- 18 Sep 2024
- 4 Minutes to read
-
Print
-
DarkLight
-
PDF
Pivoting on Enrichment Services in Threat Graph
- Updated on 18 Sep 2024
- 4 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The Threat Graph feature in ThreatConnect® provides a graph-based interface that you can use to discover, visualize, and contextualize associations and relationships between Indicators, Groups, Cases, and Tags. The Enrich option in Threat Graph, available for Indicators only, lets you to pivot on relationships available for a given third-party enrichment service and Indicator type. At this time, you can pivot on the following enrichment services in Threat Graph:
- DomainTools®: Available for Host Indicators only.
- RiskIQ®: Available for Host Indicators only.
- Shodan®: Available for Address Indicators only.
- urlscan.io: Available for URL Indicators only.
- VirusTotal™: Available for Address, File, Host, and URL Indicators only.
Before You Start
User Roles
- To pivot on enrichment service relationships for Indicators in an Organization in Threat Graph, your user account can have any Organization role.
- To pivot on enrichment service relationships for Indicators in a Community or Source in Threat Graph, your user account can have any Community role except Banned for that Community or Source.
Prerequisites
- To pivot on enrichment service relationships in Threat Graph, turn on and configure one or more of the following third-party enrichment services on your ThreatConnect instance (must be a System Administrator to perform this action): DomainTools, RiskIQ, Shodan, urlscan.io, and VirusTotal.
Performing a Pivot
- Open Threat Graph.
- Select an Indicator node on the graph corresponding to an Indicator type for which an enrichment service is turned on and configured. If no such node is on the graph, pivot in ThreatConnect or CAL to add one.
