- 16 Jan 2026
- 13 Minutes to read
-
Print
-
DarkLight
-
PDF
Dataminr Pulse Alerts Engine Integration User Guide
- Updated on 16 Jan 2026
- 13 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The Dataminr Pulse Alerts Engine Feed API Service App in ThreatConnect® unlocks real-time alerting by seamlessly ingesting Dataminr Pulse Cyber Alerts and converting them into actionable intelligence within ThreatConnect. The integration ingests Cyber Alerts from Dataminr Pulse Alert Lists and creates corresponding objects in ThreatConnect with select Dataminr Pulse metadata and AI summary information:
- Alerts are created as Event Groups in ThreatConnect. Intel Agent and Live Brief AI summaries from Dataminr Pulse are included as AI insights for the Event Group in ThreatConnect, with Intel Agent and Live Brief Tags added to Event Groups that have those respective AI summary types.
- Discovered Entities for Alerts are created as Groups (Intrusion Set, Malware, or Vulnerability) associated to the Event Group corresponding to the ingested Alert.
- Key Points for Alerts are created as Indicators (Address, ASN, File, Host, or URL) or Groups (Intrusion Set or Vulnerability) associated to the Event Group corresponding to the ingested Alert.
The Dataminr Pulse Alerts Engine App ingests new Alerts into ThreatConnect every five minutes starting from the time at which the integration is deployed.
Dependencies
ThreatConnect Dependencies
- Active ThreatConnect Application Programming Interface (API) key
- ThreatConnect instance with version 7.11.2-M1218R or newer installed
Dataminr Dependencies
- Dataminr Pulse API public key
- Dataminr Pulse API secret
Application Setup and Configuration
The Dataminr Pulse Alerts Engine App leverages the Feed Deployer to create a Source for data ingestion from Dataminr Pulse in an Organization and to configure the corresponding Service’s ingestion and authentication parameters. After you install the Dataminr Pulse Alerts Engine App on your ThreatConnect instance, you can deploy it to any Organization. It must be deployed separately for each Organization in which you want to create a Source for data ingestion and a corresponding Service.
Install the Dataminr Pulse Alerts Engine App
Follow these steps to install the Dataminr Pulse Alerts Engine App on your ThreatConnect instance:
- Log into ThreatConnect with a System Administrator account.
- From the Settings
 menu on the top navigation bar, select TC Exchange Settings.
menu on the top navigation bar, select TC Exchange Settings. - Select the Catalog tab on the TC Exchange™ Settings screen.
- Locate the Dataminr Pulse Alerts Engine App on the Catalog tab.
- Click Install
 in the Options column for the App.
in the Options column for the App. - Click INSTALL in the App’s Release Notes window.
- After you install the Dataminr Pulse Alerts Engine App, the Feed Deployer opens automatically. Follow the procedure in the “Deploy the Dataminr Pulse Alerts Engine App to an Organization” section to deploy the Dataminr Pulse Alerts Engine App to a Source in an Organization and configure the corresponding Service.
Deploy the Dataminr Pulse Alerts Engine App to an Organization
Follow these steps to deploy the Dataminr Pulse Alerts Engine App to an Organization:
- Log into ThreatConnect with a System Administrator account.
- From the Settings
 menu on the top navigation bar, select TC Exchange Settings.
menu on the top navigation bar, select TC Exchange Settings. - Locate the Dataminr Pulse Alerts Engine App on the Installed tab. Then select Deploy from the Options ⋮ dropdown.
- Follow the instructions in Table 1 to fill out the fields in the Feed Deployer window for a deployment of the Dataminr Pulse Alerts Engine App.
Name Description Required? Source Tab Sources to Create Enter the name of the Source for the feed. NoteUnless you are redeploying the feed to an existing Source in an Organization, the name of the Source must be unique on your ThreatConnect instance. It is recommended to add the Organization’s name to the end of the default Source name (e.g., Dataminr Pulse Alerts Engine – Demo Organization) for easy identification of the Source’s owner.Required Owner Select the Organization in which the Source will be created. Required Activate Deprecation Select this checkbox to allow confidence deprecation rules to be created and applied to Indicators in the Source. Optional Create Attributes Select this checkbox to allow custom Attribute Types for the Dataminr Pulse Alerts Engine App to be created on the System level of your ThreatConnect instance. ImportantIt is recommended that you keep this checkbox selected. If you deselect it, data from the Dataminr Pulse Alerts Engine App mapped to those Attribute Types will not be ingested.Optional Parameters Tab Launch Server Select tc-job as the launch server for the Feed API Service. Required Dataminr List IDs Enter the IDs for the Dataminr Pulse Cyber Alert Lists to ingest into ThreatConnect. If you leave this field blank, the App will ingest all Dataminr Pulse Cyber Alerts to which your Dataminr Pulse API account has access. NoteIf a List whose ID is entered in this field is deleted from Dataminr, the Dataminr Pulse Alerts Engine App may stop working. Please cross-check the available Alert Lists in Dataminr Pulse against the List IDs entered in this field to ensure uninterrupted ingestion from the App.Optional Variables Tab Dataminr API Public Enter the Dataminr Pulse API public key. Required Dataminr API Secret Enter the Dataminr Pulse API secret. Required Confirm Tab Run Feeds after deployment Select this checkbox to run the Dataminr Pulse Alerts Engine Service immediately after you click DEPLOY on the Feed Deployer window. Optional Confirm Deployment Over Existing Source This checkbox and a warning message are displayed on the Confirm tab if the Source name entered on the Source tab is already used by a Source owned by the selected Organization. To confirm redeploying the App to the existing Source, select the checkbox. This will activate the DEPLOY button. Otherwise, you must return to the Source tab and either change the Source name or select a different Organization. WarningWhen you redeploy a Feed API Service to a Source, existing data in the Source may be overwritten. Redeployment will also create a new Service for the Feed API Service App. It is recommended that you delete the previous Service for the Feed API Service App after the new one is created.Optional - Click DEPLOY on the Confirm tab of the Feed Deployer window to deploy the Dataminr Pulse Alerts Engine App in the Organization, which will create a Source for the feed in the Organization and a corresponding Feed API Service.
