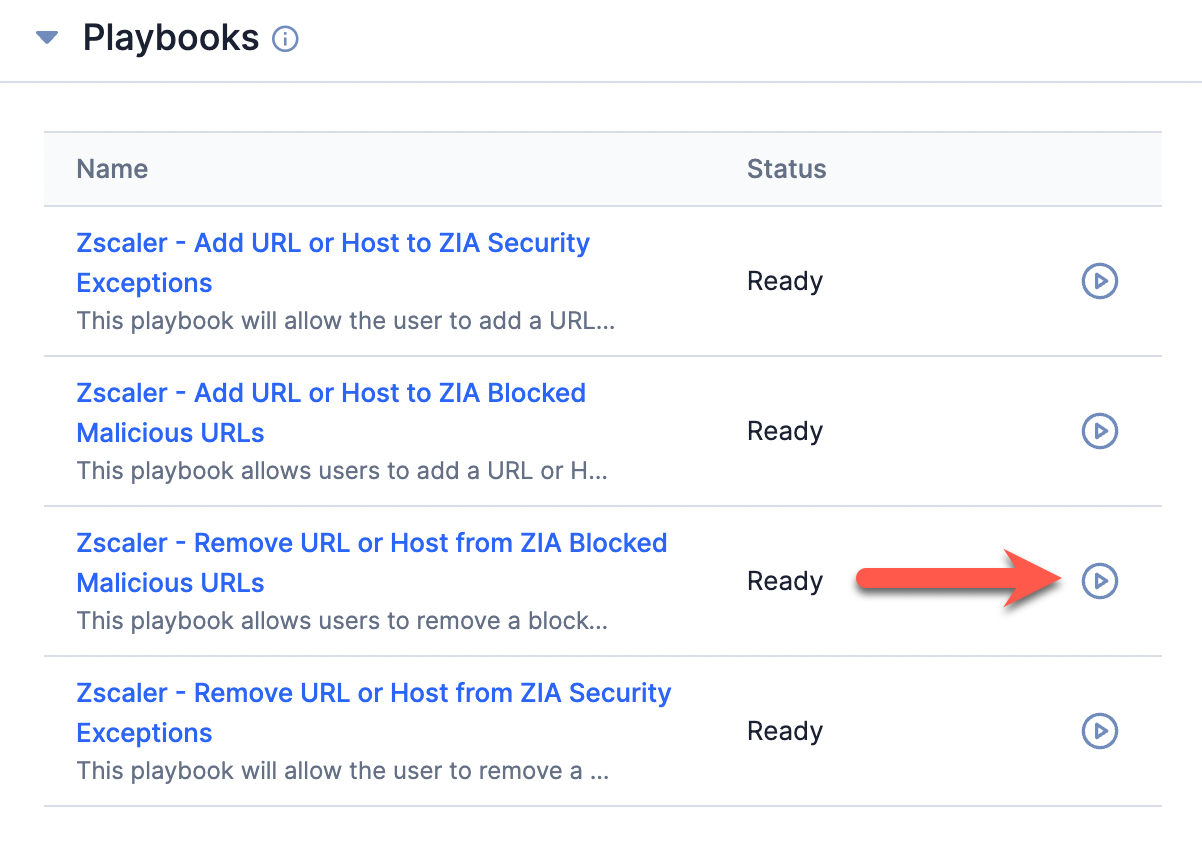
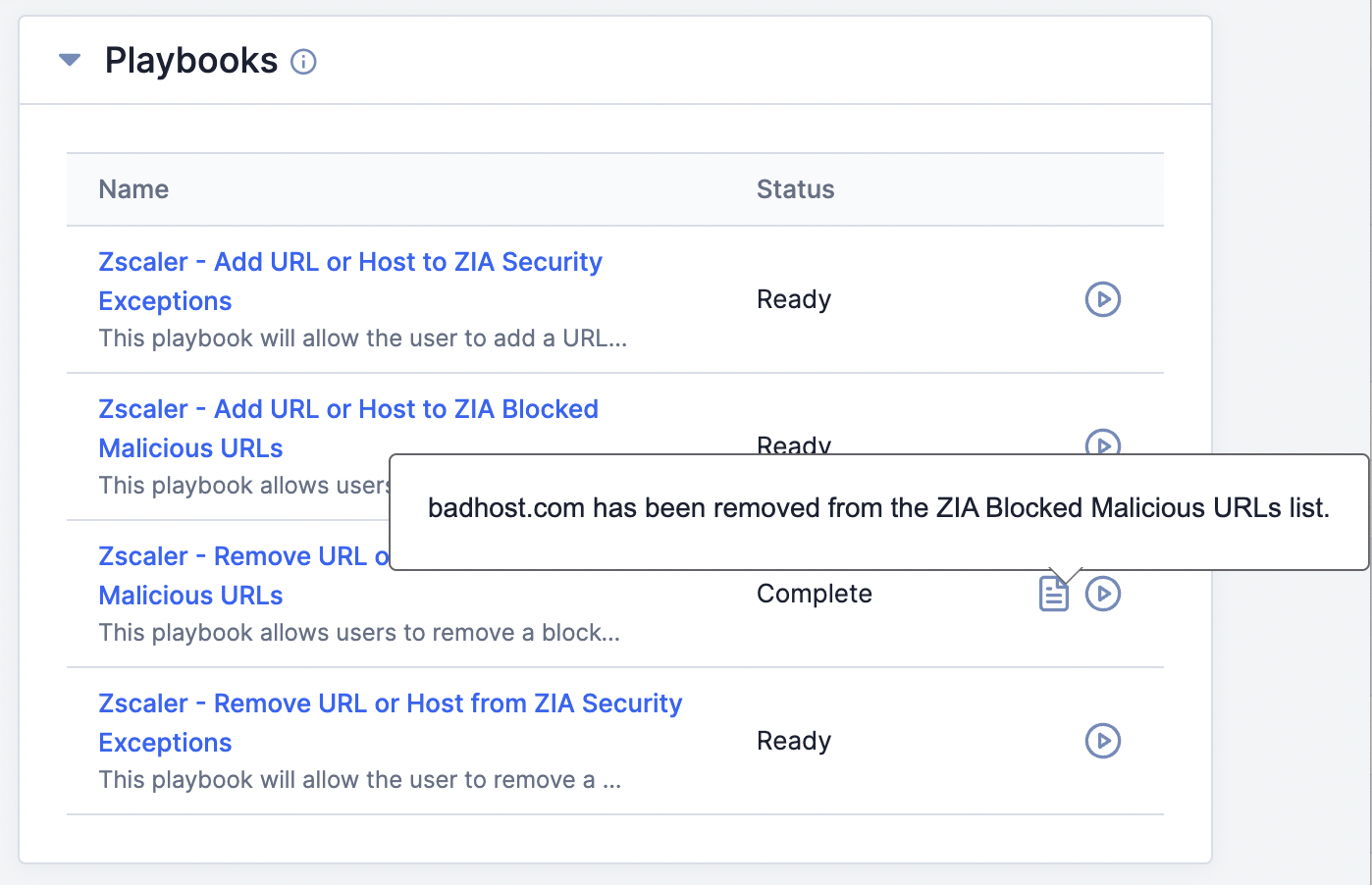
- A message stating “Starting playbook…” will be displayed at the lower-left corner of the screen. When the Playbook’s execution is complete, the Status of the Playbook will change to Complete, and a tooltip stating that the Indicator was removed from the ZIA Blocked Malicious URLs list will be displayed (Figure 14).
Threat Graph
- Navigate to Threat Graph for the Host or URL Indicator that you want to remove from the ZIA Blocked Malicious URLs list.
- Select Run Playbook… from the contextual menu for the node representing the Indicator (Figure 15).
