- 11 Jun 2025
- 4 Minutes to read
-
Print
-
DarkLight
-
PDF
AbuseIPDB Enrichment
- Updated on 11 Jun 2025
- 4 Minutes to read
-
Print
-
DarkLight
-
PDF
Overview
The AbuseIPDB built-in enrichment in ThreatConnect® allows you to check the real-time enrichment of IP addresses with the Confidence of Abuse percentage provided by AbuseIPDB. You can use this information to determine the risk level of IP addresses interacting with your network or systems to prevent future attacks.
This article describes how to enable and configure the AbuseIPDB built-in enrichment and view data from the enrichment on the Enrichment tab of an Address Indicator’s Details screen.
Before You Start
User Roles
- To enable and configure the AbuseIPDB enrichment, your user account must have a System role of Administrator.
- To view AbuseIPDB data on the Enrichment tab of an Indicator’s Details screen, your user account can have any Organization role.
- To retrieve data manually on the AbuseIPDB card on the Enrichment tab of an Indicator’s Details screen, your user account can have any Organization role.
Enabling the AbuseIPDB Enrichment
Follow these steps to enable and configure the AbuseIPDB enrichment on your ThreatConnect instance:
- Hover over Settings
 on the top navigation bar and select System Settings.
on the top navigation bar and select System Settings. - Select the Indicators tab on the System Settings screen and then click Enrichment Tools in the menu on the left side of the screen.
- Click Edit
 in the Options column for AbuseIPDB and fill out the fields on the Edit Vendor window (Figure 1) as follows:
in the Options column for AbuseIPDB and fill out the fields on the Edit Vendor window (Figure 1) as follows: 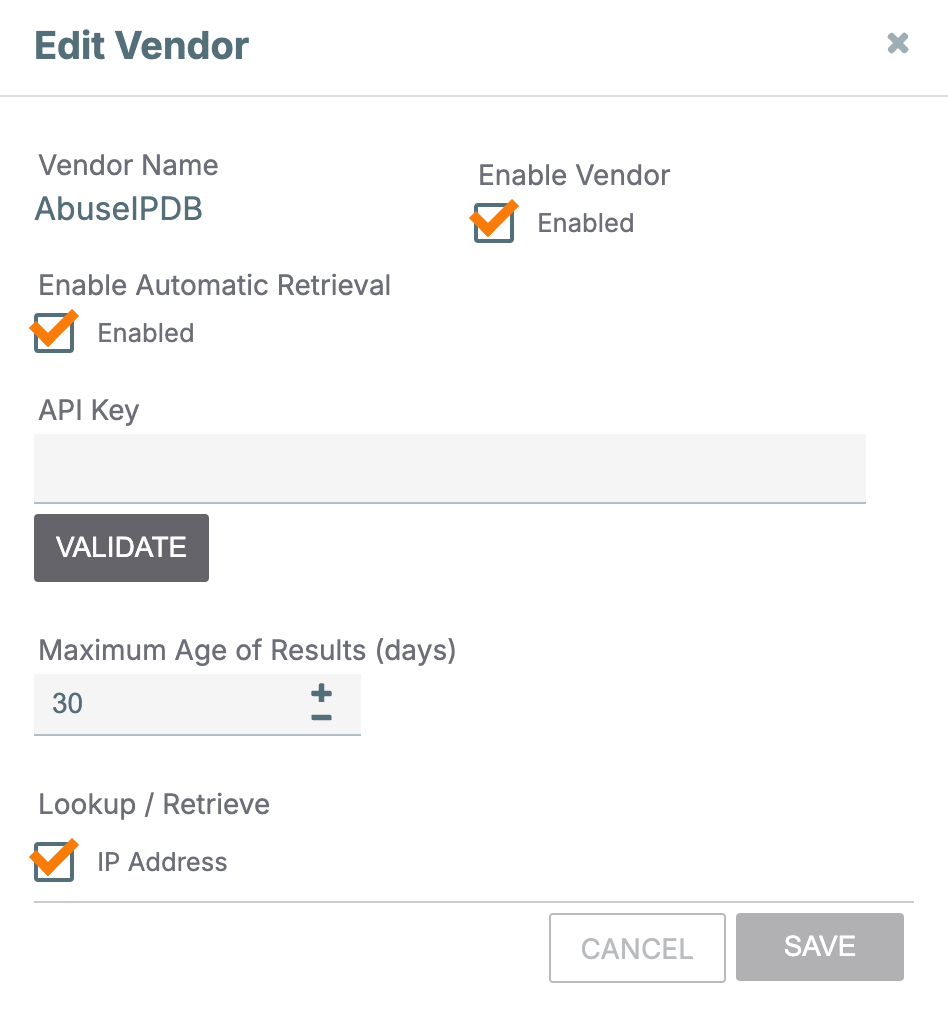
- Enable Vendor: Select this checkbox to enable AbuseIPDB.
