- 29 Apr 2024
- 3 Minutes to read
-
Print
-
DarkLight
-
PDF
CAL Automated Threat Library (ATL)
- Updated on 29 Apr 2024
- 3 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The CAL™ Automated Threat Library (ATL) Source in ThreatConnect® is the evolution of the Technical Blogs and Reports (TBR) Source. It automates, aggregates, and analyzes intelligence from multiple authoritative publishers of open-source intelligence. CAL ATL incorporates historical feedback from TBR users and leverages the cutting-edge analytics available in CAL.
Before You Start
| Minimum Role(s) | Read Only User |
|---|---|
| Prerequisites |
|
CAL ATL Features
Native Integration With the ThreatConnect Platform
CAL ATL leverages the ThreatConnect data model to its fullest with the following features:
- Individual blog posts from selected blogs as Report Groups, with HTML converted to viewable Markdown. This feature also provides artificial intelligence–generated summaries for the Report Groups via the AI Insights card on the Group’s Details screen.
- Intrusion Sets, Malware families, ATT&CK® techniques, Tools, and more as defined by the MITRE ATT&CK® Library. This set of features includes Attributes and descriptions as provided by MITRE®.
- Vulnerabilities from the National Vulnerability Database (NVD), with descriptions where applicable.
- Curation of associations between Group objects to enable proper pivoting, dashboarding, and ThreatConnect Query Language (TQL) queries. This feature includes automatic alias translation. For example, if a blog mentions “Geodo” or “Emotet,” CAL will find it and create an association to Group objects for the alias.
- Collection of Address, Host, and URL Indicators associated with blog posts. This feature also associates the collected Indicators to the Report Group for the corresponding blog post and any other related objects.
ATT&CK Technique Identification Using NLP
Using the natural-language processing (NLP) capabilities of CAL, ATL automatically associates blogs to ATT&CK techniques based on plain-English sentences. Many solutions rely on a simplistic match for something like “T1569.002” (System Services: Service Execution) to determine that text may be related to an Indicator. CAL’s approach uses a trained-NLP model to identify sentences within a blog, like “Adversaries may abuse the Windows service control manager to execute malicious commands or payloads,” to detect pertinent Attack Pattern Groups and associate them to the Report.
Smarter Indicator Curation
ATL creates a smarter way to curate Indicators beyond plain regular-expression scrapes by using CAL’s insights to normalize Source data, including the following improvements:
- Better removal of false positives that don’t belong in the Source, such as links to blogs on the same website, author email addresses, and so on.
- Better ThreatAssess mappings for the Indicators that remain. If CAL already knows about an Indicator’s reputation, CAL will set the Threat Rating and Confidence Rating accordingly to ensure that Indicators behave appropriately in your environment.
- Better inclusion of CAL’s Indicator Status so that if benign Indicators are memorialized in the platform, they are less likely to create false alerts through integrations.
Enhanced Platform Flexibility and Stability
Improvements in CAL 3.0 allow ATL to flex and scale as the volume, variety, and velocity of data sources are added.
Important Questions
How Can I Enable CAL ATL?
