- 12 Sep 2024
- 14 Minutes to read
-
Print
-
DarkLight
-
PDF
Mandiant Advantage Threat Intelligence Engine Integration Configuration Guide
- Updated on 12 Sep 2024
- 14 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The Mandiant® Advantage Threat Intelligence Engine integration with ThreatConnect® lets you ingest Mandiant Advantage Threat Intelligence Reports, Indicators, Actors, Campaigns, Events, Malware, Signatures, Tools, and Vulnerabilities into ThreatConnect seamlessly. It uses ATT&CK® Tags in ThreatConnect to represent Mandiant Attack Patterns, allowing you to interact with Mandiant data in ThreatConnect’s ATT&CK Visualizer. Finally, it ingests Mandiant Campaigns as Event Groups in ThreatConnect in order to represent each timeline object of a Campaign, enabling you to use Threat Graph to visualize a Campaign and its timeline interactively.
Dependencies
ThreatConnect Dependencies
- Active ThreatConnect Application Programming Interface (API) key
- ThreatConnect instance with version 7.2.0 or newer installed
Mandiant Dependencies
- Active Mandiant Advantage Threat Intelligence subscription that provides access to an API key
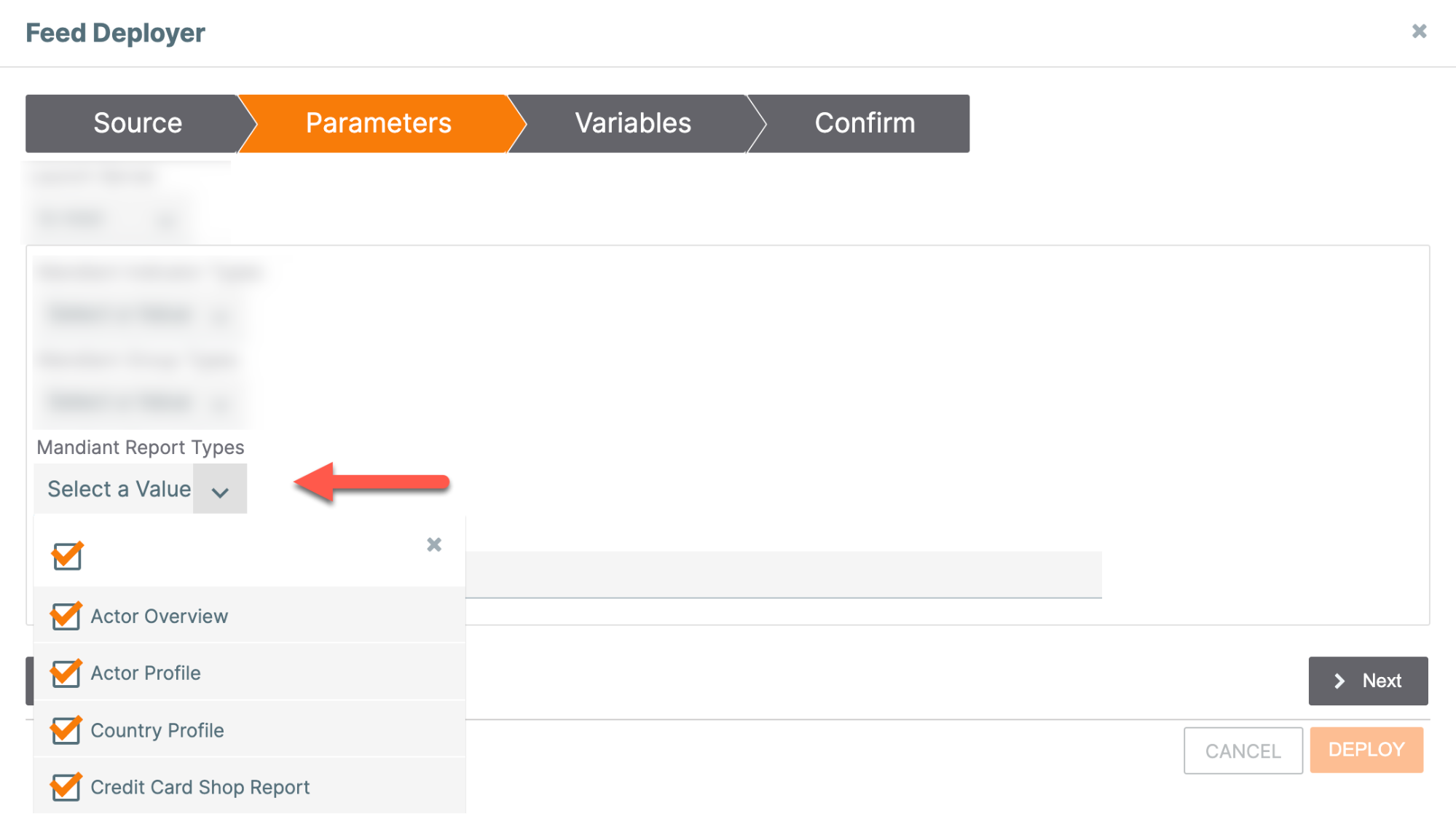
- To process and ingest all Mandiant Reports, an active Mandiant Advantage Threat Intelligence subscription to Fusion Reports is required. If you do not have a subscription to Fusion Reports and select any of the checkboxes available for the Mandiant Report Types parameter when configuring the integration (Figure 1), the Mandiant Advantage Threat Intelligence App will not start and run. Therefore ensure all checkboxes for the Mandiant Report Types parameter are cleared when configuring and deploying the App if you do not have a subscription to Fusion Reports.
Application Setup and Configuration
Follow these steps to install the Mandiant Advantage Threat Intelligence Engine App via TC Exchange™:
- Log into ThreatConnect as a System Administrator.
- Hover over Settings
 on the top navigation bar and select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen.
on the top navigation bar and select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen. - Locate the Mandiant Advantage Threat Intelligence Engine App on the Catalog tab. Then click Install
 in the Options column to install the App.
in the Options column to install the App. - After you install the Mandiant Advantage Threat Intelligence Engine App, the Feed Deployer will open automatically. Use the Feed Deployer to set up and configure the App. See the “Configuration Parameters” section for more information on the parameters available during the configuration and deployment process.