- Enable Automatic Retrieval: Select this checkbox to enable automatic data retrieval for AbuseIPDB. If automatic data retrieval is enabled, AbuseIPDB data will automatically populate when a user clicks on an Address Indicator’s Enrichment tab for the first time. This checkbox is selected by default.
- API Key: Enter the API key that will be used to retrieve data from AbuseIPDB.HintYou can create a free AbuseIPDB API user account at https://www.abuseipdb.com/register.
- VALIDATE: After entering the AbuseIPDB API key, click this button to validate it. If the API key is accepted, the VALIDATE button’s label will change to VALID.
- Maximum Age of Results (days): Enter the maximum number of days in the past for which AbuseIPDB should query for results. Limiting results based on age helps avoid false positives and ensures that returned data remain relevant and actionable.
- Lookup/Retrieve: Select the Indicator type(s) for which to retrieve data from AbuseIPDB. The only available Indicator type is IP Address.
- Click the SAVE button to save the configuration for AbuseIPDB.
When AbuseIPDB is enabled, a value of true will be displayed in the Enabled column for its entry on the Enrichment Tools screen.
Data Overview
The Overview section of the AbuseIPDB card (Figure 2) on the Enrichment tab of an Address Indicator’s Details screen provides a summary of data retrieved from AbuseIPDB for the Indicator and the date and time the data were last retrieved.
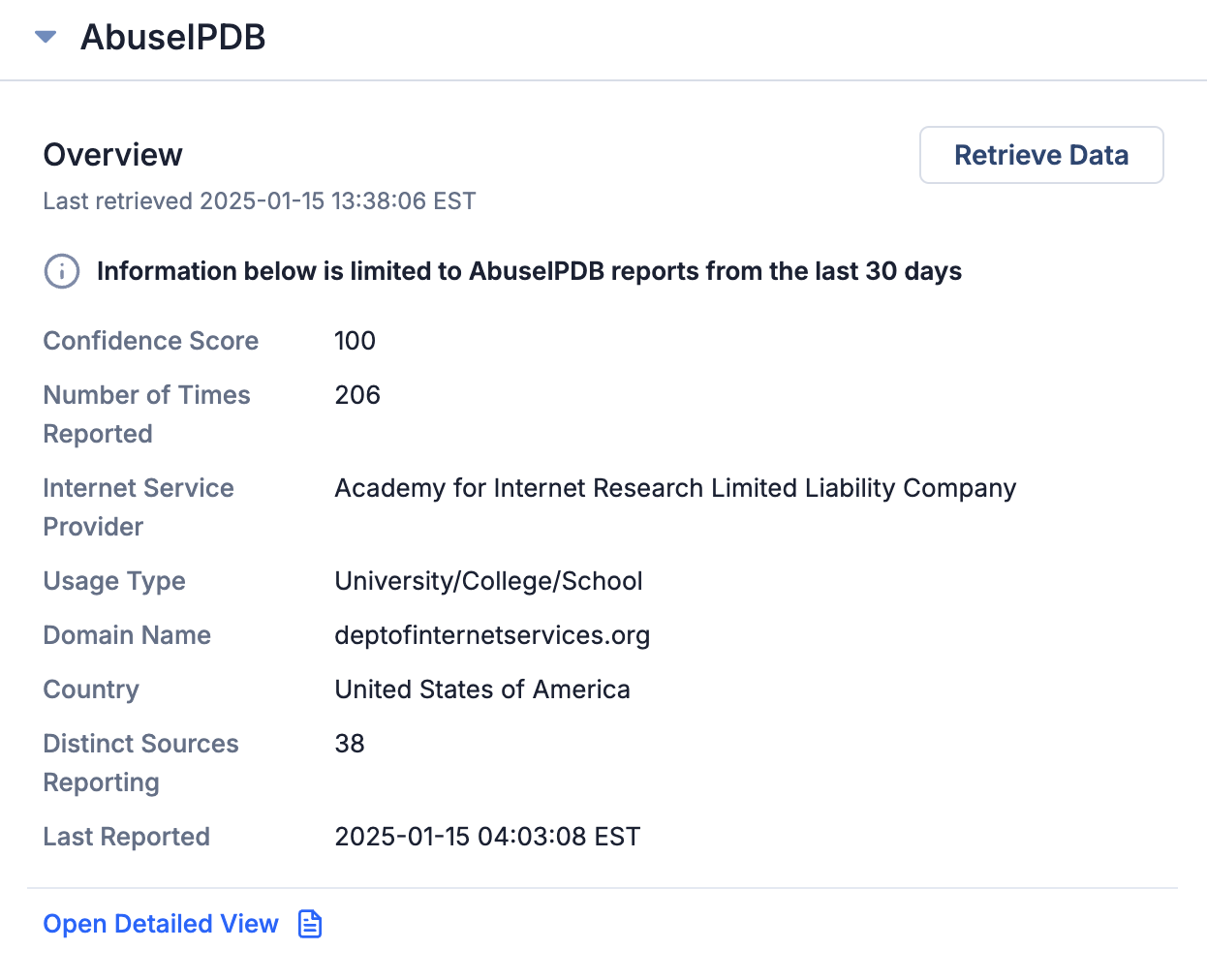
