- 30 Aug 2025
- 11 Minutes to read
-
Print
-
DarkLight
-
PDF
ThreatConnect TAXII Ingest User Guide
- Updated on 30 Aug 2025
- 11 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The ThreatConnect® TAXII™ Ingest App ingests Structured Threat Information eXpression (STIX™) 2.1 threat intelligence objects from TAXII feeds into ThreatConnect. STIX threat intelligence objects are mapped to ThreatConnect data model objects in one of three ways:
- Using a generic base mapping
- Using a mapping specific to a particular TAXII feed
- Using your own custom mapping
The ThreatConnect TAXII Ingest App creates the following object types from the STIX objects it ingests:
- Indicators: Address, ASN, CIDR, Email Address, Email Subject, File, Host, and URL
- Groups: Adversary, Campaign, Intrusion Set, Report, and Threat
The ThreatConnect TAXII Ingest App can ingest data from any TAXII feed. It supports mappings specific to the following TAXII feeds: AlienVault®, FS-ISAC®, H-ISAC®, ND-ISAC®, ReversingLabs™, Space-ISAC, and VMRay®.
Dependencies
ThreatConnect Dependencies
- Active ThreatConnect Application Programming Interface (API) key
- ThreatConnect instance with 7.9.0 or newer installed
Other Dependencies
- Running third-party (e.g., AlienVault, FS-ISAC) TAXII 2.1 server feed
Application Setup and Configuration
Follow these steps to install the ThreatConnect TAXII Ingest App via TC Exchange™ and configure it for a TAXII feed:
- Log into ThreatConnect with a System Administrator account.
- From the Settings
 menu on the top navigation bar, select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen.
menu on the top navigation bar, select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen. - Locate the ThreatConnect TAXII Ingest App on the Catalog tab. Then click Install
 in the Options column to install the App.
in the Options column to install the App. - After you install the ThreatConnect TAXII Ingest App, the Feed Deployer will open automatically. Use the Feed Deployer to set up and configure the App for a single TAXII feed. See the “Configuration Parameters” section for more information on the parameters available during the configuration and deployment process.
Configuration Parameters
Parameter Definitions
The parameters defined in Table 1 apply to the configuration parameters available when using the Feed Deployer to configure the ThreatConnect TAXII Ingest App for a TAXII feed.
| Name | Description | Required? |
|---|---|---|
| Source Tab | ||
| Sources to Create | Enter the name of the Source for the feed. Important Replace the default name with the name of a Source that is not already being used by the ThreatConnect TAXII Ingest App for a different feed. It is recommended to use a name indicating the name of the TAXII feed from which you are ingesting data (e.g., ThreatConnect TAXII Ingest - AlienVault, ThreatConnect TAXII Ingest - ReversingLabs). | Required |
| Owner | Select the Organization in which the Source will be created. | Required |
| Activate Deprecation | Select this checkbox to allow confidence deprecation rules to be created and applied to Indicators in the Source. | Optional |
| Create Attributes | Select this checkbox to allow custom Attribute Types to be created in the Source. | Optional |
| Parameters Tab | ||
| Launch Server | Select tc-app as the launch server for the Service corresponding to the Feed API Service App. | Required |
| Discovery URL or API Root URL | The TAXII Server you are using to ingest data will have either a discovery URL or an API root URL. Enter the Discovery URL or API Root URL for the TAXII Server. | Required |
| Mapping | Select the mapping to apply to threat intelligence objects ingested from the TAXII feed into ThreatConnect. Note If using a specific TAXII feed, select the mapping for that feed. Otherwise, select Generic. Available options include the following:
| Required |
| Username | Enter the username for your user account with the TAXII feed. | Required |
| Password | Enter the password for your user account with the TAXII feed. | Required |
| Collection(s) | Enter a list of STIX Collection IDs to filter ingested data by. Separate each STIX Collection ID with a comma. If you do not enter any IDs, all data from all collections to which your TAXII feed user account has access will be ingested. Important Enter only the ID field, not the full URL, for each STIX Collection ID, such as in the following example: 812F3E4A-BCC2-49CD-9CD3-11F4E0C66A4F,7f9137a7-59ff-4fc6-957a-a90cc66c91b5 | Optional |
| STIX Types | Select the STIX threat intelligence object types to ingest from the TAXII feed. Available options include the following:
| Required |
| Revoked Action (Indicators) | Select the action that ThreatConnect should take when importing a revoked Indicator from the TAXII feed. Available options include the following:
| Required |
| Revoked Action (Groups) | Select the action that ThreatConnect should take when importing a revoked Group from the TAXII feed. Available options include the following:
| Required |
| Backfill Days | Enter the number of days of historical data that the ThreatConnect TAXII Ingest App will ingest from the TAXII feed when the App runs for the first time on that feed. | Optional |
| Confirm Tab | ||
| Run Feeds after deployment | Select this checkbox to run the ThreatConnect TAXII Ingest App immediately after the deployment configuration is complete (i.e., after you click DEPLOY on the Feed Deployer window). | Optional |
| Confirm Deployment Over Existing Source | This checkbox will be displayed if the Source entered in the Sources to Create field has previously been deployed to the Organization selected in the Owner dropdown on the Source tab. Select this checkbox to confirm that you want the ThreatConnect TAXII Ingest App to write data to the same Source. This process will create a new Service for the ThreatConnect TAXII Ingest App. As such, it is recommended that you delete the old Service associated with the ThreatConnect TAXII Ingest App after the new one is created. Important If you do not select this checkbox, the DEPLOY button will be grayed out, and you will not be able to deploy the Service. Return to the Source tab and enter a different Source or select a different Organization and then proceed through the tabs of the Feed Deployer window again. Important If the Run Feeds after deployment checkbox is displayed, the ThreatConnect TAXII Ingest App has already been deployed to the Source entered in the Sources to Create field on the Source tab. Ensure that this Source is specific to the feed for which you entered information in the Parameters tab. Do not deploy the ThreatConnect TAXII Ingest App to a Source that already exists and is being actively used for another deployment of this App. | Optional |
ThreatConnect TAXII Ingest UI
After successfully configuring and activating the Feed API Service, you can access the ThreatConnect TAXII Ingest user interface (UI) for the TAXII feed. This UI allows you to interact with and manage the ThreatConnect TAXII Ingest App.
