- 18 Sep 2024
- 5 Minutes to read
-
Print
-
DarkLight
-
PDF
Pivoting With CAL in Threat Graph
- Updated on 18 Sep 2024
- 5 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The Threat Graph feature in ThreatConnect® provides a graph-based interface that you can use to discover, visualize, and contextualize associations and relationships between Indicators, Groups, Cases, and Tags. The Pivot with CAL option in Threat Graph, available for Indicators and Groups only, lets you explore Indicator and Group relationships that exist in CAL™.
Before You Start
User Roles
- To pivot on CAL relationships for Indicators and Groups in an Organization in Threat Graph, your user account can have any Organization role.
- To pivot on CAL relationships for Indicators and Groups in a Community or Source in Threat Graph, your user account can have any Community role except Banned for that Community or Source.
Prerequisites
- To use the Pivot with CAL option in Threat Graph, turn on CAL for your ThreatConnect instance (must be a System Administrator to perform this action).
Performing a Pivot
- Open Threat Graph.
- Select an Indicator or Group node on the graph. If no such node is on the graph, pivot in ThreatConnect to add one.
- Select Pivot with CAL in the node’s menu. If data exist in CAL for the Indicator or Group, the Pivot with CAL submenu will display a list of available CAL relationships you can pivot on and the number of related objects included in each relationship (Figure 1).
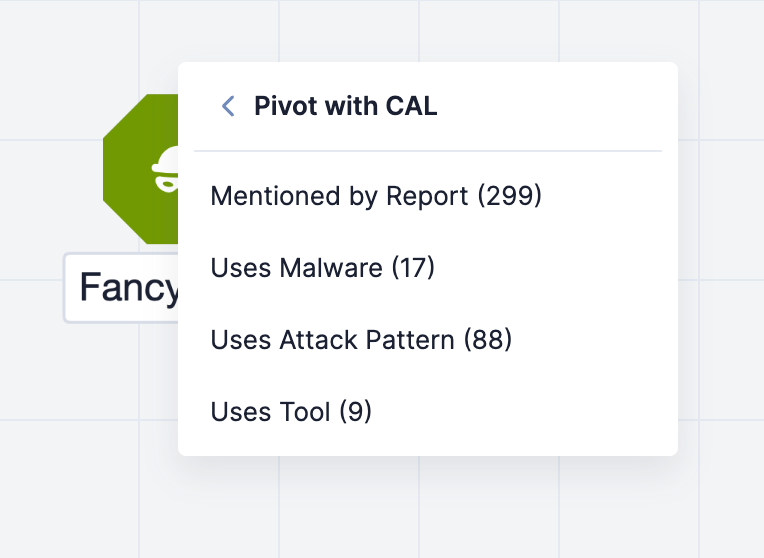
- Select an available CAL relationship to pivot on in the Pivot with CAL submenu. After you select a CAL relationship, the following items will be added to the graph:
- One or more related nodes, each of which represents a related Indicator (if pivoting from an Indicator) or Group (if pivoting from a Group) in CAL. Each related node will have a node label that displays the corresponding object’s summary.
- One or more gray arrows, each connecting a related node to the node from which you pivoted. Each gray arrow will have a label that displays the CAL relationship connecting the two nodes.