Upgrade Recommendations
If you installed version 1.0.x of the Mandiant Advantage Threat Intelligence Engine App previously, there are two ways to upgrade to version 2.0.x of the App:
- Option 1: Upgrade using the same Source that the previous version of the App uses
- Option 2: Upgrade using a new Source (recommended)
Option 1: Upgrade Using the Same Source the Previous Version of the App Uses
Using the same Source that the previous version of the Mandiant Threat Intelligence Engine App uses is best if you want to consolidate Mandiant data into a single Source in ThreatConnect and simplify where you need to look to find Mandiant data. However, having a single Source for Mandiant data created by versions 1.0.x and 2.0.x of the Mandiant Advantage Threat Intelligence Engine App will result in the Source containing two variations of Indicators and Groups that look different, as the data created by each version of the App will have differing content. Also, Indicators and Groups created by version 2.0.x of the App tend to have more data than the ones created by version 1.0.x of the App.
Upgrade Steps (Same Source)
To upgrade the Mandiant Advantage Threat Intelligence Engine App, you must be a System Administrator.
Step 1: Install Version 2.0.x
Follow these steps to install version 2.0.x of the Mandiant Advantage Threat Intelligence Engine App via TC Exchange:
- Hover over Settings
 on the top navigation bar and select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen.
on the top navigation bar and select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen. - Locate the Mandiant Advantage Threat Intelligence Engine App on the Catalog tab and confirm that its version number is 2.0.x. Then click Install
 in the Options column to install the App.
in the Options column to install the App.
Step 2: Turn Off the Service for Version 1.0x
Follow these steps to turn off the Service associated with version 1.0.x of the Mandiant Advantage Threat Intelligence Engine App:
- Hover over Playbooks on the top navigation bar and select Services.
- Locate the Mandiant Advantage Threat Intelligence Engine Feed API Service on the Services screen (i.e., the Service for version 1.0.x of the Mandiant Advantage Threat Intelligence Engine App), and then turn off the Feed Service toggle in the Type column.
