- 30 Nov 2023
- 6 Minutes to read
-
Print
-
DarkLight
-
PDF
Accenture iDefense Intelligence Engine Integration User Guide
- Updated on 30 Nov 2023
- 6 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The ThreatConnect® integration with Accenture™ iDefense® ingests data from the Accenture iDefense intel collection into ThreatConnect for analysis and response actions. The integration downloads intel Indicators (Domain, File, IPv4, IPv6, and URL), Campaigns, Malware, Reports, Signatures (YARA), Threat Actors, Tools, and Vulnerabilities.
Accenture iDefense delivers data in the STIX™ 2.1 format via a TAXII™ 2.1 server.
Dependencies
ThreatConnect Dependencies
- Active ThreatConnect Application Programming Interface (API) key
- ThreatConnect instance with version 7.0 or newer installed
Accenture iDefense Dependencies
- Active subscription to Accenture iDefense with username and password credentials
Application Setup and Configuration
Installing the App
- Log into ThreatConnect with a System Administrator account.
- Install the Accenture iDefense Intelligence Engine App via TC Exchange™.
- Use the ThreatConnect Feed Deployer to set up and configure the Accenture iDefense Intelligence Engine App.
Configuration Parameters
Parameter Definitions
The parameters defined in Table 1 apply to the configuration parameters available when using the Feed Deployer to configure the App.
| Name | Description | Required? |
|---|---|---|
| Source Tab | ||
| Sources to Create | The name of the Source to be created. | Yes |
| Owner | The Organization in which the Source will be created. | Yes |
| Parameters Tab | ||
| Launch Server | Select tc-job as the launch server for the Service corresponding to the Feed API Service App. | Yes |
| Indicator Types | Select one or more Accenture iDefense Indicator types to ingest. Available choices include the following:
