- 04 Sep 2025
- 3 Minutes to read
-
Print
-
DarkLight
-
PDF
Polarity Practical Use Case Exercises
- Updated on 04 Sep 2025
- 3 Minutes to read
-
Print
-
DarkLight
-
PDF
Polarity Practical Exercises
Prepare
Step 1
Place your Overlay Window over the right side of this page.
Step 2
Scroll down through each example and follow the directions given.
SIEM
Polarity is designed to augment your workflow, no matter which application you are viewing.
This example showcases how Polarity can augment your workflow when looking at information in a SIEM or other data aggregator.
Step 1
Select all of the text from the SIEM example area below and
Hold CTRL + C (Command + C for macOS)
or
Copy the text to your system clipboard, right click in the Polarity Overlay Window, and select “Search my Clipboard”.
| ||
|---|---|---|
i | Time | Event |
> | 1613415125 | 37,21.690344,192.168.55.133,162.159.241.165,TCP,54,62099 > 443 [ACK] Seq=1 Ack=39 Win=65535 Len=0,, field5 = TCPhost = ip-172-31-57-135.ec2.internalsource = Firewall Traffic - Sheet1.csvsourcetype = csv |
> | 2/15/21 1:52:05:000 PM | 37,21.690344,192.168.55.133,162.159.241.165,TCP,54,62099 > 443 [ACK] Seq=1 Ack=39 Win=65535 Len=0,, field5 = TCPhost = ip-172-31-57-135.ec2.internalsource = Firewall Traffic - Sheet1.csvsourcetype = csv |
> | 2/15/21 1:52:05:000 PM | 37,21.690344,192.168.55.133,162.159.241.165,TCP,54,62099 > 443 [ACK] Seq=1 Ack=39 Win=65535 Len=0,, field5 = TCPhost = ip-172-31-57-135.ec2.internalsource = Firewall Traffic - Sheet1.csvsourcetype = csv |
> | 2/15/21 1:52:05:000 PM | 34,19.706099,192.168.55.133,74.125.226.175,SSL,55,Continuation Data,, field5 = SSLhost = ip-172-31-57-135.ec2.internalsource = Firewall Traffic - Sheet1.csvsourcetype = csv |
> | 2/15/21 1:52:05.000 PM | 33,19.233835,,192.168.55.133,TCP,60,80 > 62101 [ACK] Seq=2 Ack=2 Win=64239 Len=0,, field5 = TCPhost = ip-172-31-57-135.ec2.internalsource = Firewall Traffic - Sheet1.csvsourcetype = csv |
> | 2/15/21 1:52:05.000 PM | 32,19.233734,192.168.55.133,108.162.232.205,TCP,54,"62101 > 80 [FIN, ACK] Seq=1 Ack=2 Win=64240 Len=0",, field5 = TCPhost = ip-172-31-57-135.ec2.internalsource = Firewall Traffic - Sheet1.csvsourcetype = csv |
> | 2/15/21 1:52:05:000 PM | 31,19.233649,192.168.55.133,45.128.134.14,TCP,54,62101 > 80 [ACK] Seq=1 Ack=2 Win=64240 Len=0,, field5 = TCPhost = ip-172-31-57-135.ec2.internalsource = Firewall Traffic - Sheet1.csvsourcetype = csv |
> | 2/15/21 1:52:05.000 PM | 30,19.233649,108.162.232.205,192.168.55.133,TCP,60,"80 > 62101 [FIN, PSH, ACK] Seq=1 Ack=1 Win=64240 Len=0",, field5 = TCPhost = ip-172-31-57-135.ec2.internalsource = Firewall Traffic - Sheet1.csvsourcetype = csvv |
> | 2/15/21 1:52:05.000 PM | 29,19.23343, 207.154.198.54, 192.168.55.133,TCP,,80 > 62100 [ACK] Seq=2 Ack=2 Win=64239 Len=0,, field5 = TCPhost = ip-172-31-57-135.ec2.internalsource = Firewall Traffic - Sheet1.csvsourcetype = csv |
Step 2
You should now see results from your subscribed Integrations in the Polarity Overlay Window!
Optional Step
If you would like to try Polarity On-Screen recognition:
Click on either Stream or Highlight Mode in your Polarity Overlay Window.
Click back into this window.
Scroll back up to the SIEM example, and watch Polarity start highlighting data it recognizes!
Endpoint
This example showcases how Polarity can augment your workflow when you are viewing information in an Endpoint Protection System.