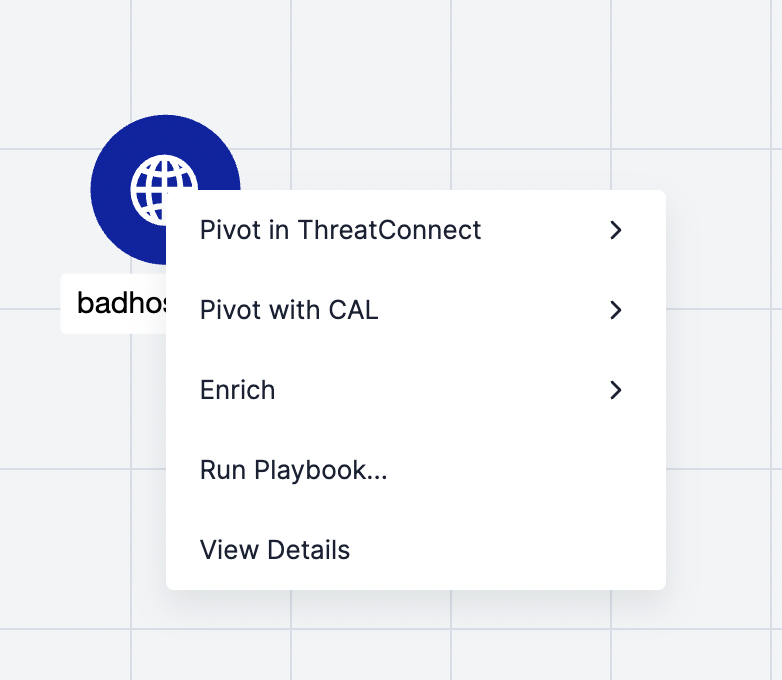
- The Select Playbook window will be displayed, showing all active Playbooks containing a UserAction Trigger configured for the Indicator’s type (Figure 16).
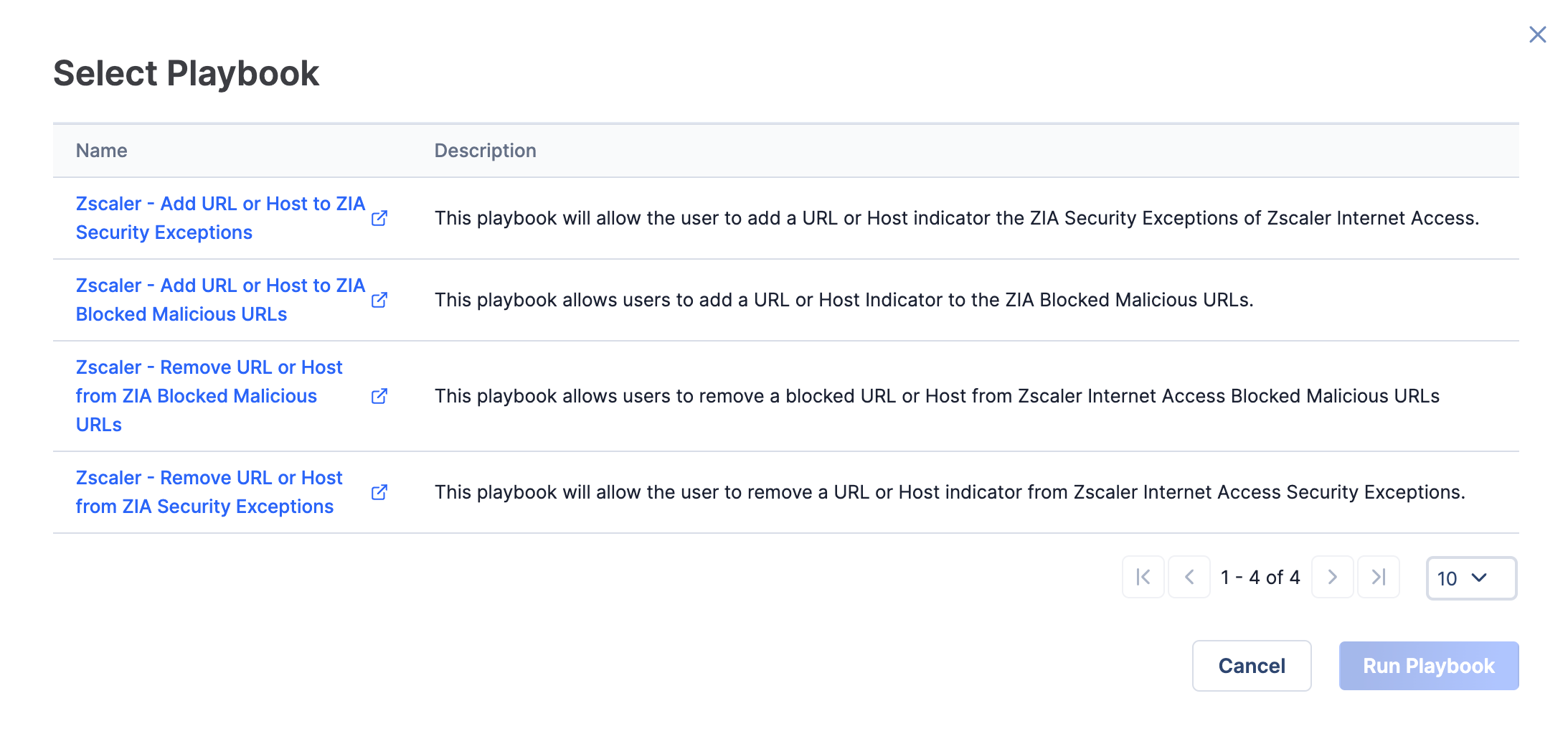
- Select the row containing the Zscaler - Remove URL or Host from ZIA Blocked Malicious URLs Playbook, and click the Run Playbook button.NoteClicking on a Playbook’s name will open the Playbook in the Playbook Designer in a new browser tab. Clicking on a Playbook’s row will select the Playbook for execution.NoteNo confirmation message that the Playbook was run will be displayed. See the “Verifying Results” section for instructions about how to verify that the operation occurred.
Verifying Results
You can verify the results of each Playbook’s execution in ThreatConnect and in Zscaler.
Verifying Results in ThreatConnect