| Yes |
| Group Types | Select one or more Accenture iDefense Group types to ingest. Available choices include the following:
| Yes |
| Schedule Interval (Hours) | The number of hours between each scheduled update interval for the App. The default value is 1. | Yes |
| Variables Tab | ||
| Accenture iDefense Password | The Accenture iDefense account password. | Yes |
| Accenture iDefense Username | The Accenture iDefense account username. | Yes |
Accenture iDefense Intelligence Engine
After successfully configuring and activating the Feed API Service, you can access the Accenture iDefense Intelligence Engine user interface (UI). This UI allows you to interact with and manage the Accenture iDefense integration.
Follow these steps to access the UI:
- Log into ThreatConnect with a System Administrator account.
- On the top navigation bar, hover over Playbooks and select Services. The Services tab of the Playbooks screen will be displayed.
- Locate the Accenture iDefense Intelligence Engine Feed API Service and then click the link in the Service’s API Path field. The DASHBOARD screen of the Accenture iDefense Intelligence Engine UI will open in a new browser tab.
The following screens are available in the Accenture iDefense Intelligence Engine UI:
- DASHBOARD
- JOBS
- TASKS
- DOWNLOAD
- REPORT
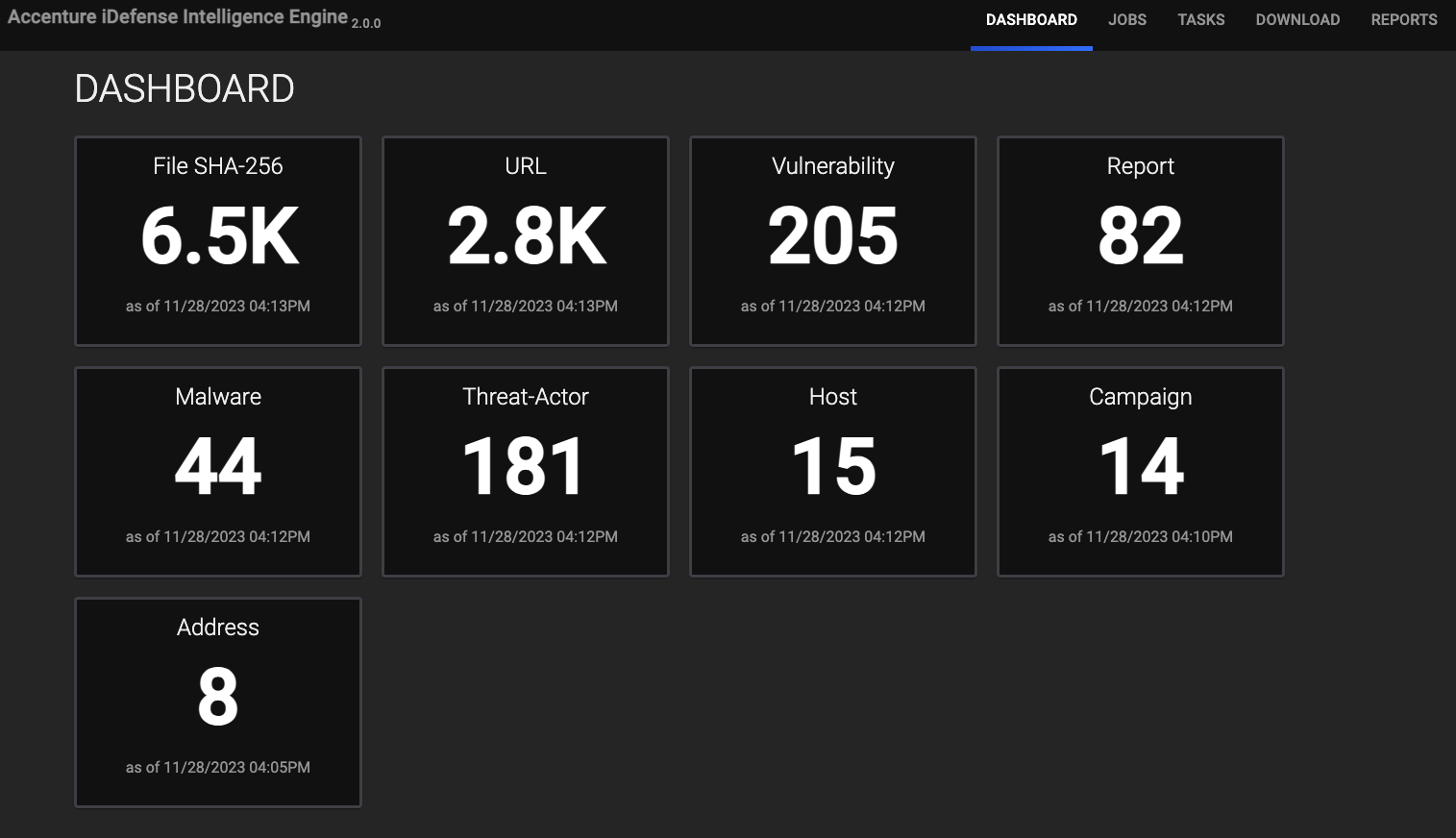
DASHBOARD
The DASHBOARD screen (Figure 1) provides an overview of the total number of Indicators (Domain, File, IPv4, IPv6, and URL), Campaigns, Malware, Reports, Signatures (YARA), Threat Actors, Tools, and Vulnerabilities retrieved from Accenture iDefense. Depending on the data available to you, cards representing all or a subset of these object types will be displayed on the DASHBOARD screen.
JOBS
The JOBS screen (Figure 2) breaks down the ingestion of Accenture iDefense data into manageable Job-like tasks.