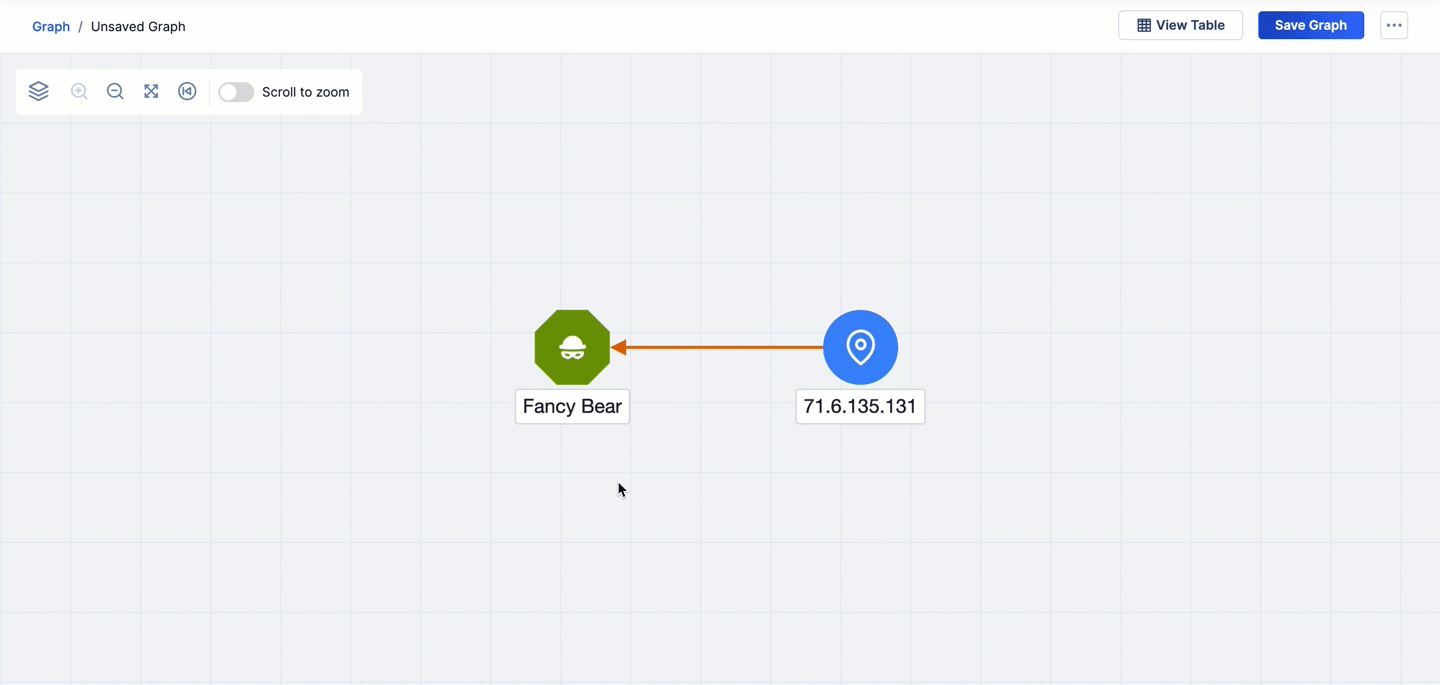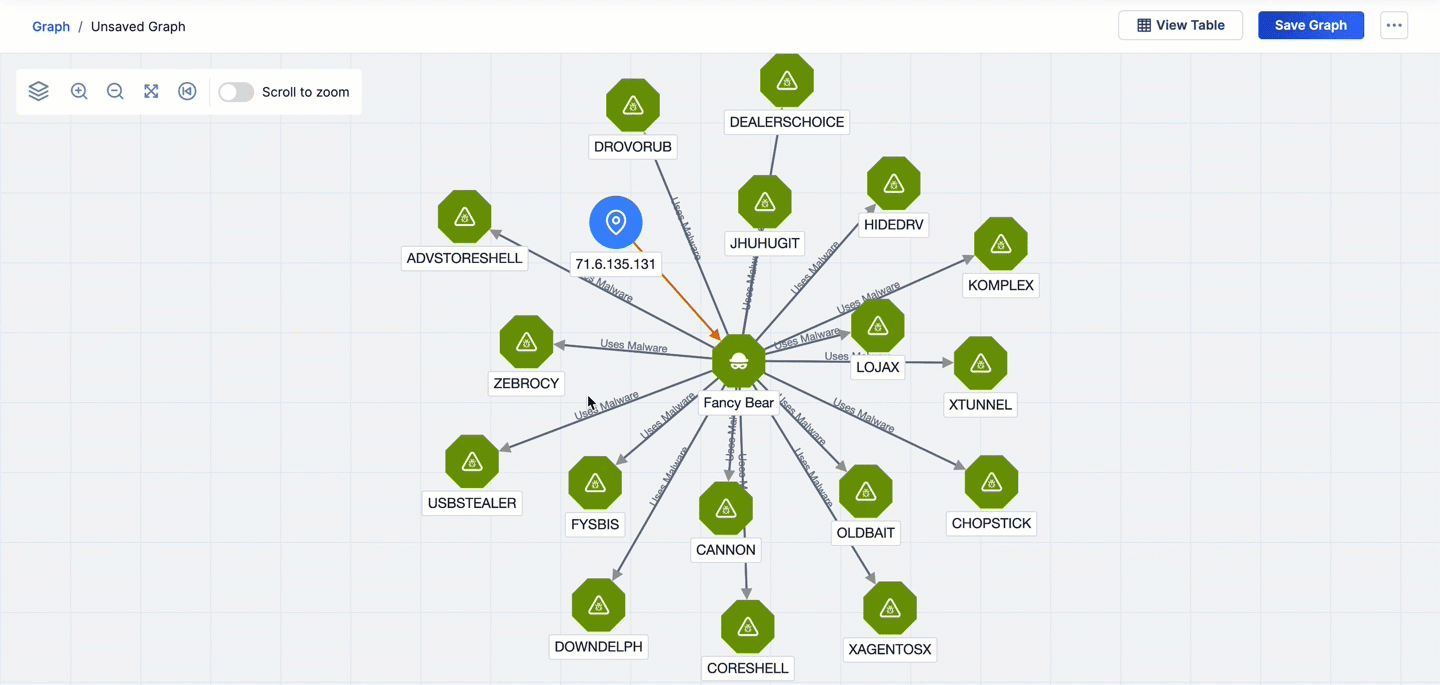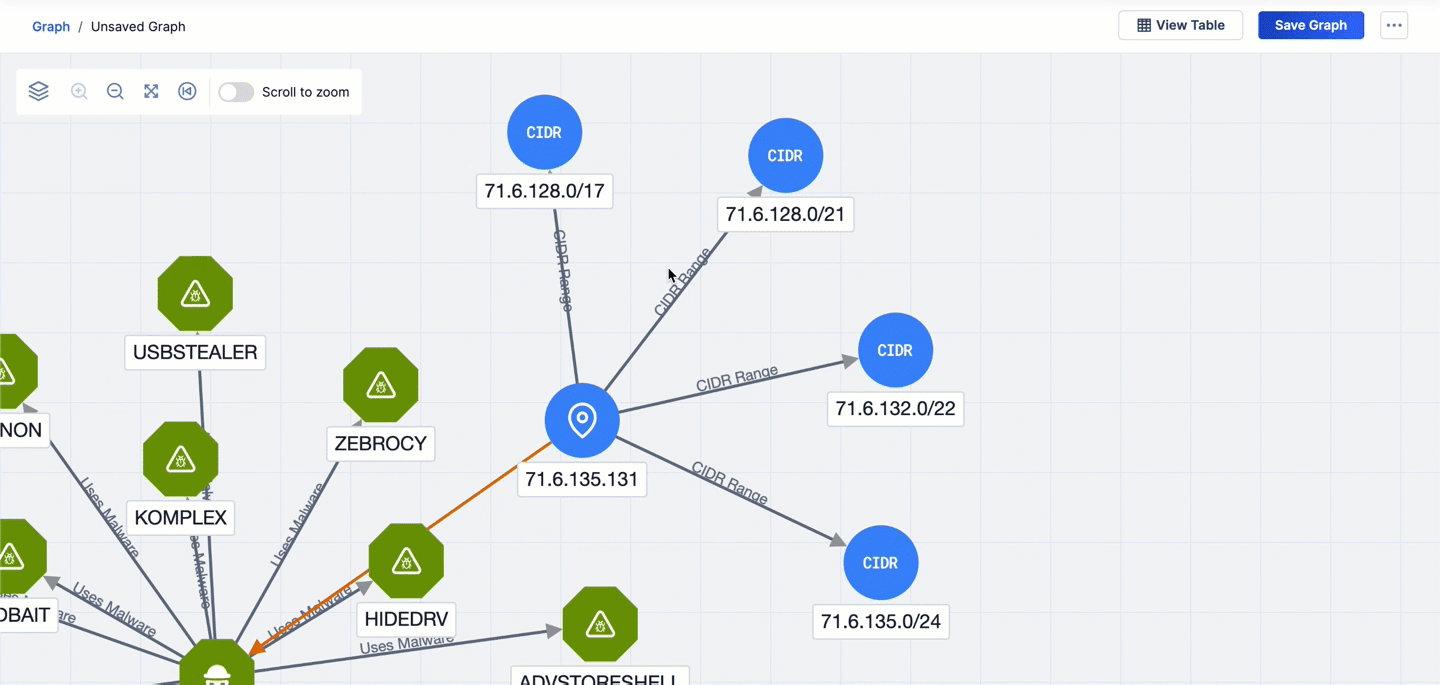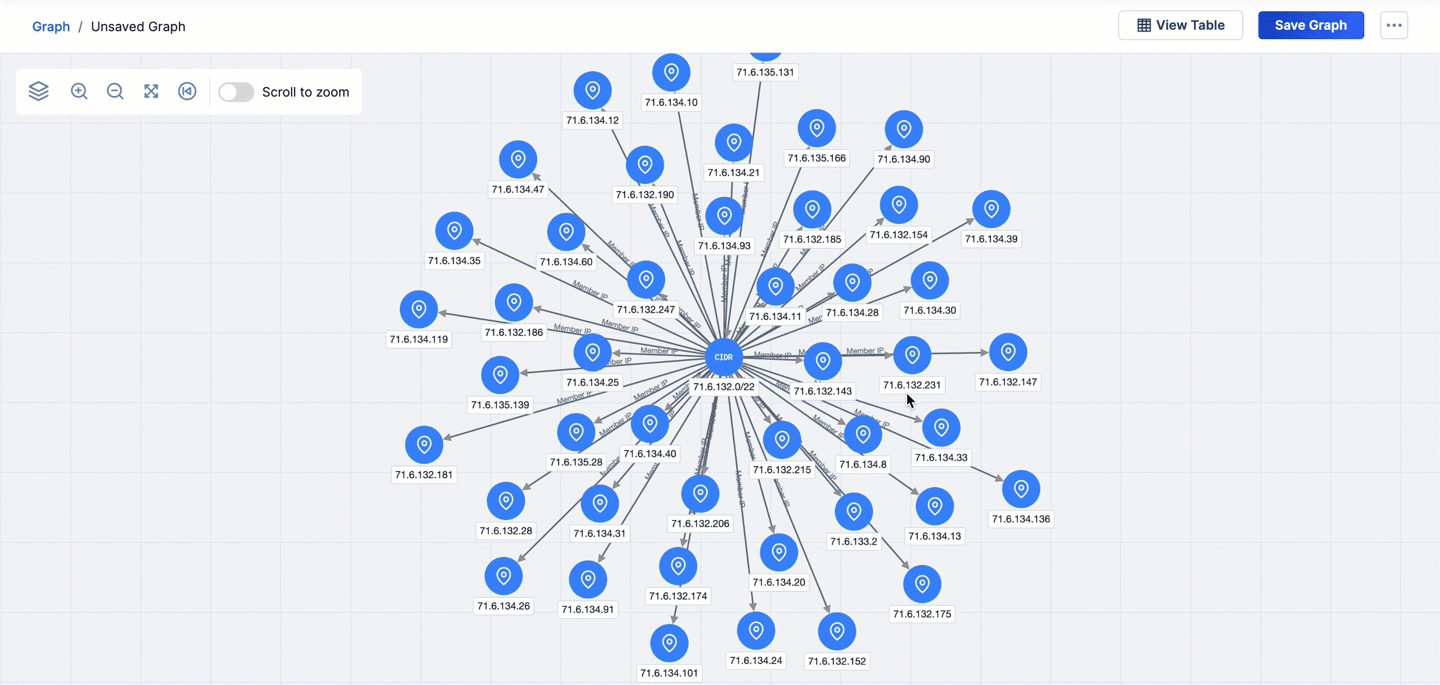
Figure 2 shows three pivots on CAL relationships in Threat Graph:
- The first pivot is on the Uses Malware CAL relationship from the Fancy Bear Adversary Group. This pivot returns 17 Malware Groups that are related to Fancy Bear and adds them to the graph.
- The second pivot is on the CIDR Ranges CAL relationship from the 71.6.135.131 Address Indicator. This pivot returns four CIDR Indicators that are related to 71.6.135.131 and adds them to the graph.
- The third pivot is on the Member IPs CAL relationship from the 71.6.132.0/22 CIDR Indicator that was added to the graph via the second pivot. This pivot returns 45 Address Indicators that are related to 71.6.132.0/22 and adds them to the graph.