Dataminr Pulse Alerts Engine UI
After installing the Dataminr Pulse Alerts Engine App and deploying it to an Organization, you can access the Dataminr Pulse Alerts Engine user interface (UI), where you can manage data ingestion from Dataminr Pulse into the Source created in the Organization.
Follow these steps to access the Dataminr Pulse Alerts Engine UI:
- Log into ThreatConnect with a System Administrator account or a user account in the Organization with an Organization role of Organization Administrator.
- From the Automation & Feeds dropdown on the top navigation bar, select Services.
- Locate the row for the Dataminr Pulse Alerts Engine Feed Service.HintYou can select Feed Service from the Service Type dropdown at the upper right to filter the screen to show only Feed API Services.
- Turn on the slider in the Enable column if the Service is not already enabled.
- Click the link in the Service’s API Path field to open the Dataminr Pulse Alerts Engine UI.
The following screens are available in the Dataminr Pulse Alerts Engine Service UI:
Dashboard
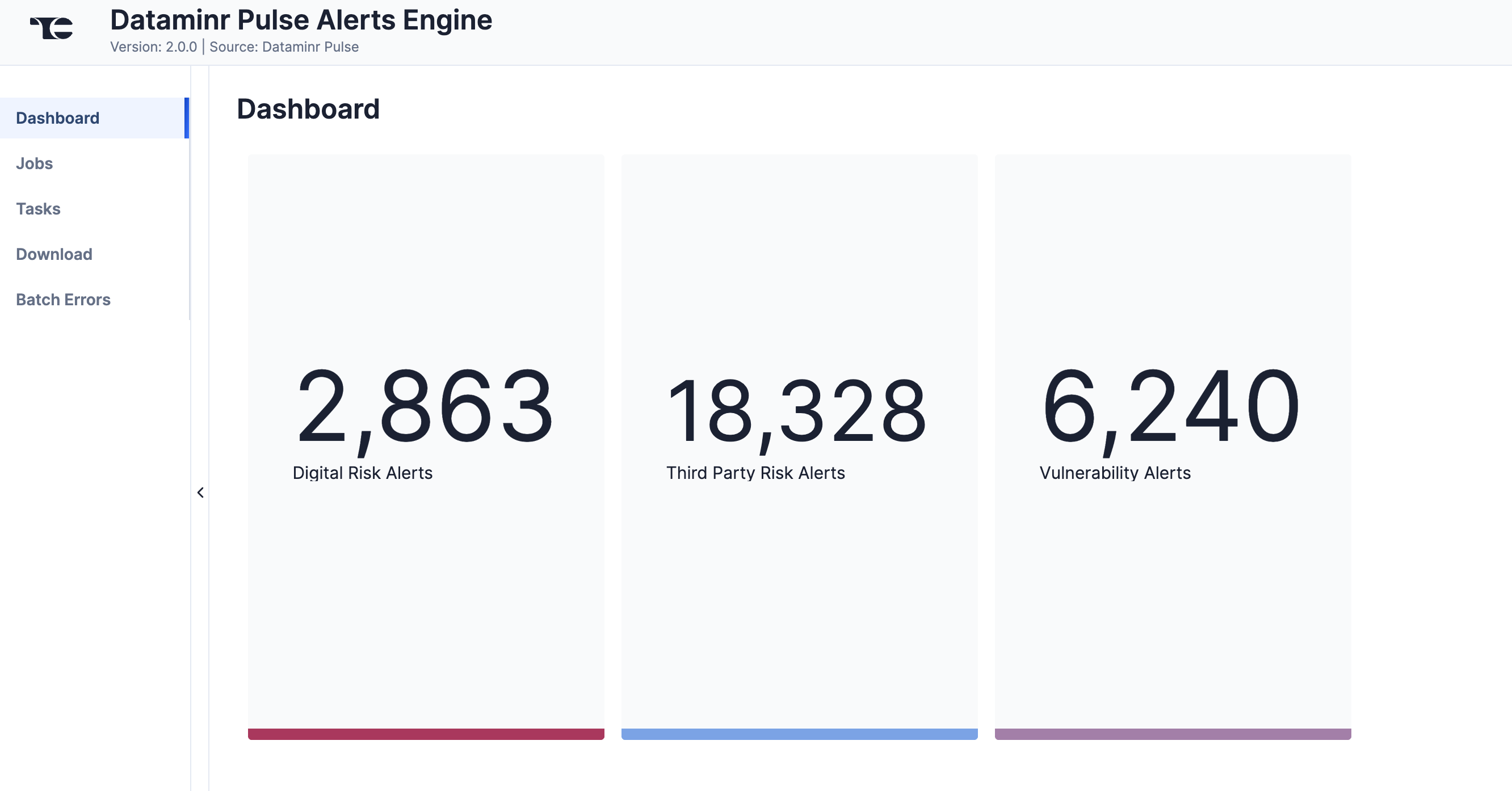
The Dashboard screen (Figure 1) provides an overview of the number of Cyber Alerts, categorized by Alert subtype, ingested from Dataminr Pulse.