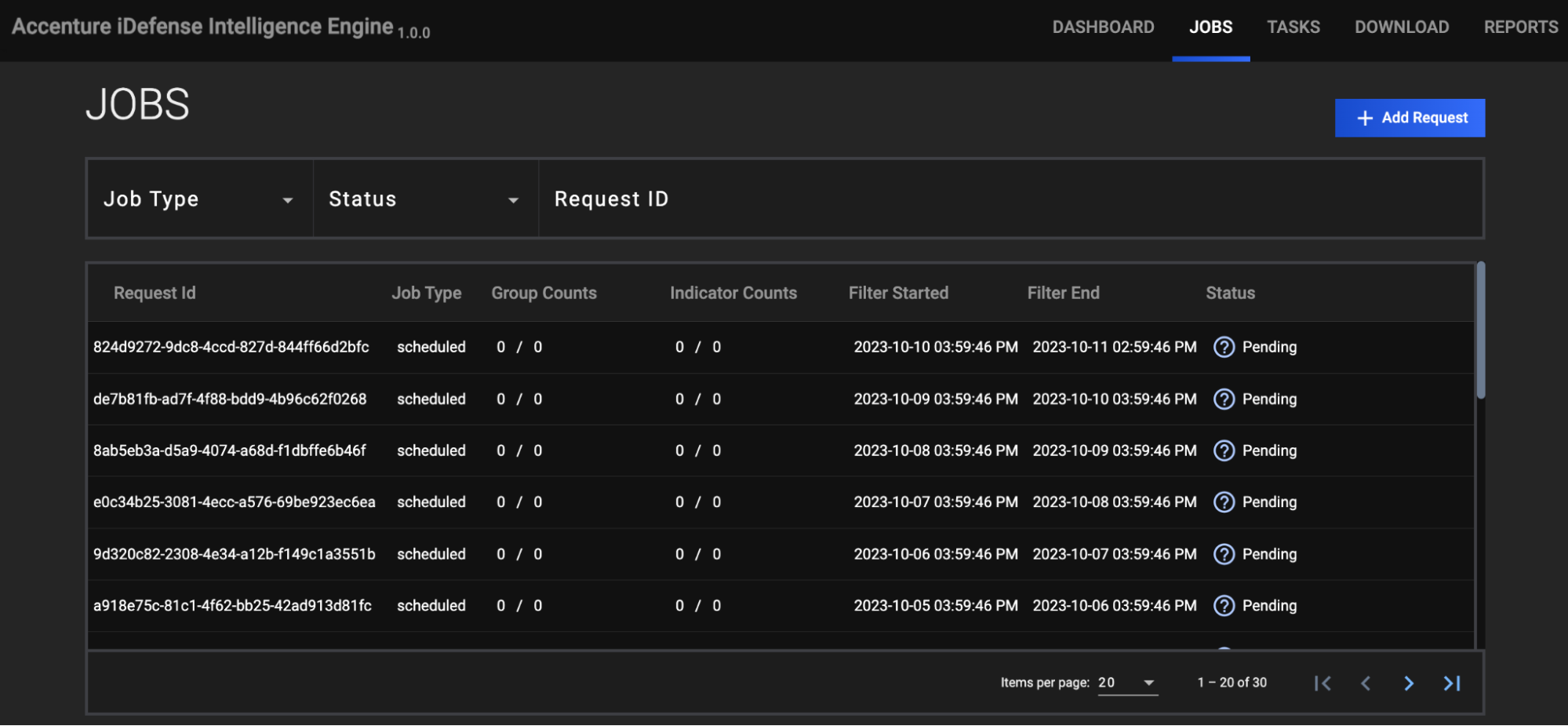
- Job Type: If desired, select a Job type by which to filter Jobs. Available types include ad-hoc and scheduled.
- Status:If desired, select a Job status by which to filter Jobs. Available statuses include the following:
- Download In Progress
- Download Complete
- Convert In Progress
- Convert Complete
- Upload In Progress
- Upload Complete
- Request ID: If desired, enter text into this box to search for a specific Job by its request ID.
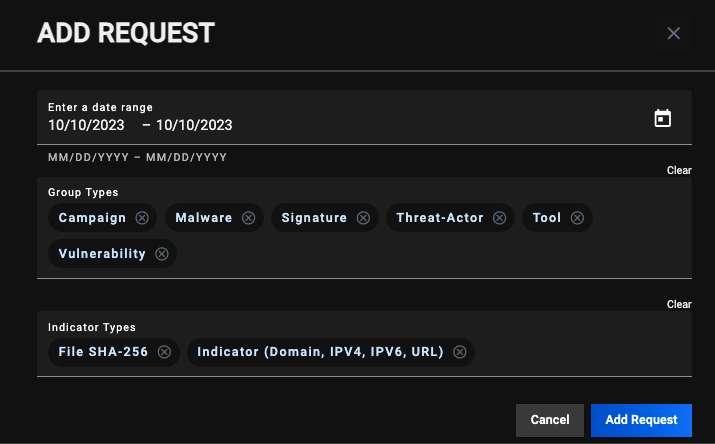
- + Add Request: Click this button to display the ADD REQUEST window (Figure 4). On this window, you can specify the date range and object types for an ad-hoc Job request. After a Job request is added, it will be displayed in the table on the JOBS screen (Figure 2), and its Job type will be listed as ad-hoc.