You can verify that an Indicator was added to or removed from the ZIA Security Exceptions or Blocked Malicious URLs list after executing one of the Playbooks in the Zscaler Internet Access Content Pack by viewing the output from the Playbook’s execution.
- After executing the Playbook, click on the Playbook’s name on the Playbooks card of the Indicator’s Details screen or the Select Playbook window when viewing the Indicator in Threat Graph to view its execution pane. Figure 17 uses the Zscaler - Add URL or Host to ZIA Security Exceptions Playbook as an example.NoteIf the Playbook’s execution pane is not displayed when the Playbook opens in the Playbook Designer, open the execution pane by clicking
 Executions on the side navigation bar of the Playbook Designer, and then click on the latest execution to open its details.
Executions on the side navigation bar of the Playbook Designer, and then click on the latest execution to open its details.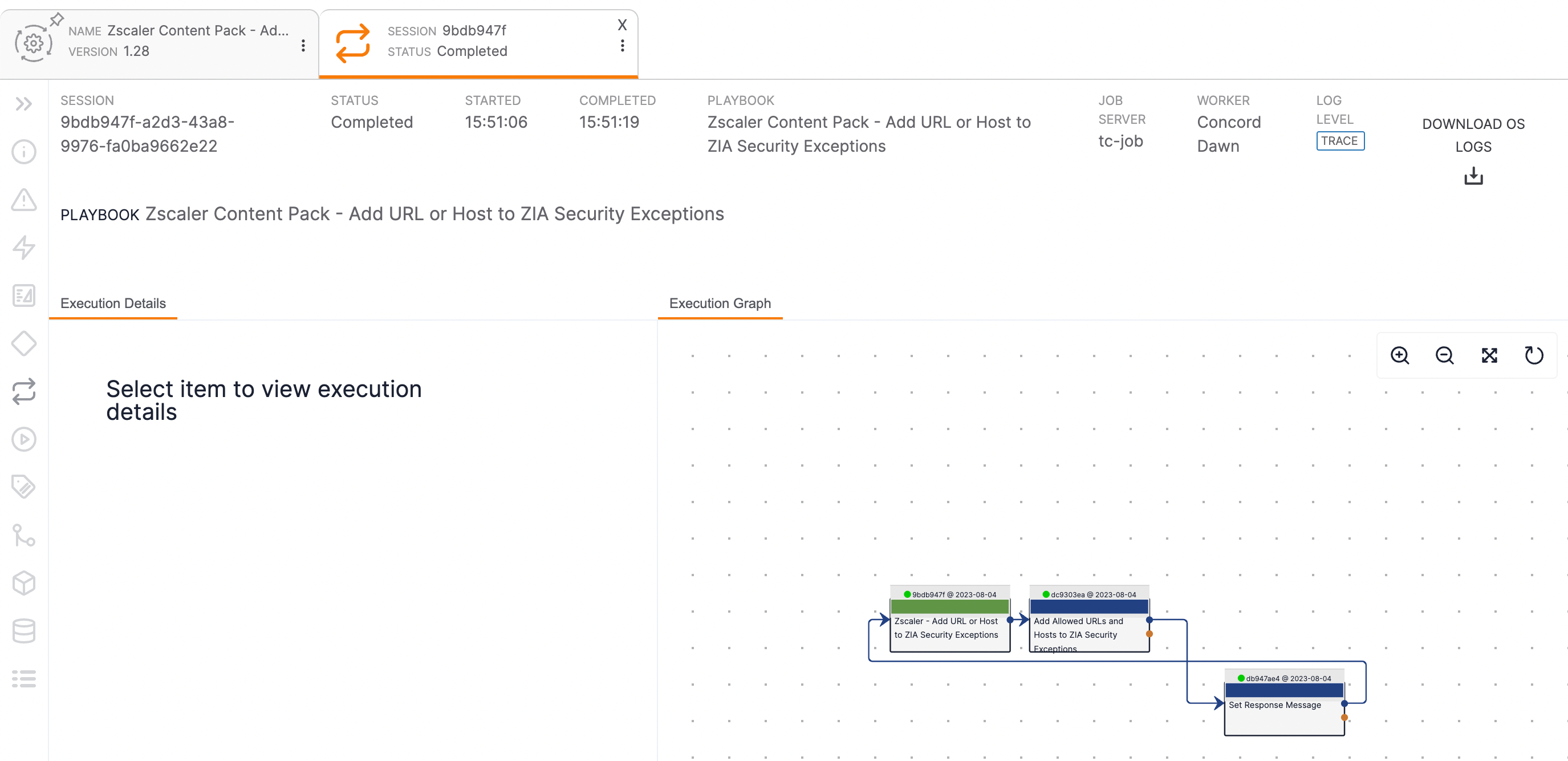
- If necessary, zoom in on the Execution Graph pane, and then click on the App corresponding to the executed Playbook in Table 1 to populate the Execution Details pane for the App. Click on the Outputs tab and scroll down to view the contents of the outputs table (Figure 18).
Playbook App Zscaler Content Pack - Add URL or Host to ZIA Security Exceptions Add Allowed URLs and Hosts to ZIA Security Exceptions Zscaler Content Pack - Add URL or Host to ZIA Blocked Malicious URLs Add Blocked URLs and Hosts to ZIA Blocked Malicious URLs Zscaler Content Pack - Remove URL or Host from ZIA Security Exceptions Remove Allowed URLs and Hosts from ZIA Security Exceptions Zscaler Content Pack - Remove URL or Host from ZIA Blocked Malicious URLs Remove Blocked URLs and Hosts from ZIA Blocked Malicious URLs 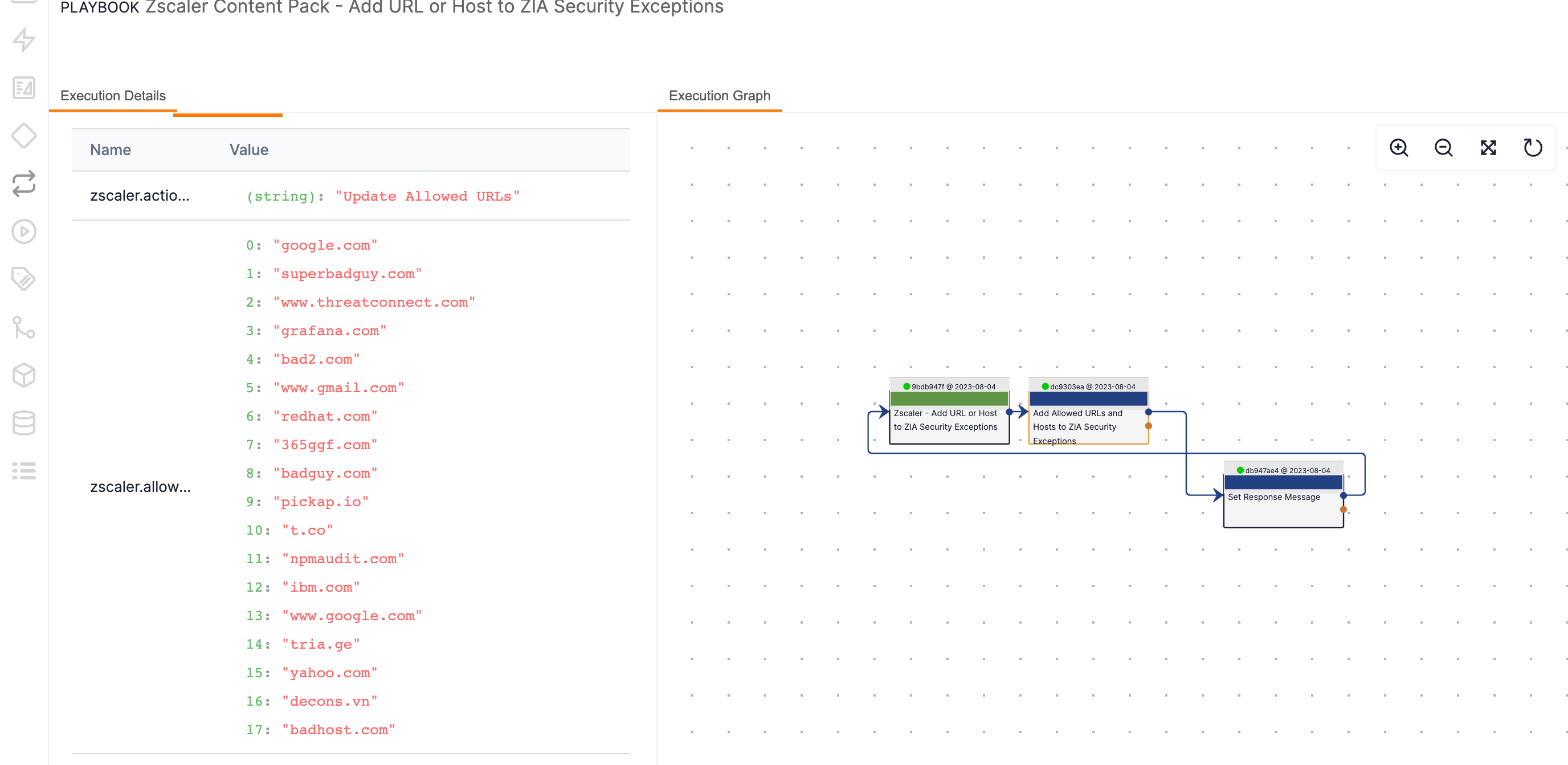
- The Outputs tab displays the contents of the Zscaler list (Security Exceptions or Blocked Malicious URLs) after the add or remove operation was performed. Confirm that the Indicator is on the list (for add operations) or is not on the list (for remove operations) in the Value column. In this example, the Indicator badhost.com (item 17 in the Value column of the Outputs tab) is on the list, confirming that the add operation was successful.ImportantThe log level of the Playbook must be set to TRACE or DEBUG for the Outputs tab to display the contents of the list.
Verifying Results in Zscaler
You can verify that an Indicator was added to or removed from the ZIA Security Exceptions or Blocked Malicious URLs list after executing one of the Playbooks in the Zscaler Internet Access Content Pack by viewing the list in ZIA.