Follow these steps to access the ThreatConnect TAXII Ingest UI for a TAXII feed:
- Log into ThreatConnect with a System Administrator account.
- From the Automation & Feeds menu on the top navigation bar, select Services.
- Locate and turn on the ThreatConnect TAXII Ingest Feed API Service for the TAXII feed.
- Click the link in the Service’s API Path field. The ThreatConnect TAXII Ingest UI will open in a new browser tab.
The following screens are available in the ThreatConnect TAXII Ingest UI:
Dashboard
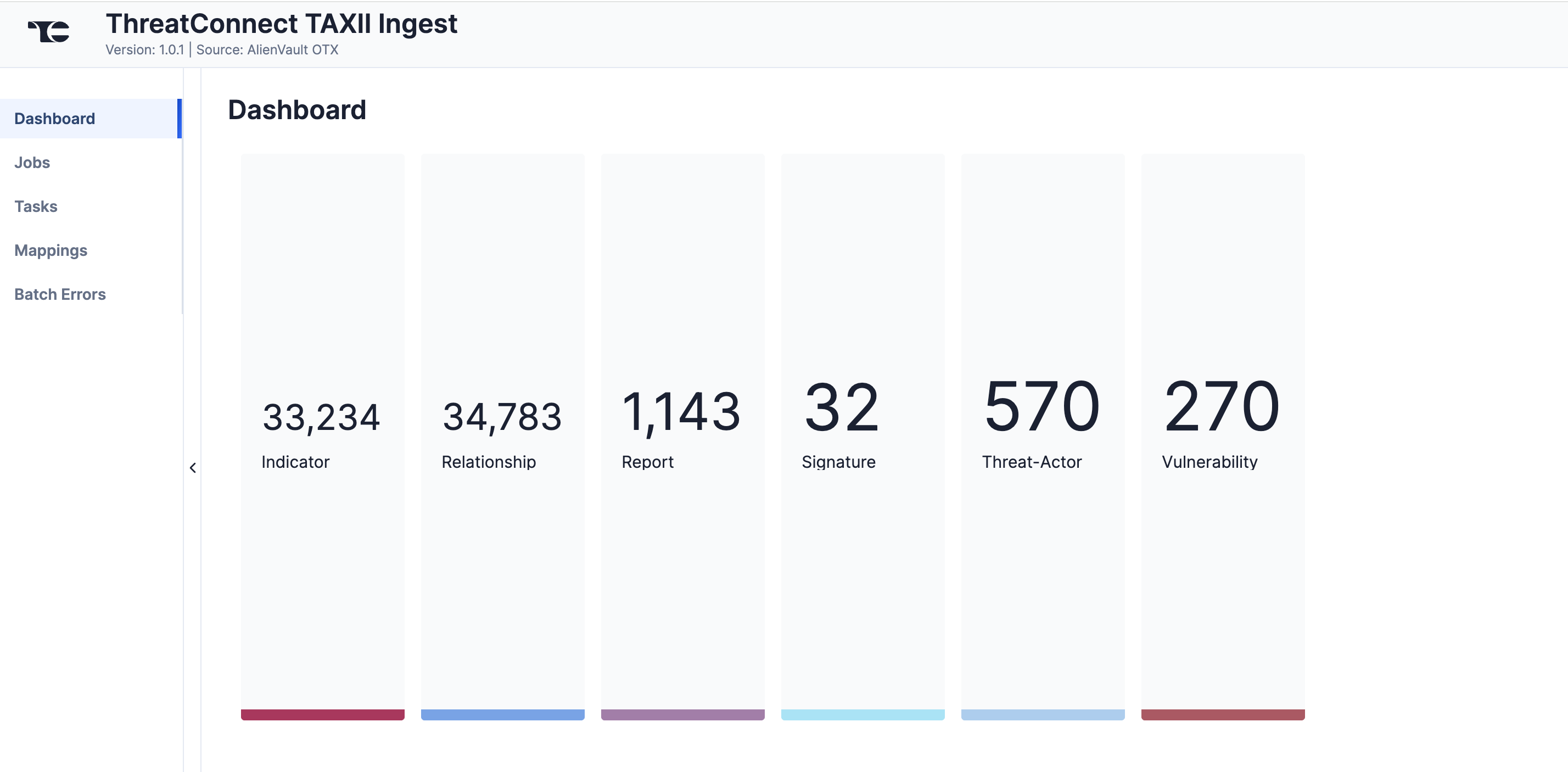
The Dashboard screen (Figure 1) provides an overview of the total number of Indicators, Groups, and Relationships ingested by the ThreatConnect TAXII Ingest App from the TAXII feed into ThreatConnect.