Step 3: Deploy Version 2.0x
Follow these steps to deploy version 2.0.x of the Mandiant Advantage Threat Intelligence Engine App:
- Hover over Settings
 on the top navigation bar and select TC Exchange Settings. Then select the Installed tab on the TC Exchange Settings screen.
on the top navigation bar and select TC Exchange Settings. Then select the Installed tab on the TC Exchange Settings screen. - Locate the Mandiant Advantage Threat Intelligence Engine App on the Installed tab and confirm that its version number is 2.0.x. Then click ⋮ in the Options column and select Deploy.
- Use the Feed Deployer to set up and configure the Mandiant Advantage Threat Intelligence Engine App, ensuring that you use the same Source name that version 1.0.x of the App uses. See the “Configuration Parameters” section for more information on the parameters available during the configuration and deployment process.
Step 4: Validate Functionality for Version 2.0x
Follow these steps to verify that version 2.0.x of the Mandiant Advantage Threat Intelligence Engine App is functioning properly after it has been installed and deployed:
- Hover over Playbooks on the top navigation bar and select Services.
- Locate the Mandiant Advantage Threat Intelligence Engine Feed API Service on the Services screen associated with version 2.0.x of the Mandiant Advantage Threat Intelligence App.
- Confirm that the Service’s Memory Usage and CPU Usage values are positive and the Errors count is 0 (Figure 2).

Step 5: Delete the Service for Version 1.0x
Follow these steps to delete the Service associated with version 1.0.x of the Mandiant Advantage Threat Intelligence Engine App:
- Hover over Playbooks on the top navigation bar and select Services.
- Locate the Mandiant Advantage Threat Intelligence Engine Feed API Service on the Services screen that you turned off in the “Step 2: Turn Off the Service for Version 1.0.x” section, click ⋮ in the Options column, and select Delete.
Outcome and Expected Behavior
Version 2.0.x of the Mandiant Advantage Threat Intelligence Engine App will add data to the existing Source using new data mappings. Consequently, the threat intelligence data objects in the Source will have mixed mappings. For instance, Indicators and Groups created by version 1.0.x of the App will not share the same Tags and Attributes as those created by version 2.0.x of the App. Be aware of this when reviewing the Source to avoid confusion over data discrepancies.
Option 2: Upgrade Using a New Source (Recommended)
Using a new Source is the recommended upgrade option because it provides a cleaner and more consistent data experience by keeping data created by version 2.0.x of the Mandiant Advantage Threat Intelligence Engine App separate from data created by version 1.0.x of the App.
Upgrade Steps (Same Source)
To upgrade the Mandiant Advantage Threat Intelligence Engine App, you must be a System Administrator.
Step 1: Install Version 2.0.x
Follow these steps to install version 2.0.x of the Mandiant Advantage Threat Intelligence Engine App via TC Exchange:
- Hover over Settings
 on the top navigation bar and select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen.
on the top navigation bar and select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen. - Locate the Mandiant Advantage Threat Intelligence Engine App on the Catalog tab and confirm that its version number is 2.0.x. Then click Install
 in the Options column to install the App.
in the Options column to install the App.
Step 2: Deploy Version 2.0x
After you install version 2.0.x of the Mandiant Advantage Threat Intelligence Engine App, the Feed Deployer will open automatically. Use the Feed Deployer to set up and configure the App, ensuring that you use a Source name that is different from the one that version 1.0.x of the App uses (e.g., Mandiant Advantage Threat Intelligence 2). See the “Configuration Parameters” section for more information on the parameters available during the configuration and deployment process.
Step 3: Validate Functionality for Version 2.0x
Follow these steps to verify that version 2.0.x of the Mandiant Advantage Threat Intelligence Engine App is functioning properly after it has been installed and deployed:
- Hover over Playbooks on the top navigation bar and select Services.
- Locate the Mandiant Advantage Threat Intelligence Engine Feed API Service on the Services screen associated with version 2.0.x of the Mandiant Advantage Threat Intelligence App.
- Confirm that the Service’s Memory Usage and CPU Usage values are positive and the Errors count is 0 (Figure 2).