Jobs
The Jobs screen (Figure 2) breaks down the ingestion of Dataminr Pulse data into manageable Job-like tasks, displaying all processes that are pending, in progress, complete, and failed. The ⋯ menu in a Job’s row provides the following options:
- Details: View details for the Job, such as download, convert, and upload start and complete times and counts of downloaded and batched Groups and Indicators.
- Download Files: Download metadata files for all Jobs and data (convert, download, and upload) files for completed Jobs.
- Batch Errors: View errors that have occurred for the Job on the Batch Errors screen.
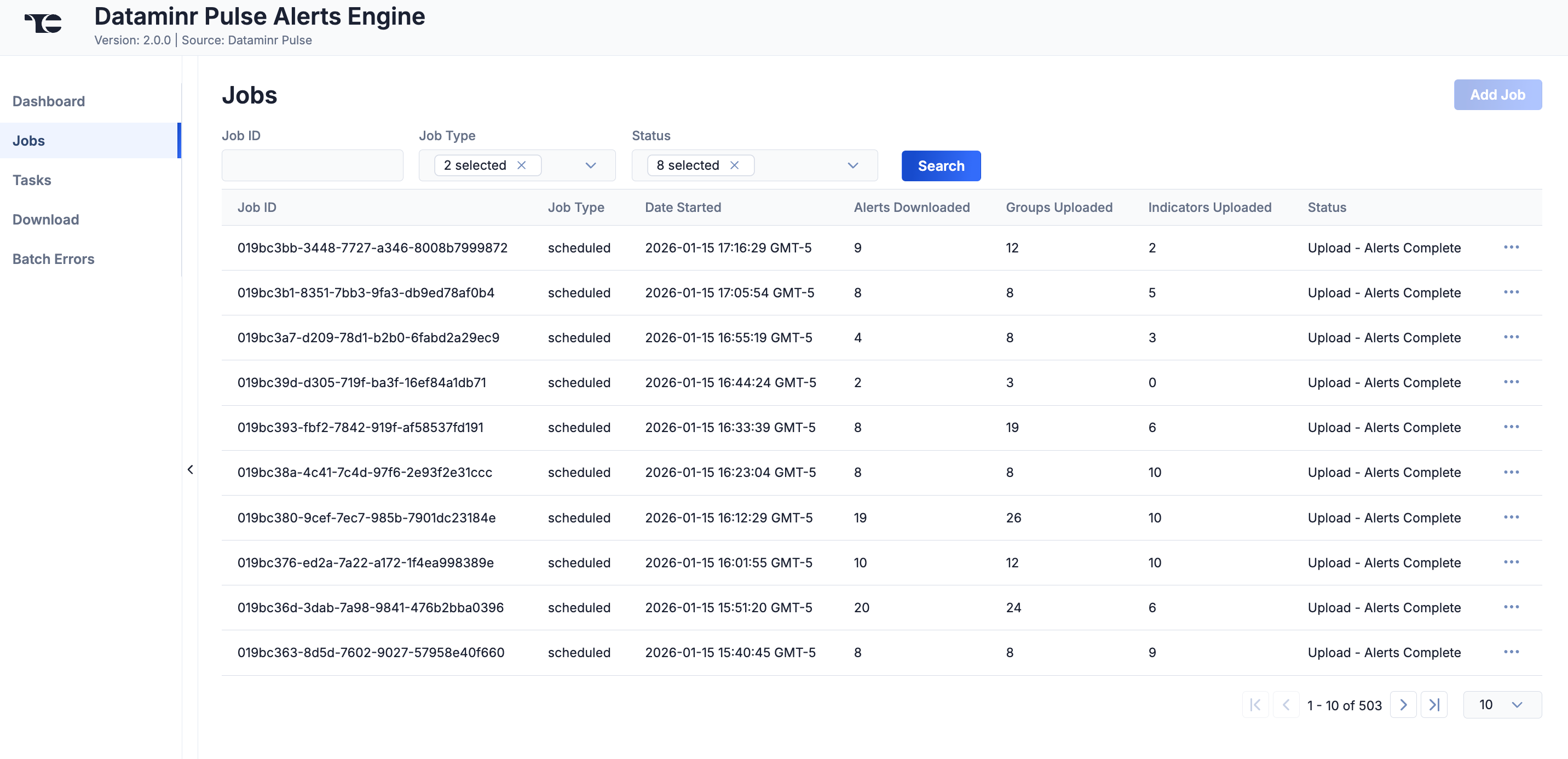
You can filter Dataminr Pulse Alerts Engine Service Jobs by the following elements:
- Job ID: Enter text into this box to search for a Job by its Job ID.
