- 24 Apr 2025
- 8 Minutes to read
-
Print
-
DarkLight
-
PDF
Feedly Intelligence Engine Integration User Guide
- Updated on 24 Apr 2025
- 8 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The Feedly™ Intelligence Engine integration with ThreatConnect® lets you ingest open-source data from Feedly Threat Intelligence into ThreatConnect. Feedly Threat Intelligence information available for ingestion includes Articles/Reports, Indicators, Actors, Events, Malware, and Vulnerabilities. These data are seamlessly ingested as Addresses, Attack Patterns, Files, Hosts, Intrusion Sets, Malware, Reports, Threat Actors, URLs, and Vulnerabilities into ThreatConnect.
Dependencies
ThreatConnect Dependencies
- ThreatConnect instance with version 7.6.2 or newer installed
Feedly Dependencies
- Feedly Enterprise-level subscription
- Active Feedly API token (known as an access token in Feedly). To create an access token in Feedly, follow the instructions in the Feedly documentation.ImportantFeedly API tokens are available to Enterprise-level customers only.
- Feedly API Stream ID. See the “Feedly API Stream ID” section for instructions on how to find your Feedly API Stream ID.
Application Setup and Configuration
Follow these steps to install the Feedly Intelligence Engine App via TC Exchange™:
- Log into ThreatConnect with a System Administrator account.
- Hover over Settings
 on the top navigation bar and select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen.
on the top navigation bar and select TC Exchange Settings. Then select the Catalog tab on the TC Exchange Settings screen. - Locate the Feedly Intelligence Engine App on the Catalog tab. Then click Install
 in the Options column to install the App.
in the Options column to install the App. - After you install the Feedly Intelligence Engine App, the Feed Deployer will open automatically. Use the Feed Deployer to set up and configure the App. See the “Configuration Parameters” section for more information on the parameters available during the configuration and deployment process.
Feedly API Stream ID
Follow these steps to find your Feedly API Stream ID for the ThreatConnect feed:
- Log into Feedly.
- Hover over ThreatConnect feed in the Team Feeds section of the left sidebar and click ⋯.
- Select Settings from the dropdown.
- Click the Sharing tab in the Folder Settings drawer.
- Click Copy ID next to the text in the Feedly API Stream ID field.
Configuration Parameters
Parameter Definitions
The parameters defined in Table 1 apply to the configuration parameters available when using the Feed Deployer to configure the Feedly Intelligence Engine App.
| Name | Description | Required? |
|---|---|---|
| Source Tab | ||
| Sources to Create | Enter the name of the Source for the feed. | Required |
| Owner | Select the Organization in which the Source will be created. | Required |
| Activate Deprecation | Select this checkbox to allow confidence deprecation rules to be created and applied to Indicators in the Source. | Optional |
| Create Attributes | Select this checkbox to allow custom Attribute Types to be created in the Source. | Optional |
| Parameters Tab | ||
| Launch Server | Select tc-job as the launch server for the Service corresponding to the Feed API Service App. | Required |
| Feedly API Token | Enter the Feedly API (access) token created in your Feedly account. To create a Feedly API token in your Feedly account, follow the instructions for creating an access token in the Feedly documentation. Important Feedly API tokens are available to Enterprise-level customers only. | Required |
| Feedly STIX Group Objects | Select the Group types to import from Feedly. All Group types are selected by default, and it is recommended to retain this selection. Available options include the following:
| Optional |
| Feedly STIX Indicator Objects | Select the Indicator types to import from Feedly. All Indicator types are selected by default, and it is recommended to retain this selection. Available options include the following:
| Optional |
| Stream ID(s) | Enter the Feedly API Stream ID. Note If entering multiple Stream IDs, use a comma as the delimiter between each Stream ID. | Required |
| Advanced Settings | There are no advanced settings to configure. Warning Leave this field blank, as entering values may result in unintended consequences. | Optional |
| Confirm Tab | ||
| Run Feeds after deployment | Select this checkbox to run the Feedly Intelligence Engine App immediately after the deployment configuration is complete (i.e., after you click DEPLOY on the Feed Deployer window). | Optional |
| Confirm Deployment Over Existing Source | This checkbox will be displayed if the Source entered in the Sources to Create field has previously been deployed to the Organization selected in the Owner dropdown on the Source tab. Select this checkbox to confirm that you want the Feedly Intelligence Engine App to write data to the same Source. This process will create a new Service for the Feedly Intelligence Engine App. As such, it is recommended that you delete the old Service associated with the Feedly Intelligence Engine App after the new one is created. Important If you do not select this checkbox, the DEPLOY button will be grayed out, and you will not be able to deploy the Service. Return to the Source tab and enter a different Source or select a different Organization and then proceed through the tabs of the Feed Deployer window again. | Optional |
Feedly Intelligence Engine UI
After successfully configuring and activating the Feed API Service, you can access the Feedly Intelligence Engine user interface (UI). This UI allows you to interact with and manage the Feedly integration.
