- 11 Nov 2025
- 4 Minutes to read
-
Print
-
DarkLight
-
PDF
Configure Azure ADFS as SAML Provider
- Updated on 11 Nov 2025
- 4 Minutes to read
-
Print
-
DarkLight
-
PDF
Configure SAML authentication with Microsoft Azure ADFS
REFERENCE
The following link provides steps on how to setup SSO in Azure ADFS:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/add-application-portal-setup-sso
Polarity-specific setup instructions can be found below.
Configure Azure ADFS for Polarity
Create a “Polarity App”
Navigate to the Azure Active Directory Admin Center
https://aad.portal.azure.com
From the left navigation menu select "Applications" -> "Enterprise applications" -> "New Application" -> "Create your own application".
Name your app (e.g., "Polarity").
Select the radio button for "Integrate any other application you don't find in the gallery (Non-gallery)".
Single Sign On
Once the application is created, select the option to "Set up single sign on". You may also find this option in the left navigation menu.
Select the "SAML" single sign-on method.
Basic SAML Configuration
In the "Basic SAML Configuration" block, click on the "Edit" icon
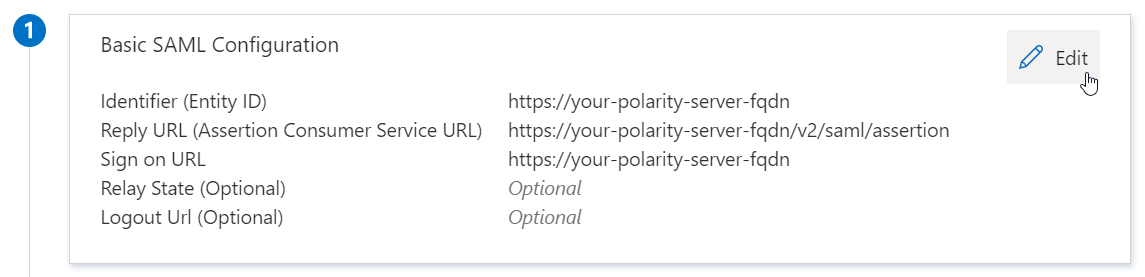
On the “Basic SAML Configuration” page, fill in the fields as specified below:
Identifier (Entity ID)
https://<your-polarity-server-fqdn>
Reply URL (Assertion Consumer Service URL)
https://<your-polarity-server-fqdn>/sso/sp/consume/saml
Sign on URL (Optional)
Optional but can be set to:
https://<your-polarity-server-fqdn>Replace
<your-polarity-server-fqdn>with the fully-qualified domain name of your Polarity server.
Default Relay State
https://<your-polarity-server-fqdn>/auth-success
Logout URL (Optional)
Not needed
Once you have filled in the "Identifier" and "Reply URL" click on the "Save" button.
Attributes & Claims
Click on the "Edit" button in the "Attributes & Claims” block.
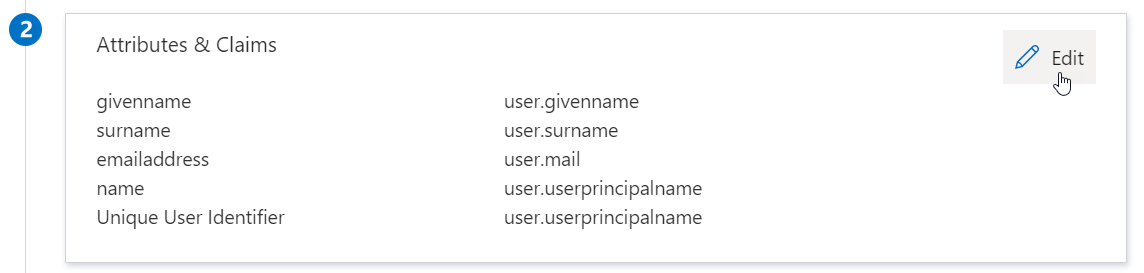
The page will show two columns. A "Claim name" column and a "Value" column. You will need to identify three required values when configuring SAML on the Polarity Server:
An email value
A username value
A full name value
In most cases there will already be an email address
user.mail) and usernameuser.userprincipalname) claim.For the full name value we suggest creating a new claim by clicking on the "Add new claim" and filling in the following values:
Name:
displaynameSource:
AttributeSource attribute:
user.displayname
Click on "Save" when done.
Note the "Claim name" for the
user.mail,user.displayname, anduser.userprincipalnamevalues. The “Claim name” for each of these values will be used when configuring SAML on the Polarity Server.
SAML Certificates
From the "SAML Certificates" block, download the "Federation Metadata XML" file. We will use the content of this file when we configure the Polarity Server to use SAML Authentication.