- Job Type: Select Job types to display on the Jobs screen.
- Status: Select Job statuses to display on the Jobs screen.
Tasks
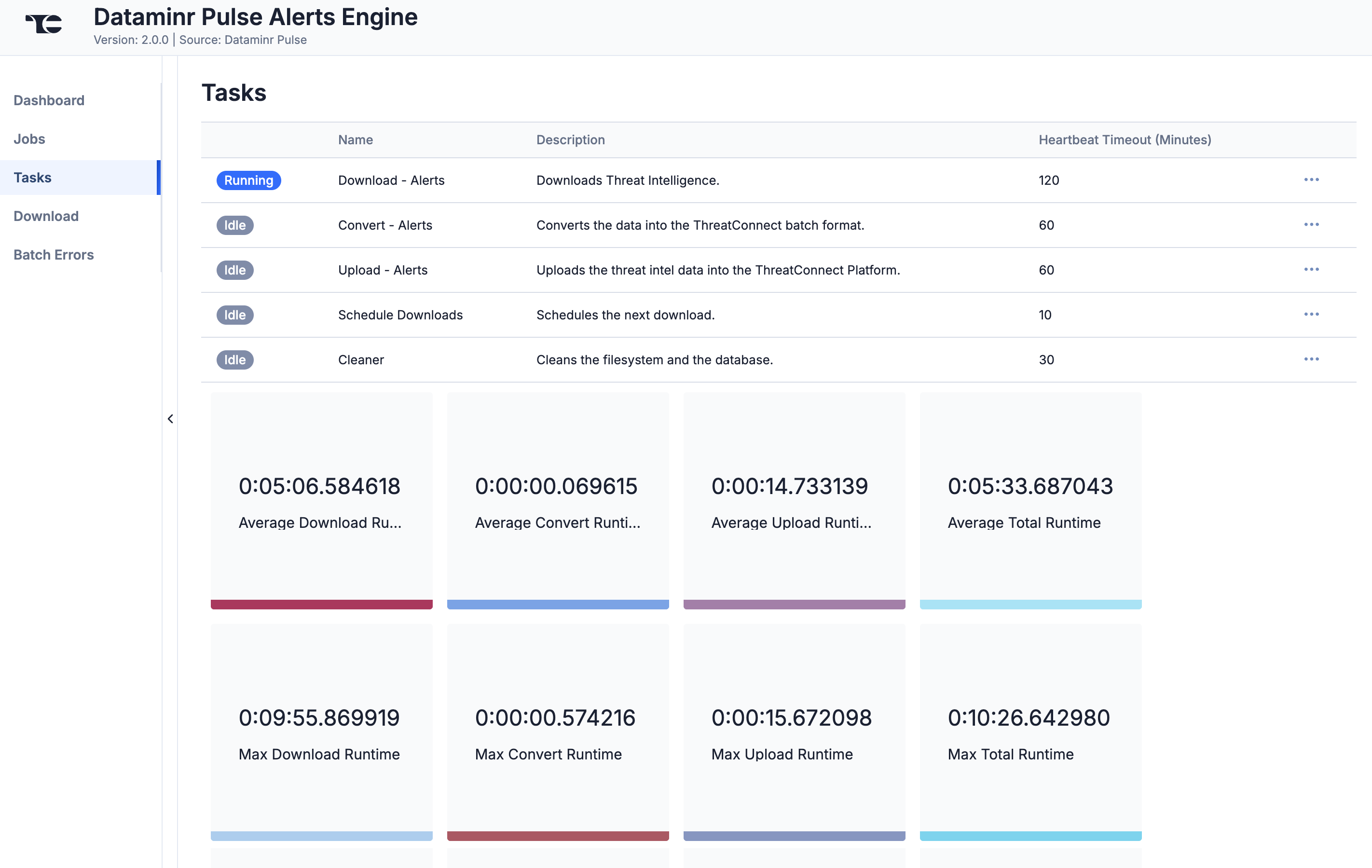
The Tasks screen (Figure 3) displays all Tasks that may be part of a Job, including each step of the download, convert, and upload processes, as well as Tasks for the Dataminr Pulse Alerts Engine Service, such as Monitor, Scheduler, and Cleaner. The current status (Idle, Paused, or Running), name, description, and heartbeat timeout length, in minutes, are displayed for each Task. The ⋯ menu in a Task’s row provides the following options, depending on the Task’s status:
- Run (idle and paused Tasks only)
- Pause (idle and running Tasks only)
- Resume (paused Tasks only)
- Kill (running Tasks only)
Under the table is a dashboard where you can view runtime analytics.