Step 1
Select all of the text from the Endpoint example area below and
Hold CTRL + C (Command + C for macOS)
or
Copy the text to your system clipboard, right click in the Polarity Overlay Window, and select “Search my Clipboard”.
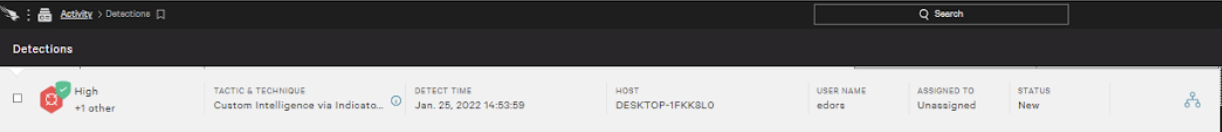
TECHNIQUE ID
CST0005
ECIA NAME
IOCRolicySHA256High
TRIGGERING INDICATORS
Associated IOC (SHA256 on library/DLL loaded)
b2191c32538842d3fdeff972e5a77527fa35d69fa400aad2aa2798b86fc6cf2a
FC00964131A8C9407BA77484E724FC9D
GLOBAL PREVALENCE
Common
LOCAL PREVALENCE
Low
USER NAME
DESKTOP-1FKKSLO
Step 2
You should now see results from your subscribed Integrations in the Polarity Overlay Window!
Optional Step
If you would like to try Polarity On-Screen recognition:
Click on either Stream or Highlight Mode in your Polarity Overlay Window.
Click back into this window.
Scroll back up to the Endpoint example, and watch Polarity start highlighting data it recognizes!
Ticketing
This example showcases how Polarity can augment your workflow when viewing information in a Ticketing product.
Step 1
Select all of the text from the Ticketing example area below and
Hold CTRL + C (Command + C for macOS)
or
Copy the text to your system clipboard, right click in the Polarity Overlay Window, and select “Search my Clipboard”.
Sender: helpdesk@msdn-update[.]com
Recipient: jane@yourcompany[.]com
Sender IP: 198.54.117[.]198
Domain: msdn-update[.]com
Recipient Internal IP: 10.10.240.17
Attachment:
crashreporter.exe
Hashes:
MD5 a20722e4bd3a6a35c8dfbb99f2cad8c0
SHA-1 8eef1361b6f8a464fc7170deaebac07dd5d681c6
SHA-256 7e8e748f39b0bff7dd70eee3c1d08241565c07ce9bfe687c18ee727cfb2bc5cfStep 2
You should now see results from your subscribed Integrations in the Polarity Overlay Window!
Optional Step
If you would like to try Polarity On-Screen recognition:
Click on either Stream or Highlight Mode in your Polarity Overlay Window.
Click back into this window.
Scroll back up to the Endpoint example, and watch Polarity start highlighting data it recognizes!
Focus Mode
Sometimes, the text is not directly accessible even though you can see it on your monitor, such as shared screen data in a meeting, a remote VDI session, or when it’s embedded in a picture.
This example showcases how Polarity can augment your workflow by running an On-Demand Search over text that is not directly accessible.
Step 1
Click on the "Focus" button in the top window bar of the Overlay Window.
Step 2
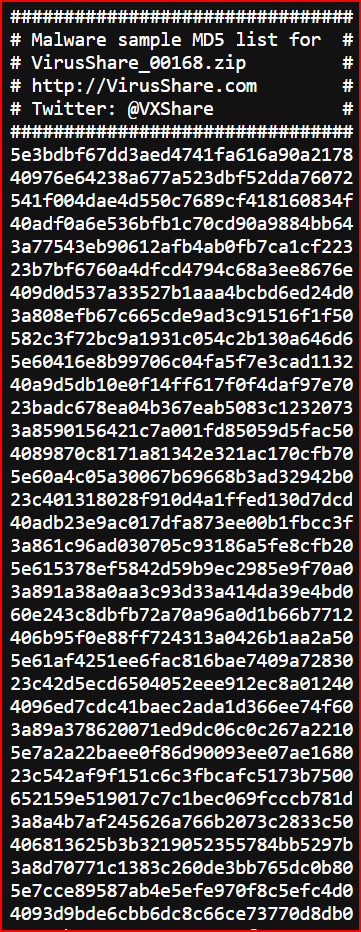
Draw a box around the picture of either the list of hashes or the QR code below (or both!).

Step 3
You should now see results from your subscribed Integrations in the Polarity Overlay Window!
What's next?
Back to Training Center
Get the Browser Plugin


.png)