- Confidence Score: The Confidence of Abuse percentage calculated by AbuseIPDB. It is a rating, from 0 to 100, of how confident AbuseIPDB is, based on user reports, that an IP address is entirely malicious.
- Number of Times Reported: The number of times the Address was reported to AbuseIPDB during the time period for which data were retrieved.
- Internet Service Provider: The Internet Service Provider for the Address.
- Usage Type: The type of entity using the Address.
- Domain Name: The domain name for the Address.
- Country: The country in which the Address is registered.
- Distinct Sources Reporting: The number of unique reporters of the Address for the time period for which data were retrieved.
- Last Reported: The data and time when the Address was last reported to AbuseIPDB.
AbuseIDPB Detailed View
Click the Open Detailed View link on the AbuseIPDB card to display the AbuseIPDB Detailed View drawer. This drawer displays cards with additional data retrieved from AbuseIPDB. The cards are collapsed by default. Figure 3 shows the AbuseIPDB Detailed View drawer with all available cards expanded.
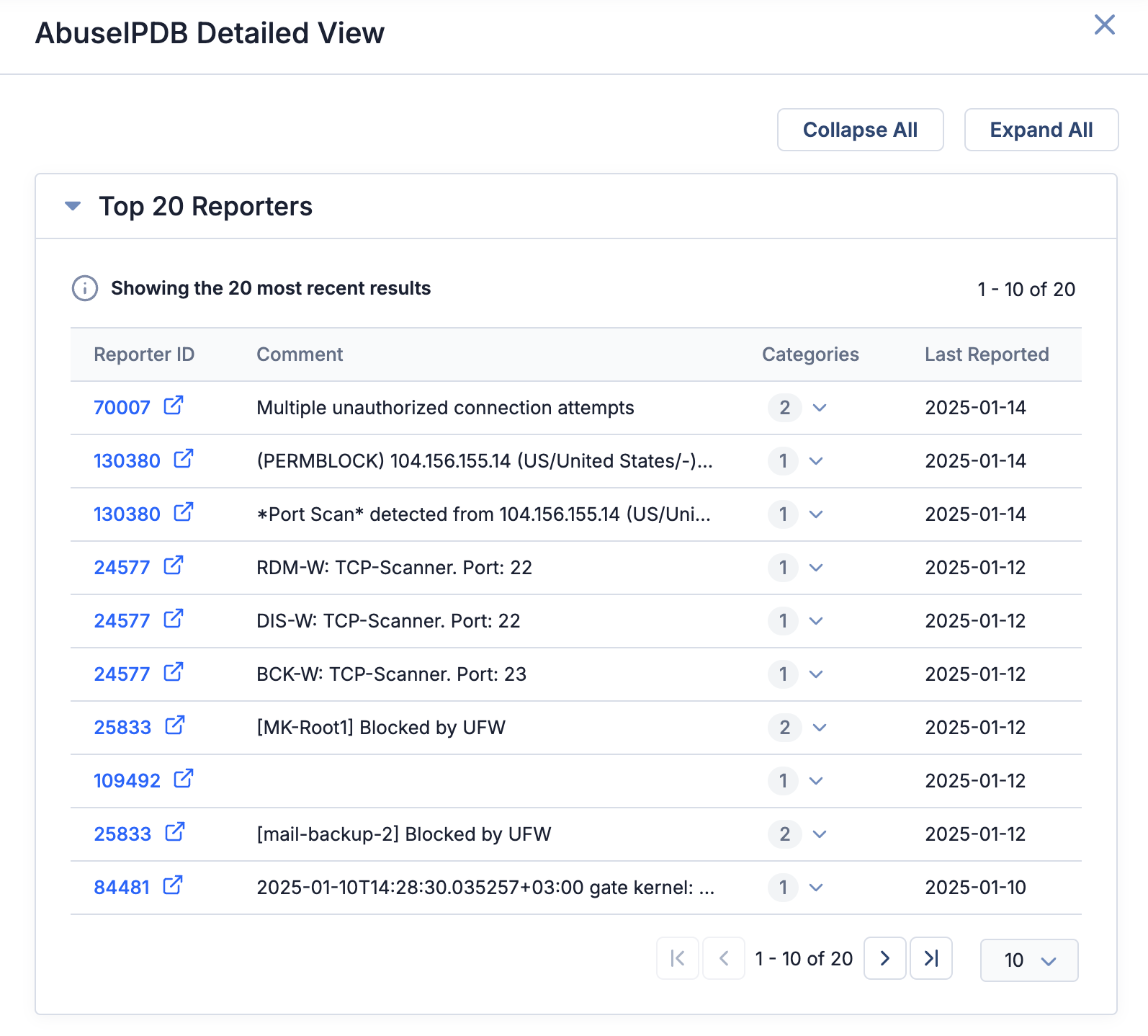
See Table 1 for a list of cards that may be displayed on the AbuseIPDB Detailed View drawer for an Address Indicator.
| Card Name | Description |
|---|---|