Follow these steps to access the Feedly Intelligence Engine UI:
- Log into ThreatConnect with a System Administrator account.
- Hover over Playbooks on the top navigation bar and select Services.
- Locate and turn on the Feedly Intelligence Engine Feed API Service.
- Click the link in the Service’s API Path field. The Feedly Intelligence Engine UI will open in a new browser tab.
The following screens are available in the Feedly Intelligence Engine UI:
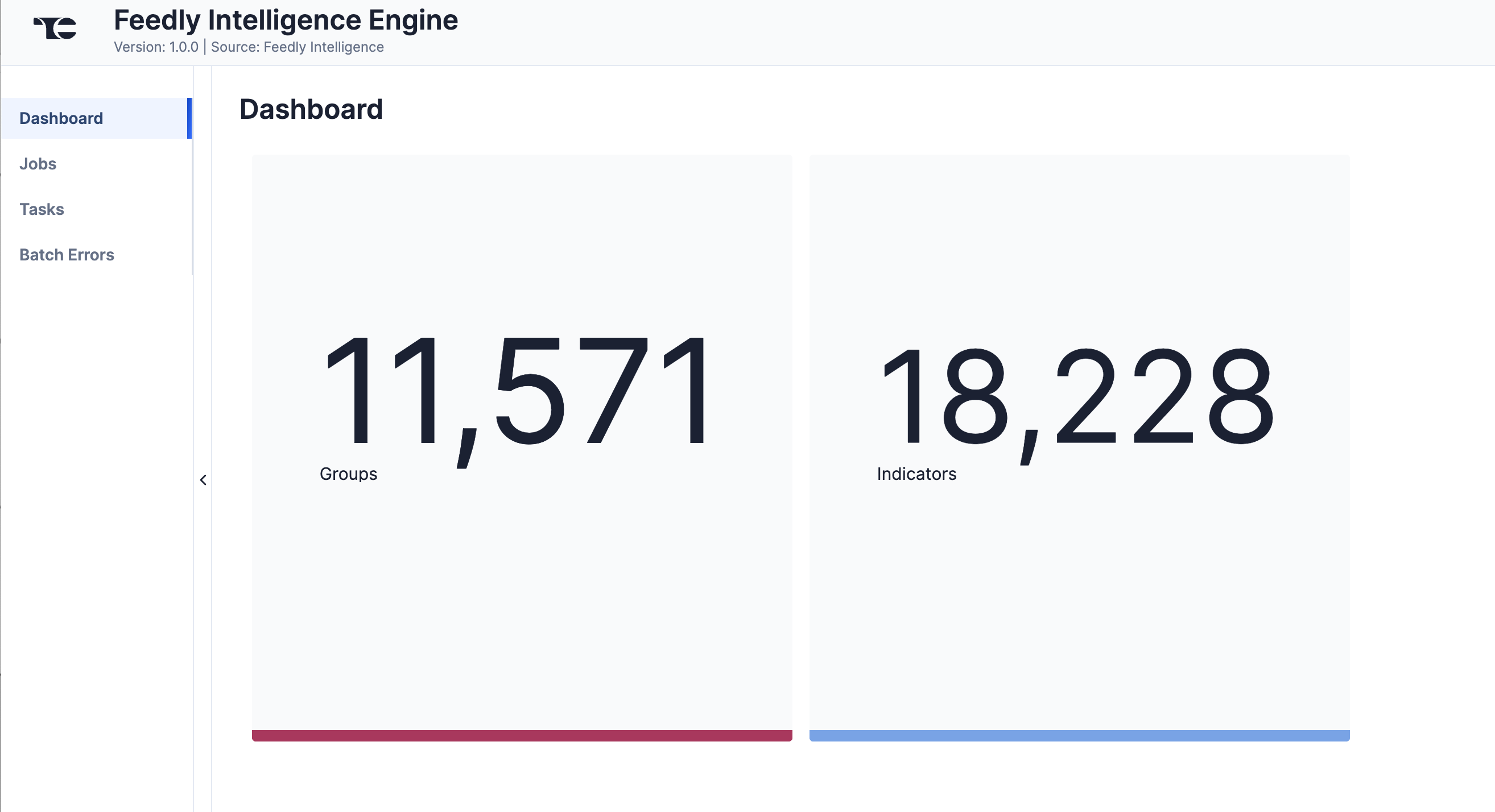
Dashboard
The Dashboard screen (Figure 1) provides an overview of the total number of Groups and Indicators retrieved from Feedly. Depending on the available data, cards representing all or a subset of these objects will be displayed on the Dashboard screen.