Users and Groups
We recommend controlling access to Polarity by granting access to the Polarity application in Azure via the “Users and groups” settings within the app, as opposed to forcing a Group attribute.
Configure Polarity for Azure ADFS
Login to the Polarity Server as a local administrator (browser recommended for this process).
Navigate to "Server Configuration" in the left navigation panel.
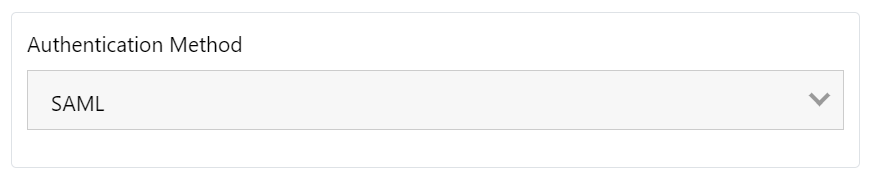
Click on the "Client Authentication" tab at the top of the page.
From the "Authentication Method" drop down select "SAML".
Fill in the following configuration details using information from the Azure app created in the previous steps:
Polarity Server Fully Qualified Domain Name (FQDN)
Fill in the FQDN of your Polarity Server to include the scheme (https://).
SAML Identity Provider (IdP) XML Metadata
Paste in the content of the full Federation Metadata XML file that was exported from Azure.
Sign in button label
You can customize the label on the SAML sign-in button by entering text here.
Username Attribute
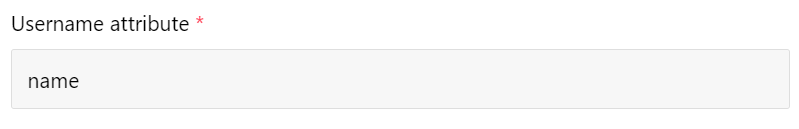
The username attribute value must be a unique value for every user on the system. In most cases you will want to use the
user.userprincipalnamevalue which will have the "Claim name":user.userprincipalnamehttp://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
You can also use an email address for the username attribute in which in most cases will be the "Claim name":
user.mailhttp://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
When setting the username attribute in the Polarity SAML configuration you will only provide the last segment of the claim name.
As an example, if you wanted to use the claim
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameyou would only enter the value name into Polarity.IMPORTANT!
Be sure to only use the last segment of the "Claim name" when configuring attributes within Polarity.
Email Attribute
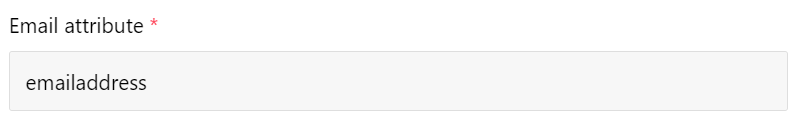
The email attribute must be a unique and valid email for each user in Polarity.
The Email Attribute will typically use the
user.mailvalue from ADFS.In most cases, the Email Attribute in Polarity use the following "Claim name":
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
As we only use the last segment of the "Claim Name", you would set the Email attribute in Polarity to
emailaddress.
Full name attribute
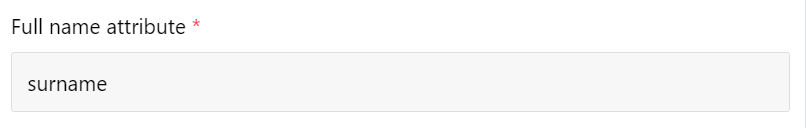
The full name attribute contains the user's given and surname.
In most cases you will want to use the value
user.displayname.There is usually no default "Claim name" for the
user.displaynameattribute.If you added this claim when configuring SAML within Azure then the "Claim name" would be
displayname.
If you did not add a
displaynameclaim when configuring SAML in Azure, you can pick either theuser.givennameoruser.surnamevalues, which are available by default in most cases.http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
orhttp://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
As an example, if you wanted to use the
surnameclaim, the Full name attribute would be set tosurname.
Group attribute
You can optionally set a "Group attribute" which is used to identify which Azure ADFS group(s) an authorized user may belong to. You can then authorize specific groups using the "Authorized groups regular expression" option.
If you leave this blank, all authenticated SAML users will be able authorized to login to the Polarity Server.
NOTE
We highly recommend leveraging the "Users and Groups" permissions within Azure ADFS to control which users and groups have access to the Polarity application, rather than controlling access from the Polarity Server.
Authorized groups regular expression
Provide one or more groups separated by a pipe (
|).More complex group matches can be accomplished with a custom regular expression.
The provided regex will be run against the provided "Group attribute" of the user.
If the regex passes, the user will be granted access to the Polarity Server.
After entering the required options in Polarity, click on "Apply Changes" in the top right.
When you navigate to the Polarity login screen, you should now see the option to login via your SAML Identity Provider.