Available CAL Relationships
Indicators
See Table 1 for a list of CAL relationships available in Threat Graph for Indicators.
| CAL Relationship Type | Starting Indicator Type(s) | Object Type Returned from Pivot |
|---|---|---|
| Base Host | URL | Host Indicator |
| Base URL | URL | URL Indicator |
| CIDR Ranges | Address, ASN | CIDR Indicator |
| DNS Resolutions | Host | Address |
| Email Host | Email Address | Host Indicator |
| Known ASNs | CIDR | ASN Indicator |
| Known Email Addresses | Host | Email Address Indicator |
| Known URL Extensions | URL | URL Indicator |
| Known URLs | Host | URL Indicator |
| Member IPs | CIDR | Address Indicator |
| Mentioned by Report | Address, ASN, CIDR, Email Address, File, Host, URL | Report Group |
| Nameserver Clients | Host | Host Indicator |
| Nameservers | Host | Host Indicator |
| Parent Domain | Host | Host Indicator |
| Registered Domains | Email Address | Host Indicator |
| Resolved Domains | Address | Host Indicator |
| Subdomains | Host | Host Indicator |
| WHOIS Registrants | Host | Email Address Indicator |
Groups
See Table 2 for a list of CAL relationships available in Threat Graph for Groups.
| CAL Relationship Type | Starting Group Type(s) | Group Type Returned from Pivot |
|---|---|---|
| Achieved By | Tactic | Attack Pattern |
| Achieves Tactic | Attack Pattern | Tactic |
| Contains Subtechnique | Attack Pattern | Attack Pattern |
| Mentioned by Report | Attack Pattern, Course of Action, Intrusion Set, Malware, Tactic, Tool, Vulnerability | Report |
| Mentions Attack Pattern | Report | Attack Pattern |
| Mentions Course of Action | Report | Course of Action |
| Mentions Intrusion Set | Report | Intrusion Set |
| Mentions Malware | Report | Malware |
| Mentions Tactic | Report | Tactic |
| Mentions Tool | Report | Tool |
| Mentions Vulnerability | Report | Vulnerability |
| Mitigated By | Attack Pattern | Course of Action |
| Mitigates Attack Pattern | Course of Action | Attack Pattern |
| Revoked By | Attack Pattern | Attack Pattern |
| Intrusion Set | Intrusion Set | |
| Malware | Malware | |
| Revokes | Attack Pattern | Attack Pattern |
| Intrusion Set | Intrusion Set | |
| Malware | Malware | |
| Subtechnique Of | Attack Pattern | Attack Pattern |
| Used by Intrusion Set | Attack Pattern | Intrusion Set |
| Used by Malware | Attack Pattern | Malware |
| Used by Tool | Attack Pattern, Intrusion Set | Tool |
| Uses Attack Pattern | Intrusion Set, Malware, Tool | Attack Pattern |
| Uses Malware | Intrusion Set | Malware |
Pivoting Behaviors
When using the Pivot with CAL option in Threat Graph, you may observe the following behaviors as you interact with and add nodes to the graph:
- If a pivot returns more than 500 related objects, only the first 500 related nodes and their respective connections will be added to the graph.
- If no CAL relationships exist for an Indicator or Group, the Pivot with CAL submenu will display a message stating so. Similarly, if an Indicator or Group does not exist in CAL, the Pivot with CAL submenu will display a message stating so.