Jobs
The Jobs screen (Figure 2) breaks down the ingestion of Feedly data into manageable Job-like tasks, displaying all processes that are pending, in progress, complete, and failed. The ⋯ menu in a Job’s row provides the following options:
- Details: View details for the Job, such as download, convert, and upload start and complete times and counts of downloaded and batched Groups and Indicators.
- Download Files: Download metadata files for all Jobs and data (convert, download, and upload) files for completed Jobs.
- Batch Errors: View errors that have occurred for the Job on the Batch Errors screen.
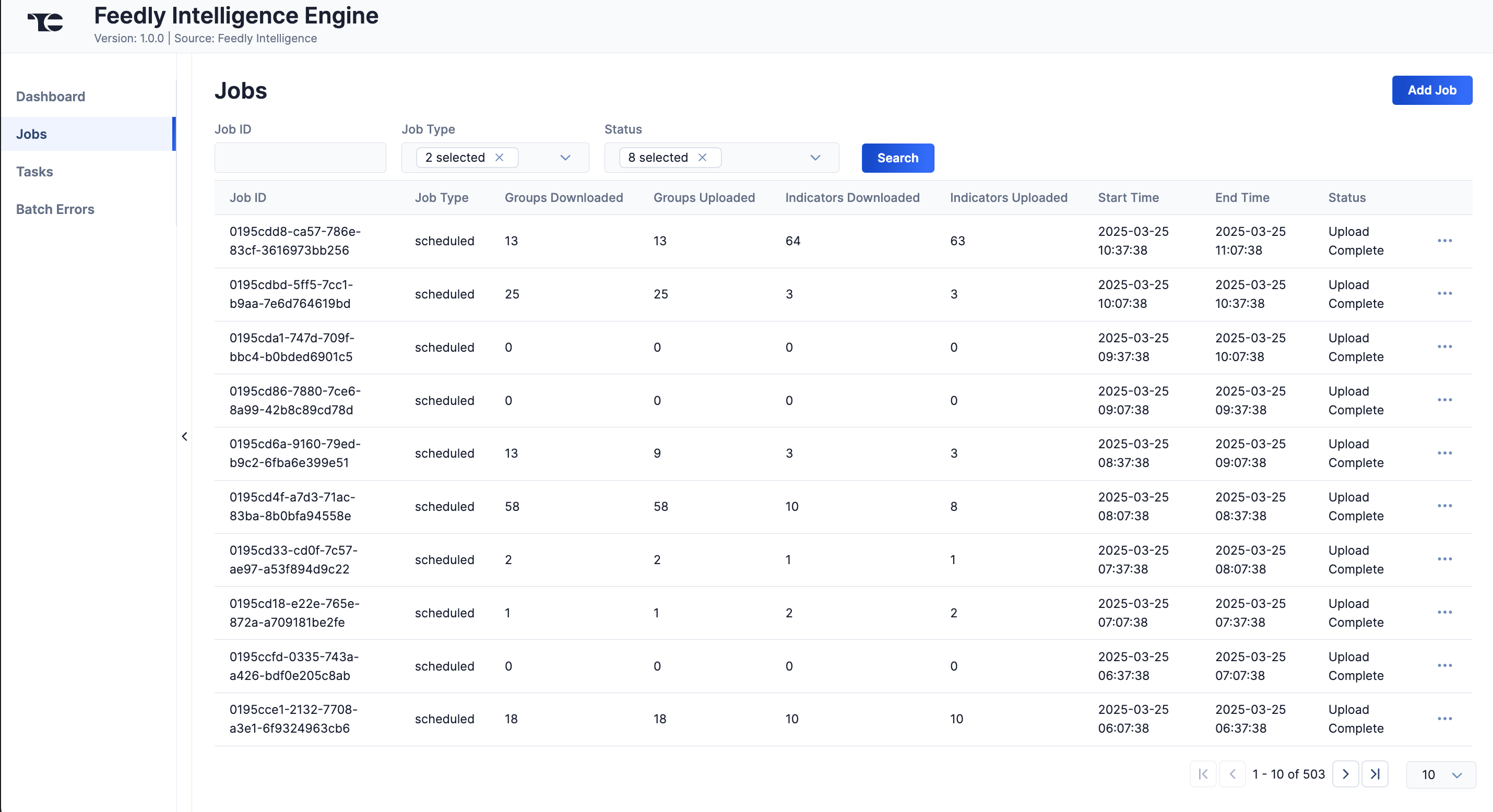
You can filter Feedly Intelligence Engine App Jobs by the following elements:
- Job ID: Enter text into this box to search for a Job by its Job ID.