Step 4: Delete the Service for Version 1.0x
Follow these steps to delete the Service associated with version 1.0.x of the Mandiant Advantage Threat Intelligence Engine App:
- Hover over Playbooks on the top navigation bar and select Services.
- Locate the Mandiant Advantage Threat Intelligence Engine Feed API Service on the Services screen associated with version 1.0.x of the Mandiant Advantage Threat Intelligence Engine App, click ⋮ in the Options column, and select Delete.
Outcome and Expected Behavior
All downstream integrations that utilize Mandiant data must be updated to use the new Source containing the threat intelligence data objects created by the new version of the Mandiant Advantage Threat Intelligence Engine App. The Source containing data from the previous version of the App can be retained until it is no longer needed, and then it can be removed. All data in the new Source will adhere to the updated data mappings included in version 2.0.x of the App.
Configuration Parameters
Parameter Definitions
The parameters defined in Table 1 apply to the configuration parameters available when using the Feed Deployer to configure the Mandiant Advantage Threat Intelligence Engine App.
| Name | Description | Required? |
|---|---|---|
| Source Tab | ||
| Source to Create | Enter the name of the Source to be created in ThreatConnect. | Required |
| Owner | Select the Organization in which the Source will be created in ThreatConnect. | Required |
| Activate Deprecation | Select this checkbox to allow the creation of depreciation rules for Indicators in the Source. | Optional |
| Create Attributes | Select this checkbox to allow the creation of custom Attribute Types in the Source. | Optional |
| Parameters Tab | ||
| Launch Server | Select tc-job as the launch server for the Service corresponding to the Feed API Service App. | Required |
| Mandiant Indicator Types | Select the Indicator type(s) to import from Mandiant. It is recommended to select all Indicator types. Available options include the following:
| Required |
| Mandiant Group Types | Select the Group type(s) to import from Mandiant. It is recommended to select all Group types. Available options include the following:
| Required |
| Mandiant Report Types | Select the Report type(s) to import from Mandiant. It is recommended to select all Report types only if you have an active Mandiant Advantage Threat Intelligence subscription to Fusion Reports. Otherwise, do not select any Report types. Available options include the following:
| Required |
| Minimum Threat Score Filter | Enter the minimum Mandiant Indicator Threat Score that Indicators in Mandiant must have in order to be imported into ThreatConnect. The default value is 60. Mandiant Indicator Threat Score represents the genuine level of threat an Indicator presents to an organization. For more information on Mandiant Indicator Threat Score, see https://docs.mandiant.com/home/mati-indicator-threat-score-methodology (must have a valid Mandiant account to view this documentation). | Required |
| Exclude OSINT | Select this checkbox to prevent open-source intelligence (OSINT) from being imported into ThreatConnect. By default, this checkbox is selected. | Required |
| Variables Tab | ||
| Mandiant Advantage API Public | Enter the Mandiant Advantage Threat Intelligence ID. | Required |
| Mandiant Advantage API Secret | Enter the Mandiant Advantage Threat Intelligence API secret key. | Required |
Data Mappings
The data mappings in Table 2 through Table 9 illustrate how data are mapped from Mandiant API endpoints into the ThreatConnect data model.