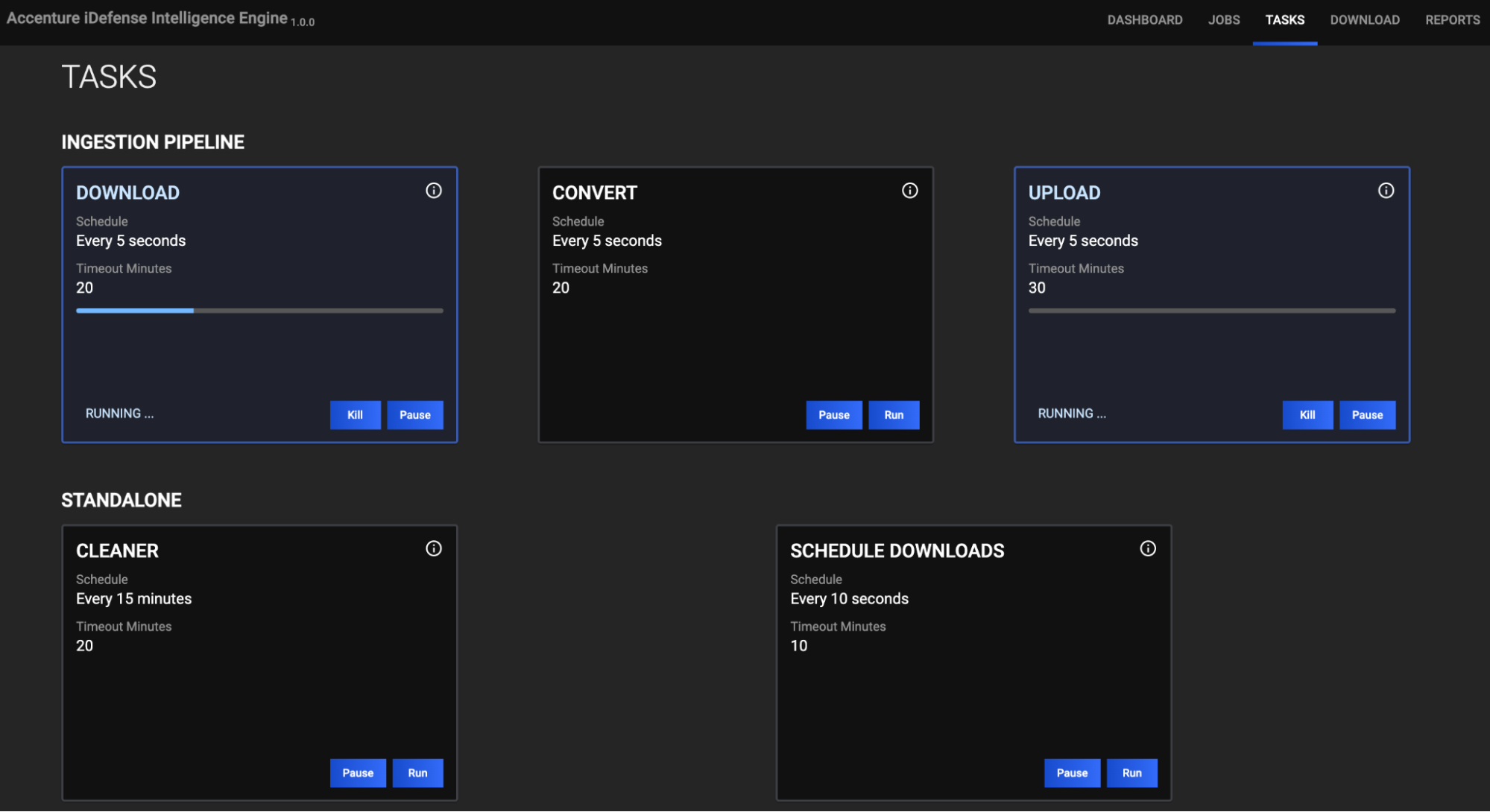
TASKS
The TASKS screen (Figure 4) is where you can view and manage the Tasks for each Job.