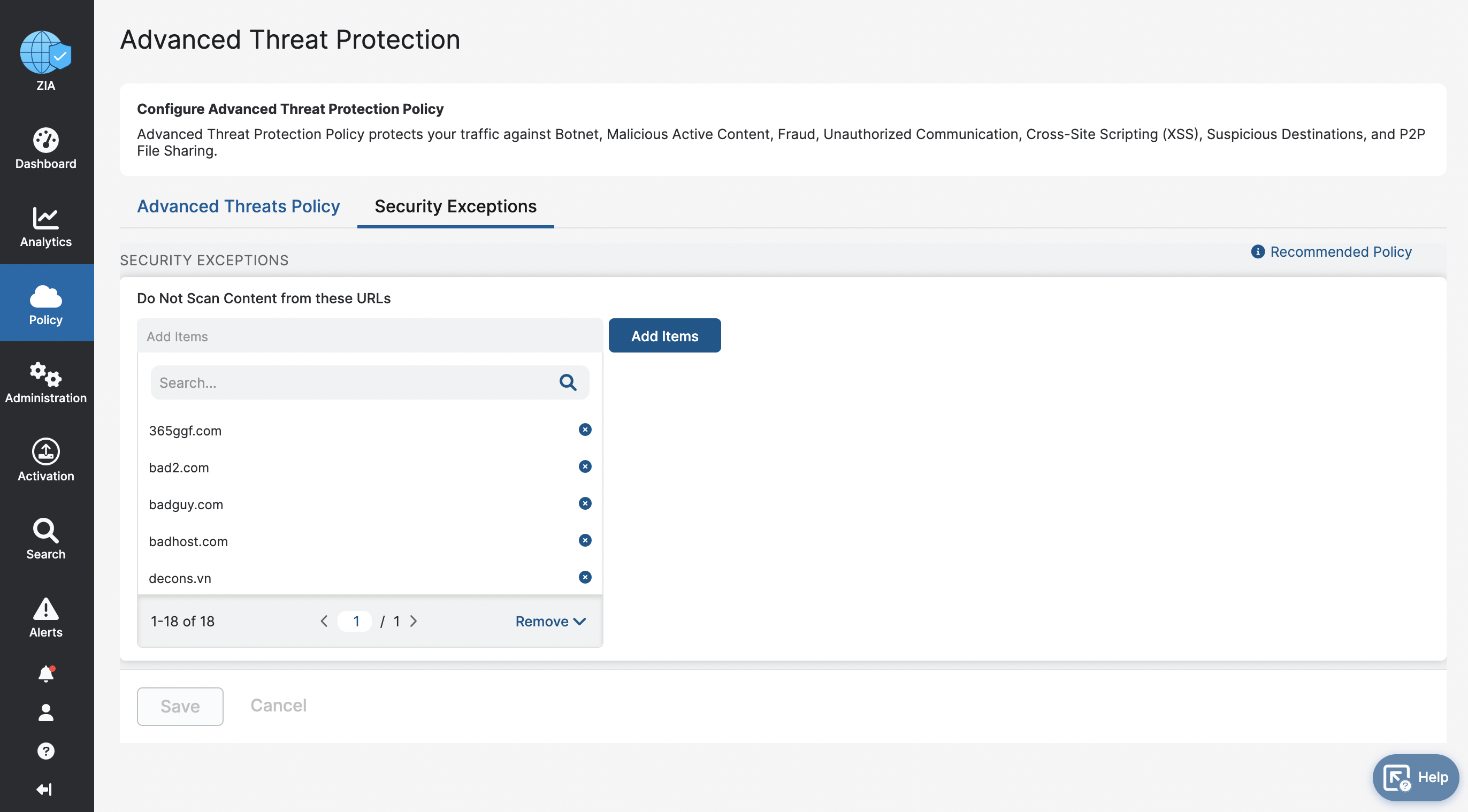
Security Exceptions List
- Log into ZIA.
- Hover over Policy on the navigation bar on the left.
- Click on Advanced Threat Protection (Figure 19).

- The Advanced Threat Protection screen will be displayed with the Advanced Threats Policy tab selected. Click on the Security Exceptions tab to view the current Security Exceptions list and verify that the Indicator is on the list (for add operations) or is not on the list (for remove operations). In this example, the Indicator badhost.com is on the list, confirming that the add operation was successful (Figure 20).