Download
The Download screen is not functional for Services for version 2.0.0 of the Dataminr Pulse Alerts Engine App.
Batch Errors
The Batch Errors screen (Figure 4) displays an overview of the batch error types that have occurred for Job requests. You can enter keywords to filter by Job ID.
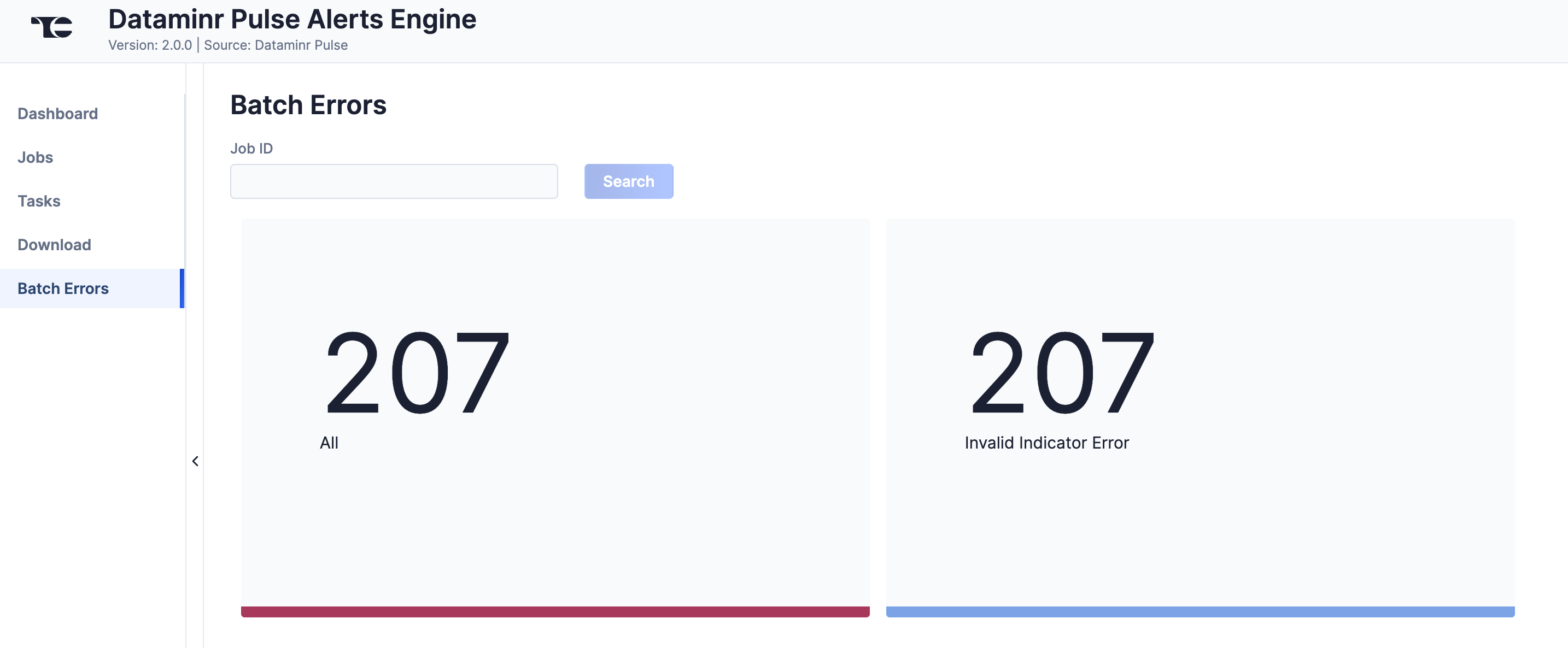
Select an error type to open a drawer containing a table with details on all batch errors of that type (Figure 5). You can enter keywords to filter by reason for error.