Jobs
The Jobs screen (Figure 2) breaks down the ingestion of ThreatConnect TAXII Ingest data into manageable Job-like tasks, displaying all processes that are pending, in progress, complete, and failed. The ⋯ menu in a Job’s row provides the following options:
- Details: View details for the Job, such as download, convert, and upload start and complete times and counts of downloaded and batched Groups and Indicators.
- Download Files: Download metadata files for all Jobs and data (convert, download, and upload) files for completed Jobs.
- Batch Errors: View errors that have occurred for the Job on the Batch Errors screen.
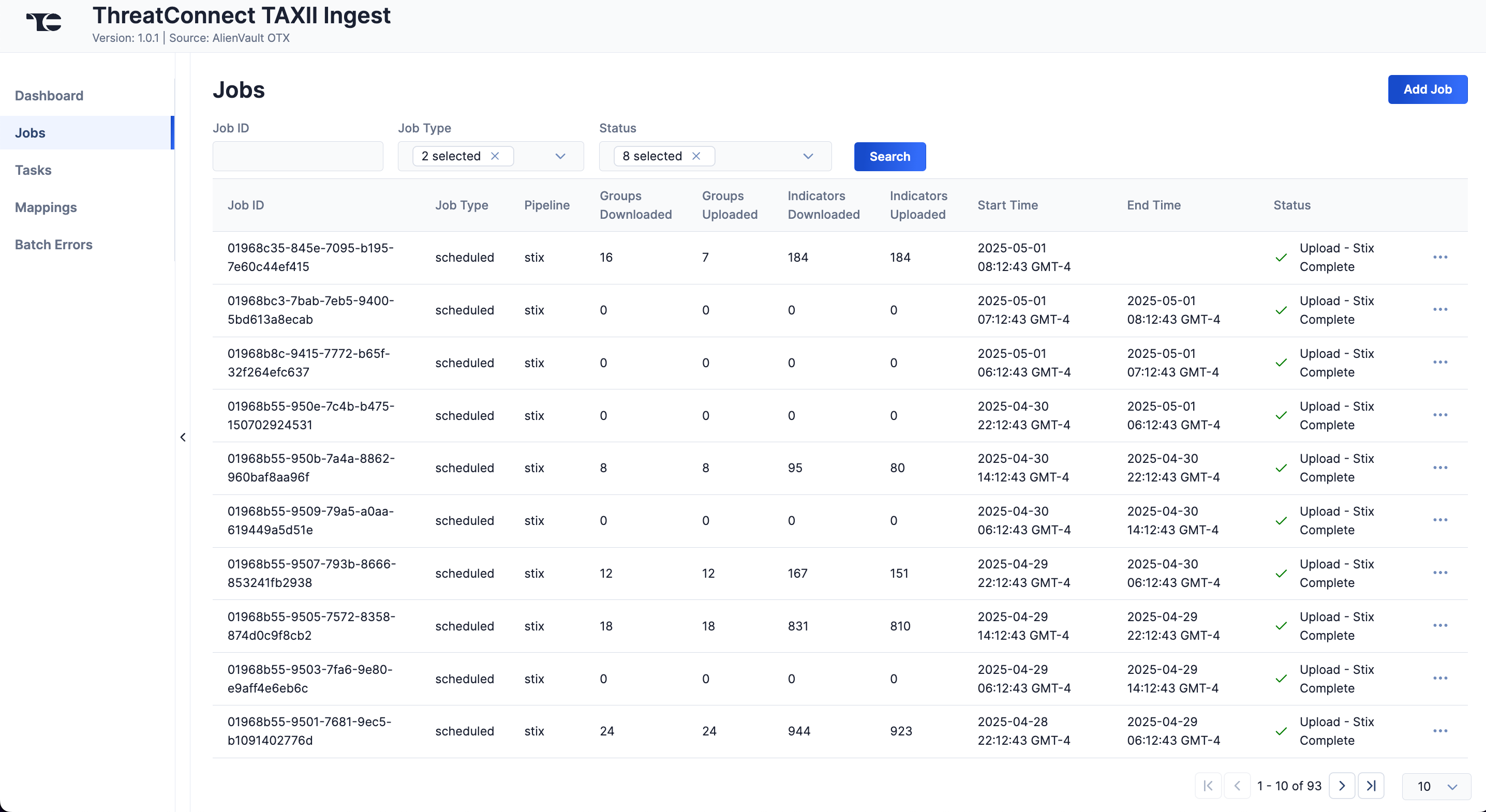
You can filter ThreatConnect TAXII Ingest App Jobs by the following elements:
- Job ID: Enter text into this box to search for a Job by its Job ID.
- Job Type: Select Job types to display on the Jobs screen.
- Status: Select Job statuses to display on the Jobs screen.
Add a Job
You can add ad-hoc Jobs on the Jobs screen. Follow these steps to create a request for an ad-hoc Job for the ThreatConnect TAXII Ingest App:
- Click Add Job (Figure 2).