- Job Type: Select Job types to display on the Jobs screen.
- Status: Select Job statuses to display on the Jobs screen.
Add a Job
You can add ad-hoc Jobs on the Jobs screen. Follow these steps to create a request for an ad-hoc Job for the Feedly Intelligence Engine App:
- Click the Add Job button at the upper right of the Jobs screen (Figure 2).
- Fill out the fields on the Add Job drawer (Figure 3) as follows:
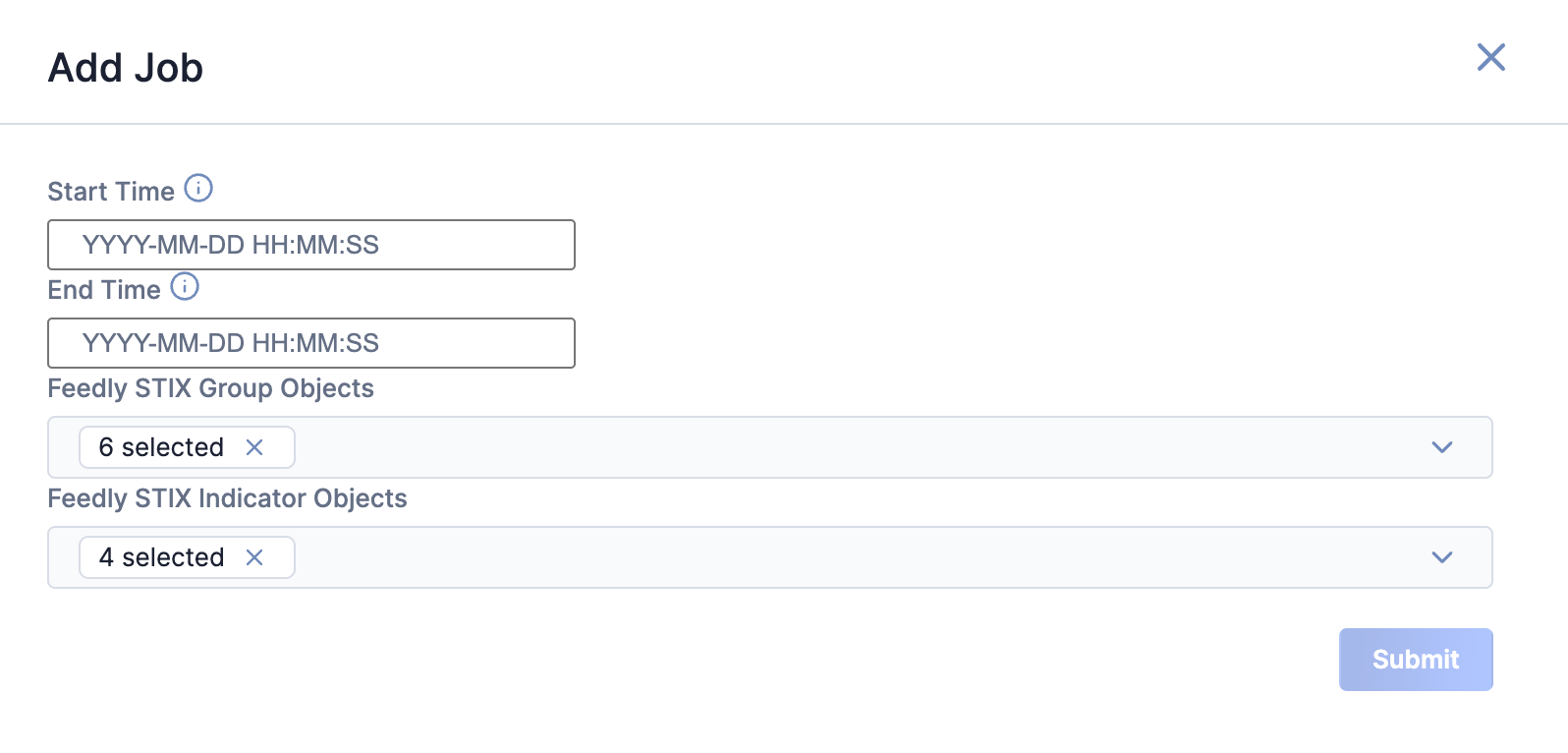
- Start Time: (Optional) Enter the time at which the Job should start.