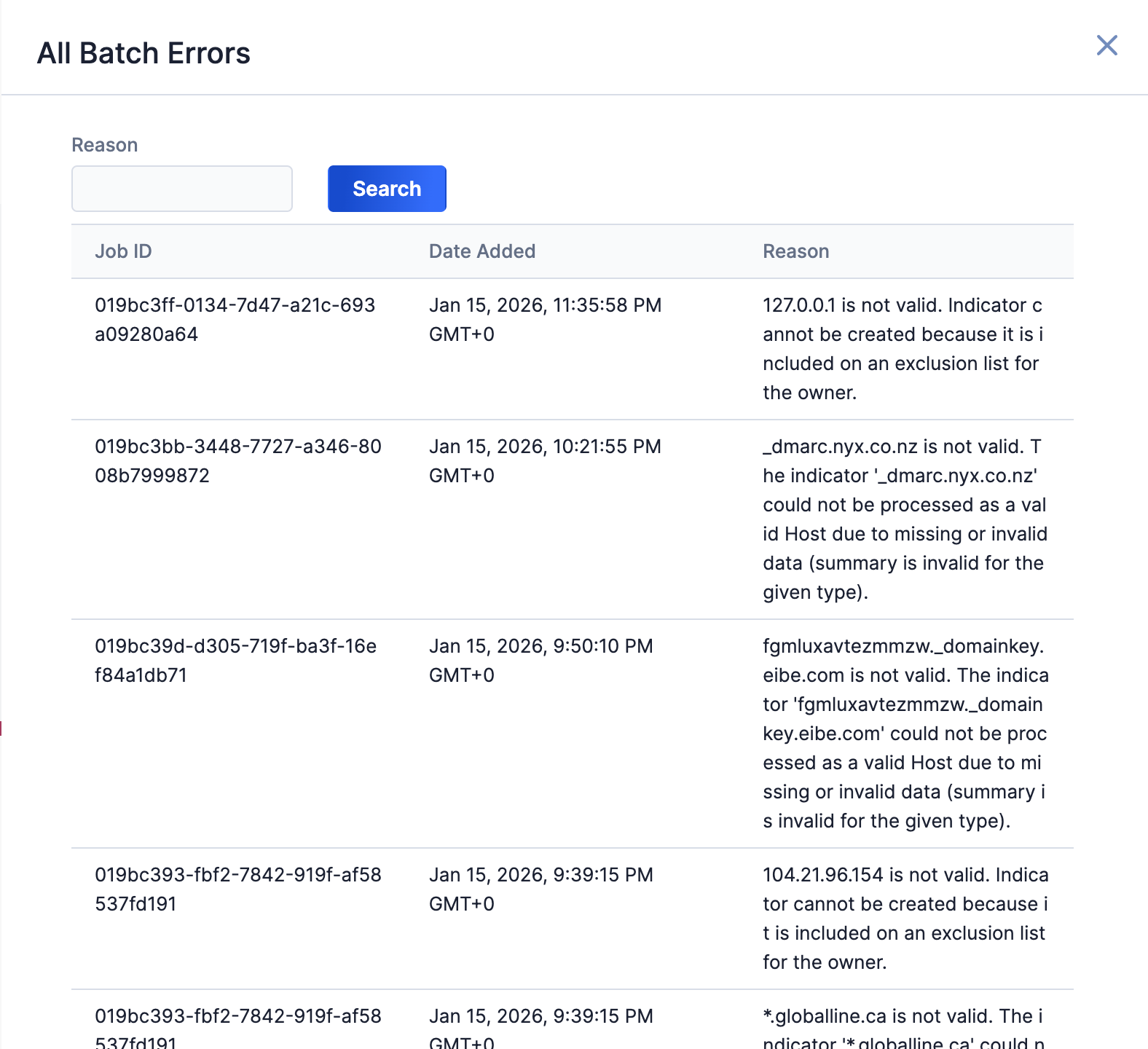
Data Mappings
The data mappings in Table 2 through Table 12 illustrate how data are mapped from Dataminr Pulse API endpoints into the ThreatConnect data model.