| Top 20 Reporters | This card displays details about the 20 most recent reports submitted by different users (or automated systems) about potentially malicious activity for the Address. Details displayed include a unique identifier assigned to the individual or system that submitted the report (click to view the reporter’s AbuseIPDB profile page), a comment detailing the malicious activity associated with the Address as described by the reporter, the number and names of the malicious activity types reported for the Address, and the date when the report was submitted. |
Retrieving Data Manually
When you click on an Address Indicator’s Enrichment tab for the first time, data will be retrieved from AbuseIPDB automatically if your System Administrator has enabled automatic data retrieval for AbuseIPDB. Otherwise, a message stating that “Automatic Data Retrieval has been disabled by the System Administrator” will be displayed on the card, and you will need to click the Retrieve Data button to populate the card with data. Once data have been retrieved, they will be cached for a period of time configured by your System Administrator. Each time you revisit that Indicator’s Enrichment tab, the cached AbuseIPDB data will be displayed until this period of time has passed.
To retrieve the latest AbuseIPDB data for the Indicator manually, click the Retrieve Data button on the AbuseIPDB card (Figure 2).
Enriching Indicators Using the ThreatConnect API
You can also use the ThreatConnect v3 API to enrich Address Indicators with data from AbuseIPDB. For instructions on using the ThreatConnect v3 API to enrich Indicators, see Indicator Enrichment Overview.
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
20146-09 v.01.C