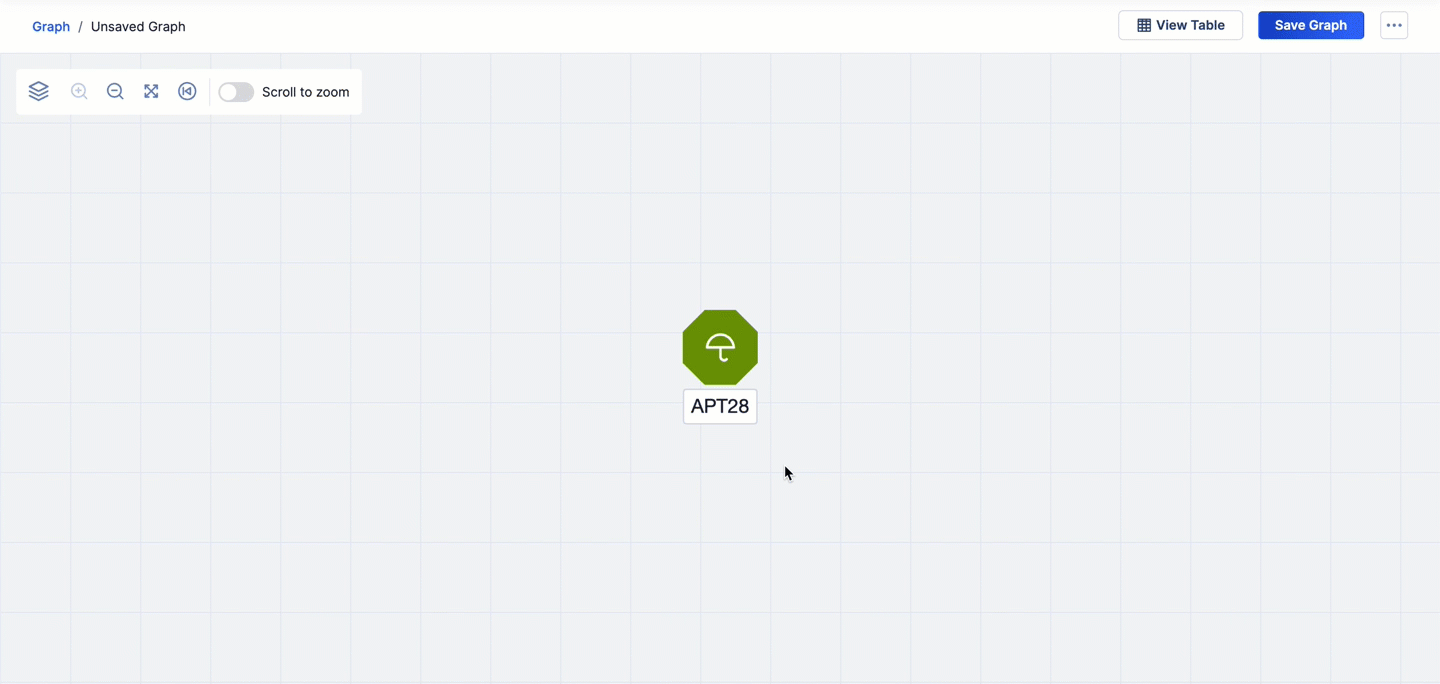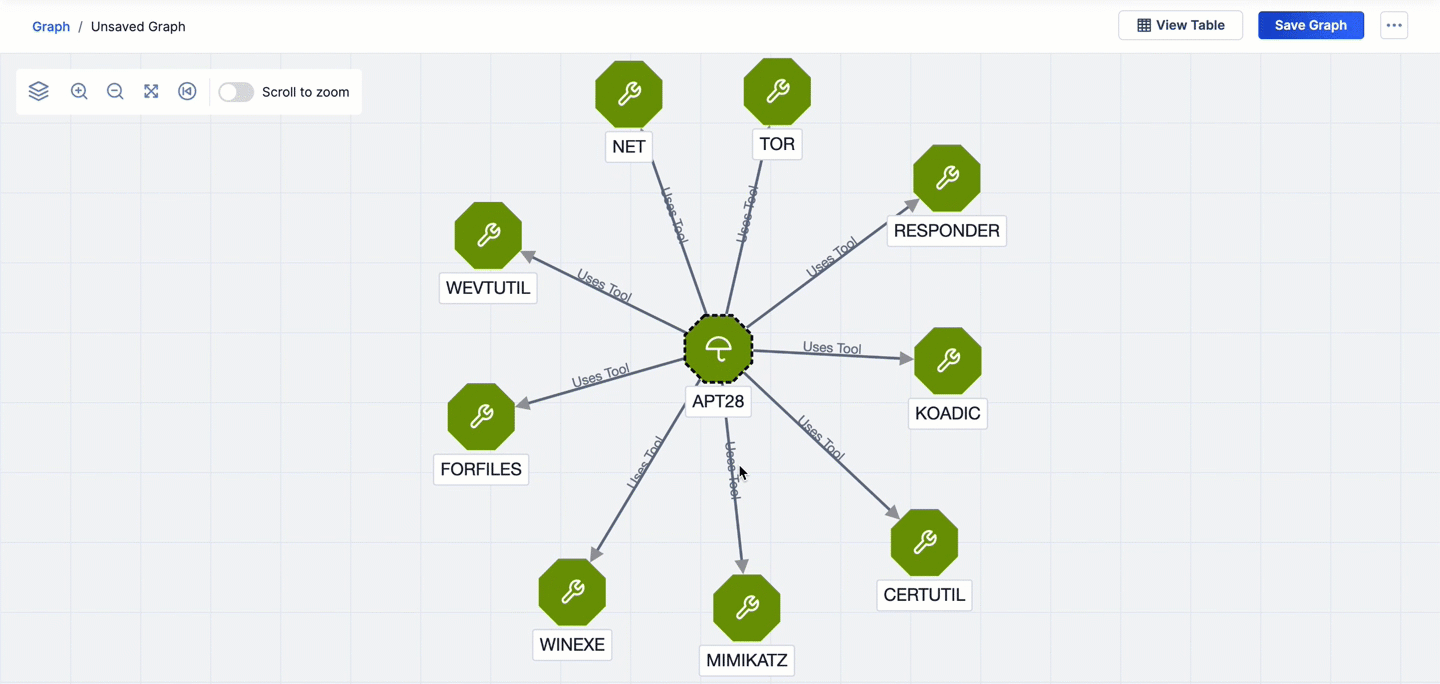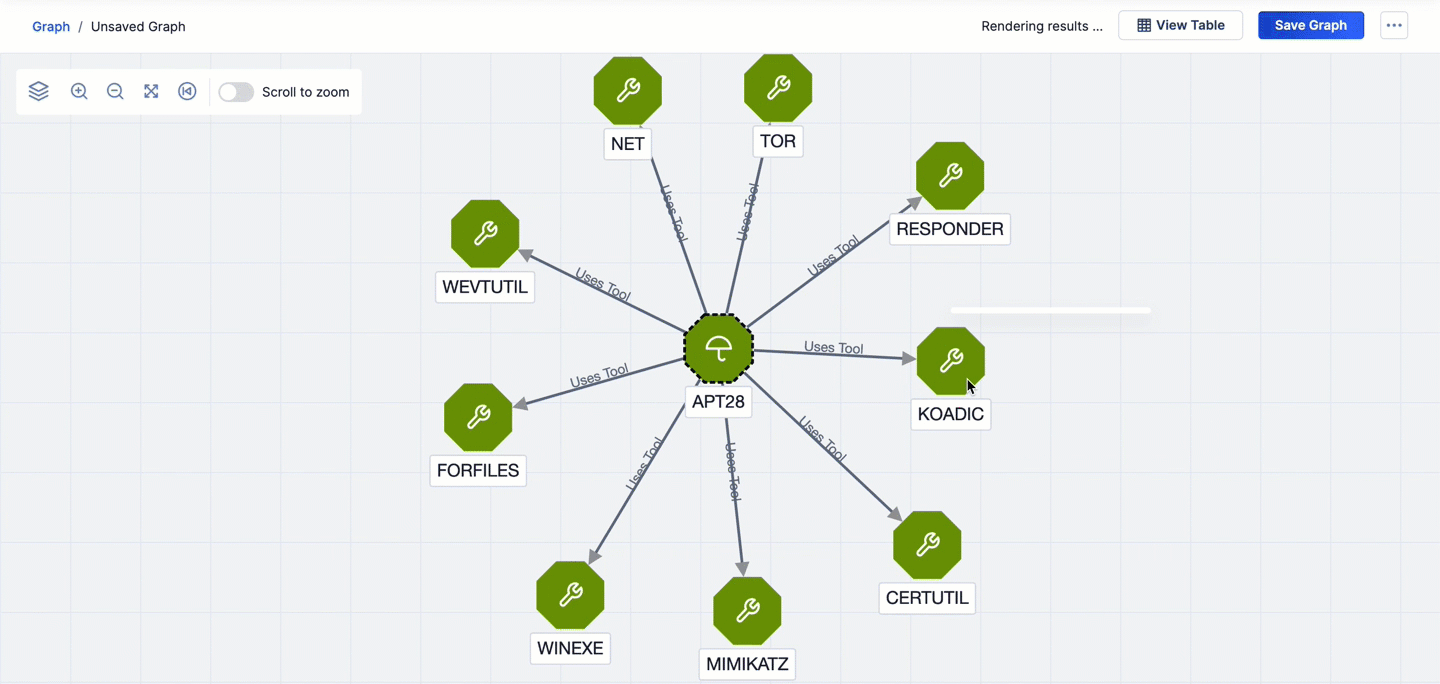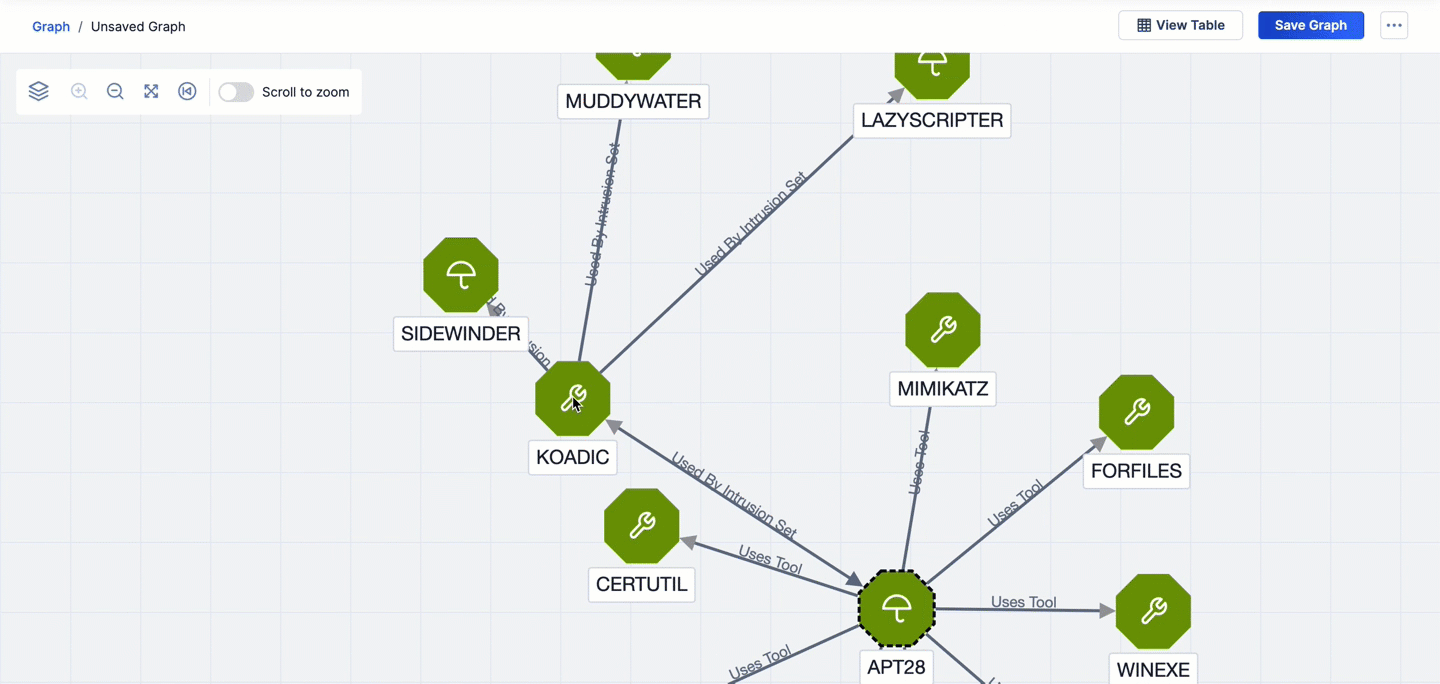
- If you pivot from one node to a second node and then pivot from the second node back to the first node, the arrow connecting the two nodes will change to a bidirectional arrow, and the arrow’s label will reflect the most recent CAL relationship type on which you pivoted. For example, in Figure 3, the first pivot is on the Uses Tool CAL relationship from the APT28 Intrusion Set Group. This pivot returns nine Tool Groups. The second pivot is on the Uses by Intrusion Set CAL relationship from the KODIAC Tool Group that was added to the graph via the first pivot. This pivot returns four related objects, one of which is the APT28 Intrusion Set already on the graph. As a result, the arrow connecting the APT28 Intrusion Set Group to the KODIAC Tool Group changes to a bidirectional arrow to reflect the pivot from KODIAC back to the APT28, and the connection label changes from Uses Tool to Used by Intrusion Set.
ThreatConnect® is a registered trademark, and CAL™ is a trademark, of ThreatConnect, Inc.
20117-13 v.02.A