Actors (From Threat-Actors Endpoint)
ThreatConnect object type: Intrusion Set Group
| Mandiant API Field | ThreatConnect Field |
|---|---|
| name |
|
| description | Attribute: "Description" (default) |
| id | Attribute: "External ID" |
| aliases[*].name | Attribute: "Aliases" (newline delimited) |
| last_updated | Attribute: "External Date Last Modified" |
| motivations[*].name | Attribute: "Adversary Motivation Type" |
| industries[*].name | Attribute: "Targeted Industry Sector" |
| observed[*].earliest (confirmed) | Attribute: "First Seen" (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| malware[*].id | Associated Malware Group |
| malware[*].name | Tag: "Malware: %name%" |
| locations.source.region.name | Attribute: "Source Region" |
| locations.source.sub_region.name | Attribute: "Source Sub Region" |
| location.source.country.iso2 | Attribute: "Source Country Code" |
| locations.target[*].iso2 | Attribute: "Target Country Code" |
| locations.target[*].target_region | Attribute: "Target Region" |
| locations.target[*].target_sub-region | Attribute: "Target Sub Region" |
| cve[*].id | Associated Vulnerability Group |
| cve[*].name | Tag: "Vulnerability: %name%" |
| associated_uncs[*].id | Associated Intrusion Set Group |
| last_activity_time | Attribute: "Last Seen" |
| tools.id | Associated Tool Group |
| tools.name | Tag: "Tool: %name%" |
| attack_patterns.{attack_pattern_id}.attack_pattern_identifier | ATT&CK Tag |
Indicators (From Indicators Endpoint)
ThreatConnect object type: Indicator (Address, File, Host, or URL)
| Mandiant API Field | ThreatConnect Field |
|---|---|
| id | Attribute: "External ID" |
| value | Indicator Value |
| first_seen | Attribute: "First Seen" |
| last_seen | Attribute: "Last Seen" |
| last_updated | Last Modified Date |
| sources.source_name sources.osint sources.first_seen sources.last_seen sources.category | Attribute: "Source" The Attribute’s value is a Markdown-formatted table with the following columns:
|
| mscore | Attribute: "Mscore" |
| attributed_associations.name attributed_associations.type |
|
| reports/report_id | Associated Report Group |
| campaign/id | Associated Campaign Group |
| threat-rating.confidence_level | Attribute: "Confidence Level" |
| threat-rating.confidence_score | Confidence Rating |
| threat-rating.severity_level | Attribute: "Threat Level" |
| threat-rating.threat_score | Threat Rating |
| category | Attribute: "Role" |
| verdict_simple | Attribute: "Verdict" The Attribute’s value is a Markdown-formatted table with the following columns:
|
Reports (From Reports Endpoint)
ThreatConnect object type: Report Group
| Mandiant API Field | ThreatConnect Field |
|---|---|
| report_Id | Attribute: "External ID" |
| title |
|
| threat_scape | Attribute: "Category" |
| audience | Tag: "Audience: %audience%" |
| publish_date | Publish Date |
| version | Attribute: "Version" |
| report_type | Attribute: "Report Type" |
| executive_summary | Attribute: "Description" (default) |
| cve_ids |
|
| previous_versions | Attribute: "Previous Versions" The Attribute’s value is a Markdown-formatted table with the following columns:
|
| tags[*].actors.id | Associated Intrusion Set Group |
| tags[*].actors.name | Tag: "Intrusion Set: %name%" |
| tags[*].affected_industries | Attribute: "Targeted Industry Sector" |
| tags[*].intended_effects | Attribute: "Intended Effects" |
| tags[*].motivations | Attribute: "Adversary Motivation Type" |
| tags[*].malware_families.id | Associated Malware Group |
| tags[*].malware_families.name | Tag: "Malware: %name%" |
| tags[*].operating_systems | Attribute: "Operating System" |
| tags[*].ttps | Attribute: "Capability" |
| tags[*].target_geographies | Attribute: "Target Geography" |
| tags[*].affected_systems | Attribute: "Affected Systems" |
| tags[*].source_geographies | Attribute: "Source Geography" |
| tags[*].targeted_informations | Attribute: "Target Information" |
Malware and Tool (From Malware Endpoint)
ThreatConnect object type: Malware or Tool Group
| Mandiant API Field | ThreatConnect Field |
|---|---|
| id | Attribute: "External ID" |
| name | Name/Summary |
| description | Attribute: "Description" (default) |
| last_updated |