- Select Enrich in the node’s menu. Then select an enrichment service on which to pivot in the Enrich submenu (Figure 1).

- Select an enrichment service relationship to pivot on in the enrichment service’s submenu. Alternatively, select All (for DomainTools, RiskIQ, urlscan.io, and VirusTotal) or All Vulnerabilities (for Shodan) to pivot on all enrichment service relationships available for the Indicator’s type. If the pivot returns related objects, the following items will be added to the graph:
- One or more related nodes, each of which represents a related object retrieved from the selected enrichment service. Each node will have a node label that displays the corresponding object’s summary.
- One or more blue arrows, each connecting a related node and the node from which you pivoted.
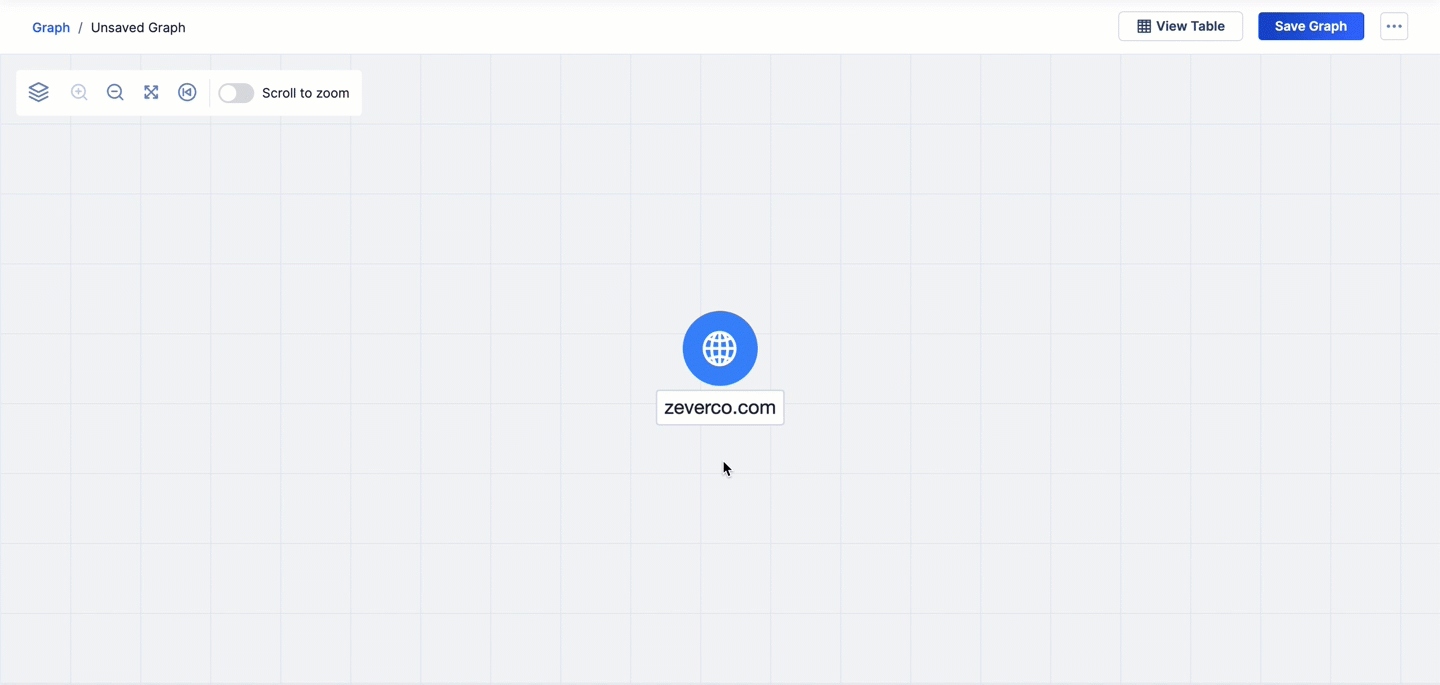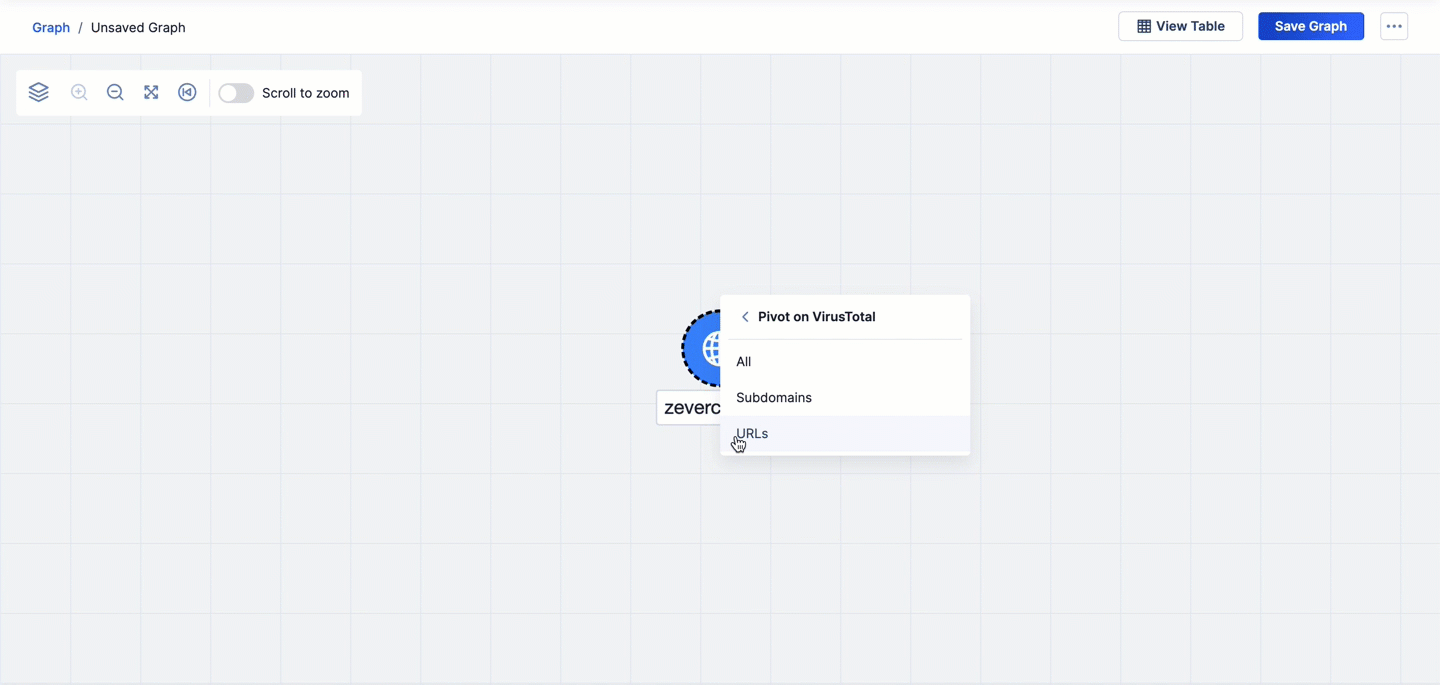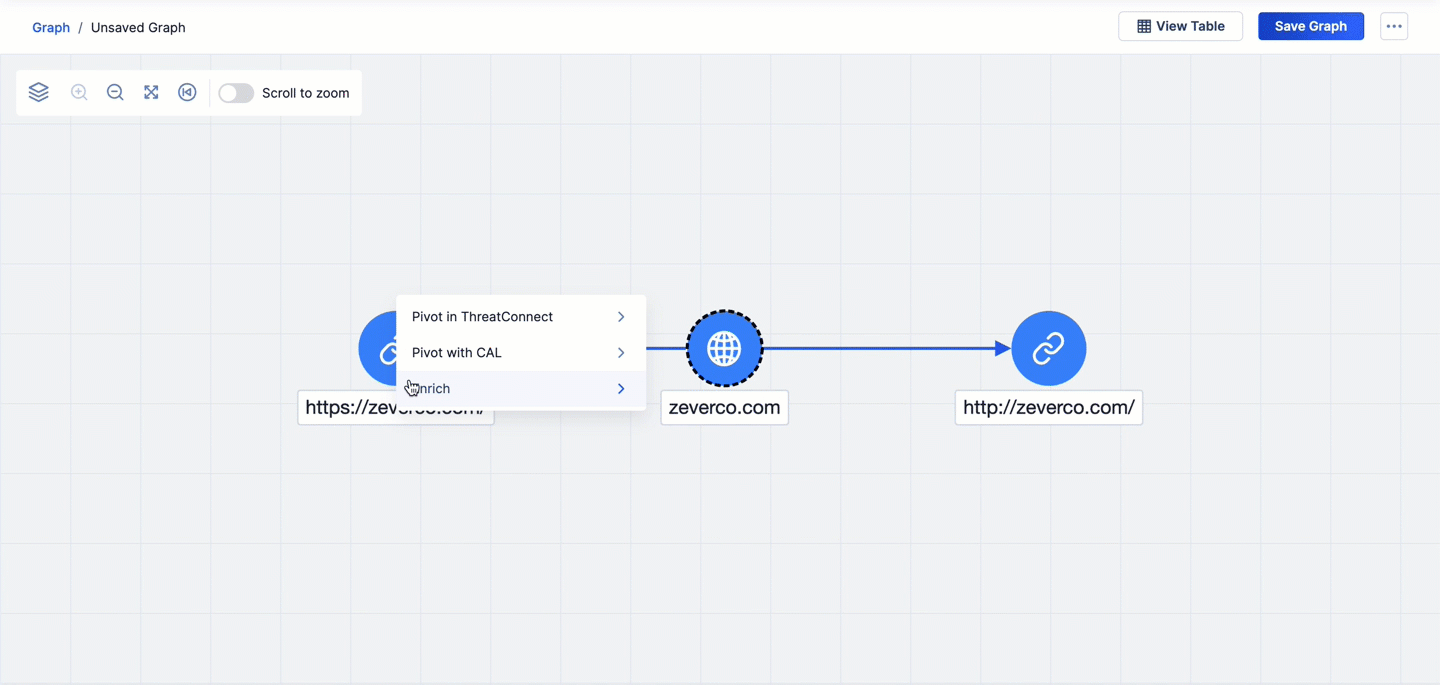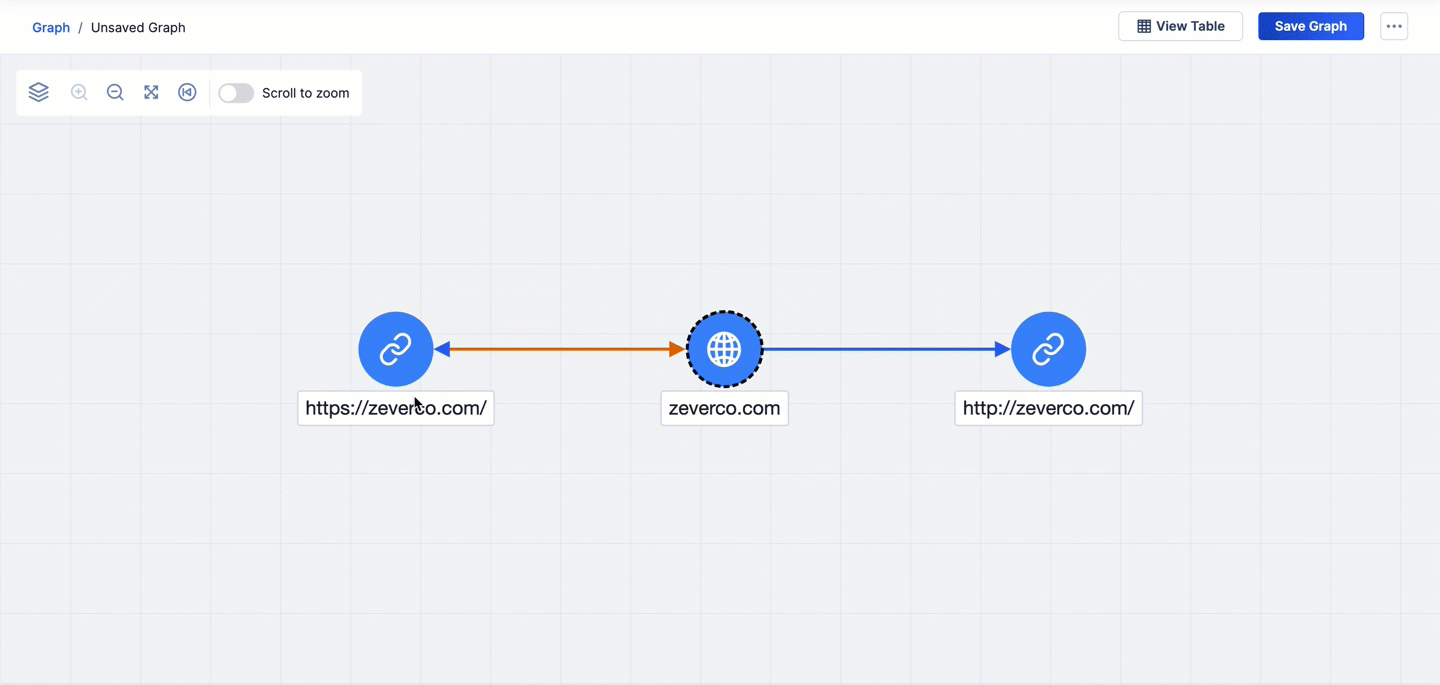