Just like all other CAL feeds, you can activate the CAL ATL feed on the Feeds tab of the TC Exchange™ Settings screen:
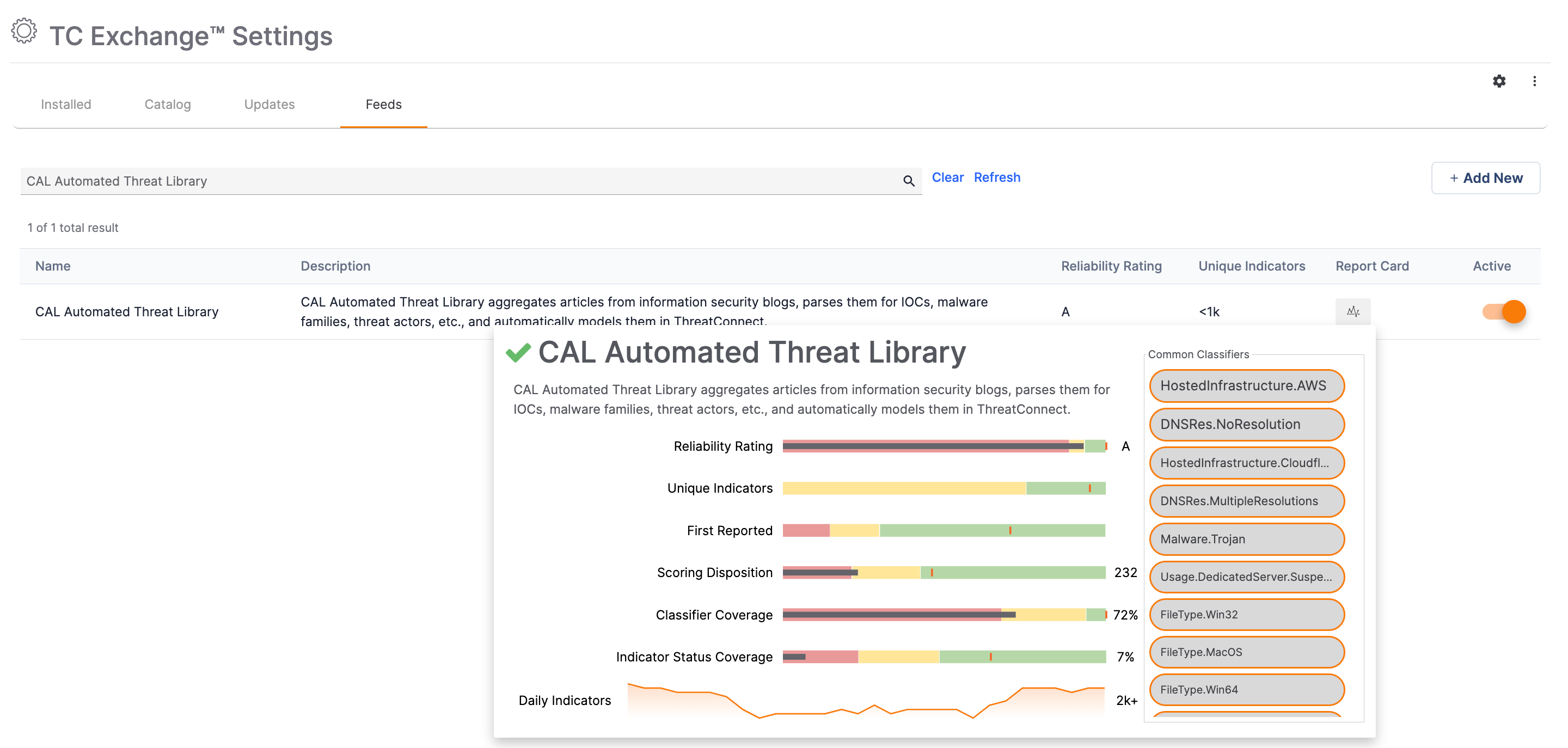
Please note the following activation guidance:
- Only Administrators can activate the CAL Automated Threat Library Source feed.
- As with other CAL feeds, users do not need to have CAL enabled in System Settings to enable ATL.
- As with other CAL feeds, On-Premises users will need to ensure that their instance can reach cal.threatconnect.com to receive the data from CAL ATL.
- The initial data load when first enabling ATL will be larger than its daily updates. While we don’t anticipate performance disruptions, we advise customers to enable ATL when the potential impact of such a data load would be minimized, such as before or after standard working hours.
Is TBR Still Available?
The Technical Blogs and Reports Source has been deprecated and de-activated. Customers who already have TBR enabled may keep their existing TBR Source within their instance for legacy purposes.
How Do I Provide Feedback About CAL ATL?
We are very excited for the initial launch of ATL and will be continuously adding new features and functionality. If you have feedback and suggestions for items such as the following, please provide them directly to your Customer Success Manager (CSM) or via Productboard:
- Requests for additional blogs
- False-positive (or false-negative!) Indicators (you may also report an Indicator as false positive from its Details screen)
- Improvements to blog parsing and rendering
- Improvements to matching analysis (aliases, Attack Patterns, etc.)
Please ensure that your feedback requests include examples, which are critical for our Product and Engineering teams to implement enhancements quickly.
ThreatConnect® is a registered trademark, and CAL™ and TC Exchange™ are trademarks, of ThreatConnect, Inc.
MITRE®, ATT&CK®, and MITRE ATT&CK® are registered trademarks of The MITRE Corporation.
20140-01 v.02.B