DOWNLOADS
The DOWNLOADS screen (Figure 5) is where you can download data exactly as they appear in Accenture iDefense.
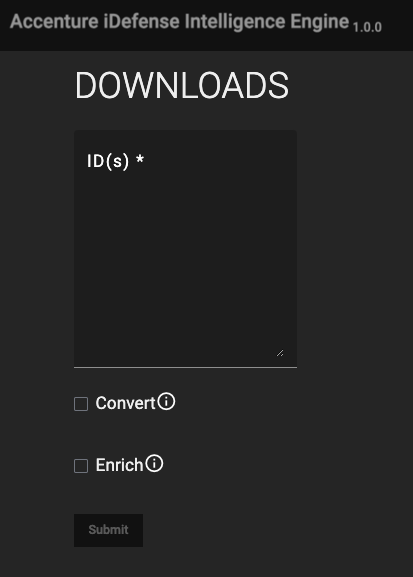
- ID(s): Enter the Accenture iDefense ID(s) for the object(s) to download. Data will be retrieved in JavaScript® Object Notation (JSON) format.
- Convert: Select this checkbox to convert the threat intelligence data to ThreatConnect batch format.
- Enrich: Select this checkbox to submit the threat intelligence data to the ThreatConnect Batch API.
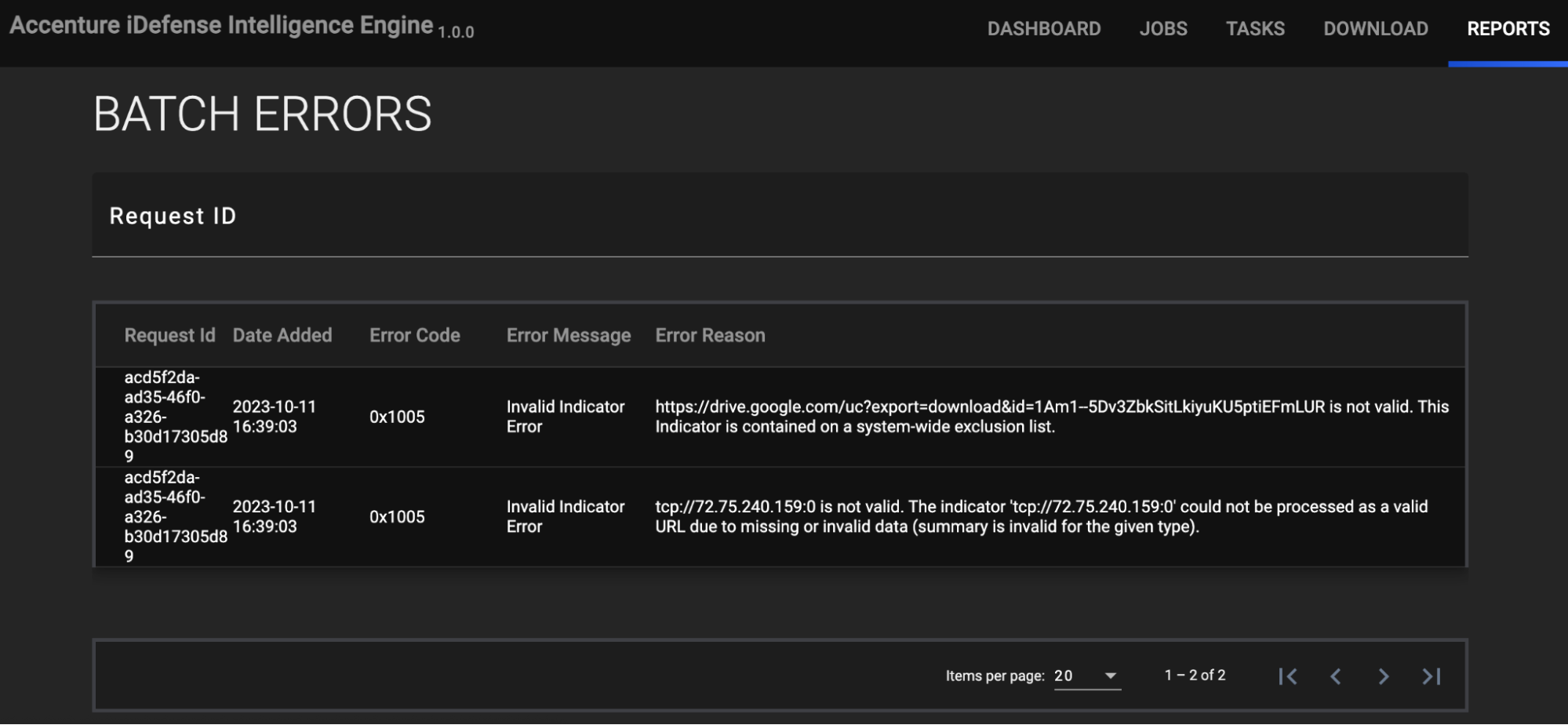
REPORTS
The REPORTS screen provides a BATCH ERRORS view (Figure 6) that displays batch errors for each request in a tabular format. Details provided for each error include the error’s code, message, and reason.