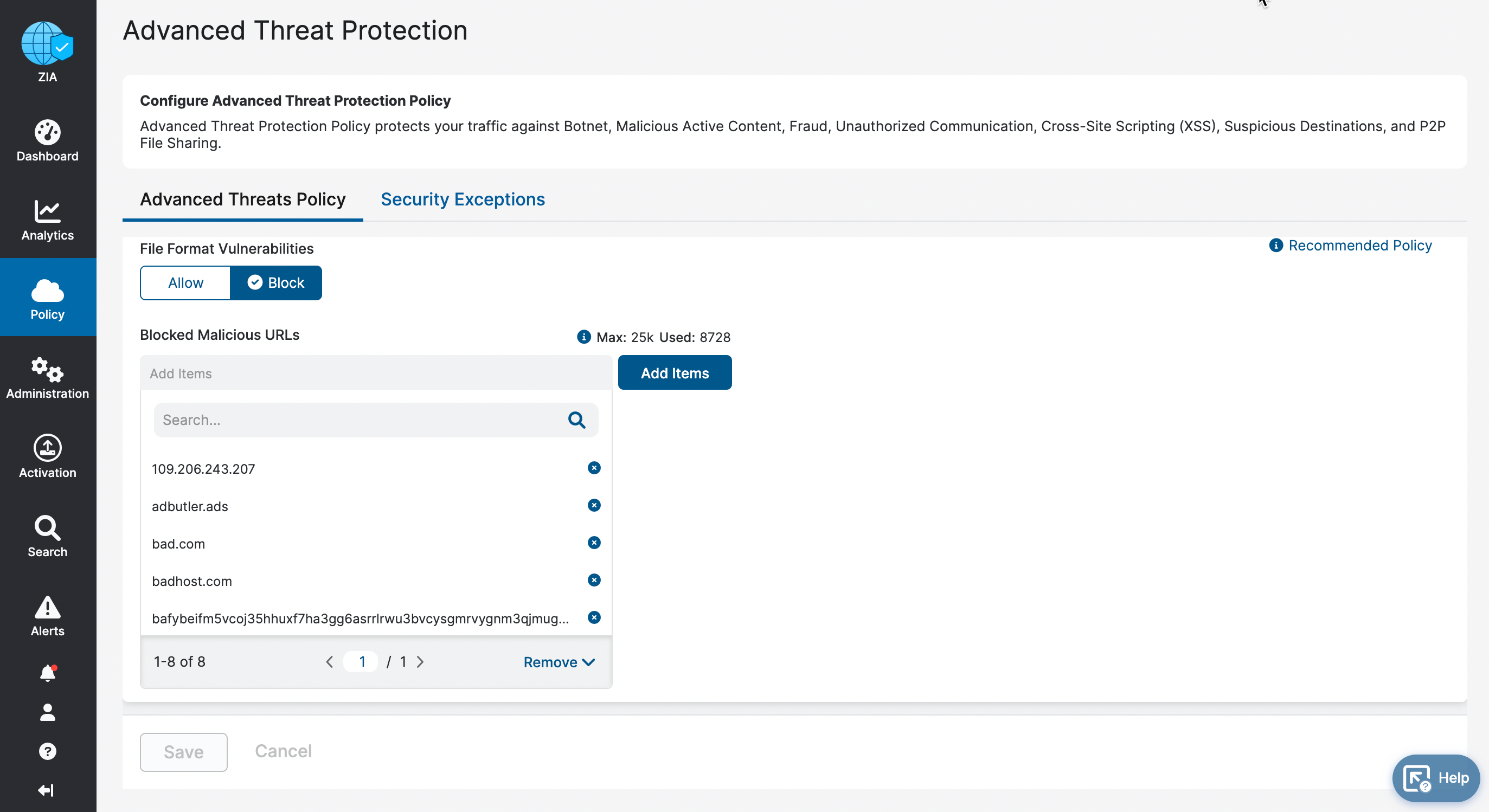
Blocked Malicious URLs List
- Log into ZIA.
- Hover over Policy on the navigation bar on the left.
- Click on Advanced Threat Protection (Figure 19).
- The Advanced Threat Protection screen will be displayed with the Advanced Threats Policy tab selected. Scroll down to view the current Blocked Malicious URLs list and verify that the Indicator is on the list (for add operations) or is not on the list (for remove operations). In this example, the Indicator badhost.com is on the list, confirming that the add operation was successful (Figure 21).
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
Zscaler™ and Zscaler Internet Access™ are trademarks of Zscaler, Inc.
20157-03 v.01.A