- End Time: (Optional) Enter the time by which the Job should end.
- Feedly STIX Group Objects: (Optional) Select the Feedly STIX Group object types to include in the ad-hoc Job.
- Feedly STIX Indicator Objects: (Optional) Select the Feedly STIX Indicator object types to include in the ad-hoc Job.
- Click Submit to submit the request for the ad-hoc Job.
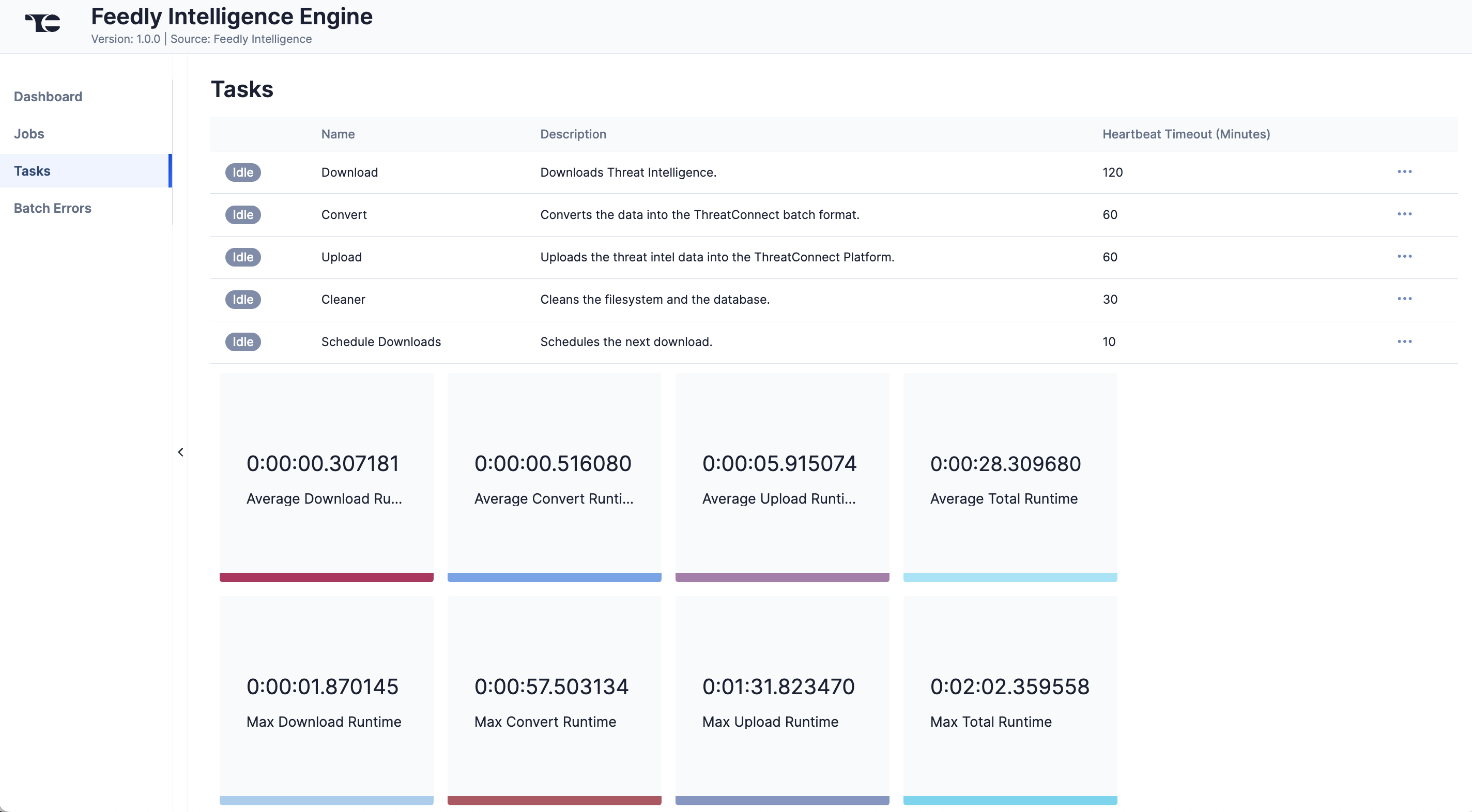
Tasks
The Tasks screen (Figure 4) displays all Tasks that may be part of a Job, including each step of the download, convert, and upload processes, as well as Tasks for the Feedly Intelligence Engine App, such as Monitor, Scheduler, and Cleaner. The current status (Idle, Paused, or Running), name, description, and heartbeat timeout length, in minutes, are displayed for each Task. The ⋯ menu in a Task’s row provides the following options, depending on the Task’s status:
- Run (idle and paused Tasks only)
- Pause (idle and running Tasks only)
- Resume (paused Tasks only)
- Kill (running Tasks only)
Under the table is a dashboard where you can view runtime analytics.