- Fill out the fields on the Add Job drawer (Figure 3) as follows:
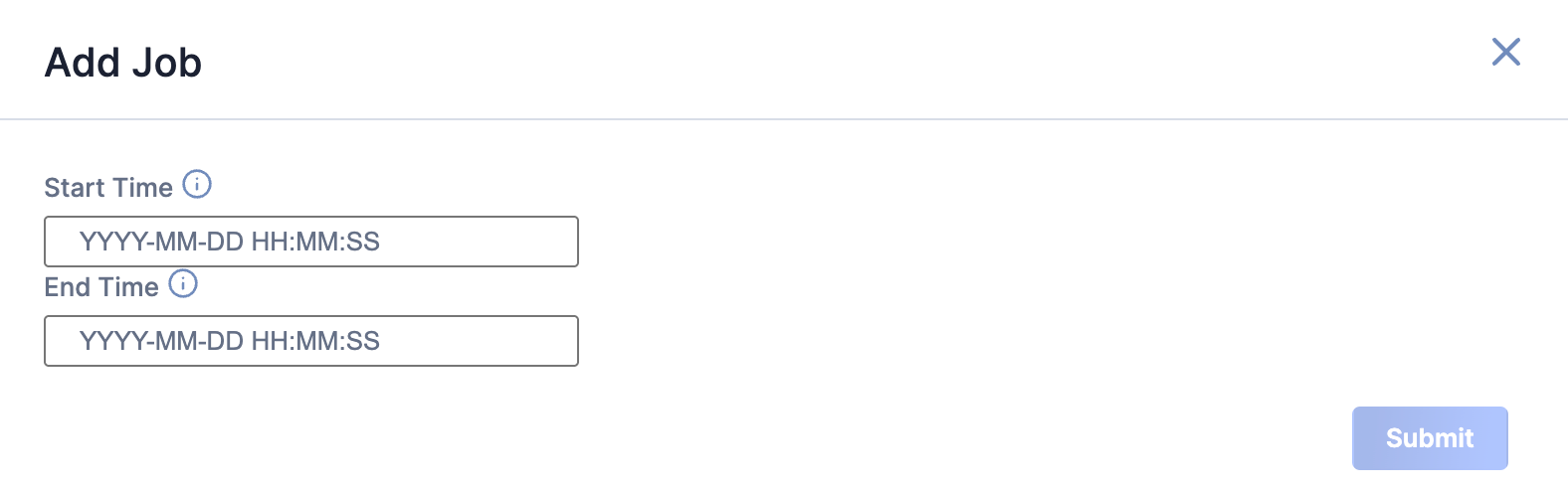
- Start Time: (Optional) Enter the time at which the Job should start.
- End Time: (Optional) Enter the time by which the Job should end.
- Click Submit to submit the request for the ad-hoc Job.
Tasks
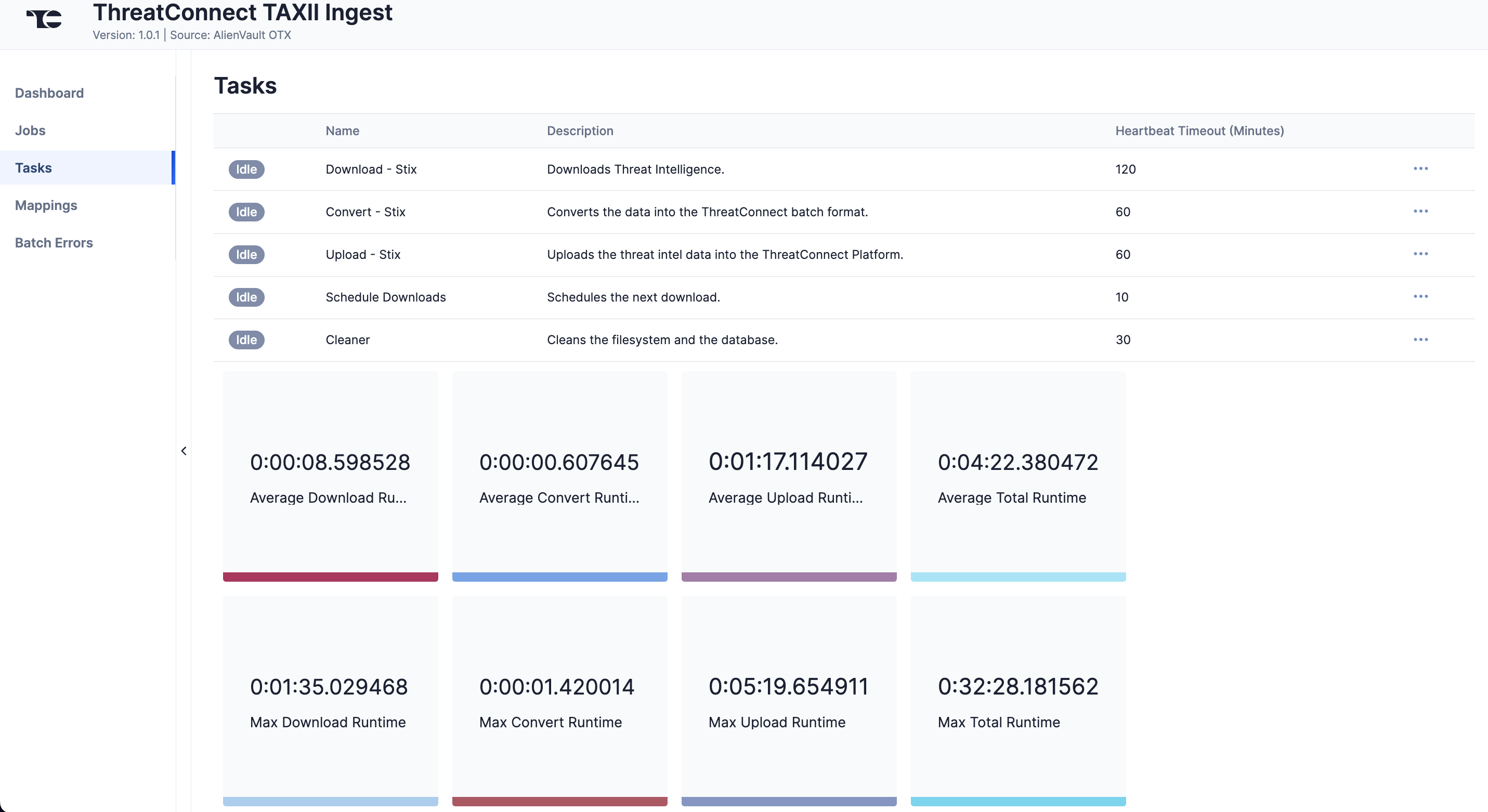
The Tasks screen (Figure 4) displays all Tasks that may be part of a Job, including each step of the download, convert, and upload processes, as well as Tasks for the ThreatConnect TAXII Ingest App, such as Monitor, Scheduler, and Cleaner. The current status (Idle, Paused, or Running), name, description, and heartbeat timeout length, in minutes, are displayed for each Task. The ⋯ menu in a Task’s row provides the following options, depending on the Task’s status:
- Run (idle and paused Tasks only)
- Pause (idle and running Tasks only)
- Resume (paused Tasks only)
- Kill (running Tasks only)
Under the table is a dashboard where you can view runtime analytics.