|
| operation_systems | Attribute: "Operating System" |
| aliases[*].name | Attribute: "Aliases" (newline delimited) |
| capabilities | Attribute: "Capability" |
| industries[*].name | Attribute: "Targeted Industry Sector" |
| detections | Attribute: "Detections" (newline delimited) |
| roles | Attribute: "Role" |
| actors/{index}/id | Associated Intrusion Set Group |
| actors/{index}/name | Tag: "Intrusion Set: %name%" |
| cve |
|
| yara.id | Associated Signature Group |
| malware/{index}/id | Associated Malware Group |
| malware/{index}name | Tag: "Malware: %name%" |
| last_activity_time | Attribute: "Last Seen" |
| attack_patterns.{attack_pattern_id}.attack_pattern_identifier | ATT&CK Tag |
Signature (From Yara Endpoint)
ThreatConnect object type: Signature Group
| Mandiant API Field | ThreatConnect Field |
|---|---|
| created |
|
| id | Attribute: "External ID" |
| malware.id | Associated Malware Group |
| malware.name | Tag: "Malware: %name%" |
| modified |
|
| name | Name/Summary |
| rule | Signature File Content |
Campaign (From Campaign Endpoint)
ThreatConnect object type: Campaign Group
| Mandiant API Field | ThreatConnect Field |
|---|---|
| id |
|
| name | Name/Summary |
| description | Attribute: "Description" (default) |
| campaign_type | Attribute: "Campaign Type" |
| last_activity_time |
|
| actors/id | Associated Intrusion Set Group (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| actors/name | Tag: "Intrusion Set: %name%" (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| malware/id | Associated Malware Group (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| malware/name | Tag: "Malware: %name%" (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| tools/id | Associated Tool Group (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| tools/name | Tag: "Tool: %name%" (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| vulnerabilities/cve_id |
|
| industries/name | Attribute: "Target Industry Sector" |
| target_locations/countries/iso2 | Attribute: "Target Country Code" |
| target_locations/regions/name | Attribute: "Target Region" |
| target_locations/sub_regions/name | Attribute: "Target Sub Region" |
| attack_patterns.{attack_pattern_id}.attack_pattern_identifier | ATT&CK Tag |
Timeline (From Campaign Endpoint)
ThreatConnect object type: Event Group
| Mandiant API Field | ThreatConnect Field |
|---|---|
| timeline/name | Attribute: "Timeline" |
| timeline/brief | Attribute: "Description" (default) |
| timeline/analyst_brief | Attribute: "Additional Analysis and Context" |
| timeline/timestamp | Event Date |
| timeline/mitre_techniques/name | Attribute: "Capability" (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| timeline/used_by/actor/id | Associated Intrusion Set Group |
| timeline/used_by/actor/name | Tag: "Intrusion Set: %name%" |
| timeline/attributions/malware/id | Associated Malware Group (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| timeline/attributions/malware/name | Tag: "Malware: %name%" (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| timeline/attributions/actor/id | Associated Intrusion Set Group (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| timeline/attributions/actor/name | Tag: "Intrusion Set: %name%" (ingested only when the attribution scope Mandiant API field has a value of confirmed) |
| timeline/attributions/vulnerabilities/cve_id |
|
Vulnerability (From Vulnerability Endpoint)
ThreatConnect object type: Vulnerability Group
| Mandiant API Field | ThreatConnect Field |
|---|---|
| title | Attribute: "Title" |
| id | Attribute: "External ID" |
| description | Attribute: "Description" (default) |
| risk_rating | Tag: "Risk Rating: %risk_rating%" |
| analysis | Attribute: "Additional Analysis and Context" |
| executive_summary | Attribute: "Executive Summary" |
| exploitation_vectors | Attribute: "Exploitation Vector" |
| exploitation_consequence | Attribute: "Exploitation Consequence" |
| exploitation_state | Attribute: "Exploitation State" |
| cwe_details/id | Tag: "%id%" |
| cve_id | Name/Summary |
| vendor_fix_references/{index}/url vendor_fix_references/{index}/name | Attribute: "Vendor Fix URL" |
| date_of_disclosure | Attribute: "Date of Disclosure" |