Batch Errors
The Batch Errors screen (Figure 5) displays an overview of the batch error types that have occurred for Job requests. You can enter keywords to filter by Job ID.
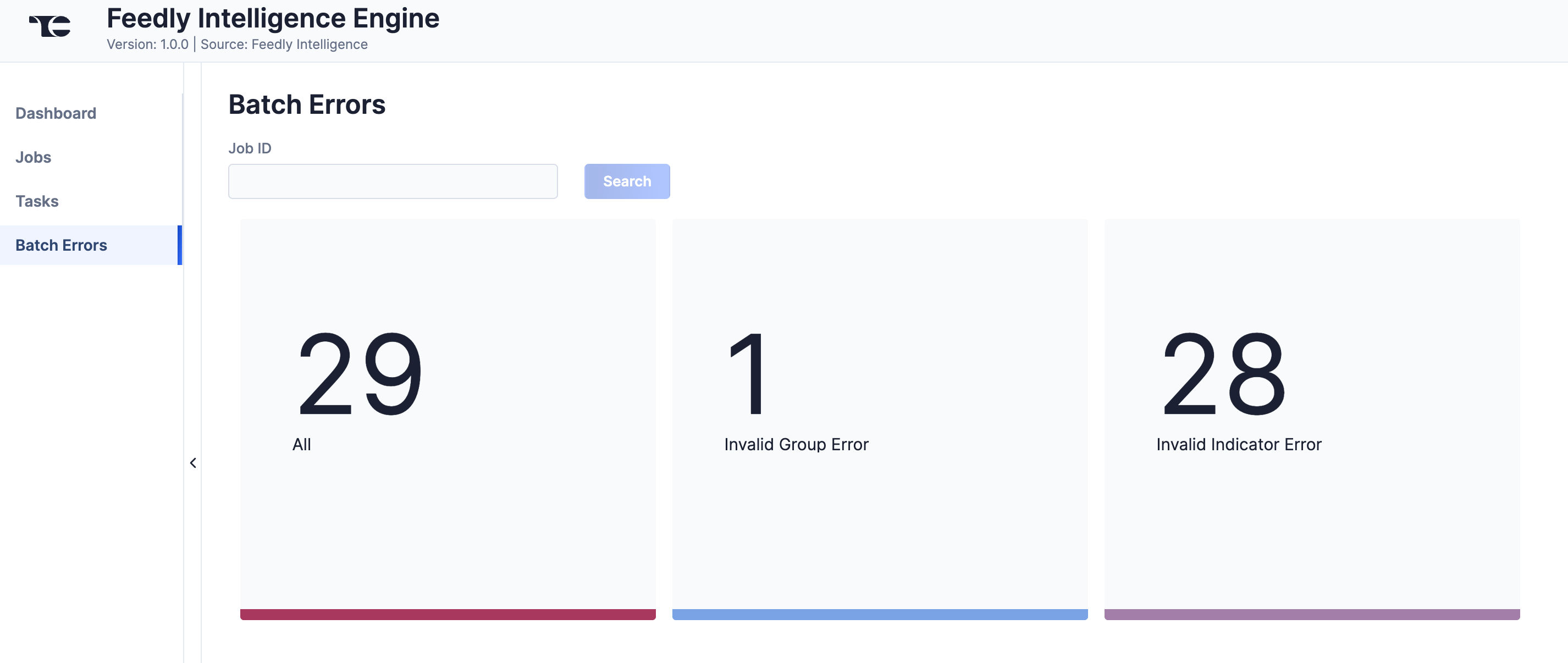
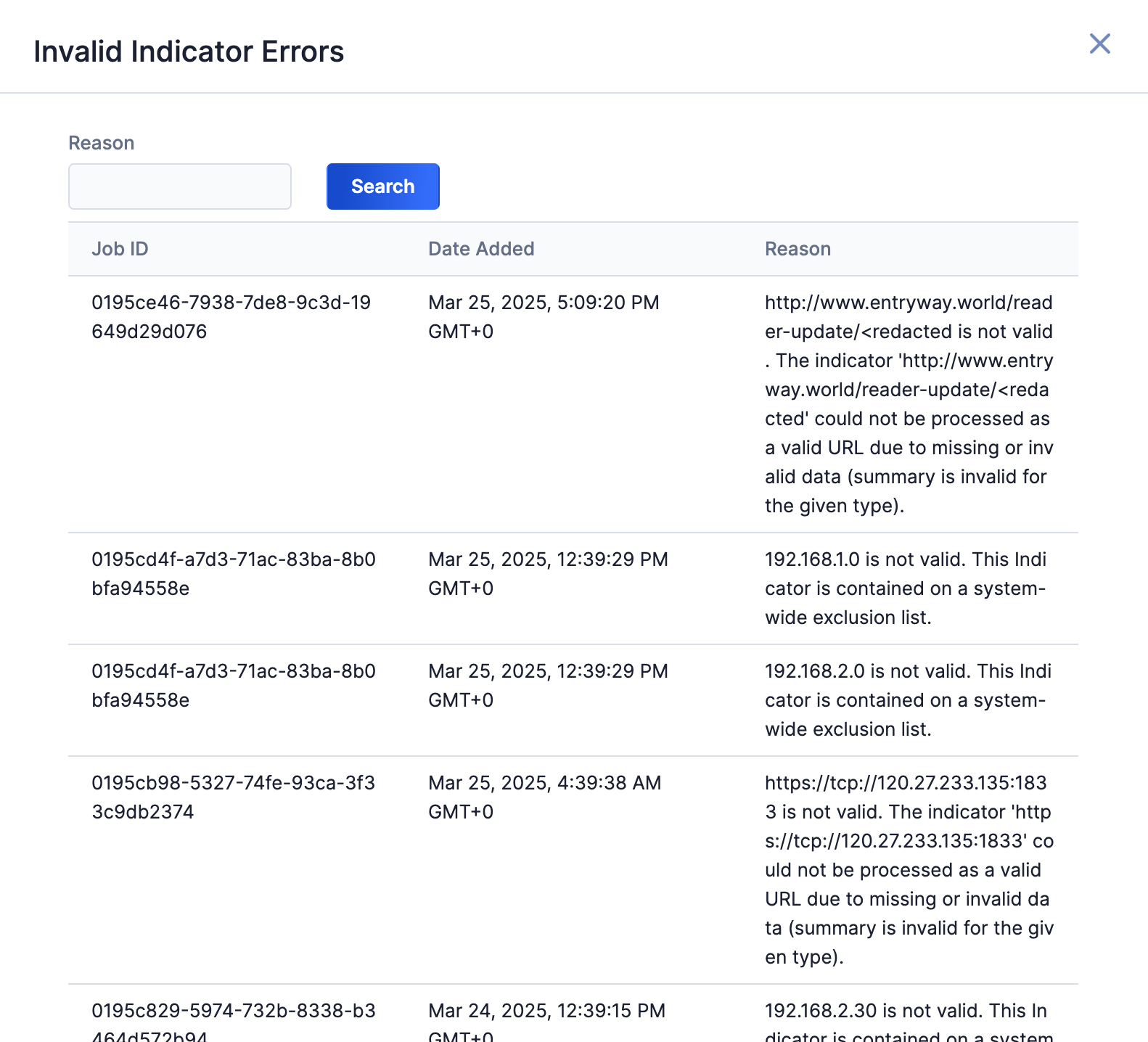
Click on an error type to open a drawer containing a table with details on all batch errors of that type (Figure 6). You can enter keywords to filter by reason for error.
Data Mappings
The data mappings in Table 2 through Table 11 illustrate how data are mapped from Feedly Intelligence API endpoints into the ThreatConnect data model.