Figure 2 shows three enrichment service pivots in Threat Graph:
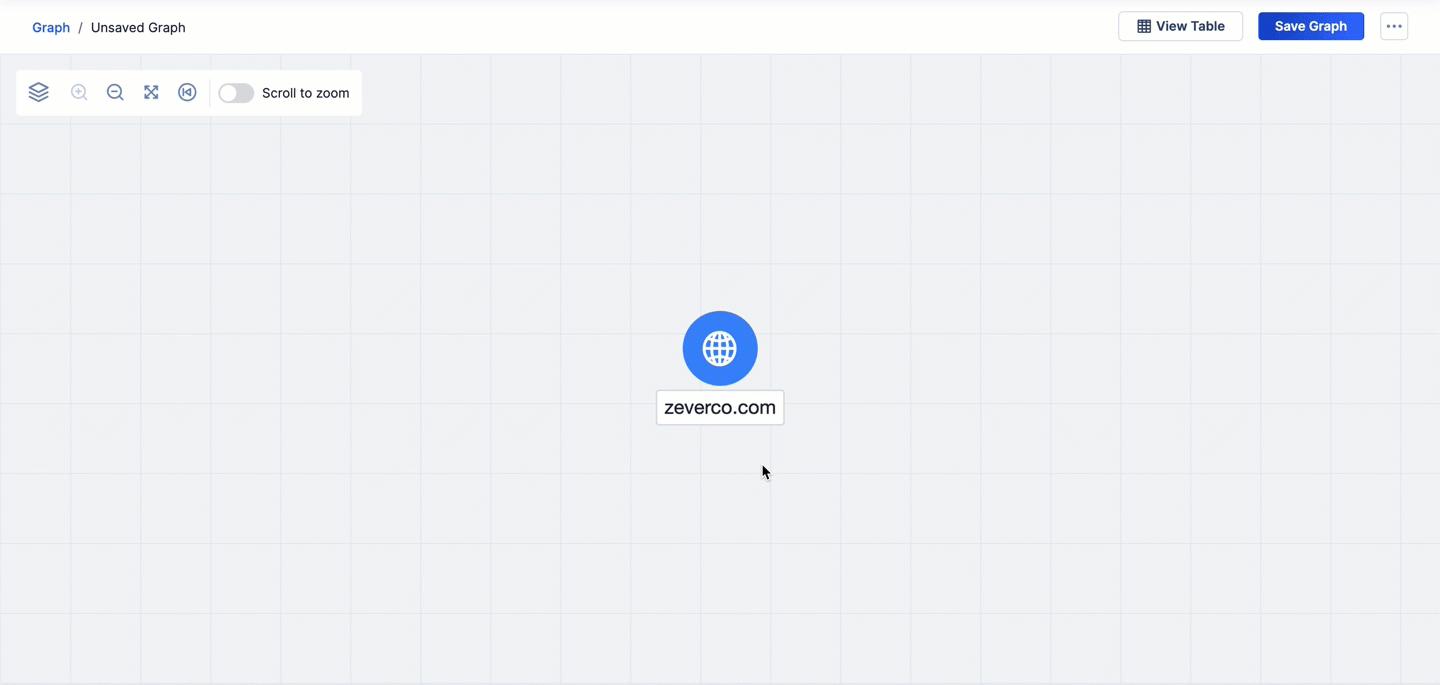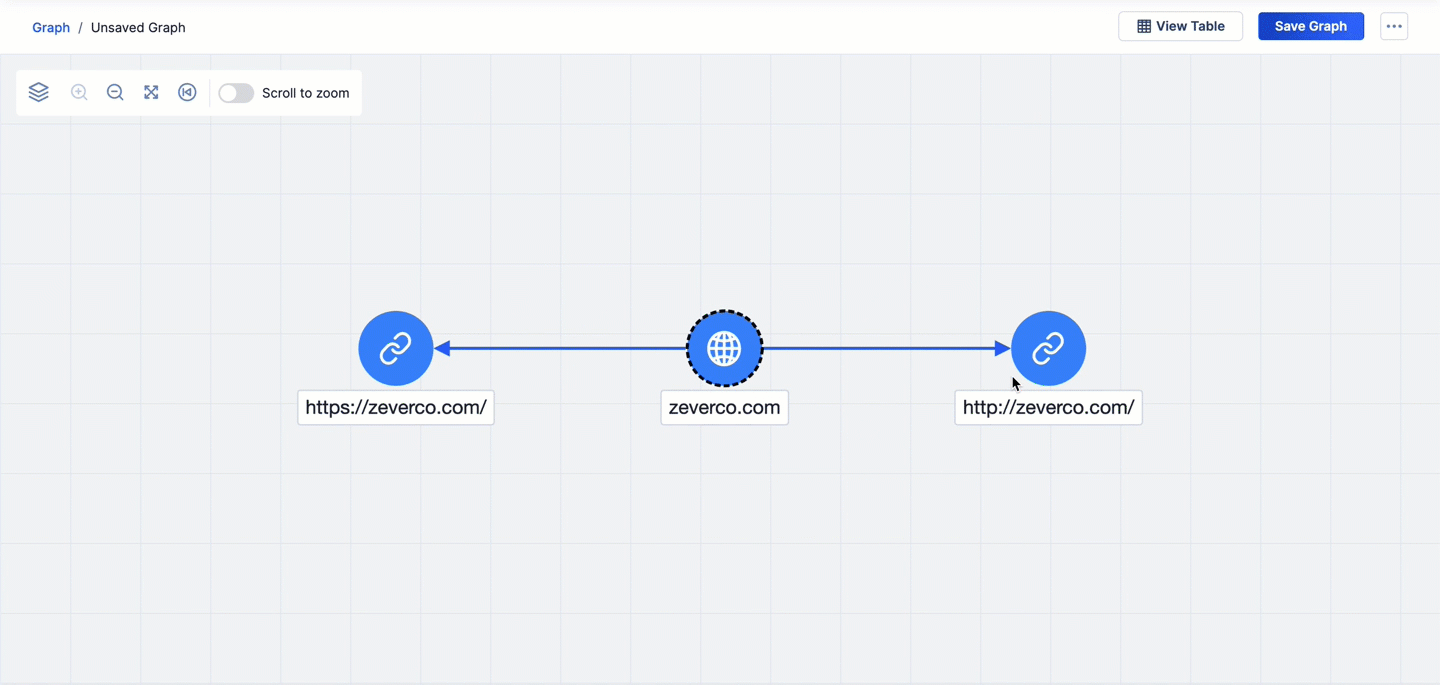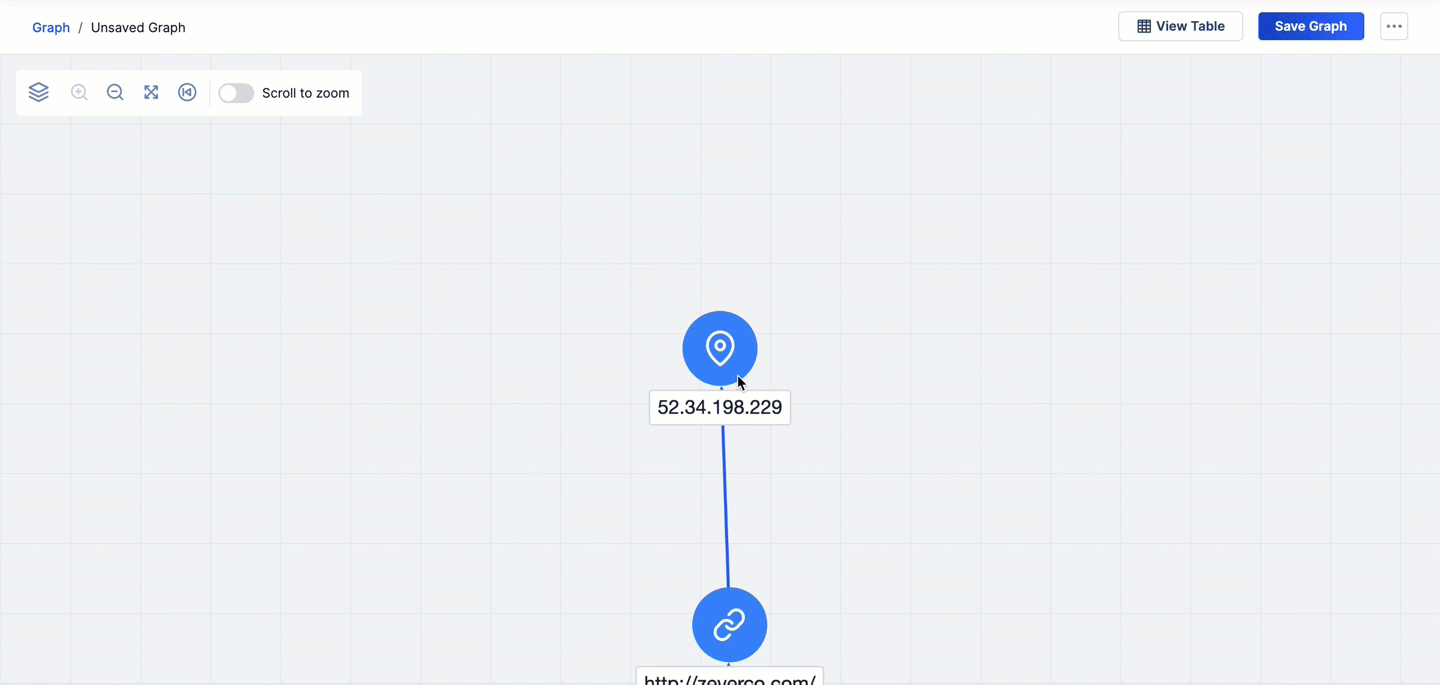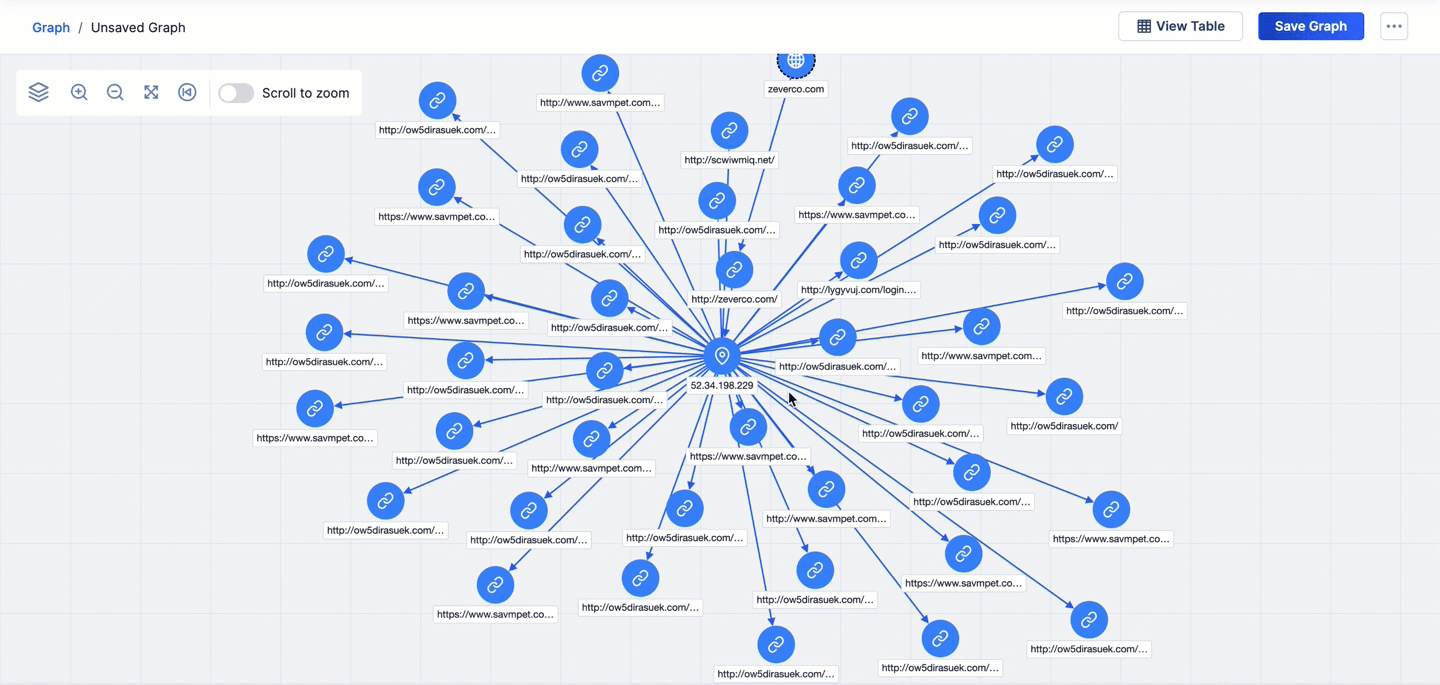
- The first pivot is on the VirusTotal URLs relationship from the zeverco.com Host Indicator. This pivot returns two URL Indicators that are related to zeverco.com and adds them to the graph.