Data Mappings
The data mappings in Table 2 through Table 13 illustrate how data are mapped from Accenture iDefense API endpoints into the ThreatConnect data model.
IPv4
ThreatConnect object type: Address Indicator
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| confidence | Threat Rating |
| created | Attribute: "External Date Created" |
| id | Attribute: "External ID" |
| labels | Tags |
| modified | Attribute: "External Date Modified" |
| name | IP Address |
| object_marking_ref/name | Security Labels |
| revoked | Indicator Status (set to active if revoked is false; set to inactive if revoked is true) |
IPv6
ThreatConnect object type: Address Indicator
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| confidence | Threat Rating |
| created | Attribute: "External Date Created" |
| id | Attribute: "External ID" |
| labels | Tags |
| modified | Attribute: "External Date Modified" |
| name | IP Address |
| object_marking_ref/name | Security Labels |
| revoked | Indicator Status (set to active if revoked is false; set to inactive if revoked is true) |
URL
ThreatConnect object type: URL Indicator
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| confidence | Threat Rating |
| created | Attribute: "External Date Created" |
| id | Attribute: "External ID" |
| labels | Tags |
| modified | Attribute: "External Date Modified" |
| name | URL |
| object_marking_ref/name | Security Labels |
| revoked | Indicator Status (set to active if revoked is false; set to inactive if revoked is true) |
Domain
ThreatConnect object type: Host Indicator
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| confidence | Threat Rating |
| created | Attribute: "External Date Created" |
| id | Attribute: "External ID" |
| labels | Tags |
| modified | Attribute: "External Date Modified" |
| name | Host Name |
| object_marking_ref/name | Security Labels |
| revoked | Indicator Status (set to active if revoked is false; set to inactive if revoked is true) |
File
ThreatConnect object type: File Indicator
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| confidence | Threat Rating |
| created | Attribute: "External Date Created" |
| id | Attribute: "External ID" |
| labels | Tags |
| modified | Attribute: "External Date Modified" |
| object_marking_ref/name | Security Labels |
| pattern | Hash Value |
| revoked | Indicator Status (set to active if revoked is false; set to inactive if revoked is true) |
Threat Actor
ThreatConnect object type: Adversary Group
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| aliases | Attribute: "Alias" |
| confidence | Attribute: "Confidence" |
| created | Attribute: "External Date Created" |
| description | Description |
| external_references | Attribute: "External Reference" |
| first_seen | Attribute: "First Seen" |
| goals | Attribute: "Goal" |
| id | Attribute: "External ID" |
| labels | Tags |
| last_seen | Attribute: "Last Seen" |
| modified | Attribute: "External Date Modified" |
| name | Name/Summary |
| object_marking_ref/name | Security Labels |
| personal_motivations | Attribute: "Personal Motivation" |
| primary_motivation | Attribute: "Adversary Motivation Type" |
| resource_level | Attribute: "Resource Level" |
| roles | Attribute: "Role" |
| secondary_motivations | Attribute: "Secondary Motivation Type" |
| sophistication | Attribute: "Sophistication" |
| threat_actor_types | Attribute: "Threat Actor Type" |
Malware
ThreatConnect object type: Malware Group
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| aliases | Attribute: "Alias" |
| confidence | Attribute: "Confidence" |
| created | Attribute: "External Date Created" |
| description | Description |
| first_seen | Attribute: "First Seen" |
| id | Attribute: "External ID" |
| kill_chain_phases | Attribute: "Phase of Intrusion" |
| labels | Tags |
| last_seen | Attribute: "Last Seen" |