Address
ThreatConnect object type: Address Indicator
| Feedly API Field | ThreatConnect Field |
|---|---|
| name | Name/Summary Note If a port value is included with the IP address, it will be removed. |
| id | Attribute: "External ID" |
| created | Attribute: "External Date Created" |
| modified | Attribute: "External Date Last Modified" |
| <extracted port> | Attribute: "Port" |
Attack Pattern
ThreatConnect object type: Attack Pattern Group
| Feedly API Field | ThreatConnect Field |
|---|---|
| name | Name/Summary |
| description | Attribute: "Description" (default) |
| id | Tag: "<MITRE ATT&CK® tactic or technique id>" |
| created | Attribute: "External Date Created" |
| modified | Attribute: "External Date Last Modified" |
| x_mitre_platforms | Attribute: "Operating System" (newline delimited) |
| kill_chain_phases[].phase_name | Attribute: "Tactic Name" |
| external_references[].source_name | Attribute: "Source" |
| external_references[].url | Attribute: "External References" |
File
ThreatConnect object type: File Indicator
| Feedly API Field | ThreatConnect Field |
|---|---|
| pattern | Name/Summary |
| created | Attribute: "External Date Created" |
| modified | Attribute: "External Date Last Modified" |
Host
ThreatConnect object type: Host Indicator
| Feedly API Field | ThreatConnect Field |
|---|---|
| name | Name/Summary Note If a port value is included in the hostname, it will be removed. |
| id | Attribute: "External ID" |
| created | Attribute: "External Date Created" |
| modified | Attribute: "External Date Last Modified" |
Intrusion Set
ThreatConnect object type: Intrusion Set Group
| Feedly API Field | ThreatConnect Field |
|---|---|
| name | Name/Summary |
| description | Attribute: "Description" (default) |
| id | Attribute: "External ID" |
| created | Attribute: "External Date Created" |
| modified | Attribute: "External Date Last Modified" |
| aliases[] | Attribute: "Alias" |
| external_references[].url | Attribute: "Source" |
Malware
ThreatConnect object type: Malware Group
| Feedly API Field | ThreatConnect Field |
|---|---|
| name | Name/Summary |
| description | Attribute: "Description" (default) |
| id | Attribute: "External ID" |
| created | Attribute: "External Date Created" |
| modified | Attribute: "External Date Last Modified" |
| aliases[] | Attribute: "Alias" |
| malware_types[] | Tag: "<malware family>" Note The value of the Tag can be the name of a malware family (e.g., “downloader”), or it can be “unknown.” |
| external_references[].url | Attribute: "External References" |
Report
ThreatConnect object type: Report Group
| Feedly API Field | ThreatConnect Field |
|---|---|
| name | Name/Summary |
| description | Attribute: "Description" (default) |
| id |
|
| published | Attribute: "External Date Created" |
| modified | Attribute: "External Date Last Modified" |
| labels[] | Tag: "<Feedly report labels>" Note Examples of Feedly report labels include “Feedly AI,” “Feedly Hashes,” and “Feedly URLs.” |
| external_references[].source_name | Attribute: "Source" |
| external_references[].url | Attribute: "External References" |
Threat Actor
ThreatConnect object type: Adversary Group
| Feedly API Field | ThreatConnect Field |
|---|---|
| name | Name/Summary |
| description | Attribute: "Description" (default) |
| id |
|
| published | Attribute: "External Date Created" |
| modified | Attribute: "External Date Last Modified" |
| external_references[].url | Attribute: "Source" |
URL
ThreatConnect object type: URL Indicator
| Feedly API Field | ThreatConnect Field |
|---|---|
| name | Name/Summary |
| id | Attribute: "External ID" |
| created | Attribute: "External Date Created" |
| modified | Attribute: "External Date Last Modified" |
Vulnerability
ThreatConnect object type: Vulnerability Group
| Feedly API Field | ThreatConnect Field |
|---|---|
| name | Name/Summary |
| description | Attribute: "Description" (default) |
| id |
|
| published | Attribute: "External Date Created" |
| modified | Attribute: "External Date Last Modified" |
| external_references[].url | Attribute: "Source" |
Frequently Asked Questions (FAQ)
How do I download a specific report from Feedly?
It is not possible to download a specific report from Feedly. The Feedly Intelligence Engine App relies on the use of the Feedly API Stream ID, which provides access to the Feedly feed stream only.
How much historical Feedly data does the Feedly Intelligence Engine App ingest into ThreatConnect?
When collecting data for the first time after installation, the Feedly Intelligence Engine App pulls all available data from the last 30 days. After that, the App performs incremental updates to collect either new reports or reports that changed since the last update.
ThreatConnect® is a registered trademark, and TC Exchange™ is a trademark, of ThreatConnect, Inc.
Feedly™ is a trademark of Feedly, Inc.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.
30091-01 EN Rev. A