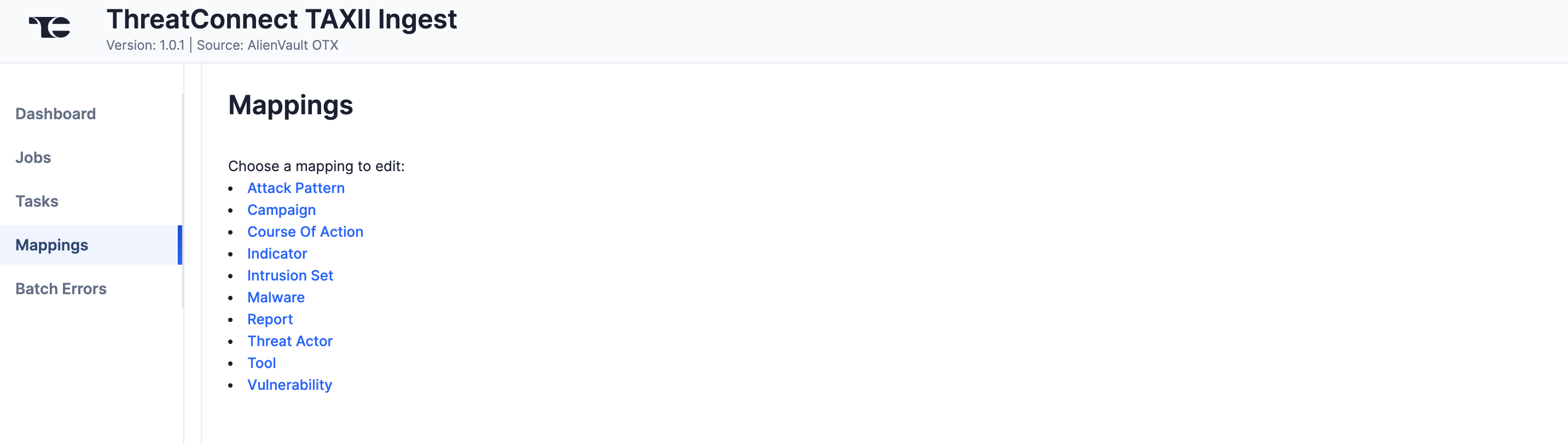
Mappings
The Mappings screen (Figure 5) displays links to the mappings for the each of the TAXI feed’s object types.
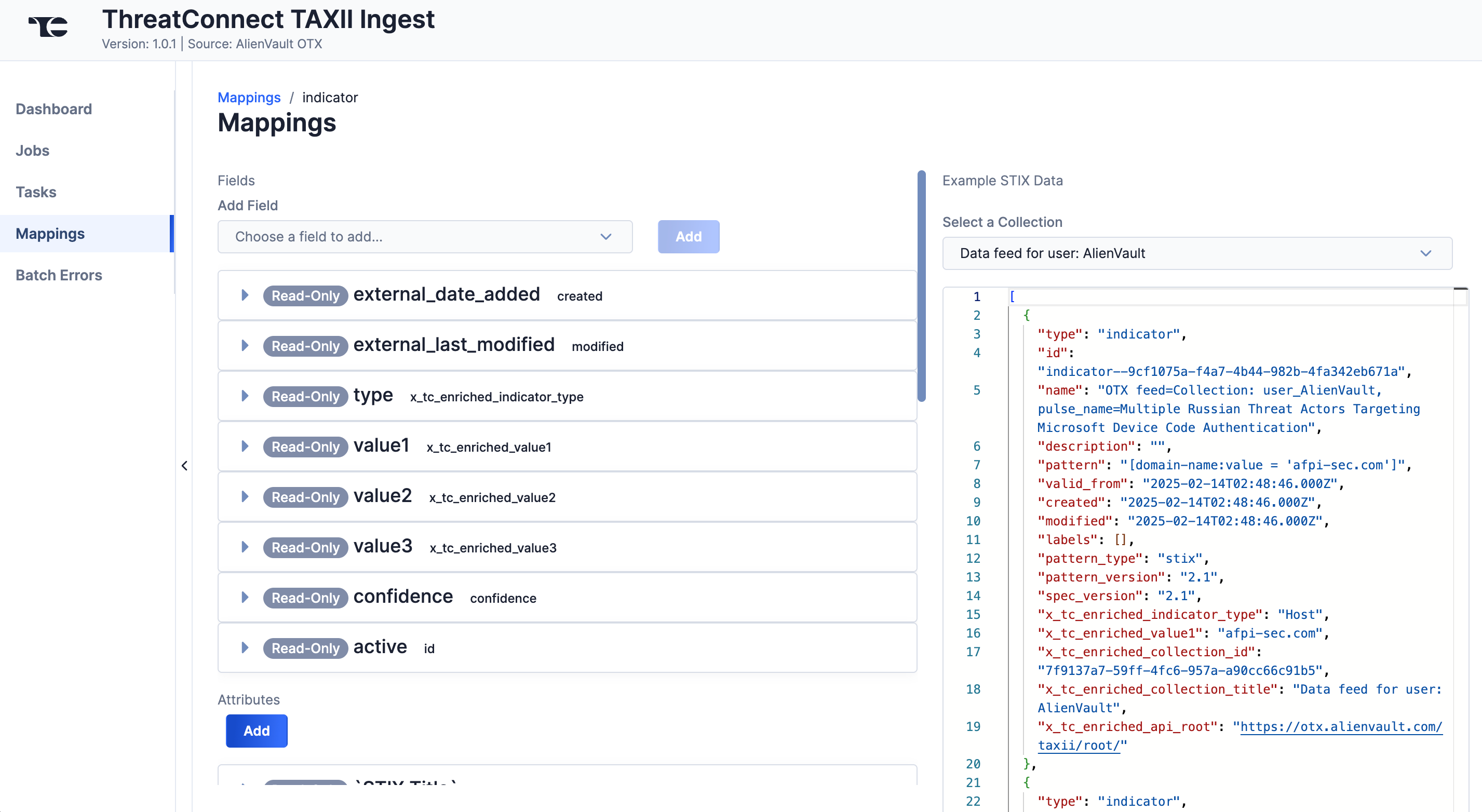
Select an object type to view its mappings for fields, Attributes, Tags, and Security Labels and example STIX data in JavaScript® Object Notation (JSON) format (Figure 6). Expand a mapping’s row to view its type (Attributes only) and value (all mapping types).
Custom Mappings
The ThreatConnect TAXII Ingest App allows you to create custom mappings, providing flexibility and control over how data are ingested.
Follow these steps to add a custom mapping in the ThreatConnect TAXII Ingest App:
- Click Add under the mapping type’s header (Attribute, Tag, and Security Label types), or select a Field from the Choose a field to add… dropdown and then click Add (Field type).NoteIf an object type does not support custom Fields, then the Choose a field to add… dropdown will be empty.
- Enter the type (Attributes only) and value (all mapping types) for the custom mapping in the new row at the bottom of the table for the mapping type.
- Click Confirm
 to save the custom mapping.NoteYou may edit and delete custom mappings. Read-only mappings may not be edited or deleted.
to save the custom mapping.NoteYou may edit and delete custom mappings. Read-only mappings may not be edited or deleted.
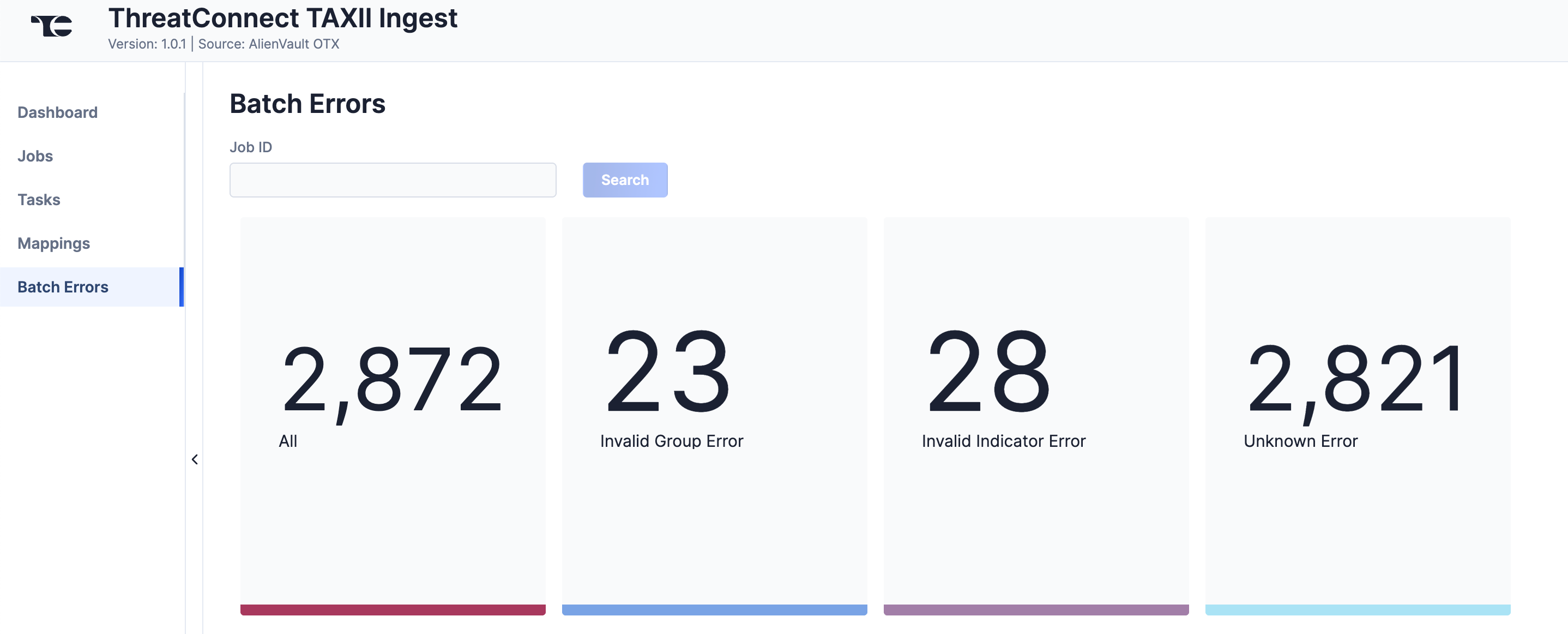
Batch Errors
The Batch Errors screen (Figure 7) displays an overview of the batch error types that have occurred for Job requests. You can enter keywords to filter by Job ID.