- The second pivot is on the urlscan.io IP Address relationship from the http://zeverco.com/ URL Indicator that was added to the graph via the first pivot. This pivot returns one Address Indicator that is related to http://zeverco.com/ and adds it to the graph.
- The third pivot is on the VirusTotal URLs relationship from the 52.34.198.229 Address Indicator that was added to the graph via the second pivot. This pivot returns 40 URL Indicators that are related to 52.34.198.229 and adds them to the graph.
Available Enrichment Relationships
DomainTools
See Table 1 for a list of DomainTools relationships available in Threat Graph for Host Indicators.
| Relationship | Starting Indicator Type | Indicator Type Returned from Pivot |
|---|---|---|
| IP Addresses | Host | Address |
| Name Servers | Host | Host |
RiskIQ
See Table 2 for a list of RiskIQ relationships available in Threat Graph for Host Indicators.
| Relationship | Starting Indicator Type(s) | Indicator Type Returned from Pivot |
|---|---|---|
| DNS | Host | Host |
| IP Resolutions | Host | Address |
| Name Servers | Host | Host |
| Subdomains | Host | Host |
Shodan
See Table 3 for a list of Shodan relationships available in Threat Graph for Address Indicators.
| Relationship | Starting Indicator Type | Group Type Returned from Pivot |
|---|---|---|
| Unverified Vulnerabilities | Address | Vulnerability |
| Verified Vulnerabilities | Address | Vulnerability |
urlscan.io
See Table 4 for a list of urlscan.io relationships available in Threat Graph for URL Indicators.
| Relationship | Starting Indicator Type | Indicator Type Returned from Pivot |
|---|---|---|
| IP Address | URL | Address |
| Links to Domains | URL | URL |
VirusTotal
See Table 5 for a list of VirusTotal relationships available in Threat Graph for Address, File, Host, and URL Indicators.
| Relationship | Starting Indicator Type(s) | Indicator Type Returned from Pivot |
|---|---|---|
| Contacted Domains | File; URL | Host |
| Contacted IPs | File; URL | Address |
| Contacted URLs | File | URL |
| Subdomains | Host | Host |
| URLs | Address; Host | URL |
Pivoting Behaviors
When using the Enrich option in Threat Graph, you may observe the following behaviors as you interact with and add nodes to the graph:
- If a pivot returns more than 500 related objects, only the first 500 related nodes and their respective connections will be added to the graph.
- If you pivot from one node to a second node and then pivot from the second node back to the first node, the arrow connecting the two nodes will change to a bidirectional arrow. For example, in Figure 3, the first pivot is on the VirusTotal URLs relationship from the zeverco.com Host Indicator. This pivot returns two URL Indicators. The second pivot is on the VirusTotal Contacted Domains relationship from the https://zeverco.com/ URL Indicator that was added to the graph via the first pivot. This pivot returns one related object, which is to the zeverco.com Host Indicator already on the graph. As a result, the arrow connecting the zeverco.com Host Indicator to the https://zeverco.com/ URL Indicator changes to a bidirectional arrow to reflect the pivot from https://zeverco.com/ back to the zeverco.com.
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
DomainTools® is a registered trademark of DomainTools, LLC.
VirusTotal™ is a trademark of Google, Inc.
RiskIQ® is a registered trademark of Microsoft Corporation.
Shodan® is a registered trademark of Shodan.
20117-10 v.05.A