| modified | Attribute: "External Date Modified" |
| name | Name/Summary |
| object_marking_ref/name | Security Labels |
Report
ThreatConnect object type: Report Group
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| confidence | Attribute: "Confidence" |
| created | Attribute: "External Date Created" |
| description | Description |
| id | Attribute: "External ID" |
| labels | Tags |
| modified | Attribute: "External Date Modified" |
| name | Name/Summary |
| object_marking_ref/name | Security Labels |
| object_refs/name | Tags |
| published | Published Date |
| report_type | Attribute: "Report Type" |
Tool
ThreatConnect object type: Tool Group
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| aliases | Attribute: "Alias" |
| confidence | Attribute: "Confidence" |
| created | Attribute: "External Date Created" |
| description | Description |
| id | Attribute: "External ID" |
| kill_chain_phases | Attribute: "Phase of Intrusion" |
| labels | Tags |
| modified | Attribute: "External Date Modified" |
| name | Name/Summary |
| object_marking_ref/name | Security Labels |
| tool_types | Attribute: "Tool Type" |
| tool_version | Attribute: "Tool Version" |
Campaign
ThreatConnect object type: Campaign Group
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| aliases | Attribute: "Alias" |
| confidence | Attribute: "Confidence" |
| created | Attribute: "External Date Created" |
| external_reference | Attribute: "External Reference" |
| first_seen | Attribute: "First Seen" |
| id | Attribute: "External ID" |
| labels | Tags |
| last_seen | Attribute: "Last Seen" |
| modified | Attribute: "External Date Modified" |
| name | Name/Summary |
| object_marking_ref/name | Security Labels |
| objective | Attribute: "Campaign Objective" |
Vulnerability
ThreatConnect object type: Vulnerability Group
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| confidence | Attribute: "Confidence" |
| created | Attribute: "External Date Created" |
| description | Description |
| id | Attribute: "External ID" |
| labels | Tags |
| modified | Attribute: "External Date Modified" |
| name | Name/Summary |
| object_marking_ref/name | Security Labels |
Signature (YARA)
ThreatConnect object type: Signature Group
| Accenture iDefense API Field | ThreatConnect Field |
|---|---|
| confidence | Attribute: "Confidence" |
| created | Attribute: "External Date Created" |
| description | Description |
| id | Attribute: "External ID" |
| kill_chain_phases | Attribute: "Phase of Intrusion" |
| labels | Tags |
| modified | Attribute: "External Date Modified" |
| name | Name/Summary |
| object_marking_ref/name | Security Labels |
| revoked | Attribute: "Active" |
Frequently Asked Questions (FAQ)
How does the Accenture iDefense Intelligence Engine App differ from the Accenture iDefense IntelGraph Intelligence Engine App?
Accenture changed its intel delivery from IntelGraph to a TAXII 2.1 server solution. This means the integration data are formatted with the STIX 2.1 standard format.
Between the two Apps, users can expect differences in the data ingested by each one. These data differences, which are due to limitations of the STIX 2.1 data format, mean that there are fewer intel data points in Accenture's new implementation for intel delivery.
Accenture will end support of its iDefense IntelGraph solution on October 16, 2023. After the end-of-support date, the Accenture iDefense IntelGraph Intelligence Engine App will not be able to collect data from Accenture iDefense.
ThreatConnect® is a registered trademark, and TC Exchange™ is a trademark, of ThreatConnect, Inc.
Accenture™ is a trademark of Accenture Global Services Limited.
iDefense® is a registered trademark of Accenture.
JavaScript® is a registered trademark of Oracle Corporation.
STIX™ and TAXII™ is a trademark of The MITRE Corporation.
30081-02 EN Rev. A