| observed_in_the_wild | Attribute: "Observed in Wild" |
| was_zero_day | Attribute: "Was Zero Day" |
| last_modified_date |
|
| workarounds_list | Attribute: "Workaround" |
| publish_date | Attribute: "Report Publish Date" |
| available_mitigation/{index} | Attribute: "Mitigations" |
| sources/{index}/source_name sources/{index}/source_description sources/{index}/date sources/{index}/url | Attribute: "Source" |
| exploits/{index} | Attribute: "Exploits" |
| associated_actors/{index} | Associated Intrusion Set Group |
| associated_malware/{index} | Associated Malware Group |
| associated_reports/{index} | Associated Report Group |
| common_vulnerability_scores/v2.0/access_complexity |
|
| common_vulnerability_scores/v2.0/base_score | Attribute: "CVSS Score v2" |
| common_vulnerability_scores/v2.0/integrity_impact |
|
| common_vulnerability_scores/v2.0/access_vector |
|
| common_vulnerability_scores/v2.0/authentication | Attribute: "CVSS v2 Authentication" |
| common_vulnerability_scores/v2.0/availability_impact |
|
| common_vulnerability_scores/v2.0/temporal_score | Attribute: "CVSS Temporal Score v2" |
| common_vulnerability_scores/v2.0/exploitability | Attribute: "CVSS v2 Exploitability" |
| common_vulnerability_scores/v2.0/confidentiality_impact |
|
| common_vulnerability_scores/v3.1/attack_complexity |
|
| common_vulnerability_scores/v3.1/base_score | Attribute: "CVSS Score v3" |
| common_vulnerability_scores/v3.1/integrity_impact |
|
| common_vulnerability_scores/v3.1/report_confidence |
|
| common_vulnerability_scores/v3.1/attack_vector |
|
| common_vulnerability_scores/v3.1/privileges_required |
|
| common_vulnerability_scores/v3.1/availability_impact |
|
| common_vulnerability_scores/v3.1/temporal_score | Attribute: "CVSS Temporal Score v3" |
| common_vulnerability_scores/v3.1/exploit_code_maturity |
|
| common_vulnerability_scores/v3.1/user_interaction |
|
| common_vulnerability_scores/v3.1/scope |
|
| common_vulnerability_scores/v3.1/confidentiality_impact |
|
| common_vulnerability_scores/v3.1/remediation_level |
|
| affects_ot | Attribute: "OT Related" |
| aliases | Attribute: "Aliases" (newline delimited) |
| epss/percentile | Attribute: "EPSS Percentile" |
| epss/score | Attribute: "EPSS Score" |
| mve_id |
Note The mve_id Mandiant API field is mapped to a Vulnerability Group’s name in certain situations. For example, if a Vulnerability Group represents a zero-day vulnerability that has not been assigned a CVE ID, the vulnerability’s MVE ID will be used as the Vulnerability Group’s name. If a CVE ID is later assigned to a vulnerability with only an MVE ID, the corresponding Vulnerability Group’s name will be updated to replace the MVE ID with the CVE ID. |
| version_history | Attribute: "Previous Versions" |
| vulnerable_cpes/vendor_name | Attribute: "Vulnerable Vendor" |
| vulnerable_cpes/technology_name | Attribute: "Vulnerable Product" |
| cpe_ranges/start_cpe/vendor cpe_ranges/start_cpe/product cpe_ranges/start_cpe/version cpe_ranges/end_cpe/version | Attribute: "Vulnerable Products" The Attribute’s value is a Markdown-formatted table with the following columns:
|
Frequently Asked Questions (FAQ)
How is Mandiant Threat Score mapped to Indicators in ThreatConnect?
In November 2023, Mandiant introduced Threat Score for Indicators, which builds on the existing MScore. Mandiant Threat Score is a combination of confidence and severity and reflects the likelihood of an Indicator being malicious. A Threat Score of 0 indicates no confidence in the Indicator being malicious, while a Threat Score of 100 indicates full confidence in the Indicator being malicious. In ThreatConnect, the 100-point Mandiant Threat Score scale is mapped to the five-skull Threat Rating scale as follows:
| Mandiant Threat Score | ThreatConnect Threat Rating |
|---|---|
| 0–19 | 0 Skulls |
| 20–39 | 1 Skull |
| 40–59 | 2 Skulls |
| 60–74 | 3 Skulls |
| 75–89 | 4 Skulls |
| 90–100 | 5 Skulls |
ThreatConnect® is a registered trademark, and TC Exchange™ is a trademark, of ThreatConnect, Inc.
Mandiant® is a registered trademark of Mandiant, Inc.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.
30002-08 EN Rev. A