Alert (Cyber)
ThreatConnect object type: Event Group
| Dataminr Pulse API Field | ThreatConnect Field |
|---|---|
| alertCompanies[].name | Attribute: "Company" |
| alertId | Attribute: "External ID" |
| alertReferenceTerms[].text | Attribute: "Alert Reference" |
| alertSectors[].name | Attribute: "Industry" |
| alertTimestamp |
|
| alertTopics[].id | Part of Attribute: "Description" |
| alertTopics[].name | Attribute: "Alert Topic" |
| alertType.name | Attribute: "Priority" |
| assetsMatched.thirdPartyAssets[].name | Attribute: "3rd Party Asset" |
| dataminrAlertUrl | Attribute: "Source" |
| estimatedEventLocation.name | Attribute: "Location Name" |
| estimatedEventLocation.coordinates[0] | Attribute: "Latitude" |
| estimatedEventLocation.coordinates[1] | Attribute: "Longitude" |
| estimatedEventLocation.probabilityRadius | Attribute: "Probability Radius" |
| headline | Name/Summary |
| intelAgents[].summary[].title |
|
| intelAgents[].summary[].content[] |
|
| linkedAlerts[].parentAlertId | Associated Event Group |
| listsMatched[].id | Part of Attribute: "Description" |
| listsMatched[].name |
|
| listsMatched[].topicIds[] | Part of Attribute: "Description" |
| listsMatched[].subType |
|
| liveBrief[].timestamp | Attribute: "Additional Analysis and Context" |
| liveBrief[].version | Attribute: "Additional Analysis and Context" |
| liveBrief[].summary |
|
| publicPost.timestamp | Part of Attribute: "Description" |
| publicPost.href | Part of Attribute: "Description" |
| publicPost.channels[] |
|
| publicPost.media[].type | Part of Attribute: "Description" |
| publicPost.media[].href | Part of Attribute: "Description" |
| subHeadline.title | Part of Attribute: "Description" |
| subHeadline.content[] | Part of "Attribute: "Description" |
| metadata.cyber.addresses[].ip | Associated Address Indicator |
| metadata.cyber.asOrgs[].asn | Associated ASN Indicator |
| metadata.cyber.malware[].name | Associated Malware Group |
intelAgents[].discoveredEntities[].name | Associated Intrusion Set, Malware, or Vulnerability Group |
| metadata.cyber.threatActors[].name | Associated Intrusion Set Group |
| metadata.cyber.URL[].name | Associated Host or URL Indicator |
| metadata.cyber.vulnerabilities[].id | Associated Vulnerability Group |
Address
ThreatConnect object type: Address Indicator
| Dataminr Pulse API Field | ThreatConnect Field |
|---|---|
| metadata.cyber.addresses[].ip | Name/Summary |
ASN
ThreatConnect object type: ASN Indicator
| Dataminr Pulse API Field | ThreatConnect Field |
|---|---|
| metadata.cyber.asOrgs[].asn | Name/Summary |
| metadata.cyber.asOrgs[].asOrg | Attribute: "ASN Host" |
Malware From Intel Agent
ThreatConnect object type: Malware Group
| Dataminr Pulse API Field | ThreatConnect Field |
|---|---|
| intelAgents[].discoveredEntities[].name | Name/Summary |
| intelAgents[].discoveredEntities[].summary | Attribute: "Description" |
| intelAgents[].discoveredEntities[].publishedDate | External Date Added |
| intelAgents[].discoveredEntities[].affectedOperatingSystems | Attribute: "Operating System" |
| intelAgents[].discoveredEntities[].yaraRules[] | Part of Attribute: "Description" |
| intelAgents[].discoveredEntities[].threatActors[].name | Associated Intrusion Set Group |
Malware From Metadata
ThreatConnect object type: Malware Group
| Dataminr Pulse API Field | ThreatConnect Field |
|---|---|
| metadata.cyber.malware[].name | Name/Summary |
Threat Actor From Intel Agent
ThreatConnect object type: Intrusion Set Group
| Dataminr Pulse API Field | ThreatConnect Field |
|---|---|
| intelAgents[].discoveredEntities[].name | Name/Summary |
| intelAgents[].discoveredEntities[].summary | Attribute: "Description" |
| intelAgents[].discoveredEntities[].publishedDate | External Date Added |
| intelAgents[].discoveredEntities[].ttps[].techniqueId | ATT&CK® Tag |
Threat Actor From Metadata
ThreatConnect object type: Intrusion Set Group
| Dataminr Pulse API Field | ThreatConnect Field |
|---|---|
| metadata.cyber.threatActors[].name | Name/Summary |
| metadata.cyber.threatActors[].countriesOfOrigin[] | Attribute: "Source Geography" |
| metadata.cyber.threatActors[].aliases[] | Attribute: "Aliases" |
URL
ThreatConnect object type: Host or URL Indicator
| Dataminr Pulse API Field | ThreatConnect Field |
|---|---|
| metadata.cyber.URL[].name | Name/Summary |
Vulnerability From Intel Agent
ThreatConnect object type: Vulnerability Group
| Dataminr Pulse API Field | ThreatConnect Field |
|---|---|
| intelAgents[].discoveredEntities[].name | Name/Summary |
| intelAgents[].discoveredEntities[].summary | Attribute: "Description" |
| intelAgents[].discoveredEntities[].publishedDate | External Date Added |
| intelAgents[].discoveredEntities[].products[].productVendor intelAgents[].discoveredEntities[].products[].productName | Attribute: "Vulnerable CPE" |
| intelAgents[].discoveredEntities[].knownExploitedDate | Attribute: "Known Exploited Date" |
| intelAgents[].discoveredEntities[].exploitPocLinks[] | Attribute: "Exploit POC Link" |
| intelAgents[].discoveredEntities[].epssScore | Attribute: "EPSS Score" |
| intelAgents[].discoveredEntities[].cvss | Attribute: "CVSS Base Score" |
| intelAgents[].discoveredEntities[].exploitable | Attribute: "Has Exploit" |
Vulnerability From Metadata
ThreatConnect object type: Vulnerability Group
| Dataminr Pulse API Field | ThreatConnect Field |
|---|---|
| metadata.cyber.vulnerabilities[].id | Name/Summary |
| metadata.cyber.vulnerabilities[].publishedDate | External Date Added |
| metadata.cyber.vulnerabilities[].products[].productVersion metadata.cyber.vulnerabilities[].products[].productVendor metadata.cyber.vulnerabilities[].products[].productName | Attribute: "Vulnerable CPE" |
| metadata.cyber.vulnerabilities[].knownExploitedDate | Attribute: "Known Exploited Date" |
| metadata.cyber.vulnerabilities[].exploitPocLinks[] | Attribute: "Exploit POC Link" |
| metadata.cyber.vulnerabilities[].epssScore | Attribute: "EPSS Score" |
| metadata.cyber.vulnerabilities[].cvss | Attribute: "CVSS Base Score" |
Frequently Asked Questions (FAQ)
When does ThreatConnect start ingesting data from Dataminr Pulse?