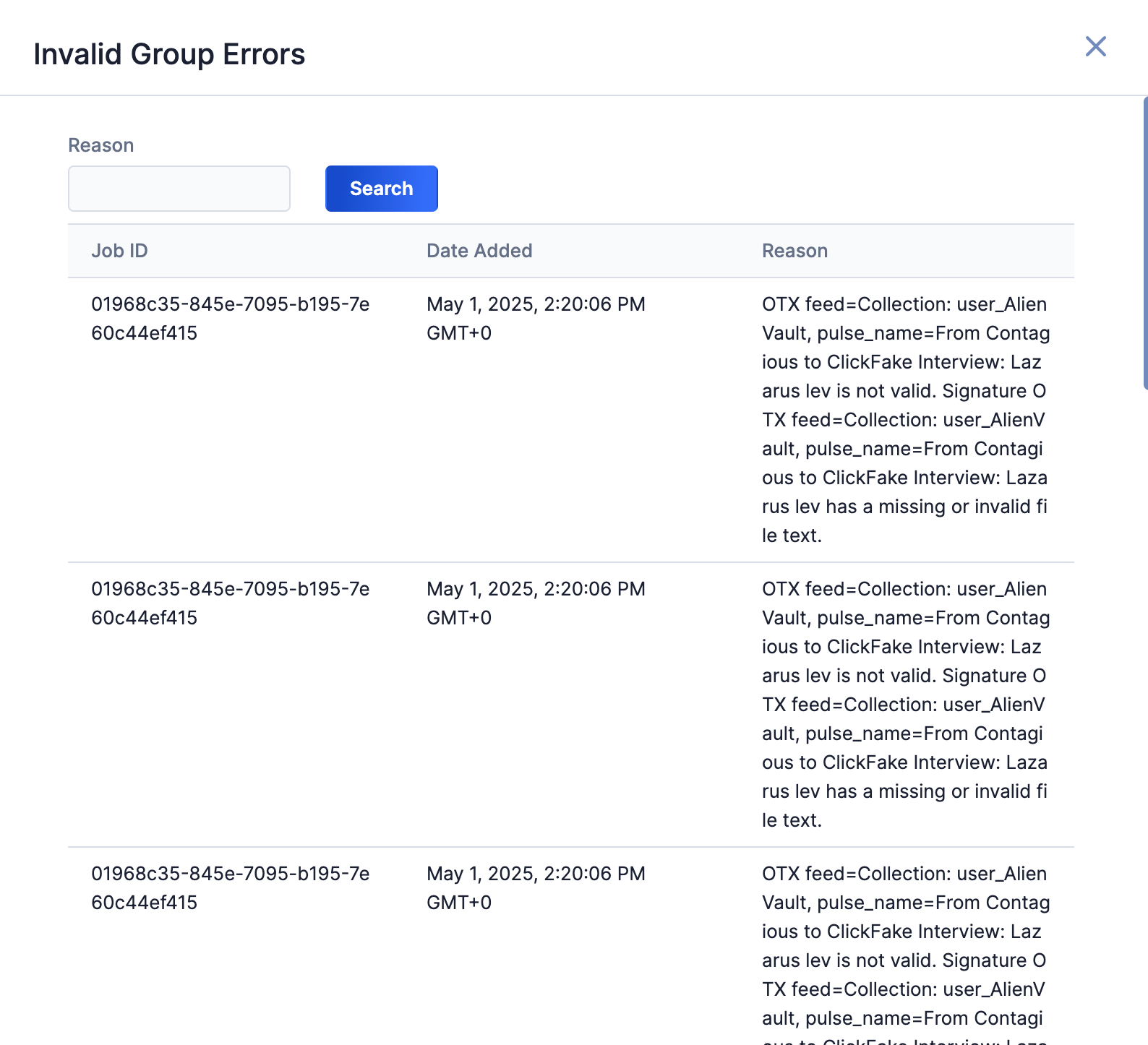
Click on an error type to open a drawer containing a table with details on all batch errors of that type (Figure 8). You can enter keywords to filter by reason for error.
Data Mappings
General Mappings
The data mappings in Table 2 through Table 11 illustrate how data are mapped from the STIX data model to the ThreatConnect data model.