If you select the Run Feeds After Deployment checkbox in the Feed Deployer when deploying the Dataminr Pulse Alerts Engine App to an Organization, ThreatConnect will ingest Dataminr Pulse data once you click DEPLOY, with the time of deployment being the starting time from which to retrieve Alerts. This means that ThreatConnect will ingest only Alerts created at the time of deployment or later; it will not ingest Alerts created before the time of deployment. If you do not select the Run Feeds After Deployment checkbox, ThreatConnect will ingest Dataminr Pulse data once you turn on the corresponding Service for the App on the Services screen.
Does ThreatConnect ingest Cyber Alerts from all Dataminr Pulse Alert Lists?
If you leave the Dataminr List IDs field blank in the Feed Deployer when deploying the Dataminr Pulse Alerts Engine App to an Organization, then ThreatConnect will ingest Cyber Alerts from all Dataminr Pulse Alert Lists you have provisioned. If you enter List IDs, then ThreatConnect will ingest Cyber Alerts only from the Dataminr Pulse Alert Lists with those IDs. Please check your Dataminr API rate limits to inform your decision on the number of Alerts you can ingest into ThreatConnect.
How can I filter my ThreatConnect data to show only Alerts from select Alert Lists from Dataminr Pulse?
Use a ThreatConnect Query Language (TQL) query to filter ingested Dataminr Pulse Alerts by Alert List. For example, the following query returns only Alerts that belong to the Vulnerability Flash Alert List (that is, the query returns only Event Groups that have an Alert List Attribute with a value of Vulnerability Flash):
typeName in ("Event") and attributeAlert_List in ("Vulnerability Flash")- Select only the Source for which the Dataminr Pulse Alerts Engine Service is configured from the owners dropdown on the Search: Groups screen or in My Intel Sources on the Legacy Browse screen.
- Add the following to the TQL query, replacing
Dataminr Pulse Alerts Sourcewith the name of the Source for which the Dataminr Pulse Alerts Engine Service is configured:and (ownerName in ("Dataminr Pulse Alerts Source"))
How can I filter my ThreatConnect data to show only Alerts with a particular priority from Dataminr Pulse?
Use a TQL query to filter ingested Dataminr Pulse Alerts by priority. For example, the following query returns only Alerts whose priority is either Urgent or Flash (that is, the query returns only Event Groups that have a Priority Attribute with a value of Urgent or Flash):
typeName in ("Event") and attributePriority in ("Urgent", "Flash")- Select only the Source for which the Dataminr Pulse Alerts Engine Service is configured from the owners dropdown on the Search: Groups screen or in My Intel Sources on the Legacy Browse screen.
- Add the following to the TQL query, replacing
Dataminr Pulse Alerts Sourcewith the name of the Source for which the Dataminr Pulse Alerts Engine Service is configured:and (ownerName in ("Dataminr Pulse Alerts Source"))
How can I filter my ThreatConnect data to show only Alerts with AI summaries from Dataminr Pulse?
Use a TQL query to filter ingested Dataminr Pulse Alerts for Alerts that have AI summary data. For example, the following query returns only Alerts that have Intel Agent or Live Brief AI summaries (that is, the query returns only Event Groups that have a Tag with a value of Intel Agent or Live Brief):
typeName in ("Event") and tag in ("Intel Agent", "Live Brief")Similarly, the following query returns only Alerts with AI summary data provided by Dataminr and containing the text Microsoft Server Message Block (that is, the query returns only Event Groups that have AI insights that are provided by Dataminr and that contain the text Microsoft Server Message Block):
typeName in ("Event") and aiProvider="Dataminr" and insights contains "Microsoft Server Message Block"- Select only the Source for which the Dataminr Pulse Alerts Engine Service is configured from the owners dropdown on the Search: Groups screen or in My Intel Sources on the Legacy Browse screen.
- Add the following to the TQL query, replacing
Dataminr Pulse Alerts Sourcewith the name of the Source for which the Dataminr Pulse Alerts Engine Service is configured:and (ownerName in ("Dataminr Pulse Alerts Source"))
ThreatConnect® is a registered trademark, and TC Exchange™ is a trademark, of ThreatConnect, Inc.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.
JavaScript® is a registered trademark of Oracle Corporation.
30087-02 EN Rev. A