Common Mapping
ThreatConnect object type: All ThreatConnect Group and Indicator object types
| STIX Property | ThreatConnect Field |
|---|---|
| name |
|
| description | Attribute: "Description" |
| id |
|
| confidence | Attribute: "STIX Confidence" |
| created | External Date Added |
| created_by_ref | Attribute: "STIX Created By Ref" |
| external_reference | ATT&CK Tags |
| labels | Tags |
| lang | Attribute: "STIX Lang" |
| modified | External Last Modified |
| object_marking_ref | Security Labels |
| revoked | Tag: "Revoked" |
| type | Attribute: "STIX Type" |
Attack Patterns
ThreatConnect object type: Attack Pattern Group
| STIX Property | ThreatConnect Field |
|---|---|
| aliases | Attribute: "Aliases" |
| kill_chain_phases | Attribute: "Phase of Intrusion" |
Campaigns
ThreatConnect object type: Campaign Group
| STIX Property | ThreatConnect Field |
|---|---|
| aliases | Attribute: "Aliases" |
| first_seen | First Seen |
| last_seen | Last Seen |
| objective | Attribute: "Campaign Objective" |
Courses of Action
ThreatConnect object type: Course of Action Group
| STIX Property | ThreatConnect Field |
|---|---|
| multi-field: <name>|<description>|<action_type> | Attribute: "Course of Action Recommendation" |
Intrusion Sets
ThreatConnect object type: Intrusion Set Group
| STIX Property | ThreatConnect Field |
|---|---|
| aliases | Attribute: "Aliases" |
| first_seen | First Seen |
| goals | Attribute: "Goals" |
| last_seen | Last Seen |
| primary_motivation | Attribute: "Adversary Motivation Type" |
| resource_level | Attribute: "Resource Level" |
| secondary_motivation | Attribute: "Secondary Motivation" |
Malware
ThreatConnect object type: Malware Group
| STIX Property | ThreatConnect Field |
|---|---|
| architecture_execution_envs | Attribute: "STIX Architecture Execution Envs" |
| aliases | Attribute: "Aliases" |
| capabilities | Attribute: "Capabilities" |
| first | First Seen |
| implementation_languages | Attribute: "STIX Implementation Languages" |
| is_family | Tag: "<Malware Family>" (if true) |
| kill_chain_phases | Attribute: "Phase of Intrusion" |
| last_seen | Last Seen |
| malware_types | Attribute: "Malware Type" |
| operating_system_refs | Attribute: "STIX Operating System Refs" |
Reports
ThreatConnect object type: Report Group
| STIX Property | ThreatConnect Field |
|---|---|
| object_refs | Associations |
| published | Publish Date |
| report_types | Attribute: "Report Type" |
Signatures
ThreatConnect object type: Signature Group
| STIX Property | ThreatConnect Field |
|---|---|
| id | File Name |
| indicator_types | Attribute: "STIX Indicator Type" |
| name|pattern|id | File Type |
| pattern | File Content |
| pattern_version | Attribute: "STIX Pattern Version" |
| valid_from | Attribute: "STIX Valid From" |
| valid_until | External Date Expires |
Threat Actors
ThreatConnect object type: Adversary Group
| STIX Property | ThreatConnect Field |
|---|---|
| aliases | Attribute: "Aliases" |
| first_seen | First Seen |
| goals | Attribute: "Goals" |
| last_seen | Last Seen |
| personal_motivation | Attribute: "Personal Motivation" |
| primary_motivation | Attribute: "Adversary Motivation Type" |
| resource_level | Attribute: "Resource Level" |
| roles | Attribute: "Roles" |
| secondary_motivation | Attribute: "Secondary Motivation" |
| sophistication | Attribute: "Sophistication" |
| threat_actor_types | Attribute: "Adversary Type" |
Tools
ThreatConnect object type: Tool Group
| STIX Property | ThreatConnect Field |
|---|---|
| aliases | Attribute: "Aliases" |
| kill_chain_phases | Attribute: "Phase of Intrusion" |
| tool_types | Attribute: "Malicious Tool Variety" |
| tool_version | Attribute: "Malicious Tool Version" |
Special Mappings
STIX Indicator Patterns
STIX Indicator patterns vary in complexity. Atomic indicators, like a single IP address or file hash, are simple and direct—they match a specific value and are easy to process. In contrast, complex patterns can involve multiple conditions, logical operators (e.g., AND, OR), temporal relationships (e.g., events happening within a time window), and behavioral indicators that describe how an attacker operates rather than what they use. The ThreatConnect TAXII Ingest App ingests atomic indicators as their corresponding ThreatConnect Indicator type. It ingests more complex patterns as Signature Groups of the STIX Pattern type.
STIX Relationships
STIX relationships are captured as object_refs on a STIX Report object and from STIX Relationship Objects (SROs). The ThreatConnect TAXII Ingest App creates these relationships as associations in ThreatConnect, including the following types of custom Indicator-to-Indicator associations:
- Address to Indicators
- Email Address to Indicators
- File to Indicators
- Host to Indicators
- URL to Indicators
ThreatConnect® is a registered trademark, and TC Exchange™ is a trademark, of ThreatConnect, Inc.
AlienVault® is a registered trademark of AlienVault, Inc.
FS-ISAC® is a registered trademark of FS-ISAC, Inc.
STIX™ and TAXII™ are trademarks of The MITRE Corporation.
ND-ISAC® is a registered trademark of National Defense Information Sharing and Analysis Center.
H-ISAC® is a registered trademark of NH-ISAC, Inc.
JavaScript® is a registered trademark of Oracle Corporation.
ReversingLabs™ is a trademark of ReversingLabs International GmbH.
VMRay® is a registered trademark of VMRay GmbH.
30092-01 EN Rev. B


